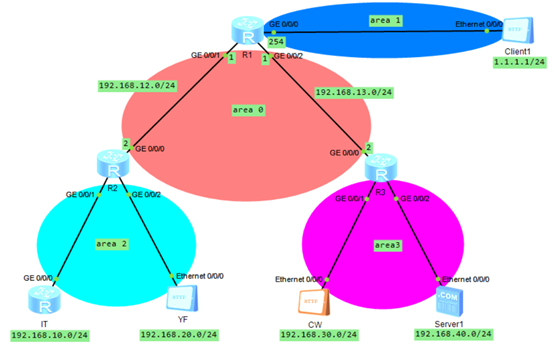
1.企业内网运行OSPF路由协议,区域规划如图所示
2.财务和研发所在的区域不受其他区域链路不稳定性影响
3.R1、R2、R3只允许被IT登录管理
4.YF和CW之间不能互通,但都可以与IT互通
5.IT和YF可以访问Client1,但CW不能访问Client1
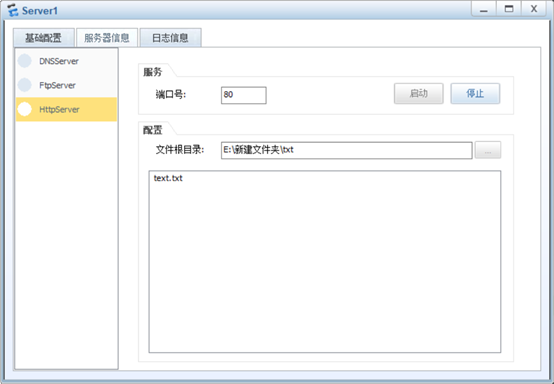
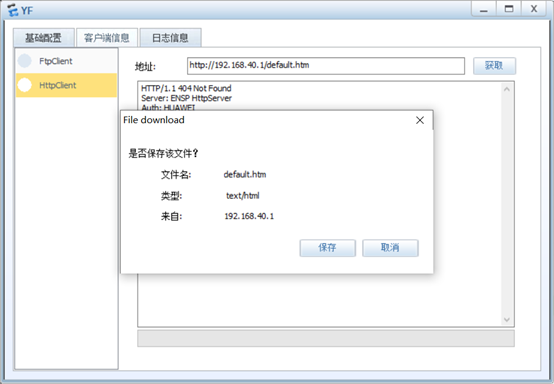
6.YF和CW只能访问Server1的WWW服务
分析:
CW
1.YF和CW之间不能互通,但都可以与IT互通
2.CW不能访问Client1
3.CW只能访问Server1的WWW服务
YF
1.YF和CW之间不能互通,但都可以与IT互通
3.YF只能访问Server1的WWW服务
IT
1.R1、R2、R3只允许被IT登录管理
2.IT可以访问Client1
配置IP:
R1
[R1]int g0/0/0
[R1-GigabitEthernet0/0/0]ip address 1.1.1.254 24
[R1-GigabitEthernet0/0/0]int g0/0/1
[R1-GigabitEthernet0/0/1]ip address 192.168.12.1 24
[R1-GigabitEthernet0/0/1]int g0/0/2
[R1-GigabitEthernet0/0/2]ip address 192.168.13.1 24
[R1-GigabitEthernet0/0/2]q
R2
[R2]int g0/0/0
[R2-GigabitEthernet0/0/0]ip address 192.168.12.2 24
[R2-GigabitEthernet0/0/0]int g0/0/1
[R2-GigabitEthernet0/0/1]ip address 192.168.10.254 24
[R2-GigabitEthernet0/0/1]int g0/0/2
[R2-GigabitEthernet0/0/2]ip address 192.168.20.254 24
[R2-GigabitEthernet0/0/2]q
R3
[R3]int g0/0/0
[R3-GigabitEthernet0/0/0]ip address 192.168.13.2 24
[R3-GigabitEthernet0/0/0]int g0/0/1
[R3-GigabitEthernet0/0/1]ip address 192.168.30.254 24
[R3-GigabitEthernet0/0/1]int g0/0/2
[R3-GigabitEthernet0/0/2]ip address 192.168.40.254 24
[R3-GigabitEthernet0/0/2]q
IT
[IT]int g0/0/0
[IT-GigabitEthernet0/0/0]ip address 192.168.10.1 24
[IT-GigabitEthernet0/0/0]q
配置OSPF:
R1
[R1]ospf 1
[R1-ospf-1]area 0
[R1-ospf-1-area-0.0.0.0]network 192.168.12.0 0.0.0.255
[R1-ospf-1-area-0.0.0.0]network 192.168.13.0 0.0.0.255
[R1-ospf-1-area-0.0.0.0]dis th
[V200R003C00]
#
area 0.0.0.0
network 192.168.12.0 0.0.0.255
network 192.168.13.0 0.0.0.255
#
return
[R1-ospf-1-area-0.0.0.0]q
[R1-ospf-1]area 1
[R1-ospf-1-area-0.0.0.1]network 1.1.1.0 0.0.0.255
[R1-ospf-1-area-0.0.0.1]dis th
[V200R003C00]
#
area 0.0.0.1
network 1.1.1.0 0.0.0.255
#
return
[R1-ospf-1-area-0.0.0.1]q
R2
[R2]ospf 1
[R2-ospf-1]area 0
[R2-ospf-1-area-0.0.0.0]network 192.168.12.0 0.0.0.255
[R2-ospf-1-area-0.0.0.0]dis th
[V200R003C00]
#
area 0.0.0.0
network 192.168.12.0 0.0.0.255
#
return
[R2-ospf-1-area-0.0.0.0]q
[R2-ospf-1]area 2
[R2-ospf-1-area-0.0.0.2]network 192.168.10.0 0.0.0.255
[R2-ospf-1-area-0.0.0.2]network 192.168.20.0 0.0.0.255
[R2-ospf-1-area-0.0.0.2]dis th
[V200R003C00]
#
area 0.0.0.2
network 192.168.10.0 0.0.0.255
network 192.168.20.0 0.0.0.255
#
return
[R2-ospf-1-area-0.0.0.2]q
R3
[R3]ospf 1
[R3-ospf-1]area 0
[R3-ospf-1-area-0.0.0.0]network 192.168.13.0 0.0.0.255
[R3-ospf-1-area-0.0.0.0]dis th
[V200R003C00]
#
area 0.0.0.0
network 192.168.13.0 0.0.0.255
#
return
[R3-ospf-1-area-0.0.0.0]q
[R3-ospf-1]area 3
[R3-ospf-1-area-0.0.0.3]network 192.168.30.0 0.0.0.255
[R3-ospf-1-area-0.0.0.3]network 192.168.40.0 0.0.0.255
[R3-ospf-1-area-0.0.0.3]dis th
[V200R003C00]
#
area 0.0.0.3
network 192.168.30.0 0.0.0.255
network 192.168.40.0 0.0.0.255
#
return
[R3-ospf-1-area-0.0.0.3]q
IT
[IT]ospf 1
[IT-ospf-1]area 2
[IT-ospf-1-area-0.0.0.2]network 192.168.10.0 0.0.0.255
[IT-ospf-1-area-0.0.0.2]dis th
[V200R003C00]
#
area 0.0.0.2
network 192.168.10.0 0.0.0.255
#
return
[IT-ospf-1-area-0.0.0.2]q
此时检查网络中都可以互相连通:
[IT]ping 1.1.1.1
PING 1.1.1.1: 56 data bytes, press CTRL_C to break
Reply from 1.1.1.1: bytes=56 Sequence=1 ttl=253 time=20 ms
Reply from 1.1.1.1: bytes=56 Sequence=2 ttl=253 time=20 ms
Reply from 1.1.1.1: bytes=56 Sequence=3 ttl=253 time=30 ms
Reply from 1.1.1.1: bytes=56 Sequence=4 ttl=253 time=30 ms
