s3
dynamodb: https://aws.amazon.com/cn/dynamodb/
new-session-manager: https://aws.amazon.com/cn/blogs/china/new-session-manager/
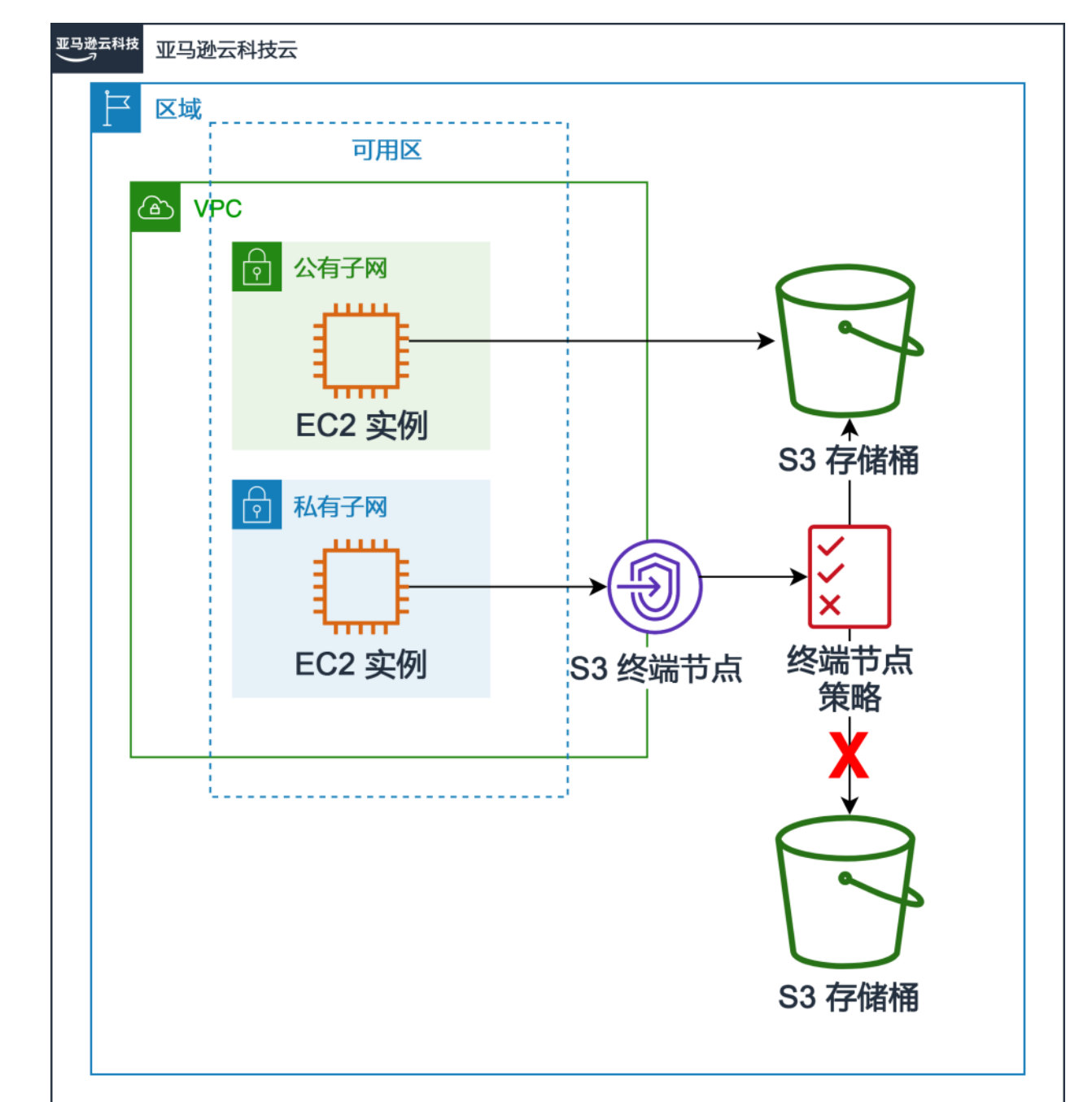
网关终端节点: 需要建一个网关
接口终端节点: 类似插入一张网卡到你的VPC
实验:
公有子网

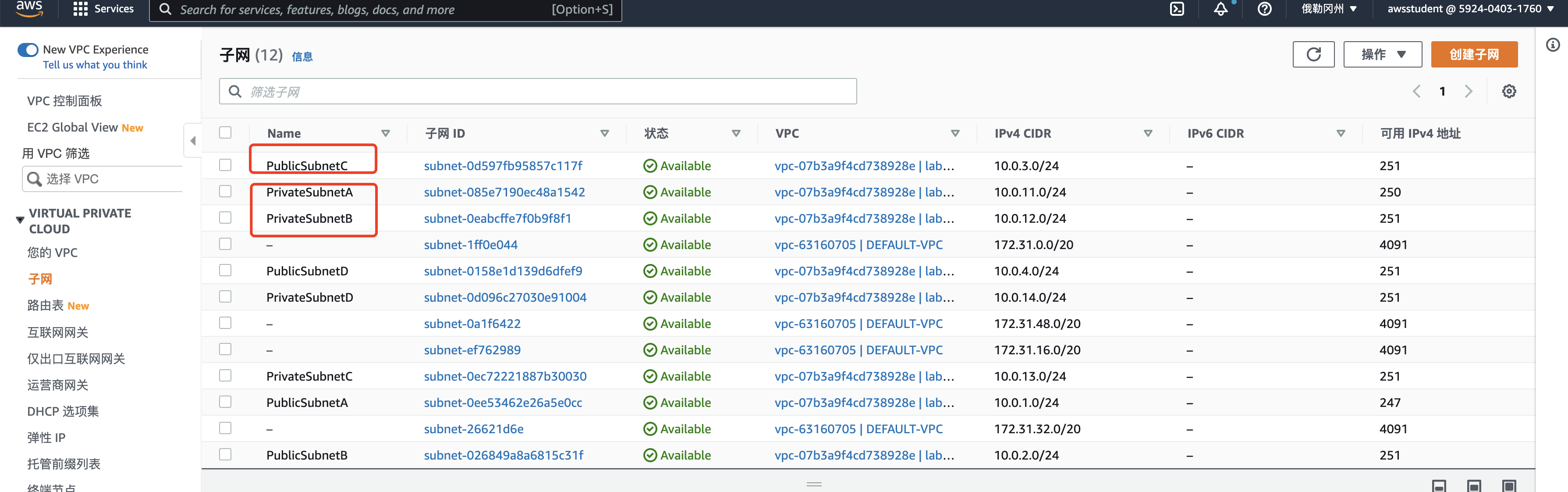

| subnet-0d597fb95857c117f / PublicSubnetC | 10.0.3.0/24 | – |
|---|---|---|
| subnet-0158e1d139d6dfef9 / PublicSubnetD | 10.0.4.0/24 | – |
| subnet-0ee53462e26a5e0cc / PublicSubnetA | 10.0.1.0/24 | – |
