1./etc/motd
操作:echo " Authorized users only. All activity may be monitored and reported " > /etc/motd
效果:telnet和ssh登录后的输出信息

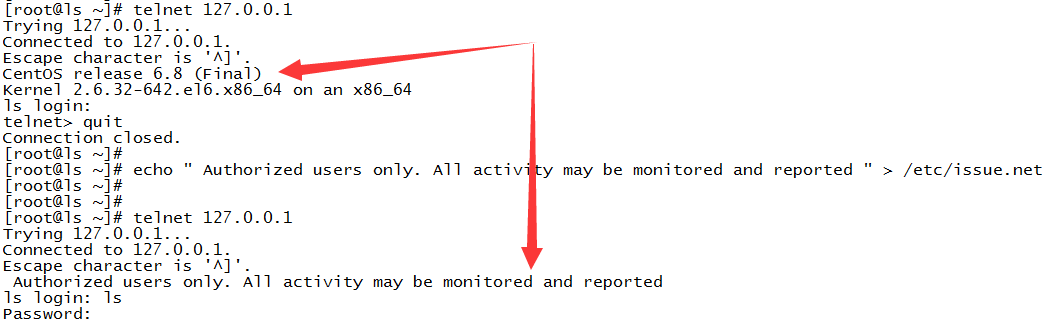
2. /etc/issue和/etc/issue.net
操作:echo " Authorized users only. All activity may be monitored and reported " > /etc/issue.net
效果:telnet主机未登录时输出的信息
3./etc/syslog.conf--远程日志服务配置文件
4./etc/sysctl.conf--操作系统配置文件
5./etc/vsftpd/vsftpd.conf--vsftpd配置文件
6./etc/ssh/sshd_config--ssh配置文件
7./etc/hosts.allow和/etc/hosts.deny--服务连接白名单/黑名单文件
8./etc/pam.d/system-auth--系统登录验证配置文件
9./etc/init/control-alt-delete.conf--ctrl+alt+del快捷键启用/禁用
10./etc/profile--环境变量配置文件,通常用于配置UMASK和TMOUT
11./etc/login.defs--口令(长度及有效时长等)配置文件
12.基线合规配置脚本(IP注意修改)

MDFDATE=`date +"%Y%m%d"` #add telnet and ssh banner cp -p /etc/motd /etc/motd.bak${MDFDATE} cp -p /etc/issue /etc/issue.bak${MDFDATE} cp -p /etc/issue.net /etc/issue.net.bak${MDFDATE} echo " Authorized users only. All activity may be monitored and reported " > /etc/motd echo " Authorized users only. All activity may be monitored and reported " > /etc/issue echo " Authorized users only. All activity may be monitored and reported " > /etc/issue.net #/etc/init.d/xinetd restart #set ftp default right cp -p /etc/vsftpd/vsftpd.conf /etc/vsftpd/vsftpd.conf.bak${MDFDATE} sed -i 's/#ls_recurse_enable=/ls_recurse_enable=/g' /etc/vsftpd/vsftpd.conf echo "anon_umask=022" >> /etc/vsftpd/vsftpd.conf #vsftpd sed -i '/^anonymous_enable=YES/d' /etc/vsftpd/vsftpd.conf echo 'anonymous_enable=NO' >> /etc/vsftpd/vsftpd.conf sed -i '/^chroot_local_user=/d' /etc/vsftpd/vsftpd.conf echo 'chroot_local_user=YES' >> /etc/vsftpd/vsftpd.conf sed -i '/^userlist_enable=/d' /etc/vsftpd/vsftpd.conf echo 'userlist_enable=YES' >> /etc/vsftpd/vsftpd.conf echo 'userlist_deny=NO' >> /etc/vsftpd/vsftpd.conf echo 'userlist_file=/etc/vsftpd/ftpuser_deny' >> /etc/vsftpd/vsftpd.conf cat> /etc/vsftpd/ftpuser_deny << EOF root daemon bin sys adm lp uucp nuucp listen nobody noaccess nobody4 EOF #close not need service chkconfig cups off #forbidden icmp redirect cp -p /etc/sysctl.conf /etc/sysctl.conf.bak${MDFDATE} echo "net.ipv4.conf.all.accept_redirects=0" >> /etc/sysctl.conf #sysctl -p #add remote log server cp /etc/syslog.conf /etc/syslog.conf.bak${MDFDATE} sed -i '/remote-host:514/a*.info @192.168.220.128' /etc/syslog.conf echo 'auht.info /var/log/authlog' >> /etc/syslog.conf echo 'authpriv.