那个男人必须die
一个魔改md5的题。
IDA打开文件,找到主函数一片红,发现有花指令。
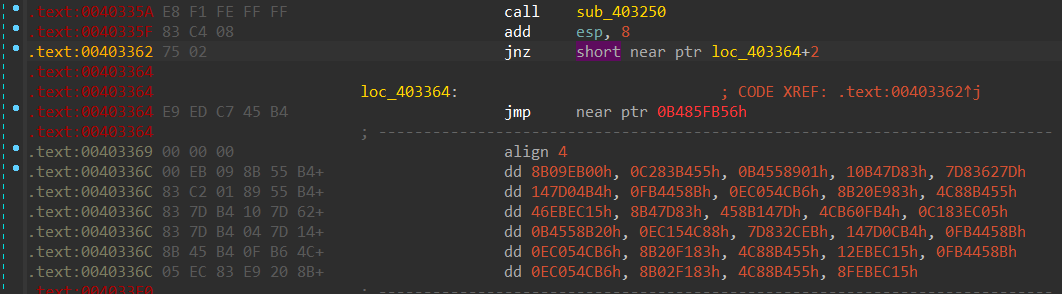
花指令为,0xe8,0xed。
patch一下
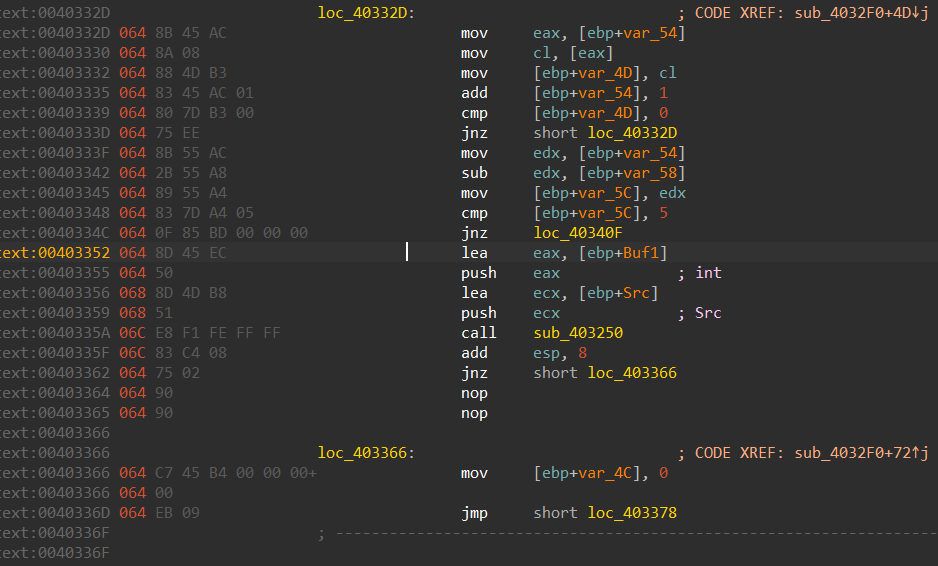
然后再函数头按p恢复成函数。然后再f5。成功恢复。

首先判断输入应为5个字符。

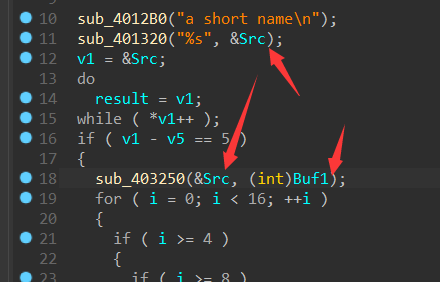
并把输入的字符传入sub_403250,然后返回给Buf1.