Reply from 1.1.1.1: bytes=56 Sequence=5 ttl=253 time=30 ms
--- 1.1.1.1 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 20/26/30 ms
[IT]ping 192.168.40.1
PING 192.168.40.1: 56 data bytes, press CTRL_C to break
Request time out
Reply from 192.168.40.1: bytes=56 Sequence=2 ttl=252 time=30 ms
Reply from 192.168.40.1: bytes=56 Sequence=3 ttl=252 time=30 ms
Reply from 192.168.40.1: bytes=56 Sequence=4 ttl=252 time=20 ms
Reply from 192.168.40.1: bytes=56 Sequence=5 ttl=252 time=40 ms
--- 192.168.40.1 ping statistics ---
5 packet(s) transmitted
4 packet(s) received
20.00% packet loss
round-trip min/avg/max = 20/30/40 ms
按要求配置ACL:
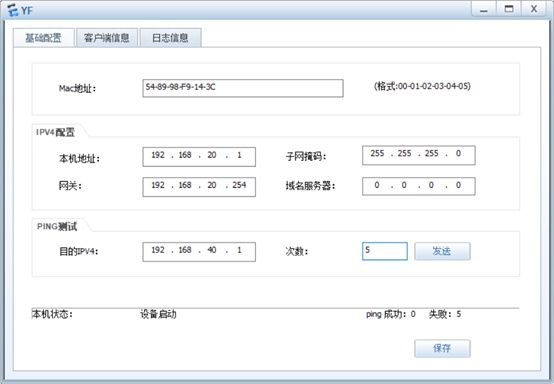
CW:
[R3]acl 3000
[R3-acl-adv-3000]rule 5 deny ip source 192.168.30.0 0.0.0.255 destination 1.1.1.
0 0.0.0.255
[R3-acl-adv-3000]rule 10 deny ip source 192.168.30.0 0.0.0.255 destination 192.1
68.20.0 0.0.0.255
[R3-acl-adv-3000]rule 15 permit tcp source 192.168.30.0 0.0.0.255 destination 19
2.168.40.1 0 destination-port eq www
[R3-acl-adv-3000]rule 20 deny ip source 192.168.30.0 0.0.0.255 destination 192.1
68.40.1 0
[R3-acl-adv-3000]q
[R3]int g0/0/1
[R3-GigabitEthernet0/0/1]traffic-filter inbound acl 3000
[R3-GigabitEthernet0/0/1]q
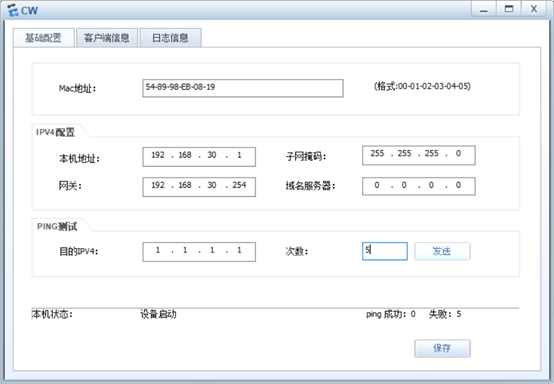
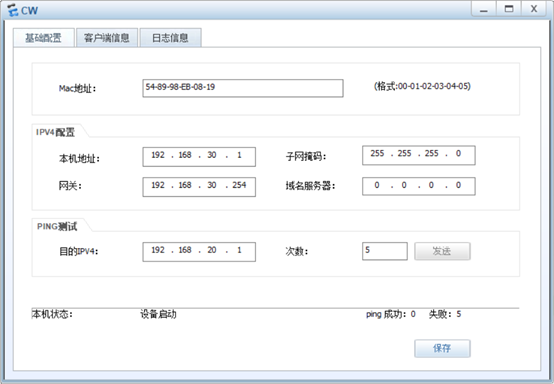
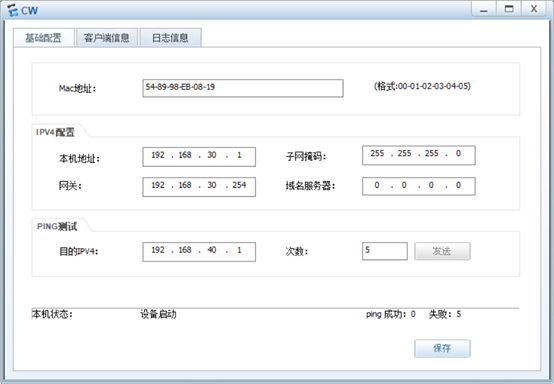


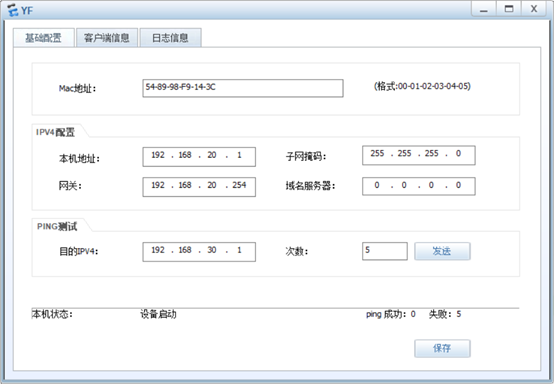
YF:
[R2]acl 3001
[R2-acl-adv-3001]rule 5 permit tcp source 192.168.20.0 0.0.0.255 destination 192
.168.40.1 0 destination-port eq www
[R2-acl-adv-3001]rule 10 deny ip source 192.168.20.0 0.0.0.255 destination 192.1
68.40.1 0
[R2-acl-adv-3001]q
[R2]int g0/0/2
[R2-GigabitEthernet0/0/2]traffic-filter inbound acl 3001
