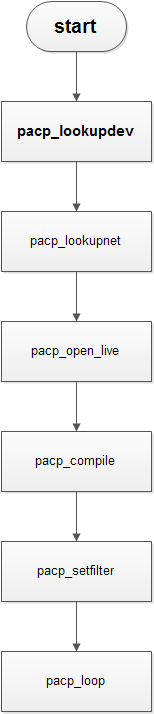
代码:
1: /*
2: * =====================================================================================
3: *
4: * Filename: cap.c
5: *
6: * Description:
7: *
8: * Version: 1.0
9: * Created: 03/15/2013 11:23:38 AM
10: * Revision: none
11: * Compiler: gcc
12: *
13: * Author: YOUR NAME (),
14: * Company:
15: *
16: * =====================================================================================
17: */
18:
19:
20: #include <pcap/pcap.h>
21:
22: #include <stdio.h>
23: #include <stdlib.h>
24:
25: #define N 256
26:
27: void handler(u_char *arg, const struct pcap_pkthdr *pkthdr, const u_char *packet)
28: {
29: int i = 0;
30: int *count = (int *)arg;
31:
32: printf("Packet Count: %d\n",++(*count));
33:
34: printf("Received package size :%d\n",pkthdr->len);
35:
36:
37: printf("Payload:\n");
38:
39: for(i = 0; i<pkthdr->len; i++)
40: {
41: printf("%02x ", (unsigned int)packet[i]);
42:
43: if((i%16 == 15 && i!=0) || (i == pkthdr->len - 1))
44: {
45: printf("\n");
46: }
47:
48:
49:
50: }
51: printf("\n\n****************************************\n");
52: return ;
53: }
54: int main(int argc, char *argv[])
55: {
56: char *device;
57: int count = 0;
58: char err_buffer[N];
59: bpf_u_int32 netp;
60: bpf_u_int32 maskp;
61: pcap_t *p;
62: struct bpf_program fp;
63: char str[40] = "host 192.168.1.173"; //过滤条件