进入sub_403250看看。
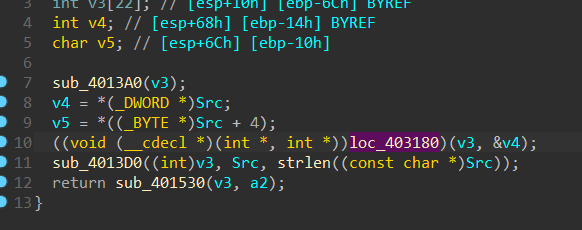
发现是将输入流拆开来赋值给v4和v5
然后传入loc_403180。进行4个常数的数组密钥生成
发现该函数也被花指令混淆,且垃圾数据一样,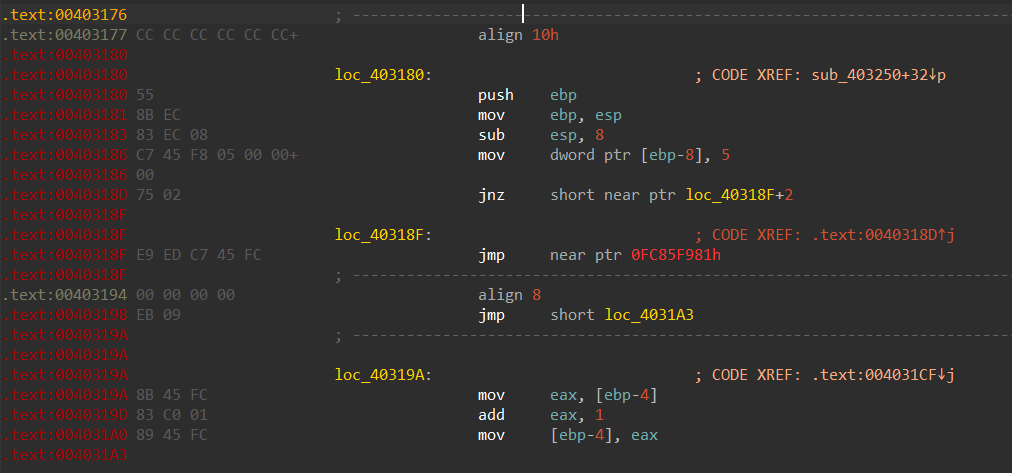
再一次patch掉。恢复如下
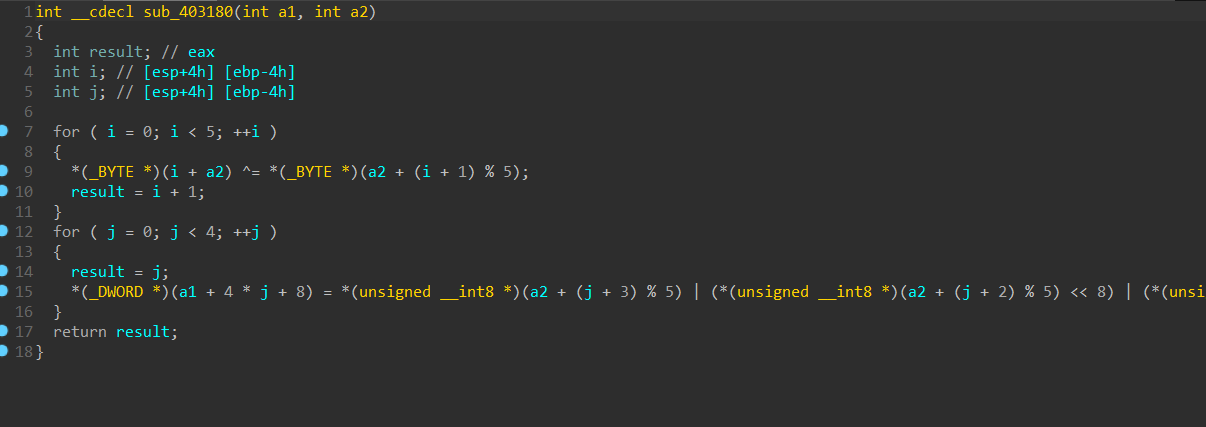
动调发现,是将5个字符的扩展然后异或的操作生成16个字符。
然后分成四组传入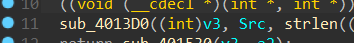
对md5的四个常数进行赋值。
然后再回到主函数中对输入的五个字符进行魔改的md5编码,然后再对生成的32个字符进行分组单字节加减,异或操作。然后比对硬编码。

通过复现他的算法。
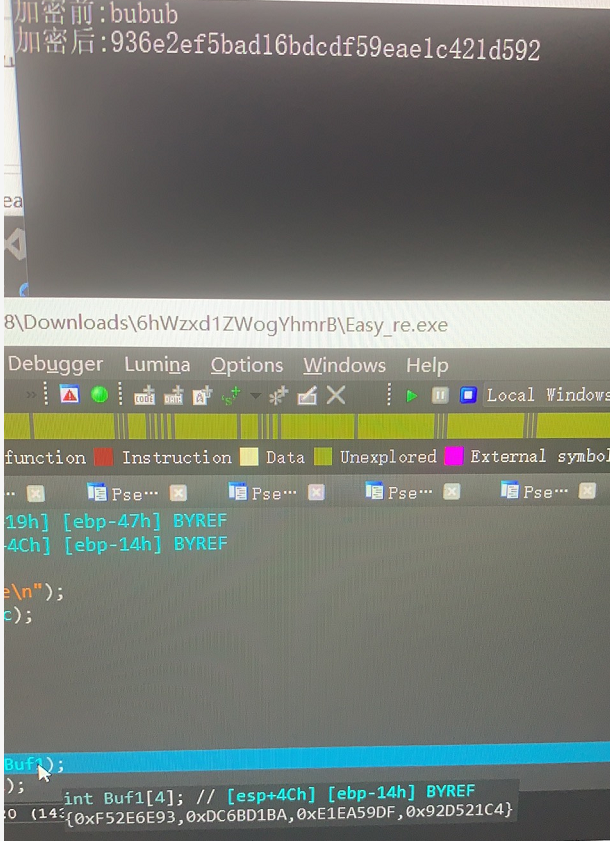
成功验证了我上面的猜想。那么要得到对应的硬编码,且输入只有5个字符。我们可以写一个爆破脚本进行爆破。
完整算法如下:
brute.cpp
#include <stdio.h>
#include <stdlib.h>
#include "md5.h"
#include<stdlib.h>
#include<string.h>
#define _CRT_SECURE_NO_WARNINGS;
#pragma warning(disable:4996);
int main(int argc, char* argv[])
{
int i1;
int j;
unsigned char encrypt[6] = "";
for (int k0 = 65; k0 < 123; k0++)
{
//printf("%c", k0);
for (int k1 = 65; k1 < 123; k1++)
{
for (int k2 = 65; k2 <123; k2 ++)
{
for (int k3 = 65; k3 < 123; k3++)
{
for (int k4 = 65; k4 < 123; k4++)
{
encrypt[0] = k0;
encrypt[1] = k1;
encrypt[2] = k2;
encrypt[3] = k3;
encrypt[4] = k4;
unsigned char encrypt1[6];
memcpy(encrypt1, encrypt, 6);
unsigned char decrypt[16];
MD5_CTX md5;
_int32 a1[4] = {};
for (i1 = 0; i1 < 5; ++i1)
*(i1 + encrypt) ^= *(encrypt + (i1 + 1) % 5);
for (j = 0; j < 4; ++j)
*(a1 + j) = *(encrypt + (j + 3) % 5) | (*(encrypt + (j + 2) % 5) << 8) | (*(j + encrypt + 1) << 16) | (*(j + encrypt) << 24);
//unsigned char encrypt1[] = "bubub";
MD5Init(&md5, a1);
MD5Update(&md5, encrypt1, strlen((char*)encrypt1));
MD5Final(&md5, decrypt);
//printf("%s
", encrypt1);
for (int i = 0; i < 16; ++i)
{
if (i >= 4)
{
if (i >= 8)
{
if (i >= 12)
*(decrypt + i) ^= 2u;
else
*(decrypt + i) ^= 0x20u;
}
else
{
*(decrypt + i) += 32;
}
}
else
{
*(decrypt + i) -= 32;
}
}
/* for (int i = 0; i < 16; i++)
{
printf( "%02x",decrypt[i]);
} */
unsigned char enc[] = { 0x66, 0x13, 0x48, 0xF1, 0x1B, 0x99, 0xF7, 0x84, 0x05, 0xB1,
0x54, 0x04, 0xC3, 0x52, 0xCA, 0x8D };
if (!memcmp(decrypt, &enc, 0xA))
{
printf("%s", encrypt1);
exit(1);
}
}
}
}
}
}
//unsigned char encrypt[] = "bubub";//21232f297a57a5a743894a0e4a801fc3
//unsigned char encrypt1[6];
//memcpy(encrypt1, encrypt, 6);
//
//unsigned char decrypt[16];
//MD5_CTX md5;
//_int32 a1[4] = {};
//for (i1 = 0; i1 < 5; ++i1)
// *(i1 + encrypt) ^= *(encrypt + (i1 + 1) % 5);
//for (j = 0; j < 4; ++j)
// *(a1 +j ) = *(encrypt + (j + 3) % 5) | (*(encrypt + (j + 2) % 5) << 8) | (*(j + encrypt + 1) << 16) | (*(j + encrypt) << 24);
////unsigned char encrypt1[] = "bubub";
