背景:
1客户A和B俩台主机之间需要实现免密钥登录,已绑定腾讯云申请的密钥对
系统:centos7.3
A:192.168.0.100
B:192.168.0.84
A主机的私钥文件:aaa
B主机的私钥文件:bbb
公钥文件:authorized_keys
/etc/ssh/sshd.conf文件修改参数,前面有“#”注释符的需要去掉
HostKey /etc/ssh/ssh_host_rsa_key
RSAAuthentication yes
PubkeyAuthentication yes
AuthorizedKeysFile .ssh/authorized_keys
PasswordAuthentication no
参考sshd_config配置文件,注意系统版本,不适用centos6.x版本,修改配置文件前做好备份

1 # $OpenBSD: sshd_config,v 1.93 2014/01/10 05:59:19 djm Exp $ 2 3 # This is the sshd server system-wide configuration file. See 4 # sshd_config(5) for more information. 5 6 # This sshd was compiled with PATH=/usr/local/bin:/usr/bin 7 8 # The strategy used for options in the default sshd_config shipped with 9 # OpenSSH is to specify options with their default value where 10 # possible, but leave them commented. Uncommented options override the 11 # default value. 12 13 # If you want to change the port on a SELinux system, you have to tell 14 # SELinux about this change. 15 # semanage port -a -t ssh_port_t -p tcp #PORTNUMBER 16 # 17 #Port 22 18 #AddressFamily any 19 #ListenAddress 192.168.0.100 20 #ListenAddress 192.168.0.100 21 22 # The default requires explicit activation of protocol 1 23 #Protocol 2 24 25 # HostKey for protocol version 1 26 #HostKey /etc/ssh/ssh_host_key 27 # HostKeys for protocol version 2 28 HostKey /etc/ssh/ssh_host_rsa_key 29 #HostKey /etc/ssh/ssh_host_dsa_key 30 HostKey /etc/ssh/ssh_host_ecdsa_key 31 HostKey /etc/ssh/ssh_host_ed25519_key 32 33 # Lifetime and size of ephemeral version 1 server key 34 #KeyRegenerationInterval 1h 35 #ServerKeyBits 1024 36 37 # Ciphers and keying 38 #RekeyLimit default none 39 40 # Logging 41 # obsoletes QuietMode and FascistLogging 42 #SyslogFacility AUTH 43 SyslogFacility AUTHPRIV 44 #LogLevel INFO 45 46 # Authentication: 47 48 #LoginGraceTime 2m 49 #PermitRootLogin yes 50 #StrictModes yes 51 #MaxAuthTries 6 52 #MaxSessions 10 53 54 RSAAuthentication yes 55 PubkeyAuthentication yes 56 57 # The default is to check both .ssh/authorized_keys and .ssh/authorized_keys2 58 # but this is overridden so installations will only check .ssh/authorized_keys 59 AuthorizedKeysFile .ssh/authorized_keys 60 61 #AuthorizedPrincipalsFile none 62 63 #AuthorizedKeysCommand none 64 #AuthorizedKeysCommandUser nobody 65 66 # For this to work you will also need host keys in /etc/ssh/ssh_known_hosts 67 #RhostsRSAAuthentication no 68 # similar for protocol version 2 69 #HostbasedAuthentication no 70 # Change to yes if you don't trust ~/.ssh/known_hosts for 71 # RhostsRSAAuthentication and HostbasedAuthentication 72 #IgnoreUserKnownHosts no 73 # Don't read the user's ~/.rhosts and ~/.shosts files 74 #IgnoreRhosts yes 75 76 # To disable tunneled clear text passwords, change to no here! 77 #PasswordAuthentication no 78 #PermitEmptyPasswords no 79 PasswordAuthentication no 80 81 # Change to no to disable s/key passwords 82 #ChallengeResponseAuthentication yes 83 ChallengeResponseAuthentication no 84 85 # Kerberos options 86 #KerberosAuthentication no 87 #KerberosOrLocalPasswd yes 88 #KerberosTicketCleanup yes 89 #KerberosGetAFSToken no 90 #KerberosUseKuserok yes 91 92 # GSSAPI options 93 GSSAPIAuthentication yes 94 GSSAPICleanupCredentials no 95 #GSSAPIStrictAcceptorCheck yes 96 #GSSAPIKeyExchange no 97 #GSSAPIEnablek5users no 98 99 # Set this to 'yes' to enable PAM authentication, account processing, 100 # and session processing. If this is enabled, PAM authentication will 101 # be allowed through the ChallengeResponseAuthentication and 102 # PasswordAuthentication. Depending on your PAM configuration, 103 # PAM authentication via ChallengeResponseAuthentication may bypass 104 # the setting of "PermitRootLogin without-password". 105 # If you just want the PAM account and session checks to run without 106 # PAM authentication, then enable this but set PasswordAuthentication 107 # and ChallengeResponseAuthentication to 'no'. 108 # WARNING: 'UsePAM no' is not supported in Red Hat Enterprise Linux and may cause several 109 # problems. 110 UsePAM yes 111 112 #AllowAgentForwarding yes 113 #AllowTcpForwarding yes 114 #GatewayPorts no 115 X11Forwarding yes 116 #X11DisplayOffset 10 117 #X11UseLocalhost yes 118 #PermitTTY yes 119 #PrintMotd yes 120 #PrintLastLog yes 121 #TCPKeepAlive yes 122 #UseLogin no 123 UsePrivilegeSeparation sandbox # Default for new installations. 124 #PermitUserEnvironment no 125 #Compression delayed 126 #ClientAliveInterval 0 127 #ClientAliveCountMax 3 128 #ShowPatchLevel no 129 UseDNS no 130 #PidFile /var/run/sshd.pid 131 #MaxStartups 10:30:100 132 #PermitTunnel no 133 #ChrootDirectory none 134 #VersionAddendum none 135 136 # no default banner path 137 #Banner none 138 139 # Accept locale-related environment variables 140 AcceptEnv LANG LC_CTYPE LC_NUMERIC LC_TIME LC_COLLATE LC_MONETARY LC_MESSAGES 141 AcceptEnv LC_PAPER LC_NAME LC_ADDRESS LC_TELEPHONE LC_MEASUREMENT 142 AcceptEnv LC_IDENTIFICATION LC_ALL LANGUAGE 143 AcceptEnv XMODIFIERS 144 145 # override default of no subsystems 146 Subsystem sftp /usr/libexec/openssh/sftp-server 147 148 # Example of overriding settings on a per-user basis 149 #Match User anoncvs 150 # X11Forwarding no 151 # AllowTcpForwarding no 152 # PermitTTY no 153 # ForceCommand cvs server
操作步骤
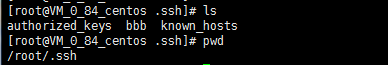
1.首先把aaa和bbb私钥文件分别上传到A主机和B主机上的/root/.ssh/目录中(上传可以安装lrzsz工具,直接拖文件到服务器即可)
A主机:
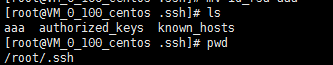
B:主机
2.将A主机中的authorized_keys中的公钥拷贝到B主机的authorized_keys文件中
将B主机中的authorized_keys中的公钥保存的A主机的authorized_keys文件中
A主机的authorized_keys文件
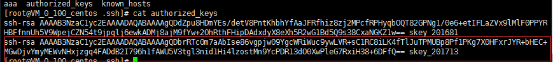
B主机的authorized_keys文件
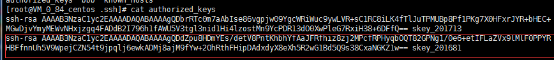
3.将A主机和B主机的私钥文件分别修改为id_rsa
A主机.ssh/目录下的内容
mv /root/.ssh/aaa /root/.ssh/id_rsa
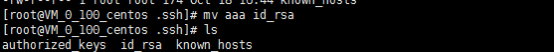
B主机.ssh/目录下的内容
mv /root/.ssh/aaa /root/.ssh/id_rsa
4.分别在A主机和B主机上执行下面授权操作
chmod 700 ~/.ssh/
chmod 600 ~/.ssh/authorized_keys
chmod 600 ~/.ssh/id_rsa
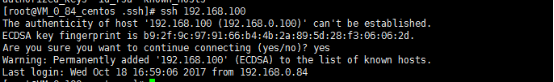
最后来验证
A主机远程B主机:
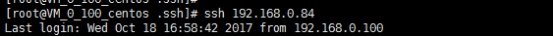
B主机远程A主机