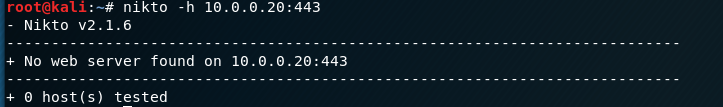
HTTP Enumeration
Target Host IP: 10.0.0.20
Brute Forcing using DirBuster
1. Start the dirbuster and set the options.
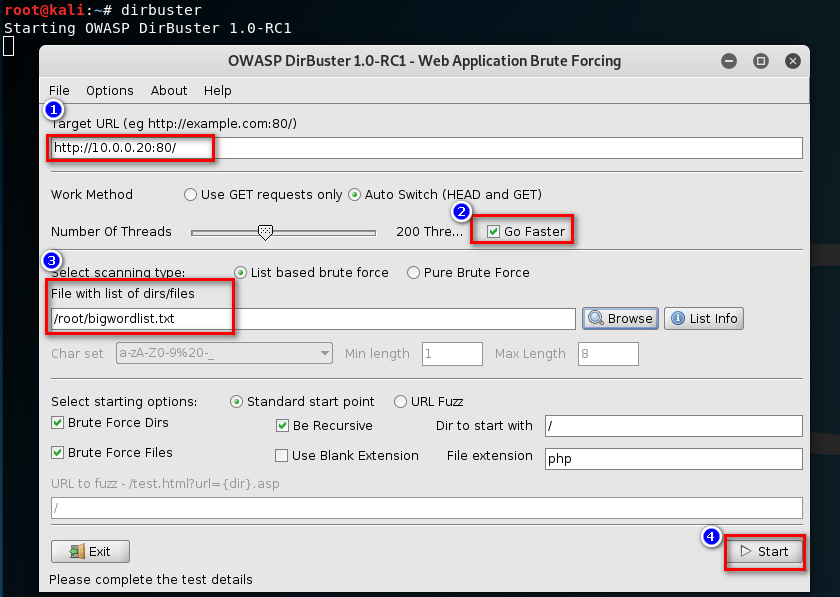
Note:
1. The wordlist can be found locally or downloaded from the Internet.
OR Dirbuster-ng big wordlist dowload site:https://github.com/digination/dirbuster-ng/tree/master/wordlists
2. Progress in sacanning.
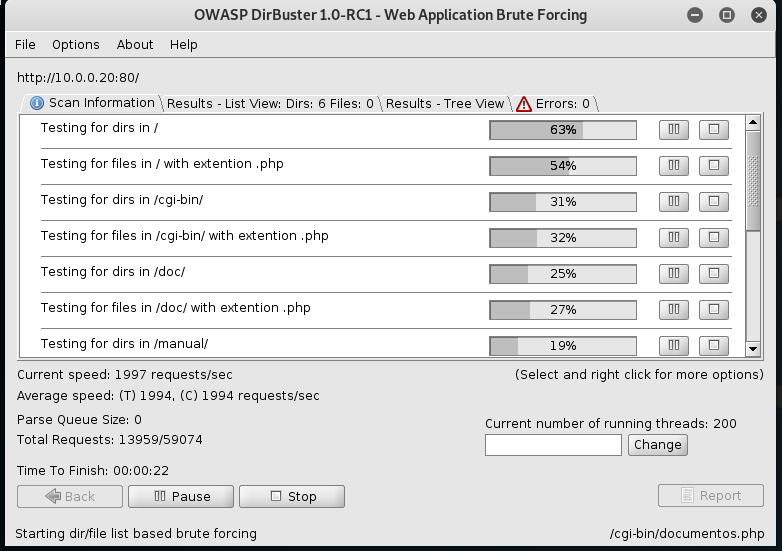
3. Scan result tree. We may find some interesting things here.
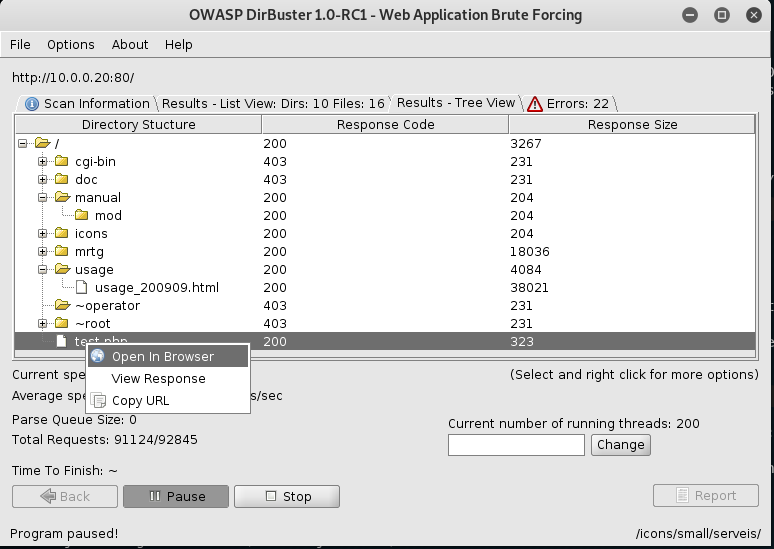
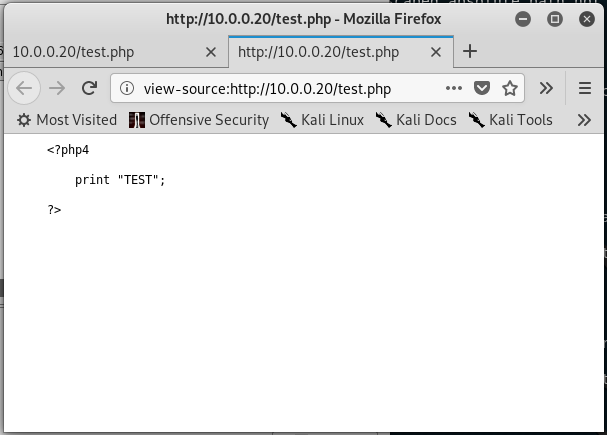
4.Open the test.php in browser, and review the source code.
Brute Forcing using nikto
1. Scan the target port 80(http).
nikto -h 10.0.0.20

2. Scan the target port 443(https).
nikto -h 10.0.0.20:443