//MD5Init(&md5,a1);
//MD5Update(&md5, encrypt1, strlen((char*)encrypt1));
//MD5Final(&md5, decrypt);
//printf("加密前:%s
加密后:", encrypt1);
/*for (int i = 0; i < 16; i++)
{
printf("%02x", decrypt[i]);
}*/
getchar();
return 0;
}
md5.cpp
#include <memory.h>
#include "md5.h"
unsigned char PADDING[] = { 0x80,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,
0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,
0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,
0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0 };
void MD5Init(MD5_CTX* context,__int32 a1[])
{
context->count[0] = 0;
context->count[1] = 0;
context->state[0] = a1[0];
context->state[1] = a1[1];
context->state[2] = a1[2];
context->state[3] = a1[3];
}
void MD5Update(MD5_CTX* context, unsigned char* input, unsigned int inputlen)
{
unsigned int i = 0, index = 0, partlen = 0;
index = (context->count[0] >> 3) & 0x3F;
partlen = 64 - index;
context->count[0] += inputlen << 3;
if (context->count[0] < (inputlen << 3))
context->count[1]++;
context->count[1] += inputlen >> 29;
if (inputlen >= partlen)
{
memcpy(&context->buffer[index], input, partlen);
MD5Transform(context->state, context->buffer);
for (i = partlen; i + 64 <= inputlen; i += 64)
MD5Transform(context->state, &input[i]);
index = 0;
}
else
{
i = 0;
}
memcpy(&context->buffer[index], &input[i], inputlen - i);
}
void MD5Final(MD5_CTX* context, unsigned char digest[16])
{
unsigned int index = 0, padlen = 0;
unsigned char bits[8];
index = (context->count[0] >> 3) & 0x3F;
padlen = (index < 56) ? (56 - index) : (120 - index);
MD5Encode(bits, context->count, 8);
MD5Update(context, PADDING, padlen);
MD5Update(context, bits, 8);
MD5Encode(digest, context->state, 16);
}
void MD5Encode(unsigned char* output, unsigned int* input, unsigned int len)
{
unsigned int i = 0, j = 0;
while (j < len)
{
output[j] = input[i] & 0xFF;
output[j + 1] = (input[i] >> 8) & 0xFF;
output[j + 2] = (input[i] >> 16) & 0xFF;
output[j + 3] = (input[i] >> 24) & 0xFF;
i++;
j += 4;
}
}
void MD5Decode(unsigned int* output, unsigned char* input, unsigned int len)
{
unsigned int i = 0, j = 0;
while (j < len)
{
output[i] = (input[j]) |
(input[j + 1] << 8) |
(input[j + 2] << 16) |
(input[j + 3] << 24);
i++;
j += 4;
}
}
void MD5Transform(unsigned int state[4], unsigned char block[64])
{
unsigned int a = state[0];
unsigned int b = state[1];
unsigned int c = state[2];
unsigned int d = state[3];
unsigned int x[64];
MD5Decode(x, block, 64);
