Interacting with Metasploit
Early-stage Preparation:
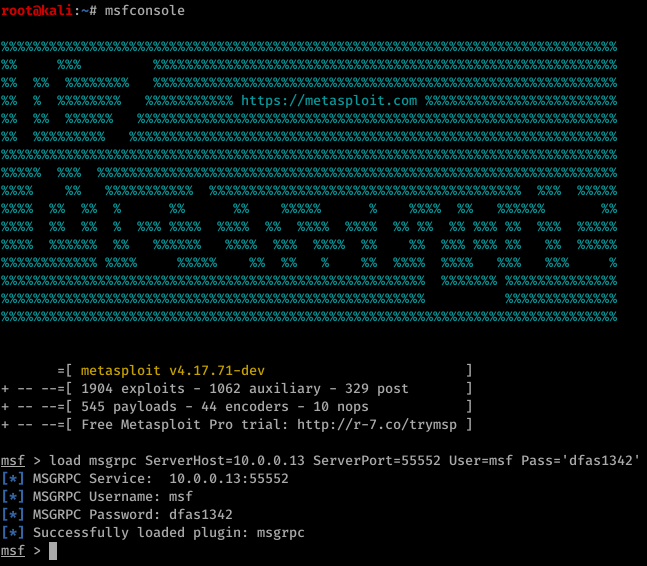
Setting up your environment - start the Metasploit console as well as the RPC listener through the msgrpc module in Metasploit.
load msgrpc ServerHost=10.0.0.13 ServerPort=55552 User=msf Pass='dfas1342'
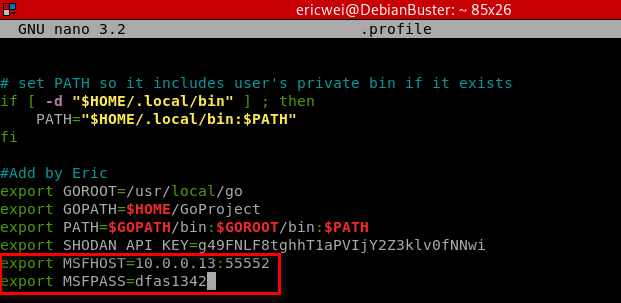
To make the code more portable and avoid hardcoding values, set the environment variables.
First, review the Metasploit API developer documentation at the official website https://metasploit.help.rapid7.com/docs/rpc-api.
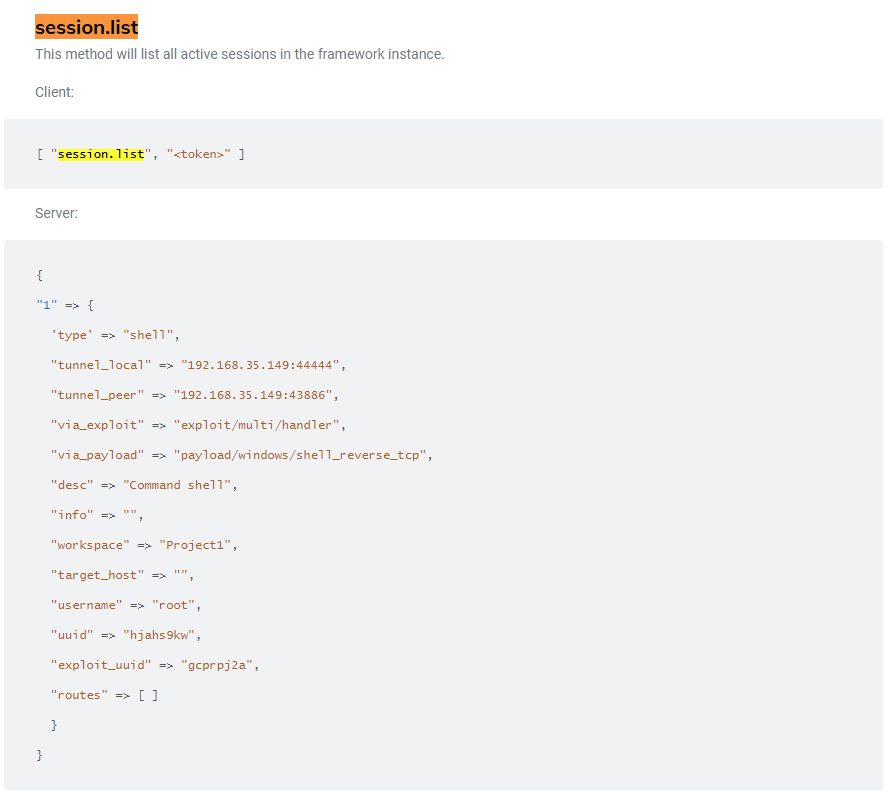
session.list API method.
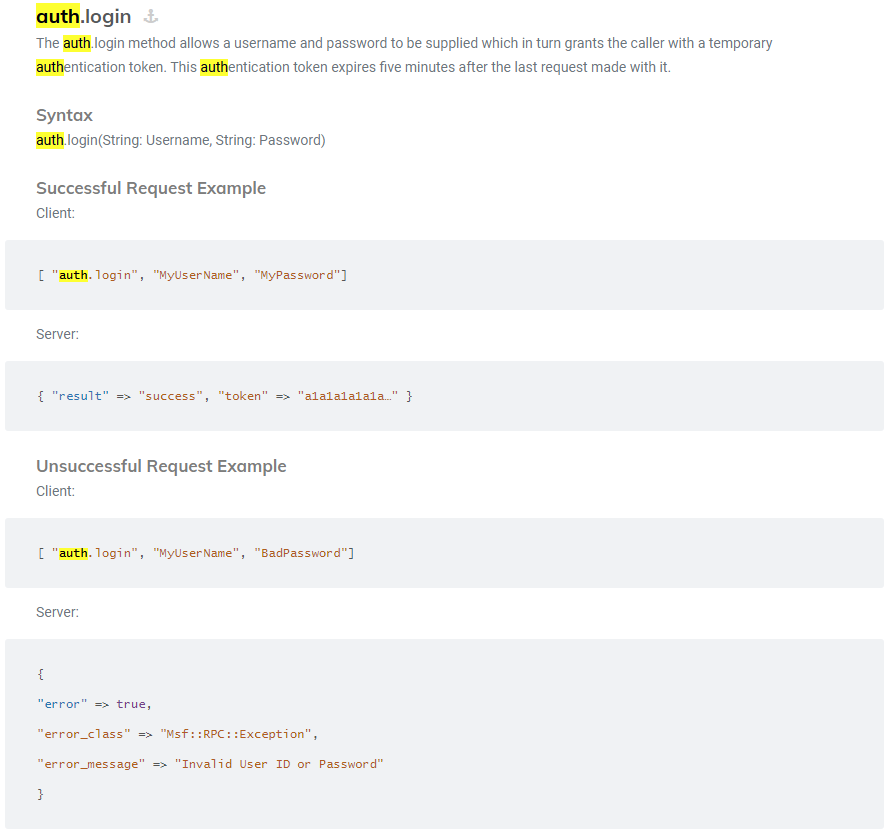
auth.login API method.
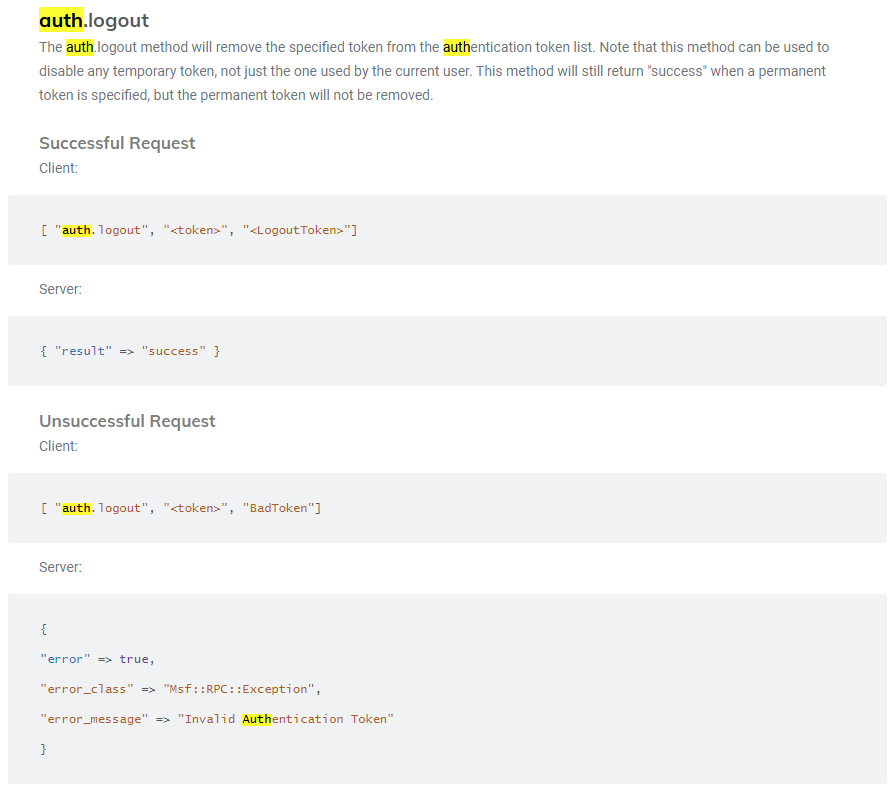
auth.logout API method
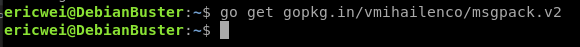
Metasploit communicates using MessagePack, a compact and efficient binary format. So let's install a standard MessagePack package.
go get gopkg.in/vmihailenco/msgpack.v2
Create your directory structure.