| subnet-026849a8a6815c31f / PublicSubnetB | 10.0.2.0/24 | – |
私有子网
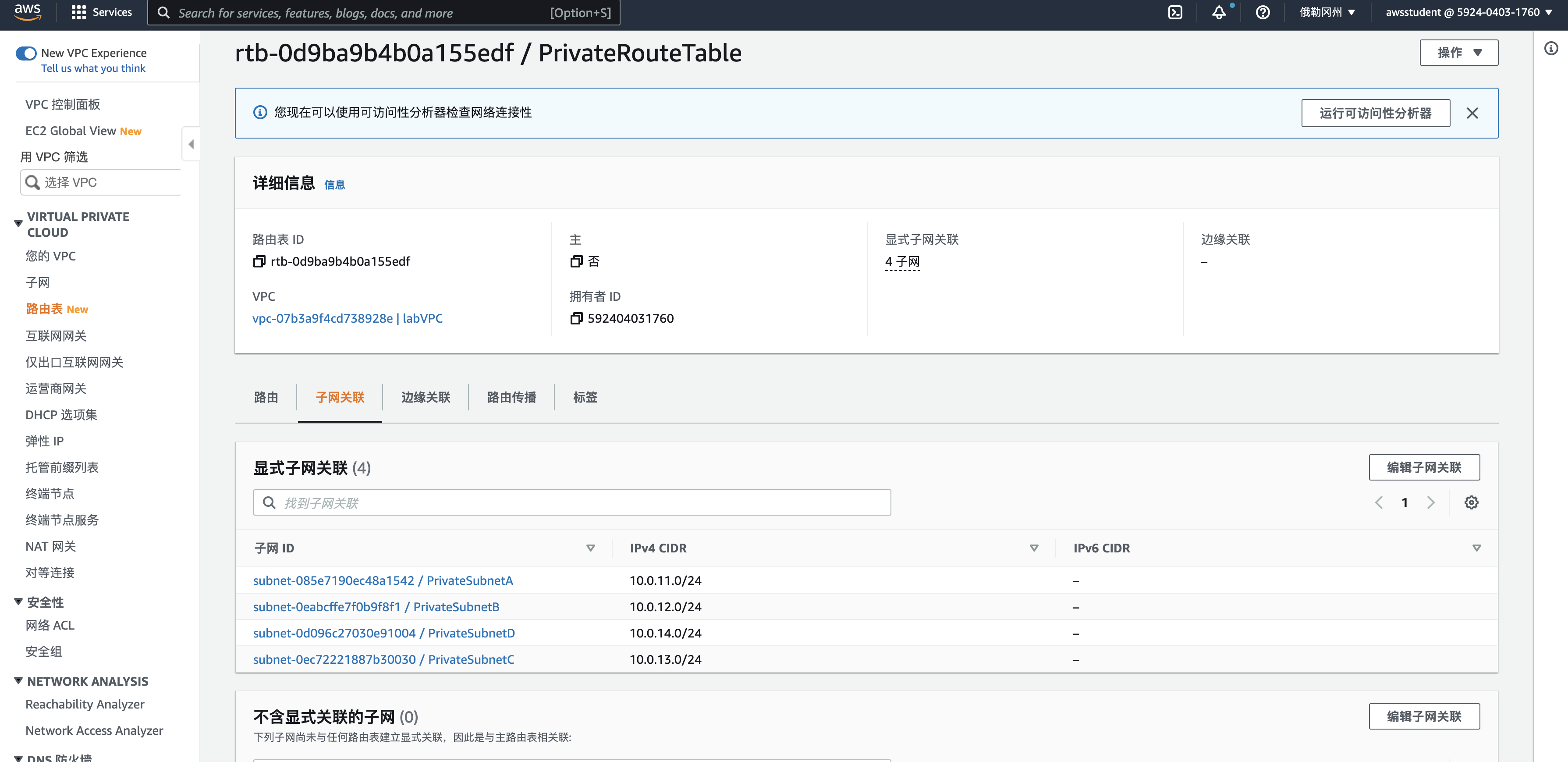
| subnet-085e7190ec48a1542 / PrivateSubnetA | 10.0.11.0/24 | – |
|---|---|---|