FF(a, b, c, d, x[0], 7, 0xd76aa478); /* 1 */
FF(d, a, b, c, x[1], 12, 0xe8c7b756); /* 2 */
FF(c, d, a, b, x[2], 17, 0x242070db); /* 3 */
FF(b, c, d, a, x[3], 22, 0xc1bdceee); /* 4 */
FF(a, b, c, d, x[4], 7, 0xf57c0faf); /* 5 */
FF(d, a, b, c, x[5], 12, 0x4787c62a); /* 6 */
FF(c, d, a, b, x[6], 17, 0xa8304613); /* 7 */
FF(b, c, d, a, x[7], 22, 0xfd469501); /* 8 */
FF(a, b, c, d, x[8], 7, 0x698098d8); /* 9 */
FF(d, a, b, c, x[9], 12, 0x8b44f7af); /* 10 */
FF(c, d, a, b, x[10], 17, 0xffff5bb1); /* 11 */
FF(b, c, d, a, x[11], 22, 0x895cd7be); /* 12 */
FF(a, b, c, d, x[12], 7, 0x6b901122); /* 13 */
FF(d, a, b, c, x[13], 12, 0xfd987193); /* 14 */
FF(c, d, a, b, x[14], 17, 0xa679438e); /* 15 */
FF(b, c, d, a, x[15], 22, 0x49b40821); /* 16 */
/* Round 2 */
GG(a, b, c, d, x[1], 5, 0xf61e2562); /* 17 */
GG(d, a, b, c, x[6], 9, 0xc040b340); /* 18 */
GG(c, d, a, b, x[11], 14, 0x265e5a51); /* 19 */
GG(b, c, d, a, x[0], 20, 0xe9b6c7aa); /* 20 */
GG(a, b, c, d, x[5], 5, 0xd62f105d); /* 21 */
GG(d, a, b, c, x[10], 9, 0x2441453); /* 22 */
GG(c, d, a, b, x[15], 14, 0xd8a1e681); /* 23 */
GG(b, c, d, a, x[4], 20, 0xe7d3fbc8); /* 24 */
GG(a, b, c, d, x[9], 5, 0x21e1cde6); /* 25 */
GG(d, a, b, c, x[14], 9, 0xc33707d6); /* 26 */
GG(c, d, a, b, x[3], 14, 0xf4d50d87); /* 27 */
GG(b, c, d, a, x[8], 20, 0x455a14ed); /* 28 */
GG(a, b, c, d, x[13], 5, 0xa9e3e905); /* 29 */
GG(d, a, b, c, x[2], 9, 0xfcefa3f8); /* 30 */
GG(c, d, a, b, x[7], 14, 0x676f02d9); /* 31 */
GG(b, c, d, a, x[12], 20, 0x8d2a4c8a); /* 32 */
/* Round 3 */
HH(a, b, c, d, x[5], 4, 0xfffa3942); /* 33 */
HH(d, a, b, c, x[8], 11, 0x8771f681); /* 34 */
HH(c, d, a, b, x[11], 16, 0x6d9d6122); /* 35 */
HH(b, c, d, a, x[14], 23, 0xfde5380c); /* 36 */
HH(a, b, c, d, x[1], 4, 0xa4beea44); /* 37 */
HH(d, a, b, c, x[4], 11, 0x4bdecfa9); /* 38 */
HH(c, d, a, b, x[7], 16, 0xf6bb4b60); /* 39 */
HH(b, c, d, a, x[10], 23, 0xbebfbc70); /* 40 */
HH(a, b, c, d, x[13], 4, 0x289b7ec6); /* 41 */
HH(d, a, b, c, x[0], 11, 0xeaa127fa); /* 42 */
HH(c, d, a, b, x[3], 16, 0xd4ef3085); /* 43 */
HH(b, c, d, a, x[6], 23, 0x4881d05); /* 44 */
HH(a, b, c, d, x[9], 4, 0xd9d4d039); /* 45 */
HH(d, a, b, c, x[12], 11, 0xe6db99e5); /* 46 */
HH(c, d, a, b, x[15], 16, 0x1fa27cf8); /* 47 */
HH(b, c, d, a, x[2], 23, 0xc4ac5665); /* 48 */
/* Round 4 */
II(a, b, c, d, x[0], 6, 0xf4292244); /* 49 */
II(d, a, b, c, x[7], 10, 0x432aff97); /* 50 */
II(c, d, a, b, x[14], 15, 0xab9423a7); /* 51 */
II(b, c, d, a, x[5], 21, 0xfc93a039); /* 52 */
