Overview
https://docs.docker.com/network/
docker强大之处在于实现资源隔离的同时,也可是构建容器连接,容器和容器(同主机),容器和容器(不同主机),或者容器和外部,
One of the reasons Docker containers and services are so powerful is that you can connect them together, or connect them to non-Docker workloads. Docker containers and services do not even need to be aware that they are deployed on Docker, or whether their peers are also Docker workloads or not. Whether your Docker hosts run Linux, Windows, or a mix of the two, you can use Docker to manage them in a platform-agnostic way.
This topic defines some basic Docker networking concepts and prepares you to design and deploy your applications to take full advantage of these capabilities.
三种模式:
网桥 -- 相同的docker deamon(主机)上,不同的容器之间通信。 默认模式。
主机 -- 共享主机网络资源。
overlay -- 构建虚拟网域,在不同主机上, 部署统一业务的不同组件。
bridge: The default network driver. If you don’t specify a driver, this is the type of network you are creating. Bridge networks are usually used when your applications run in standalone containers that need to communicate. See bridge networks.
host: For standalone containers, remove network isolation between the container and the Docker host, and use the host’s networking directly. See use the host network.
overlay: Overlay networks connect multiple Docker daemons together and enable swarm services to communicate with each other. You can also use overlay networks to facilitate communication between a swarm service and a standalone container, or between two standalone containers on different Docker daemons. This strategy removes the need to do OS-level routing between these containers. See overlay networks.
bridge
https://docs.docker.com/network/bridge/
In terms of Docker, a bridge network uses a software bridge which allows containers connected to the same bridge network to communicate, while providing isolation from containers which are not connected to that bridge network. The Docker bridge driver automatically installs rules in the host machine so that containers on different bridge networks cannot communicate directly with each other.
docker network create my-net
docker create --name my-nginx \ --network my-net \ --publish 8080:80 \ nginx:latest
docker network connect my-net my-nginxoverlay
https://docs.docker.com/network/overlay/
The
overlaynetwork driver creates a distributed network among multiple Docker daemon hosts. This network sits on top of (overlays) the host-specific networks, allowing containers connected to it (including swarm service containers) to communicate securely when encryption is enabled. Docker transparently handles routing of each packet to and from the correct Docker daemon host and the correct destination container.
host
https://docs.docker.com/network/host/
If you use the
hostnetwork mode for a container, that container’s network stack is not isolated from the Docker host (the container shares the host’s networking namespace), and the container does not get its own IP-address allocated. For instance, if you run a container which binds to port 80 and you usehostnetworking, the container’s application is available on port 80 on the host’s IP address.
Command
https://docs.docker.com/engine/reference/commandline/network/
docker network connect Connect a container to a network docker network create Create a network docker network disconnect Disconnect a container from a network docker network inspect Display detailed information on one or more networks docker network ls List networks docker network prune Remove all unused networks docker network rm Remove one or more networks
Good Tutorial
https://www.cnblogs.com/qsing/p/15125319.html
https://docker-k8s-lab.readthedocs.io/en/latest/docker/port-mapping.html
Bridge and Host Diff
https://www.tutorialspoint.com/docker-host-network-vs-bridge-network#:~:text=In%20case%20of%20a%20host%20network%2C%20a%20particular,nginx%20container%20with%20the%20help%20of%20host%20networking.
host 模式 容器共享主机的 网络资源 (IP + PORT)
bridge模式 容器拥有独立的网络资源(桥IP + 容器本身PORT),如果需要外部访问容器端口,需要做端口映射。
There are two types of single−host networks available for Docker Networking - “host” and “bridge” networks. Single−host networks mean that their effect is local to each individual host.
In case of a host network, a particular Docker Container can directly use the Networking of the host for sending and receiving the packets. In the case of a bridge network, it requires port mapping to communicate.
