更多,更好内容请参见: http://www.ibm.com/developerworks/cn/aix/library/au-tcpwrapper/
一. 用处和用法
没有符合hosts.allow,hosts.deny中的配置的主机,用ssh登陆到我的系统的时候,我希望记录下他的动作,以便用于查询认证只用,这个时候就可以用到TCP Wrappers 的特殊功能。 但是要确定安装tcp_wrappers软件才能使用: " yum install tcp_wrappers"。 这时,就会有更加详细的操作:
spawn : 可以利用后续的shell进行额外的工作,并且可以使用变量:
%h: hostname
%a: address
%d: daemon
twist: 立刻一后续的命令进行,且执行完后终止此次连接
二. 简单范例
1. spawn的使用:
1.1 设置hosts.allow,hosts.deny. 加入相应的spawn配置。
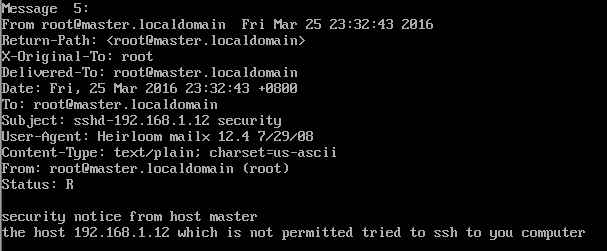
达到的目标: 如果是未经允许的网段登录到我的主机时,就向root账户发送一条mail,mail的内容形式为:
security notice from host ****
the host **** which is not permitted tried to ssh to you computer
hosts.allow
# # hosts.allow This file contains access rules which are used to # allow or deny connections to network services that # either use the tcp_wrappers library or that have been # started through a tcp_wrappers-enabled xinetd. # # See 'man 5 hosts_options' and 'man 5 hosts_access' # for information on rule syntax. # See 'man tcpd' for information on tcp_wrappers # sshd: 192.168.1.2,192.168.1.1: allow
hosts.deny
# # hosts.deny This file contains access rules which are used to # deny connections to network services that either use # the tcp_wrappers library or that have been # started through a tcp_wrappers-enabled xinetd. # # The rules in this file can also be set up in # /etc/hosts.allow with a 'deny' option instead. # # See 'man 5 hosts_options' and 'man 5 hosts_access' # for information on rule syntax. # See 'man tcpd' for information on tcp_wrappers # sshd: ALL :spawn ( echo "security notice from host $(/bin/hostname)";
echo "the host %h which is not permitted tried to ssh to you computer"; echo;) | /bin/mail -s "%d-%h security" root
1.2 用不在允许范围的主机192.168.1.12尝试用ssh登陆到这台主机(192.168.1.11)
主机拒绝登陆

1.3 在主机(192.168.1.11)查看收到的新mai,内容如下:
 l
l
2.twist用法
在hosts.deny文件后边加上设置:
# # hosts.deny This file contains access rules which are used to # deny connections to network services that either use # the tcp_wrappers library or that have been # started through a tcp_wrappers-enabled xinetd. # # The rules in this file can also be set up in # /etc/hosts.allow with a 'deny' option instead. # # See 'man 5 hosts_options' and 'man 5 hosts_access' # for information on rule syntax. # See 'man tcpd' for information on tcp_wrappers # sshd: ALL :spawn ( echo "security notice from host $(/bin/hostname)";
echo "the host %h which is not permitted tried to ssh to you computer"; echo;) | /bin/mail -s "%d-%h security" root & :twist (/bin/echo "YOU ARE NOT ALLOWED TO ENTER THE COMPUTER")
在192.168.1.12上用ssh登陆到192.168.1.11上时,并没有出现YOU ARE NOT ALLOWED TO ENTER THE COMPUTER。 查找了很长时间的问题,但是依然没有解决。
这样 sshd: ALL :twist (/bin/echo "YOU ARE NOT ALLOWED TO ENTER THE COMPUTER"),也不行。
求高手解答