64:
65: if(argc < 2) //获取或指定网络设备,如指定 "eth0"
66: {
67: device = pcap_lookupdev(err_buffer);
68: }
69: else
70: {
71: device = argv[1];
72: }
73:
74: printf("device : %s\n",device);
75:
76: if(pcap_lookupnet(device, &netp, &maskp, err_buffer) < 0) //获取设备的网络信息
77: {
78: printf("error! %s\n",err_buffer);
79: exit(-1);
80: }
81:
82: if((p = pcap_open_live(device, 2048, 1, 0, err_buffer)) == NULL) //打开网络设备device,返回用于捕获数据包的句柄
83: {
84: printf("error! %s\n",err_buffer);
85: exit(-1);
86: }
87:
88: if(pcap_compile(p, &fp, str, 1, maskp) < 0) //根据过滤条件生成过滤器
89: {
90: printf("fail to pcap_compile");
91: exit(-1);
92: }
93:
94:
95: if(pcap_setfilter(p, &fp) < 0) //安装生成的过滤器
96: {
97: printf("fail to pcap_next");
98: exit(-1);
99: }
100:
101: if(pcap_loop(p, 2, handler, (u_char *)&count) < 0) //循环捕获两帧数据
102: {
103: printf("fail to pcap_loop");
104: exit(-1);
105: }
106:
107:
108: return 0;
109: }
110:
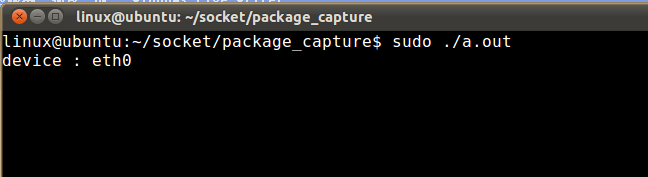
运行:
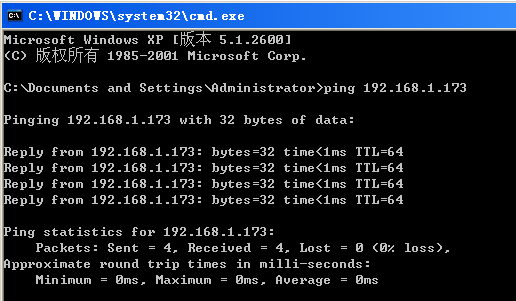
然后再windows下,或者再开一个窗口,ping 过滤条件中的ip地址。
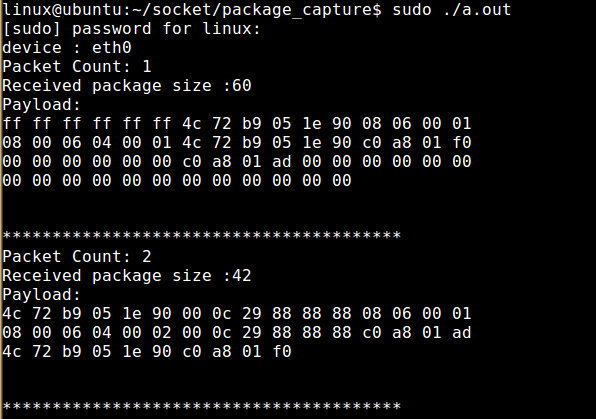
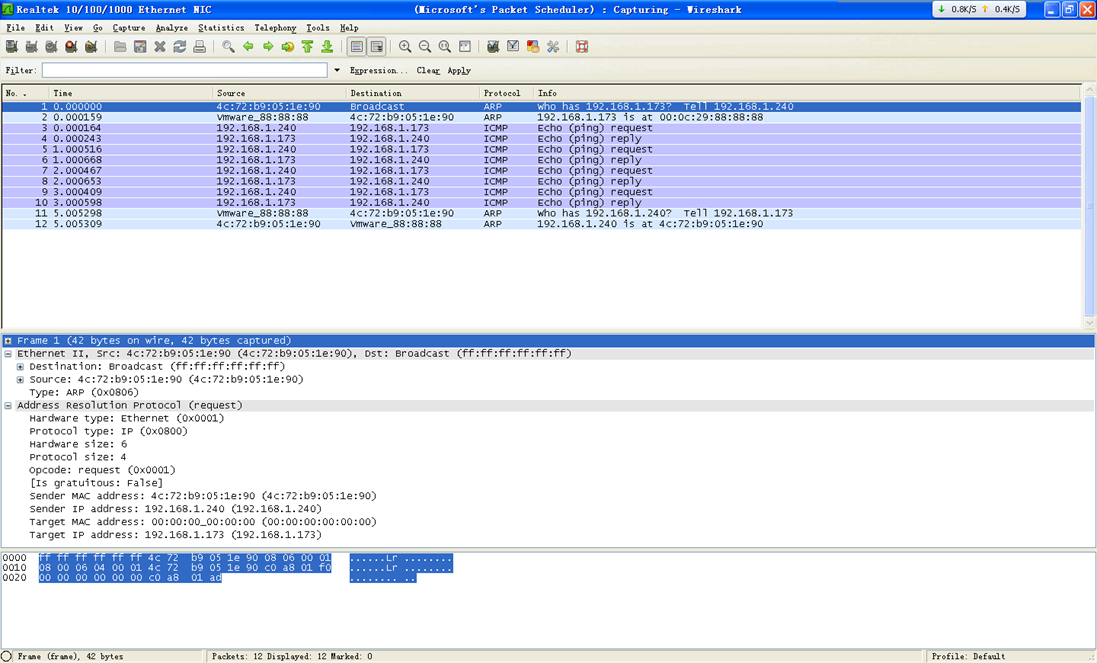
可以看到,已经捕获到两帧数据。
可以看到,捕获到的第一帧数据的目的MAC是 ff ff ff ff ff ff ,即是一个广播数据包的目的MAC,源MAC地址是4c 72 b9 05 1e 90,它是我的windows下面的网卡的物理MAC地址。协议类型为 0806,是一个ARP协议包,用于地址解析,是数据链路层的协议。收到的第二帧数据是虚拟机回复的消息。
下面是通过抓包工具wireshark的抓包结果: