Local Host Vulnerabilities
CVE(Common Vulnerabilities and Exposures) Database
https://www.cvedetails.com/vendor.php
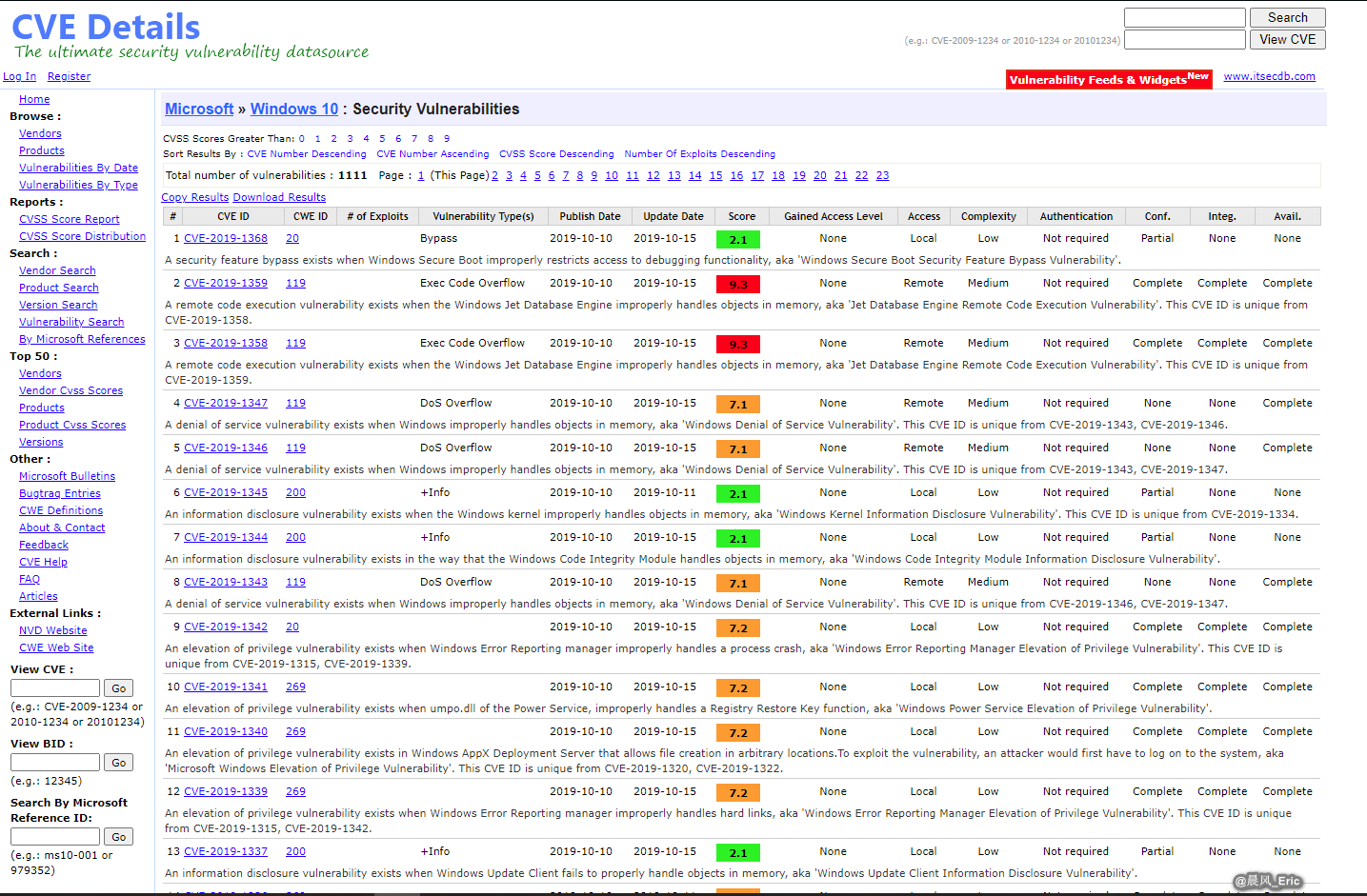
Windows 10
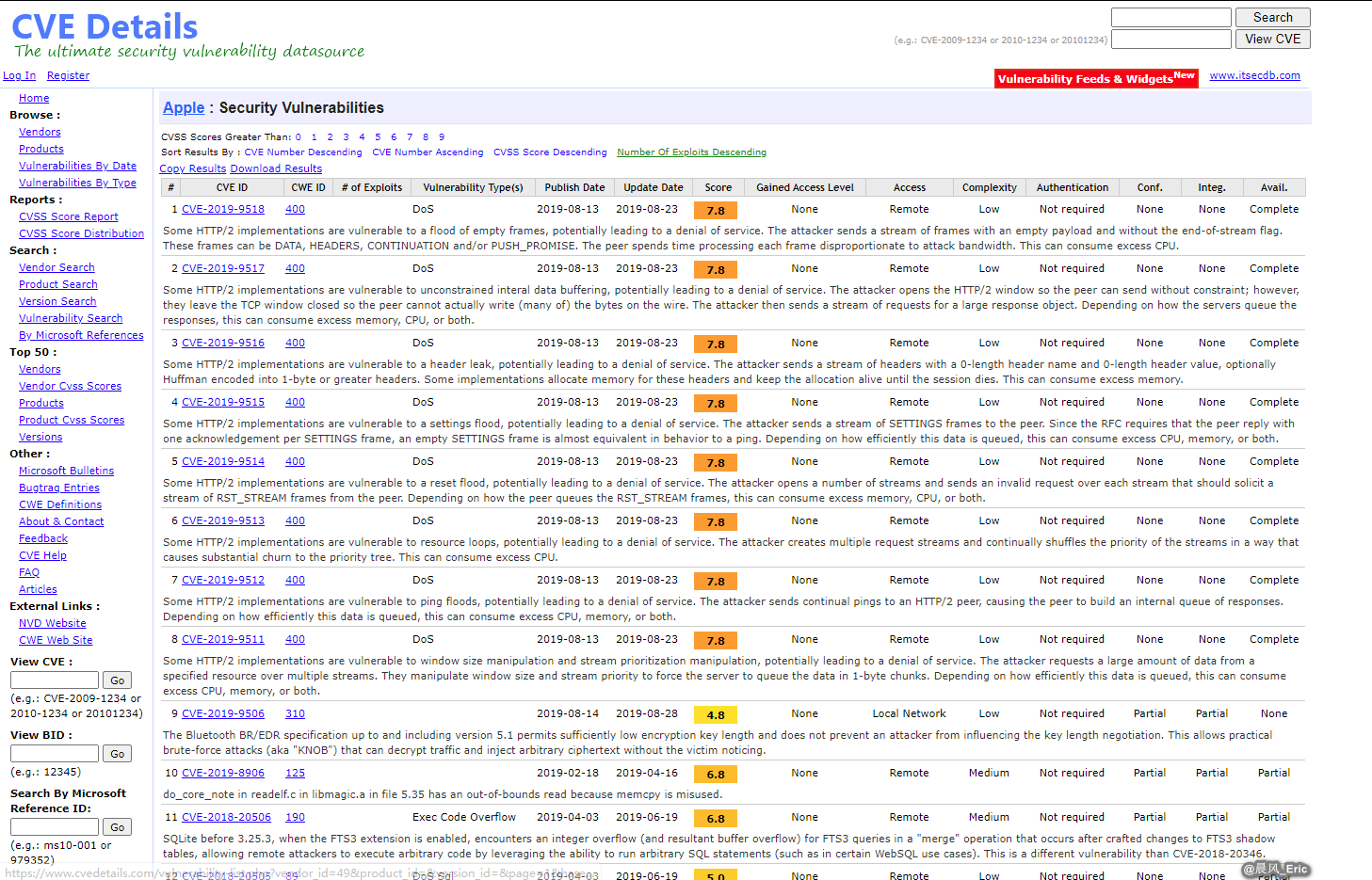
Apple
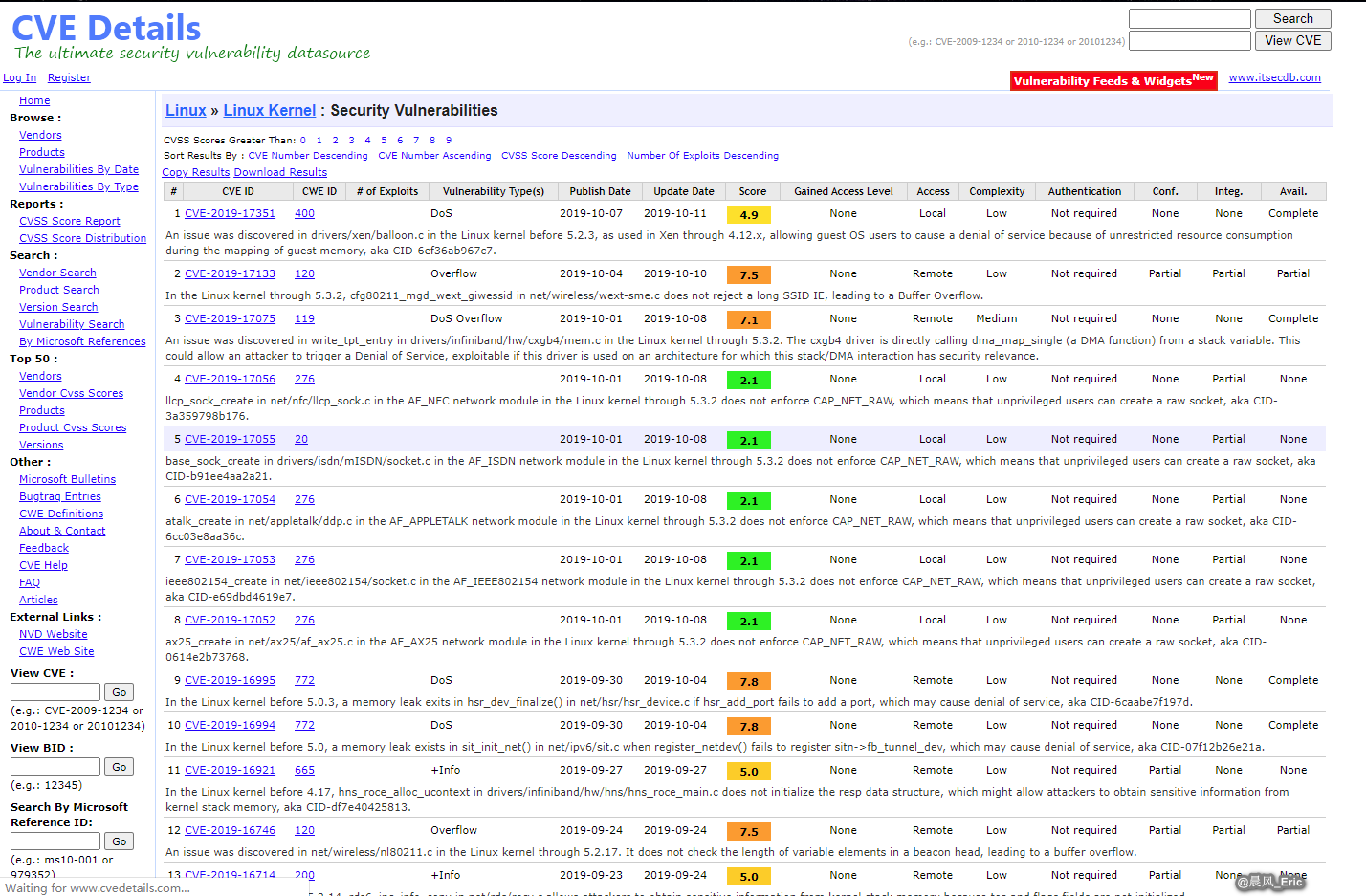
