1. 配置基于 SSH 密钥的身份验证
用户可通过使用公钥身份验证进行ssh登录身份验证。ssh允许用户使用私钥-公钥方案进行身份验证。这意味着将生成私钥和公钥这两个密钥。私钥文件用作身份验证凭据,像密码一样,必须妥善保管。公钥复制到用户希望登录的系统,用于验证私钥。公钥并不需要保密。拥有公钥的ssh服务器可以发布仅持有您私钥的系统才可解答的问题。因此,可以根据所持有的密钥进行验证。如此一来,就不必在每次访问系统时键入密码,但安全性仍能得到保证。
使用ssh-keygen命令生成密码。将会生成私钥/.ssh/id_rsa和公钥/.ssh/id_rsa.pub。
注意:
生成密钥时,系统将提供指定密码的选项,在访问私钥时必须提供该密码。如果私钥被偷,除颁发者之外的其他任何人很难使用该私钥,因为已使用密码对其进行保护。这样,在攻击者破解并使用私钥前,会有足够的时间生成新的密钥对并删除所有涉及旧密钥的内容。
生成ssh密钥后,密钥将默认存储在家目录下的.ssh/目录中。私钥和公钥的权限就分别为600和644。.ssh目录权限必须是700。
在可以使用基于密钥的身份验证前,需要将公钥复制到目标系统上。可以使用ssh-copy-id完成这一操作
//使用 ssh-keygen 创建公钥-私钥对
[root@liping ~]# ssh-keygen -t rsa
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa):
Created directory '/root/.ssh'.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /root/.ssh/id_rsa.
Your public key has been saved in /root/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:diMSSq7vXv6wkyHC44YoAbajDtRgwh9AnSoywDARYgM root@liping
The key's randomart image is:
+---[RSA 2048]----+
|EB. . |
|=ooo |
|o+... . |
|Bo+o.. . |
|=+.oo . S o |
|oo+.. .o o . |
|++oo .oo |
|* o. ooo |
|oo o+ oo. |
+----[SHA256]-----+
//使用 ssh-copy-id 将公钥复制到远程系统上的正确位置
[root@liping ~]# ls .ssh/
id_rsa id_rsa.pub
[root@liping ~]# ssh-copy-id root@192.168.136.128
/usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "/root/.ssh/id_rsa.pub"
The authenticity of host '192.168.136.128 (192.168.136.128)' can't be established.
ECDSA key fingerprint is SHA256:uN0Vd9u/GGh1TgTNrXBRphj1OpHmNrDfRpU0H0l14tQ.
ECDSA key fingerprint is MD5:07:4c:6d:0a:1b:ac:d0:c0:d1:b2:95:e3:a8:a3:65:e6.
Are you sure you want to continue connecting (yes/no)? yes
/usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed
/usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys
root@192.168.136.128's password:
Number of key(s) added: 1
Now try logging into the machine, with: "ssh 'root@192.168.136.128'"
and check to make sure that only the key(s) you wanted were added.
//使用 ssh 命令无命令登录远程主机
[root@liping ~]# ssh root@192.168.136.128
Last login: Tue Oct 22 14:10:35 2019 from 192.168.136.1
[root@liping ~]# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:26:a4:52 brd ff:ff:ff:ff:ff:ff
inet 192.168.136.128/24 brd 192.168.136.255 scope global dynamic eth0
valid_lft 1704sec preferred_lft 1704sec
inet6 fe80::24c7:7536:259a:b17c/64 scope link
valid_lft forever preferred_lft forever
3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:26:a4:5c brd ff:ff:ff:ff:ff:ff
4: eth2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:26:a4:66 brd ff:ff:ff:ff:ff:ff
//使用 scp 命令登录远程主机
[root@liping .ssh]# ls
authorized_keys known_hosts
[root@liping .ssh]# ssh-keygen -t rsa
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /root/.ssh/id_rsa.
