R1模拟总部,R2 与R3模拟分部
如图配置
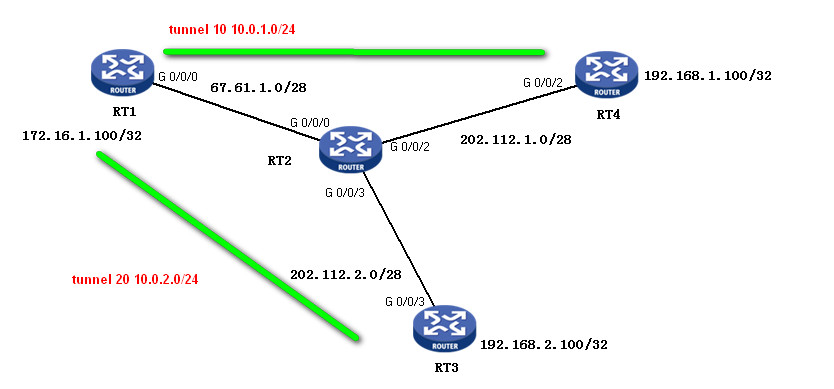
(1)网络中目前只有两站点, R1 和R2 。同时R2为动态获取IP地址一方,要求使用要求使用 GRE over IPSec VPN 野蛮模式,保证R1和R2 内网互通。
(2)由于公司规模的扩大,又有新的站点R3接入,同时R3为动态获取IP地址一方,使用相同的方式保证R1 和R3内网互通。
注意:这里要求总部尽量使用较少的命令完成以上配置(模板技术)
步骤:
1、 完成GRE隧道的配置
[RT1-Tunnel10]source 1.1.1.1
[RT1-Tunnel10]de 4.4.4.4
[RT1-Tunnel20]source 1.1.1.1
[RT1-Tunnel20]de 3.3.3.3
[RT4-Tunnel10]source 4.4.4.4
[RT4-Tunnel10]de 1.1.1.1
[RT3-Tunnel10]source 3.3.3.3
[RT3-Tunnel10]destination 1.1.1.1
2、 完成IKE Peer配置
[RT1-ike-peer-zb]exchange-mode aggressive
[RT1-ike-peer-zb]pre-shared-key simple cisco
[RT1-ike-peer-zb]id-type name
[RT1-ike-peer-zb]remote-name fb
[RT3-ike-peer-fb]exchange-mode aggressive
[RT3-ike-peer-fb]id-type name
[RT3-ike-peer-fb]remote-name fb
[RT3-ike-peer-fb]pre-shared-key simple cisco
[RT4-ike-peer-zb]exchange-mode aggressive
[RT4-ike-peer-zb]pre-shared-key simple cisco
[RT4-ike-peer-zb]remote-address 67.61.1.1
[RT4-ike-peer-zb]remote-name zb
[RT4-ike-peer-zb]id-type name
[RT3-ike-peer-zb]pre-shared-key simple cisco
[RT3-ike-peer-zb]exchange-mode aggressive
[RT3-ike-peer-zb]id-type name
[RT3-ike-peer-zb]remote-address 67.61.1.1
[RT3-ike-peer-zb]remote-name zb
3、 配置Ipsec policy模板和ipsec policy
[RT1-ipsec-policy-template-huawei-1]ike-peer zb
[RT1-ipsec-policy-template-huawei-1]proposal 1
[RT1]ipsec policy h3c 1 isakmp template Huawei
[RT1-GigabitEthernet0/0/0]ipsec policy h3c
[RT3-acl-adv-3000]rule permit ip source 3.3.3.3 0 de 1.1.1.1 0
[RT3-ipsec-policy-isakmp-h3c-1]security acl 3000
[RT3-ipsec-policy-isakmp-h3c-1]ike-peer zb
[RT3-ipsec-policy-isakmp-h3c-1]proposal 1
[RT3-GigabitEthernet0/0/3]ipsec policy h3c
[RT4-acl-adv-3000]rule permit ip source 4.4.4.4 0 de 1.1.1.1 0
[RT4-ipsec-policy-isakmp-h3c-1]security acl 3000
[RT4-ipsec-policy-isakmp-h3c-1]proposal 1
[RT4-GigabitEthernet0/0/3]ipsec policy h3c
4、 测试
192.168.1.100 ping 172.16.1.100
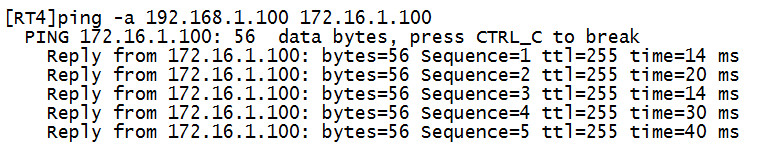
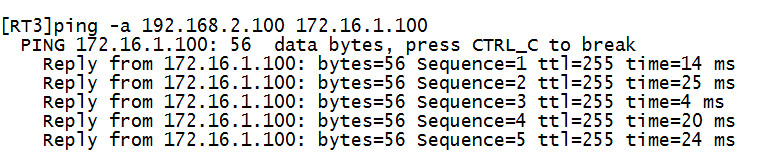
192.168.2.100 ping 172.16.1.100
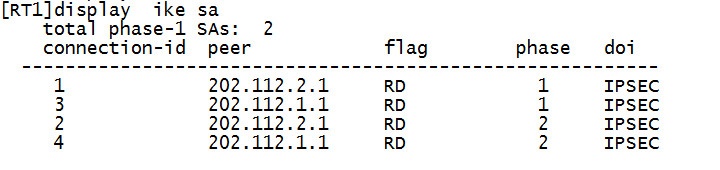
RT1查看Ike sa
更换RT3和RT4 地址后查看RT1上的IKE SA