docker网桥原理
https://www.cnblogs.com/Hai--D/p/7017933.html
docker0
一.Docker容器的网络基础
通过ifconfig查看docker0的网络设备,docker守护进程就是通过docker0为docker的容器提供网络连接的各种服务。docker0是Linux虚拟网桥。Linux虚拟网桥的特点:
- 可以设置IP地址
- 相当于拥有一个隐藏的虚拟网卡
docker0的地址划分:
- IP:172.17.42.1 子网掩码: 255.255.0.0
- MAC: 02:42:ac:11:00:00 到 02:42:ac:11:ff:ff
- 总共提供65534个地址
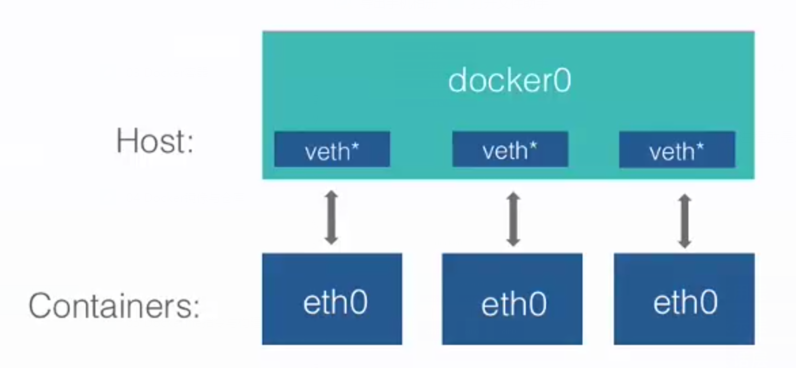
docker守护进程在一个容器启动时,实际上它要创建网络连接的两端。一端是在容器中的网络设备,而另一端是在运行docker守护进程的主机上打开一个名为veth*的一个接口,用来实现docker这个网桥与容器的网络通信。
https://www.cnblogs.com/qsing/p/15125319.html
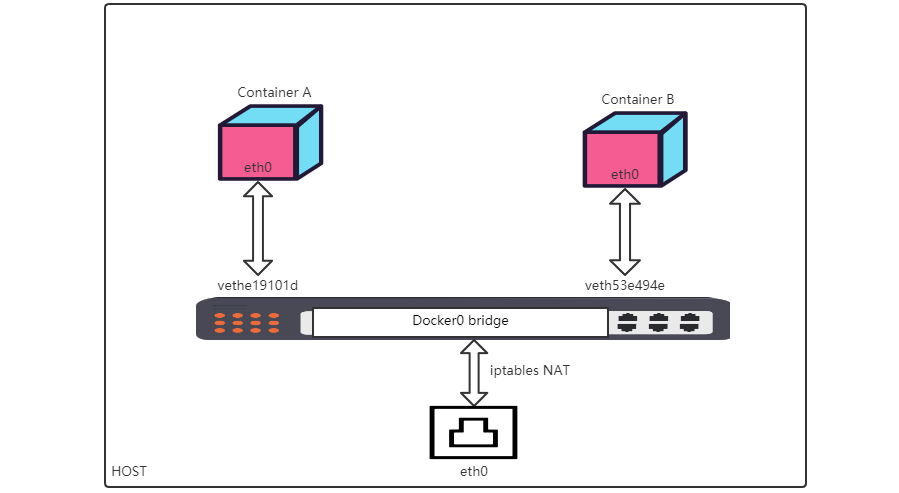
我们从下面这张图展开bridge网络工作原理
我们安装Docker后守护进程将创建一个linux虚拟以太网桥docker0,它会在连接到其上的所有接口之间转发数据包,默认情况下主机上的所有容器都连接到这个内部桥接器,它会将一个接口(虚拟设备对veth pair)作为容器的eth0接口和主机命名空间中的另一个接口。这样容器就获得了私有 IP 地址分配。同时为了防止本地网络上的 ARP 冲突,Docker 守护进程从分配的 IP 地址上生成一个随机 MAC 地址。这样一来容器就和网桥连接起来了,然后通过iptables NAT规则和主机上eth0网卡交换数据。
veth pair我们可以理解为一条虚拟网络电缆,其两端都有一个虚拟网络接口设备。
None模式
https://docs.docker.com/network/none/
不建立与docker0的联系,容器外不能访问容器内,容器内不能访问容器外。
If you want to completely disable the networking stack on a container, you can use the
--network noneflag when starting the container. Within the container, only the loopback device is created. The following example illustrates this.docker run --rm -dit \ --network none \ --name no-net-alpine \ alpine:latest \ ash
LINK -- CONTERPART BEFORE NETWORK
在网络功能出现之前, LINK功能就是实现容器通信的主要方法。
https://www.educba.com/docker-container-linking/?source=leftnav
Docker container linking is used to link multiple containers to each other and share connection information. Data or information of a source container can be shared with a recipient container when containers are linked which means the recipient container can see selected information of the source container. It is a legacy feature of Docker and it may be removed in future versions. It was the main way of communication between containers before introducing the Docker Networking feature by Docker in Docker version 1.9. However, it is good to know about container linking as there might be some legacy code running using it.
volume
https://blog.container-solutions.com/understanding-volumes-docker
Sharing Data
To give another container access to a container's volumes, we can provide the --volumes-from argument to docker run. For example:
This works whether container-test is running or not. A volume will never be deleted as long as a container is linked to it. We could also have mounted the volume by giving its name to the -v flag i.e:
Note that using this syntax allows us to mount the volume to a different directory inside the container.