老样子,把新下的拖到ida中
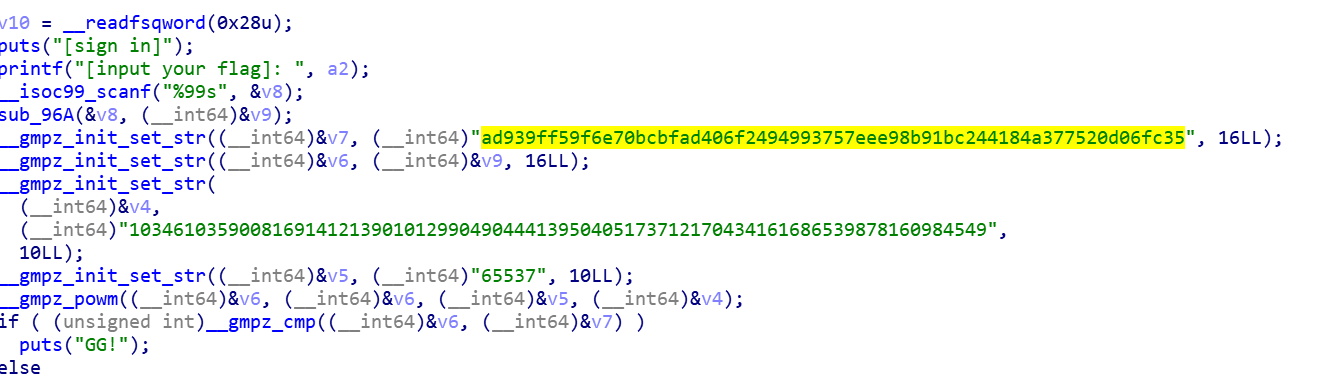
有个65537,是个常见的e的取值,n肯定就是10的那一串,进行爆破,解出来p和q
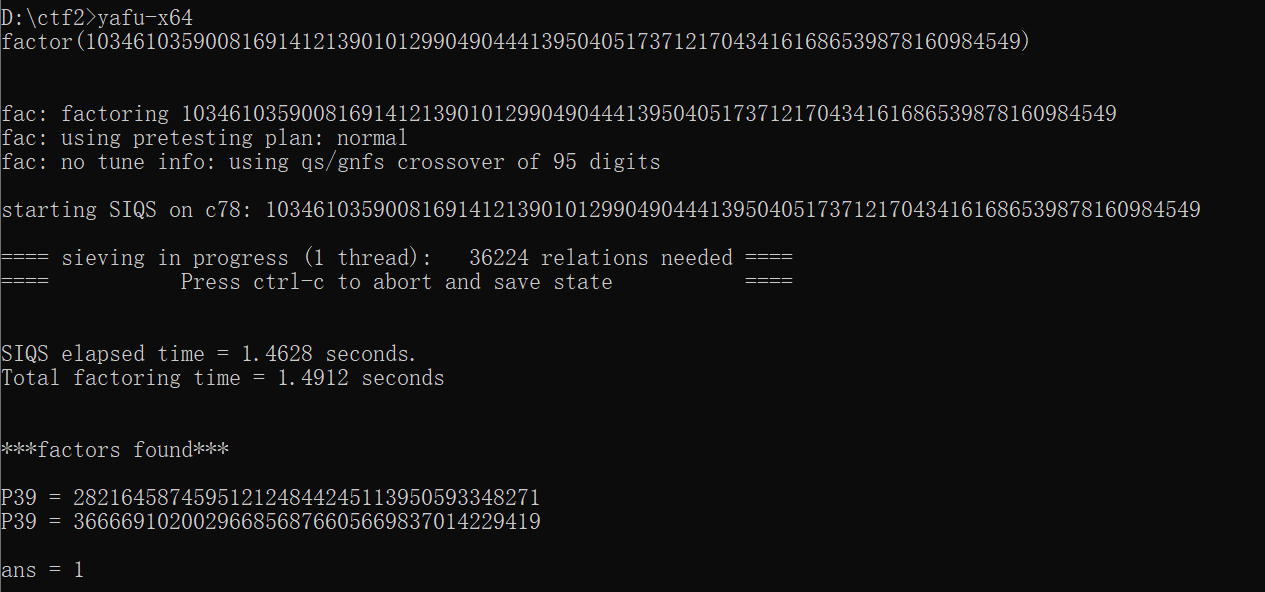
P39 = 282164587459512124844245113950593348271
P39 = 366669102002966856876605669837014229419
然后那一串16进制的字母,解一下密应该就是我们所求的flag,由于数字都比较大,要用gmpy2这个库(之前试过不带库的失败了)
import gmpy2
p = gmpy2.mpz(282164587459512124844245113950593348271)
q = gmpy2.mpz(366669102002966856876605669837014229419)
e = gmpy2.mpz(65537)
phi_n = (p - 1) * (q - 1)
d = gmpy2.invert(e, phi_n)
print ("private key:")
print (d)
c = gmpy2.mpz(78510953323073667749065685964447569045476327122134491251061064910992472210485)
print ("plaintext:")
print (pow(c,d,p*q))
#73756374667b50776e5f405f68756e647265645f79656172737d
在网上找脚本,爆破一下d,再顺便解密,解出来
185534734614696481020381637136165435809958101675798337848243069
是个十进制,先转16进制,再转字符串,就应该是flag
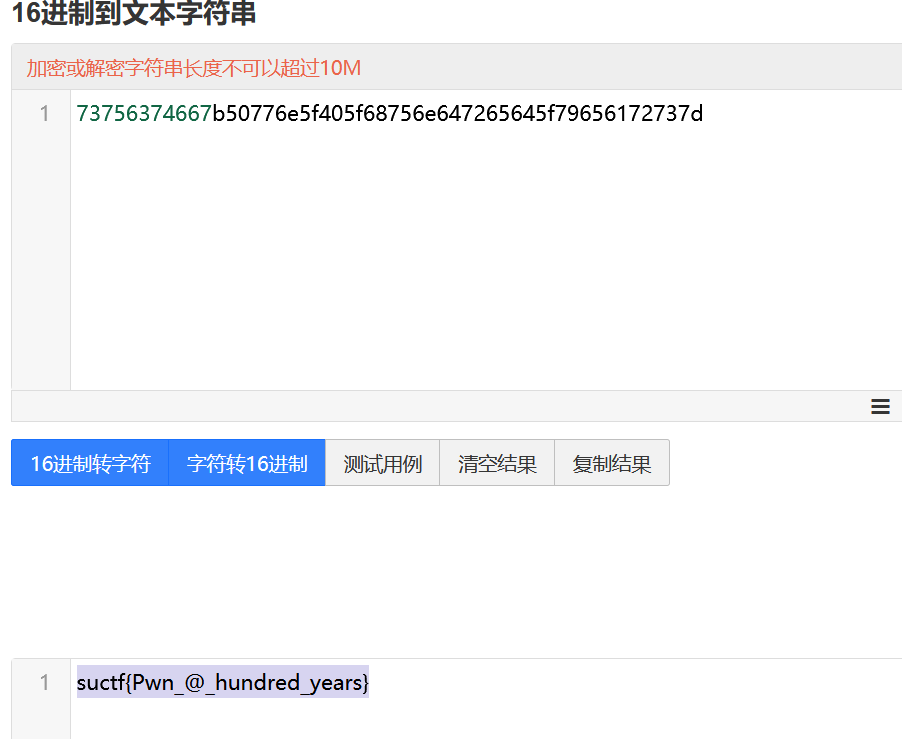
由于本人水平有限,只会线上解码