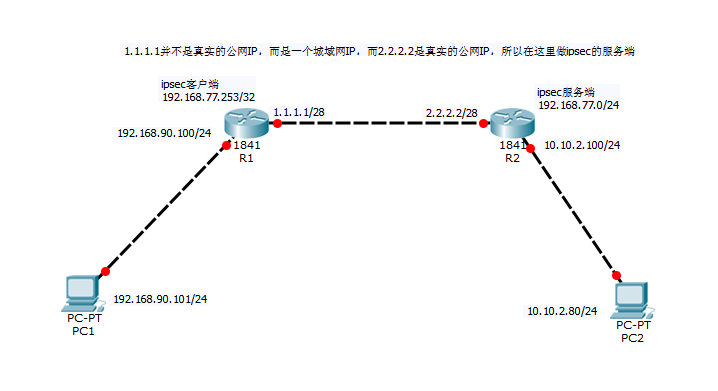
先介绍下环境拓扑图:
1.1.1.1并不是真实的公网IP,而是一个城域网IP,而2.2.2.2是真实的公网IP,所以在这里做ipsec的服务端
1.1.1.1被nat出去以后的IP是b.b.b.b
客户端配置:
/interface bridge
add name=bridge1-wan
/interface ethernet
set [ find default-name=ether1 ] name=ether1-wan
set [ find default-name=ether2 ] name=ether2-wan
set [ find default-name=ether3 ] name=ether3-wan
set [ find default-name=ether4 ] name=ether4-wan
set [ find default-name=ether5 ] name=ether5-lan
/interface pppoe-client
add disabled=no interface=bridge1-wan name=pppoe-out1 password=123456 user=
02501017724
/ip ipsec mode-config
add name=cfg1 responder=no
/ip ipsec profile
add enc-algorithm=aes-256 hash-algorithm=sha256 name=ikev2-profile1
/ip ipsec peer
add address=2.2.2.2/32 exchange-mode=ike2 name=ikev2-peer1 profile=
ikev2-profile1
/ip ipsec proposal
add auth-algorithms=sha256 enc-algorithms=aes-256-cbc name=ikev2-proposal1
pfs-group=none
/interface bridge port
add bridge=bridge1-wan interface=ether1-wan
add bridge=bridge1-wan interface=ether2-wan
add bridge=bridge1-wan interface=ether3-wan
add bridge=bridge1-wan interface=ether4-wan
/ip address
add address=192.168.90.100/24 interface=ether5-lan network=192.168.90.0
/ip dns
set servers=114.114.114.114
/ip firewall nat
add action=accept chain=srcnat dst-address=10.10.2.0/24 src-address=
192.168.77.0/24
add action=accept chain=srcnat dst-address=10.10.2.0/24 src-address=
192.168.90.0/24
add action=masquerade chain=srcnat out-interface=pppoe-out1
/ip ipsec identity
add generate-policy=port-strict mode-config=cfg1 peer=ikev2-peer1 secret=
12345678
/ip ipsec policy(这里要斟酌下1.1.1.1这里的IP怎么写,因为这个IP是城域网IP,nat出去以后并不是这个ip,nat出去以后是b.b.b.b这个ip)
add dst-address=10.10.2.0/24 level=unique proposal=ikev2-proposal1
sa-dst-address=2.2.2.2 sa-src-address=1.1.1.1 src-address=
192.168.90.0/24 tunnel=yes
/ip route
add distance=1 gateway=pppoe-out1
服务端配置:
/interface ethernet
set [ find default-name=ether1 ] name=ether1-wan
set [ find default-name=ether2 ] name=ether2-lan
/ip ipsec profile
add enc-algorithm=aes-256 hash-algorithm=sha256 name=ikev2-profile1
/ip ipsec peer
add exchange-mode=ike2 name=ikev2-peer1 passive=yes profile=ikev2-profile1
send-initial-contact=no
/ip ipsec proposal
add auth-algorithms=sha256 enc-algorithms=aes-256-cbc name=ikev2-proposal1
pfs-group=none
/ip pool
add name=ikev2-pool ranges=192.168.77.2-192.168.77.254
/ip ipsec mode-config
add address-pool=ikev2-pool address-prefix-length=32 name=cfg1
split-include=10.10.2.0/24 system-dns=no
/ip address
add address=2.2.2.2/28 interface=ether1-wan network=2.2.2.0
add address=10.10.2.100/24 interface=ether2-lan network=10.10.2.0
/ip firewall nat
add action=accept chain=srcnat dst-address=192.168.77.0/24 src-address=
10.10.2.0/24
add action=accept chain=srcnat dst-address=192.168.90.0/24 src-address=
10.10.2.0/24
add action=masquerade chain=srcnat out-interface=ether1-wan
/ip ipsec identity
add generate-policy=port-strict mode-config=cfg1 peer=ikev2-peer1 secret=
12345678
/ip ipsec policy(这里需要斟酌下,IP公网怎么写,b.b.b.b是客户端路由nat以后的公网IP)
add dst-address=192.168.90.0/24 level=unique proposal=ikev2-proposal1
sa-dst-address=b.b.b.b sa-src-address=2.2.2.2
src-address=10.10.2.0/24 tunnel=yes
/ip route
add distance=1 gateway=2.2.2.1