Linux Kernel
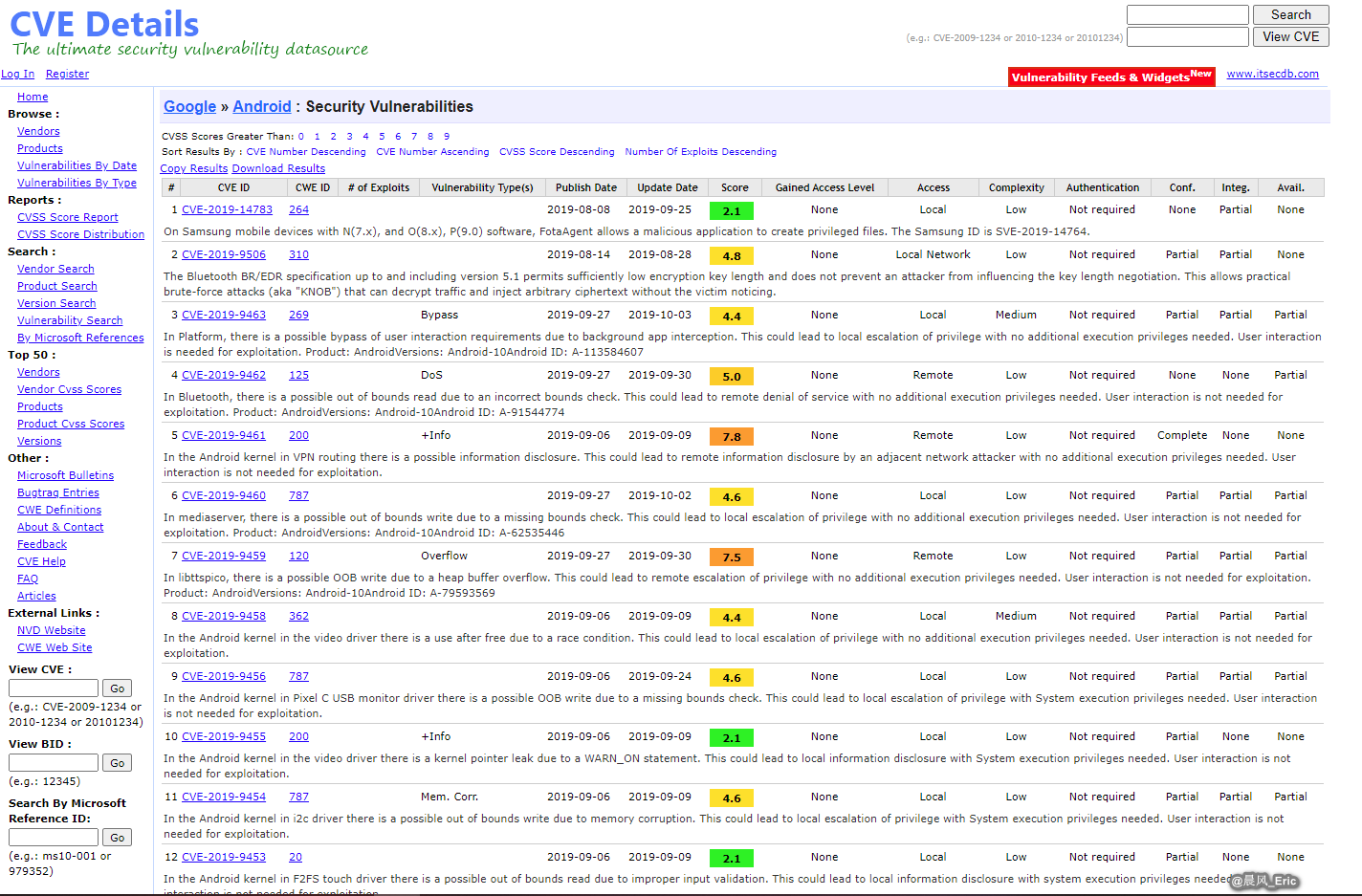
Android
QUICK REVIEW
- Every operating system has its own specific vulnerabilities
- Online vulnerability repositories make it easy to determine which vulnerabilities apply to a specific target.