II(a, b, c, d, x[12], 6, 0x655b59c3); /* 53 */
II(d, a, b, c, x[3], 10, 0x8f0ccc92); /* 54 */
II(c, d, a, b, x[10], 15, 0xffeff47d); /* 55 */
II(b, c, d, a, x[1], 21, 0x85845dd1); /* 56 */
II(a, b, c, d, x[8], 6, 0x6fa87e4f); /* 57 */
II(d, a, b, c, x[15], 10, 0xfe2ce6e0); /* 58 */
II(c, d, a, b, x[6], 15, 0xa3014314); /* 59 */
II(b, c, d, a, x[13], 21, 0x4e0811a1); /* 60 */
II(a, b, c, d, x[4], 6, 0xf7537e82); /* 61 */
II(d, a, b, c, x[11], 10, 0xbd3af235); /* 62 */
II(c, d, a, b, x[2], 15, 0x2ad7d2bb); /* 63 */
II(b, c, d, a, x[9], 21, 0xeb86d391); /* 64 */
state[0] += a;
state[1] += b;
state[2] += c;
state[3] += d;
}
md5.h
#pragma once
#ifndef MD5_H
#define MD5_H
typedef struct
{
unsigned int count[2];
unsigned int state[4];
unsigned char buffer[64];
}MD5_CTX;
#define F(x,y,z) ((x & y) | (~x & z))
#define G(x,y,z) ((x & z) | (y & ~z))
#define H(x,y,z) (x^y^z)
#define I(x,y,z) (y ^ (x | ~z))
#define ROTATE_LEFT(x,n) ((x << n) | (x >> (32-n)))
#define FF(a,b,c,d,x,s,ac)
{
a += F(b,c,d) + x + ac;
a = ROTATE_LEFT(a,s);
a += b;
}
#define GG(a,b,c,d,x,s,ac)
{
a += G(b,c,d) + x + ac;
a = ROTATE_LEFT(a,s);
a += b;
}
#define HH(a,b,c,d,x,s,ac)
{
a += H(b,c,d) + x + ac;
a = ROTATE_LEFT(a,s);
a += b;
}
#define II(a,b,c,d,x,s,ac)
{
a += I(b,c,d) + x + ac;
a = ROTATE_LEFT(a,s);
a += b;
}
void MD5Init(MD5_CTX* context,_int32 a1[]);
void MD5Update(MD5_CTX* context, unsigned char* input, unsigned int inputlen);
void MD5Final(MD5_CTX* context, unsigned char digest[16]);
void MD5Transform(unsigned int state[4], unsigned char block[64]);
void MD5Encode(unsigned char* output, unsigned int* input, unsigned int len);
void MD5Decode(unsigned int* output, unsigned char* input, unsigned int len);
#endif
运行几分钟
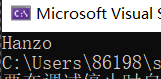
出现flag然后括上括号提交即可。
flag{Hanzo}
Crypto
rsa
源代码
from flag import text,flag
from Crypto.Util.number import *
import hashlib
assert hashlib.new('md5', text).hexdigest() == flag[5:-1]
text = m1 + m2 + m3
p1 = getPrime(512)
q1 = getPrime(512)
n1 = p1 * q1
phi = (p1-1) * (q1-1)
while True:
d1 = getRandomNBitInteger(200)
if GCD(d1, phi) == 1:
e1 = inverse(d1, phi)
break
m1 = bytes_to_long(m1)
c1 = pow(m1, e1, n1)
print (c1,e1,n1)
m2 = bytes_to_long(m2)
n2 = 0x57696c78e1d443a3c9211963c721c16e47068eb3b52dfb79ef55af340e7894c7e301a5f38734ddd10e67d0dd2f5759ae0443ca47719d82bfcccc9d26b05043b0b66b253219f266ea133fc613e23dbe14d5f731c5ad4158286a1139e2927b8a485df0e662d77277f61f4ff334a24b51959e399e5e778b6934897b6b9f4b315207L
