原文:
https://www.cnblogs.com/ou11/p/10133217.html
1.在阿里云控制台-访问控制中创建读写权限策略
https://help.aliyun.com/document_detail/31935.html?spm=5176.doc32069.2.4.AxKPsA%EF%BC%89
新建自定义策略
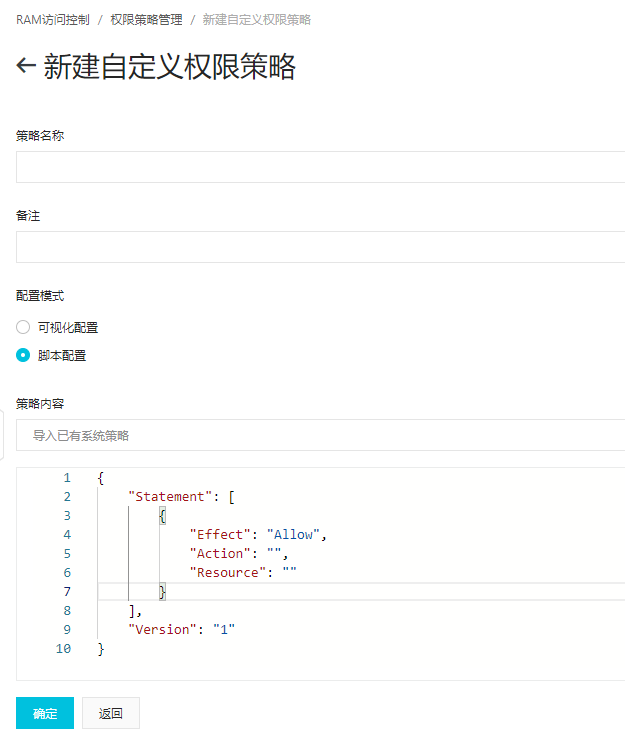
权限策略格式
{
"Version": "1",
"Statement": [
{
"Effect": "Allow",
"Action": [
"oss:DeleteObject",
"oss:ListParts",
"oss:AbortMultipartUpload",
"oss:PutObject",
"oss:GetObject"
],
"Resource": [
"acs:oss:*:*:YourBucketName",
"acs:oss:*:*:YourBucketName/*"
]
}
]
}
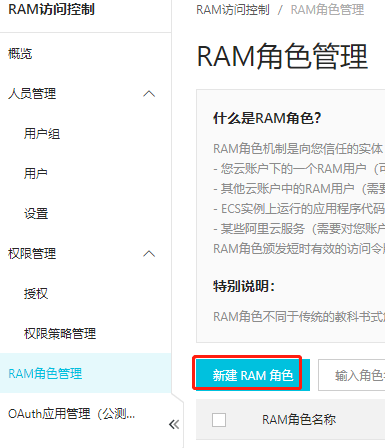
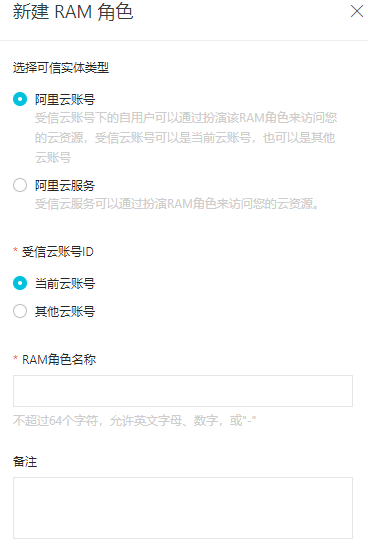
2.创建角色
新建RAM角色
3.为新增的角色添加自定义权限策略
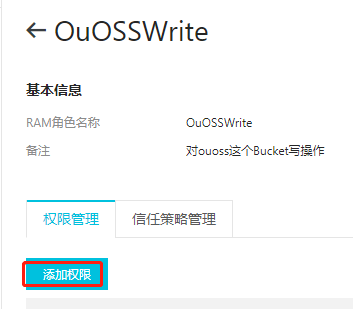
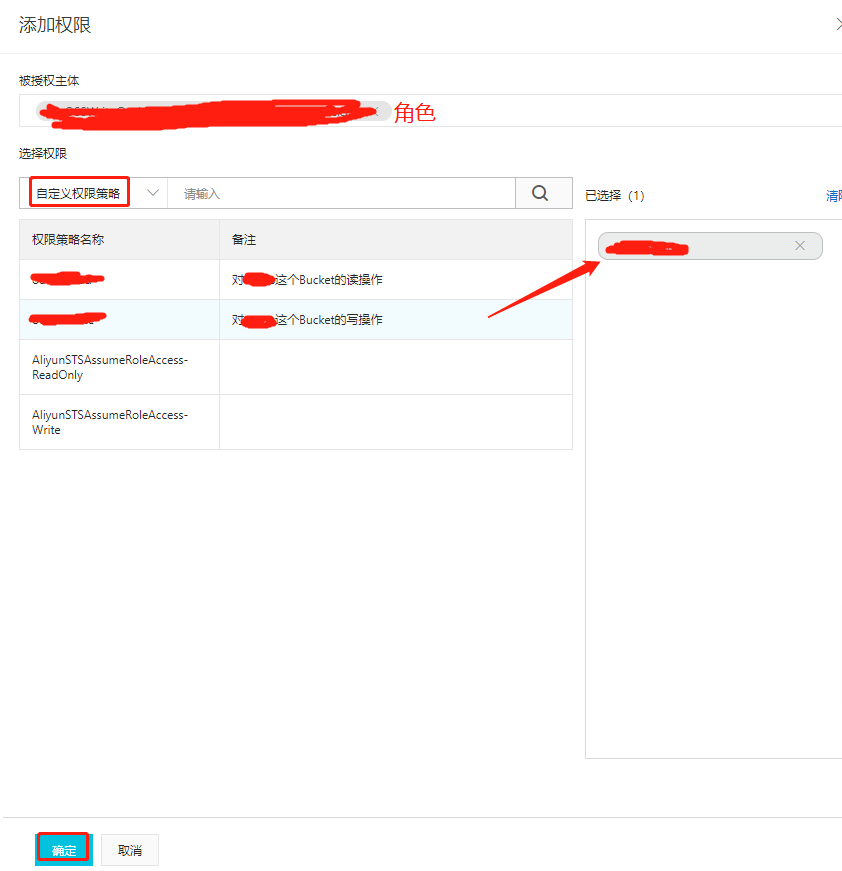
获取到ARN


