pku 1107:
Description
Weird Wally's Wireless Widgets, Inc. manufactures an eclectic assortment of small, wireless, network capable devices, ranging from dog collars, to pencils, to fishing bobbers. All these devices have very small memories. Encryption algorithms like Rijndael, the candidate for the Advanced Encryption Standard (AES) are demonstrably secure but they don't fit in such a tiny memory. In order to provide some security for transmissions to and from the devices, WWWW uses the following algorithm, which you are to implement.
Encrypting a message requires three integer keys, k1, k2, and k3. The letters [a-i] form one group, [j-r] a second group, and everything else ([s-z] and underscore) the third group. Within each group the letters are rotated left by ki positions in the message. Each group is rotated independently of the other two. Decrypting the message means doing a right rotation by ki positions within each group.
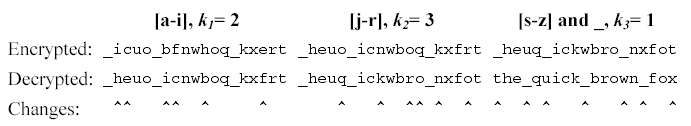
Consider the message the_quick_brown_fox encrypted with ki values of 2, 3 and 1. The encrypted string is _icuo_bfnwhoq_kxert. The figure below shows the decrypting right rotations for one character in each of the three character groups.
Encrypting a message requires three integer keys, k1, k2, and k3. The letters [a-i] form one group, [j-r] a second group, and everything else ([s-z] and underscore) the third group. Within each group the letters are rotated left by ki positions in the message. Each group is rotated independently of the other two. Decrypting the message means doing a right rotation by ki positions within each group.
Consider the message the_quick_brown_fox encrypted with ki values of 2, 3 and 1. The encrypted string is _icuo_bfnwhoq_kxert. The figure below shows the decrypting right rotations for one character in each of the three character groups.


题目大意:给出一种加密方式,现在给出明文让你解密生成密文。这种加密方式的细节是,对于一个密文字符串,将其分成三个组,然后对应三个密匙k1、k2、k3.加密过程是一个轮转过程,以第一组为例,其字符集合形式是{a,b,c,d},对应的位置集合是{2,4,6,7}这两个集合的元素形成一一映射,设密匙k1 = 2,则完成对字符集合向左轮转k1次,而位置集合不变,即加密之后字符集合编程{c、d、a、b}。(这里也可以参考题目描述中给出的解释)。三组字符串分别进行这种轮换,然后基于字符集合和位置集合的一一映射,得到明文。
分析:
数据结构:
很显然我们应该建立三个字符串数组来分别记录三组字符,而对于每个字符,通过对加密方式的理解能够看到,它在字符串中的位置非常重要,因此这里我们应该建立记录每个字符参数的结构体。
解密方法:能够看到,这种加密方式的揭秘方法非常简单,考虑到加密是完成向左的轮转,解密自然而然是向右轮转。
程序语言实现解密:这里我们先利用一个空串str来记录解密后的密文,现在我们有第一组的字符集合c = {c1,c2,c3,c4…cn},及与之形成一一映射的位置集合num = {num1,num2,num3…numn},密匙是k1,则遍历num数组,有如下的对应关系:
str[numi + k1] = ci.
同样对于第二组和第三组,也是相同的解谜思路。
接下来便是模拟编程实现了。
#include<cstdio> #include<cstring> using namespace std; const int maxn = 85; struct ele { char c; int p; }; int main() { char str[maxn]; int k1 , k2 , k3; struct ele group1[maxn] , group2[maxn] , group3[maxn]; while(scanf("%d%d%d",&k1,&k2,&k3) != EOF) { getchar(); scanf("%s",str); int index1 , index2 , index3; index1 = 0; index2 = 0; index3 = 0; for(int i = 0;i < strlen(str);i++) { if(str[i] >= 'a' && str[i] <= 'i') group1[index1].p = i , group1[index1++].c = str[i]; else if(str[i] >= 'j' && str[i] <= 'r') group2[index2].p = i , group2[index2++].c = str[i]; else group3[index3].p = i , group3[index3++].c = str[i]; }//分组并记录字符的参数 //解密 for(int i = 0;i < index1;i++) { int j = i + k1; if(j >= index1) j %= index1;//因为是一个轮转,千万不要忘记取余 str[group1[j].p] = group1[i].c; } for(int i = 0;i < index2;i++) { int j = i + k2; if(j >= index2) j %= index2; str[group2[j].p] = group2[i].c; } for(int i = 0;i < index3;i++) { int j = i + k3; if(j >= index3) j %= index3; str[group3[j].p] = group3[i].c; } printf("%s ",str); } }