n3 = 0xc7e5c4318b4376a93588ea853a70f5576aaa3a291acff806f87b00b01443edfd9298915343e8d219fc09ab464c02d12fa72abb0e70d40b12c63274bcf4a61ccb7c81d42fbb04f54e9ce972c3467c851932ecf8f0ada57f56ee91dad3837669fc501d69c68dce305d62cd1f09acff28874792ef343fca185bdc9d2432fd45d3d1L
n4 = 0x8d0899da21f7a50a5a869b0914fdfbc7d67aa85941021403889d24cb5b8029dd45a14e02f83dba7c21b3759fb152e045dcad6f11421e578a1b01d5e0b077810fc33e5f8d6d8e3623d278c908bbf7f4f7adb7224014e1f14272214e1a05cf4314dd950290fddbec9870be2c1d100bcdaf7056a1b909a400bb1f549efbede68bcfL
c2 = pow(m2, e2, n2)
c3 = pow(m2, e3, n3)
c4 = pow(m2, e4, n4)
print (c2,c3,c4)
m3 = bytes_to_long(m3)
p5 = getPrime(1024)
q5 = getPrime(1024)
n5 = p5 * q5
print pow(m3,e5,n5)
print (e5,n5)
print p5>>428
审计代码发现,和国赛一道题很像。可能是改编题。
分三步,
步骤一,e过大,维也纳攻击,直接分解出d。
步骤二,hastada攻击
步骤三,已知p高位攻击
sage脚本如下:
from Crypto.Util.number import bytes_to_long, long_to_bytes, inverse
c=51084654001062999676284508744761337160593155669881973332922269056143420517629679695048487021241292007953887627491190341353167847566083172502480747704275374070492531393399916651443961186981687573379323436438906676133035045064486529453649419053918833072924346775468502743027859482041178726542991466613589539914
d=1261275156996674929317726421604559358091356492791511348711829
n=151092363916177851152025151918241584641682210212036254637668925062407387596818893923128056380386244596150134405578253100187360613990057596729265767426618262474915825169178445560157476701330766996735046666440633251722785157310664928275249725806466188778983132016426476941426227570021630850606892034122220619913
m1=long_to_bytes(pow(c,d,n))
import binascii,gmpy2
n = [
0x57696c78e1d443a3c9211963c721c16e47068eb3b52dfb79ef55af340e7894c7e301a5f38734ddd10e67d0dd2f5759ae0443ca47719d82bfcccc9d26b05043b0b66b253219f266ea133fc613e23dbe14d5f731c5ad4158286a1139e2927b8a485df0e662d77277f61f4ff334a24b51959e399e5e778b6934897b6b9f4b315207
,0xc7e5c4318b4376a93588ea853a70f5576aaa3a291acff806f87b00b01443edfd9298915343e8d219fc09ab464c02d12fa72abb0e70d40b12c63274bcf4a61ccb7c81d42fbb04f54e9ce972c3467c851932ecf8f0ada57f56ee91dad3837669fc501d69c68dce305d62cd1f09acff28874792ef343fca185bdc9d2432fd45d3d1
,0x8d0899da21f7a50a5a869b0914fdfbc7d67aa85941021403889d24cb5b8029dd45a14e02f83dba7c21b3759fb152e045dcad6f11421e578a1b01d5e0b077810fc33e5f8d6d8e3623d278c908bbf7f4f7adb7224014e1f14272214e1a05cf4314dd950290fddbec9870be2c1d100bcdaf7056a1b909a400bb1f549efbede68bcf
]