* /var/log/authlog' >> /etc/syslog.conf echo '*.err;auth.info /var/adm/messages' >> /etc/syslog.conf touch /var/log/authlog for f in `cat /etc/rsyslog.conf|grep -v "@"|grep -v "^#" |grep -v "^$"|grep "/var" |grep -v "-/"|awk "{print$2}"` do chmod 640 $f done #forbid root romote login cp -p /etc/ssh/sshd_config /etc/ssh/sshd_config.bak${MDFDATE} sed -i 's/^PermitRootLogin yes/#PermitRootLogin yes/g' /etc/ssh/sshd_config sed -i '/PermitRootLogin yes/aPermitRootLogin no' /etc/ssh/sshd_config #/etc/init.d/sshd restart sed -i 's/^pts/#pts/g' /etc/securetty #ssh banner touch /etc/sshbanner chown bin:bin /etc/sshbanner chmod 644 /etc/sshbanner echo " Authorized users only. All activity may be monitored and reported " > /etc/sshbanner echo "Banner /etc/sshbanner" >> /etc/ssh/sshd_config service sshd restart #limit ip to login echo 'sshd:all:deny' >> /etc/hosts.deny echo 'sshd:192.168.220.129:allow' >> /etc/hosts.allow echo 'sshd:192.168.220.:allow' >> /etc/hosts.allow #add password limit #password remember #add auth clock cp -p /etc/pam.d/system-auth /etc/pam.d/system-auth.bak${MDFDATE} echo "" >> /etc/pam.d/system-auth echo "password requisite pam_cracklib.so dcredit=-1 lcredit=-1 ocredit=-1 minclass=2 minlen=8" >> /etc/pam.d/system-auth echo "password sufficient pam_unix.so remember=5 md5 shadow nullok try_first_pass use_authtok" >> /etc/pam.d/system-auth echo "auth required pam_tally2.so deny=6 onerr=fail no_magic_root unlock_time=120" >> /etc/pam.d/system-auth #forbid ctrl+alt+del cp -p /etc/inittab /etc/inittab.bak${MDFDATE} sed -i '/ctrlaltdel/d' /etc/inittab cp /etc/init/control-alt-delete.conf /etc/init/control-alt-delete.conf.bak${MDFDATE} sed -i 's/^start/#start/g' /etc/init/control-alt-delete.conf sed -i 's/^exec/#exec/g' /etc/init/control-alt-delete.conf #umask cp -p /etc/profile /etc/profile.bak${MDFDATE} sed -i 's/umask 022/umask 027/g' /etc/profile echo 'umask 027' >> /etc/profile sed -i '/^TMOUT.*/d' /etc/profile echo "export TMOUT=540" >>/etc/profile cp -p /etc/csh.cshrc /etc/csh.cshrc.bak${MDFDATE} echo 'set autologout = 540' >> /etc/csh.cshrc #password file chmod u+rw /etc/shadow cp /etc/shadow /etc/shadow.bak${MDFDATE} sed -i 's/^lp:/lp:!!/g' /etc/shadow sed -i 's/^nobody:/nobody:!!/g' /etc/shadow sed -i 's/^uucp:/uucp:!!/g' /etc/shadow sed -i 's/^games:/games:!!/g' /etc/shadow sed -i 's/^rpm:/rpm:!!/g' /etc/shadow sed -i 's/^smmsp:/smmsp:!!/g' /etc/shadow sed -i 's/^nfsnobody:/nfsnobody:!!/g' /etc/shadow chmod 0644 /etc/passwd chmod 0400 /etc/shadow chmod 0644 /etc/group cp /etc/login.defs /etc/login.defs.bak${MDFDATE} sed -i 's/PASS_MIN_LEN.*5*/PASS_MIN_LEN 8/g' /etc/login.defs sed -i 's/PASS_MAX_DAYS.*99999/PASS_MAX_DAYS 90/g' /etc/login.defs #application user #useradd -U forchk