Your public key has been saved in /root/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:e4oTz7xNDyIUaxq9O3wWSLUWXzbpl+DtSqnQklJHP5g root@liping
The key's randomart image is:
+---[RSA 2048]----+
| . |
| o . * |
| .. = O + . |
| ..o+ E = + |
| ..=+S+ = |
| =+.=.. o . |
| ..o*o++o . |
| ++**.o. |
| o=o.. . |
+----[SHA256]-----+
[root@liping .ssh]# ls
authorized_keys id_rsa id_rsa.pub known_hosts
[root@liping .ssh]#
[root@liping .ssh]# scp ~/.ssh/id_rsa.pub root@192.168.136.129:~/.ssh/authorized_keys
root@192.168.136.129's password:
id_rsa.pub 100% 393 500.4KB/s 00:00
验证:
[root@liping .ssh]# ssh root@192.168.136.129
Last login: Tue Oct 22 14:10:31 2019 from 192.168.136.1
[root@liping ~]# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:00:52:6e brd ff:ff:ff:ff:ff:ff
inet 192.168.136.129/24 brd 192.168.136.255 scope global dynamic ens33
valid_lft 1674sec preferred_lft 1674sec
inet6 fe80::cb81:16ba:de26:872d/64 scope link
valid_lft forever preferred_lft forever
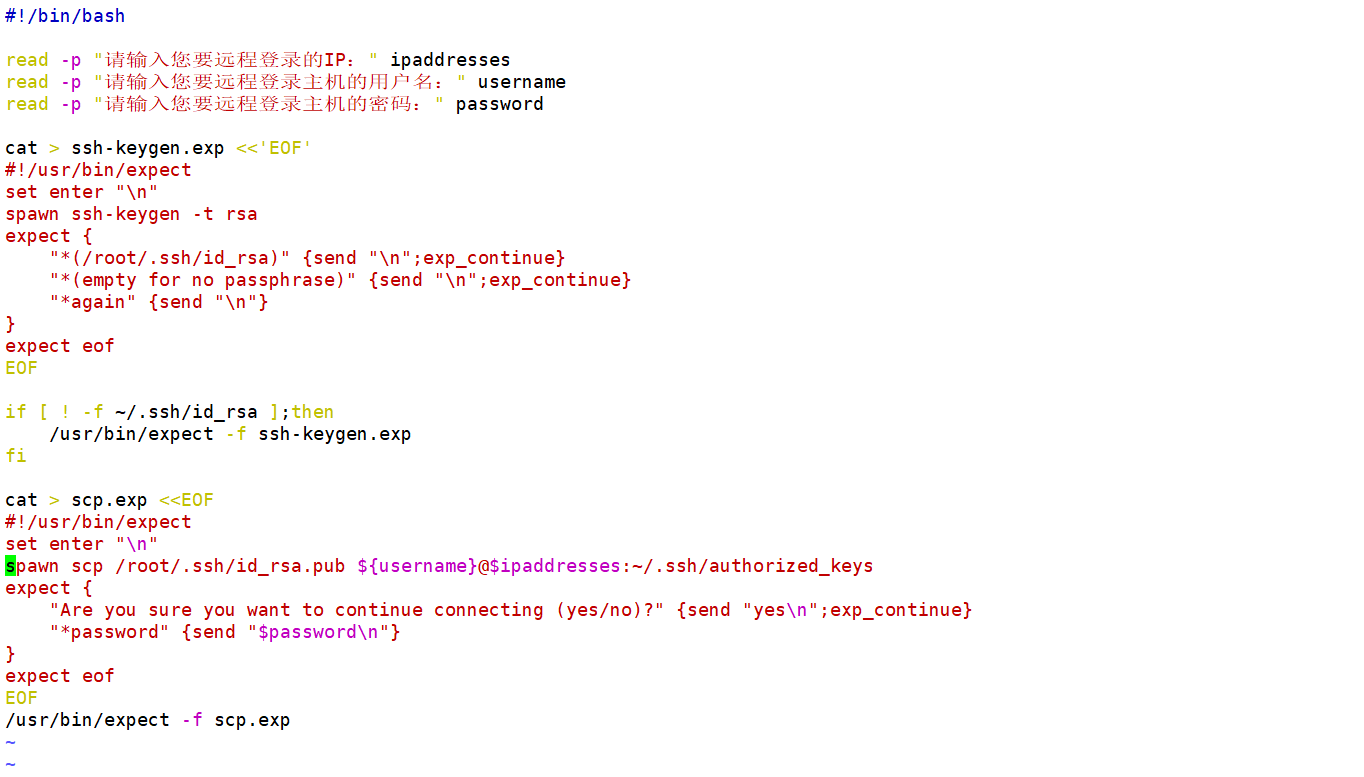
2.两种方法登录的脚本
2.1官方步骤

2.2第三方步骤