c = [24168576475826731342981309869386844888048819155804916609868467364828794195081900378454942799582364951590154660883127133517306279315632213654294241046389472660162658285116025022019193389467425762033793233310853287285710051131156746537960416278314488047201950871542871471614834606092674080171837479678908485762,59042322068112449729750363498227925481549151238455994334741763136215058751527859574931116063334209500284095818008451340013716449554106507373112252757273078880364298445003064190906862585372984554264625861222115429779924444369582923270264732188891567089849725691839301479707767233813043465943547876632578498984,86124343357786577132154304914637897169467679024253471444678880447274558440276584635040507167438356800005540641456548793163113750596432451742228432593182300337042281015596655874375158300461112977200671847176880860698060672936210257455599090524023845268651175379694950602443080246153556268191330489901634436
]
print('
')
def CRT(mi, ai):
#assert(reduce(gmpy2.gcd,mi)==1)
#assert (isinstance(mi, list) and isinstance(ai, list))
M = reduce(lambda x, y: x * y, mi)
ai_ti_Mi = [a * (M // m) * inverse(M // m, m) for (m, a) in zip(mi, ai)]
return reduce(lambda x, y: x + y, ai_ti_Mi) % M
e=0x3
m=gmpy2.iroot(CRT(n, c), e)[0]
m2=binascii.unhexlify(hex(m)[2:].strip("L"))
print(m1+m2)
#sage
pbits = 1024
n=12382768780688845948585828171746451695620690637388724603203719934675129634162669400211587652801497553140445052212955447547285342951827548927777971592012005336108991182804517438932388430909818349339928033362693776498198280566445301283769762658236093273135470594245556180103947875110497679850836950853434075025187940546602828416710260312146348085635062790163306288554171471977697811571151068804586709977754482736587083043633360827556846476139372134496068081264161278183780518986923815627524813237434789592133132430580528353375704616450593022343415392743694469637309237497448893478902243349283615118435345397909237495251L
p4= 182635381484380563458311202271781328898053732908212705893542973352083240894286209775590202544476913342359034598901737742898345569752615514577169505593025259879429231797401548503324
#已知P的高位
e=65537
pbits=1024 #P原本的位数
kbits=pbits - p4.nbits()
print (p4.nbits())
p4 = p4 << kbits
PR.<x> = PolynomialRing(Zmod(n))
f = x + p4
roots = f.small_roots(X=2^kbits,beta=0.4)[0]
print(roots)
# 经过以上一些函数处理后,n和p已经被转化为10进制
p= p4 + (roots)
q=n//int(p)