[R2-GigabitEthernet0/0/2]q
IT:
在R1上配置
[R1]acl 2000
[R1-acl-basic-2000]rule 10 permit source 192.168.10.0 0.0.0.255
[R1-acl-basic-2000]q
[R1]user-interface vty 0 4
[R1-ui-vty0-4]authentication-mode password
Please configure the login password (maximum length 16):123
[R1-ui-vty0-4]acl 2000 inbound
[R1-ui-vty0-4]dis th
[V200R003C00]
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
acl 2000 inbound
authentication-mode password
set authentication password cipher %$%$%b|hVM5/mDVFw|~(AMI>,"IGSBN(Nlh/TT~eGJ@
)@g#"IJ,%$%$
user-interface vty 16 20
#
return
[R1-ui-vty0-4]q
在R2上配置
[R2]acl 2000
[R2-acl-basic-2000]rule 10 permit source 192.168.10.0 0.0.0.255
[R2-acl-basic-2000]q
[R2]user-interface vty 0 4
[R2-ui-vty0-4]acl 2000 inbound
[R2-ui-vty0-4]authentication-mode password
Please configure the login password (maximum length 16):123
[R2-ui-vty0-4]dis th
[V200R003C00]
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
acl 2000 inbound
authentication-mode password
set authentication password cipher %$%$pZAl@MK"R7m2k.8=Fd[3,..2h4=V"fJsdR8ORh=s
cxlL..5,%$%$
user-interface vty 16 20
#
return
[R2-ui-vty0-4]q

在R3上配置
[R3]acl 2000
[R3-acl-basic-2000]rule 10 permit source 192.168.10.0 0.0.0.255
[R3-acl-basic-2000]q
[R3]user-interface vty 0 4
[R3-ui-vty0-4]acl 2000 inbound
[R3-ui-vty0-4]authentication-mode password
Please configure the login password (maximum length 16):123
[R3-ui-vty0-4]dis th
[V200R003C00]
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
acl 2000 inbound
authentication-mode password
set authentication password cipher %$%$eC/~%Q{M>U38eS9fW{hA,.we<>,5(&g1YG#wd3L3
jHl1.wh,%$%$
user-interface vty 16 20
#
return
[R3-ui-vty0-4]q