4.创建子账号

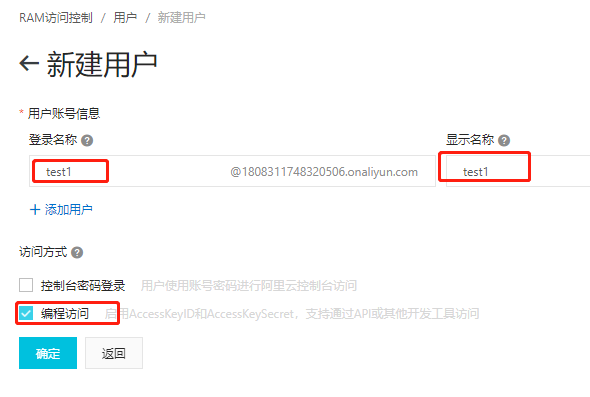
获取到AccessKeyID和AccessKeySecret

为该用户添加调用STS服务AssumeRole接口的权限

5.服务端调用
添加依赖
<dependency>
<groupId>com.aliyun</groupId>
<artifactId>aliyun-java-sdk-sts</artifactId>
<version>3.0.0</version>
</dependency>
<dependency>
<groupId>com.aliyun</groupId>
<artifactId>aliyun-java-sdk-core</artifactId>
<version>3.5.0</version>
</dependency>
赋予角色方法
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
|
/** * 赋予角色 * * @param accessKeyId * @param accessKeySecret * @param roleArn * @param roleSessionName * @param policy * @param seconds * @param protocolType * @return * @author 欧解决 * @date 2018-12-17 17:32:18 **/ public AssumeRoleResponse assumeRole( String regionId, String accessKeyId, String accessKeySecret, String roleArn, String roleSessionName, String policy, Long seconds) { try { // 创建一个 Aliyun Acs Client, 用于发起 OpenAPI 请求 IClientProfile profile = DefaultProfile.getProfile(regionId, accessKeyId, accessKeySecret); DefaultAcsClient client = new DefaultAcsClient(profile); // 创建一个 AssumeRoleRequest 并设置请求参数 final AssumeRoleRequest request = new AssumeRoleRequest(); //POST请求 request.setMethod(MethodType.POST); //https协议 request.setProtocol(ProtocolType.HTTPS); //持续时间 request.setDurationSeconds(seconds); //角色id request.setRoleArn(roleArn); //应用程序标识(自己定义) request.setRoleSessionName(roleSessionName); //在赋予角色的同时,还赋予其他的权限策略 request.setPolicy(policy); // 发起请求,并得到response final AssumeRoleResponse response = client.getAcsResponse(request); return response; } catch (Exception e) { e.printStackTrace(); } return null; } |
Controller调用
@Autowired
private OSSProperties ossProperties;
@Autowired
private StsService stsService;
/**
* 签名授权
*
* @return
* @author 欧解决
* @date 2018-12-17 15:08:55
**/
@GetMapping("/getOssToken")
public Object getOssToken() {
AssumeRoleResponse response = stsService.assumeRole(
ossProperties.getRegionId(),
ossProperties.getAccessKey(),
ossProperties.getAccessSecret(),
ossProperties.getRoleArn(),
"my-session-name",
null,
3600L
);
if (response != null) {
return new BaseTRo<>(response.getCredentials());
}
return new BaseRo(SystemError.ProcessMsg, "OssToken获取失败");
}
接口返回数据
|
1
2
3
4
5
6
7
8
9
10
|
{ "code": "0", "msg": "", "data": { "securityToken": "CAIS7gF1q6Ft5B2yfSjIr4vaMc+F2Ilz+7ahTH+IgXgFfuQY3LzdtTz2IHxJfHBhBusev/4+mGlT5/8ZlqNzVplUWEqBZNNxtn6HNrUyJ9ivgde8yJBZor/HcDHhJnyW9cvWZPqDP7G5U/yxalfCuzZuyL/hD1uLVECkNpv74vwOLK5gPG+CYCFBGc1dKyZ7tcYeLgGxD/u2NQPwiWeiZygB+CgE0DMvs/rknJPAs0KE1QalltV4/dqhfsKWCOB3J4p6XtuP2+h7S7HMyiY46WIRqPou1f0bom+W5IDBWgIAuk6cXurJ48BpPNnK5EGq9GovGoABfy0gMkLTYW4gEzdc5wxcZNWl/orL/DmvymDIWe1M/u/JUDpA3NfQTTnxG9xSxTz4lwPeEG9LgoYZzXuDTtmRcl/wQetvjDU7PBC1urYMNtVlyaST3jGfa+WU0zAW57zOBqeBejxui9AE1JCOcg2CDA/u5Mz2Hu79Ci7UTJ0eusw=", "accessKeySecret": "FAA1KeGnmMEWjYHaKuL5WP5NSeVVFor7hMHd4VBQ7Uaa", "accessKeyId": "STS.NHozu15VRLuJNY9exPrk13yvW", "expiration": "2018-12-17T11:52:38Z" }} |