c=7479226689503128706443123521570581658668839203982072419275773066090139369387752424856982287500754805036668221578674582111373214400048065981143586768159093517856729586240876781314226713473457848588205839635234624256432258024026698381646902196832849461804350553542541128509121012667792037004716033974053614737451942287543723238730054875983726091182977666880984732837604625557483621161056089767140997756267432137190239967241490004246596723655769407636914860893150081043179313259622038983431488143887092338693868571374510729082940832360819295528352729394196810748661957966996263811903630229686768254608968394381708296458
phi=(p-1)*(q-1)
d=inverse(e,phi)
m3=long_to_bytes(pow(c,d,n))
m=m1+m2+m3
import hashlib
flag='flag{'+hashlib.md5(m).hexdigest()+'}'
print(flag)
#flag{096d9ddd8c911b95d91fa7d6d7460c3c}
rekey
MT19937算法
import random
from Crypto.Cipher import AES
from Crypto.Util.number import long_to_bytes
# right shift inverse
def inverse_right(res, shift, bits=32):
tmp = res
for i in range(bits // shift):
tmp = res ^ tmp >> shift
return tmp
# right shift with mask inverse
def inverse_right_mask(res, shift, mask, bits=32):
tmp = res
for i in range(bits // shift):
tmp = res ^ tmp >> shift & mask
return tmp
# left shift inverse
def inverse_left(res, shift, bits=32):
tmp = res
for i in range(bits // shift):
tmp = res ^ tmp << shift
return tmp
# left shift with mask inverse
def inverse_left_mask(res, shift, mask, bits=32):
tmp = res
for i in range(bits // shift):
tmp = res ^ tmp << shift & mask
return tmp
def extract_number(y):
y = y ^ y >> 11
y = y ^ y << 7 & 2636928640
y = y ^ y << 15 & 4022730752
y = y ^ y >> 18
return y & 0xffffffff
def recover(y):
y = inverse_right(y, 18)
y = inverse_left_mask(y, 15, 4022730752)
y = inverse_left_mask(y, 7, 2636928640)
y = inverse_right(y, 11)
return y & 0xffffffff
f = open('output', 'r').read().strip().split(',')
r = [int(i) for i in f[:-1]]
c = long_to_bytes(int(f[-1], 16))
state = []
for _ in range(624):
state.append(recover(r[_]))
for i in range(624):
for j in range(i+1):
state[j] ^= i % 256
s = (3, tuple(state+[0]), None)
print(len(s[1]))
random.setstate(s)
key = long_to_bytes(random.getrandbits(128))
a = AES.new(key, AES.MODE_ECB)
print(a.decrypt(c))
#b'0000000000flag{5FSB8f5ZRwouow77tT09V4icpflf0AIg}'
info
010打开是PK文件头,改后缀为压缩包,解压出来然后进行得到一张图片。图片注释有一串密文,密钥在文件内容尾
尝试后发现是base64编码了密文,且加密是DES加密
from Crypto.Cipher import DES
key=b'iamakeys'
enc=base64.b64decode('TxnaVrv9nTiXlFaED3K34oYrCryk4sGK9/3oqaDZ/CRnzKxnA5JdgQ==')
de=DES.new(key,DES.MODE_ECB)
print(de.decrypt(enc))
#b'flag{ab096922210dfd2ca59025513f0eef1c}x00x00'