| subnet-0eabcffe7f0b9f8f1 / PrivateSubnetB | 10.0.12.0/24 | – |
| subnet-0d096c27030e91004 / PrivateSubnetD | 10.0.14.0/24 | – |
| subnet-0ec72221887b30030 / PrivateSubnetC | 10.0.13.0/24 | – |
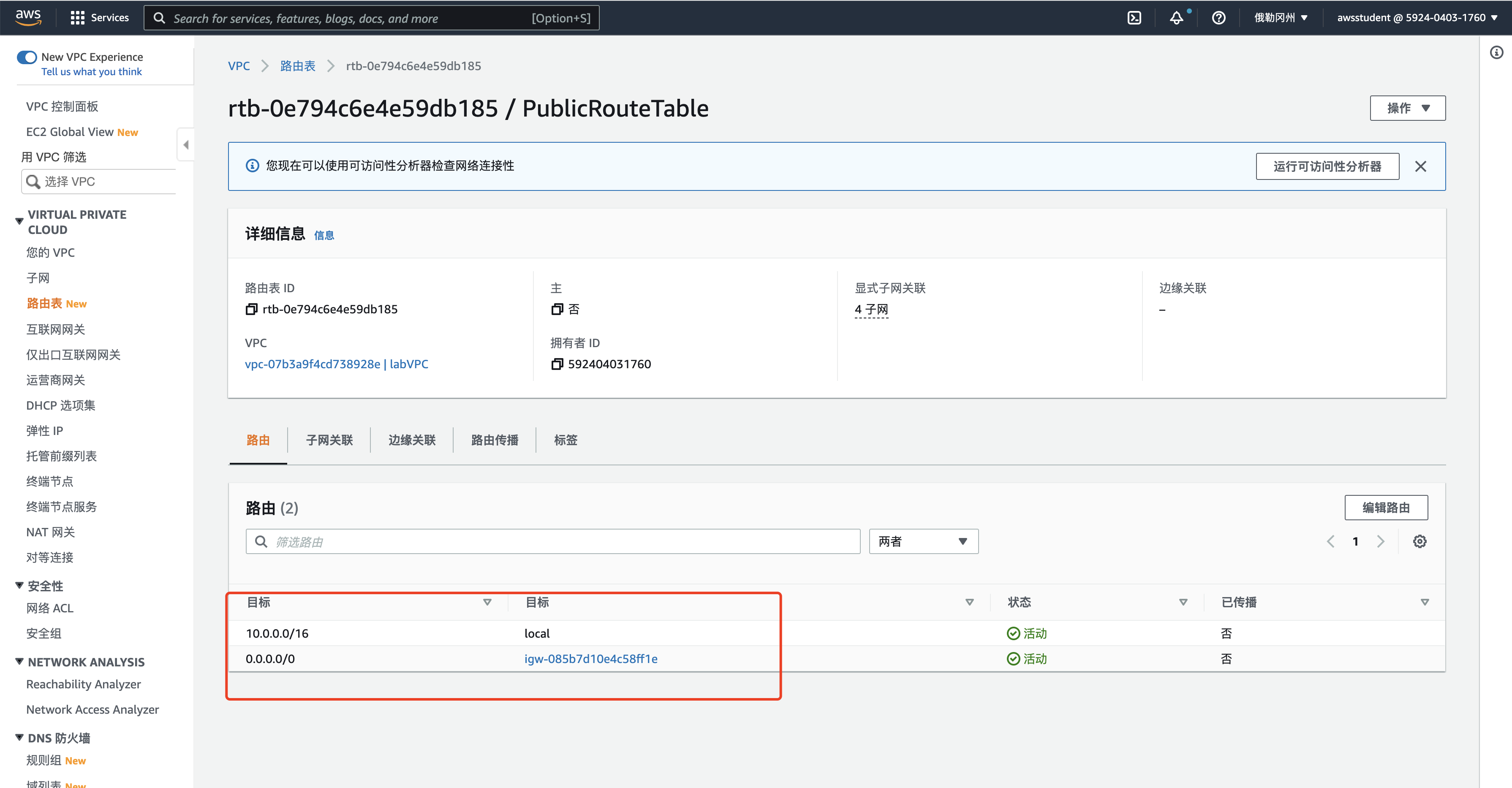
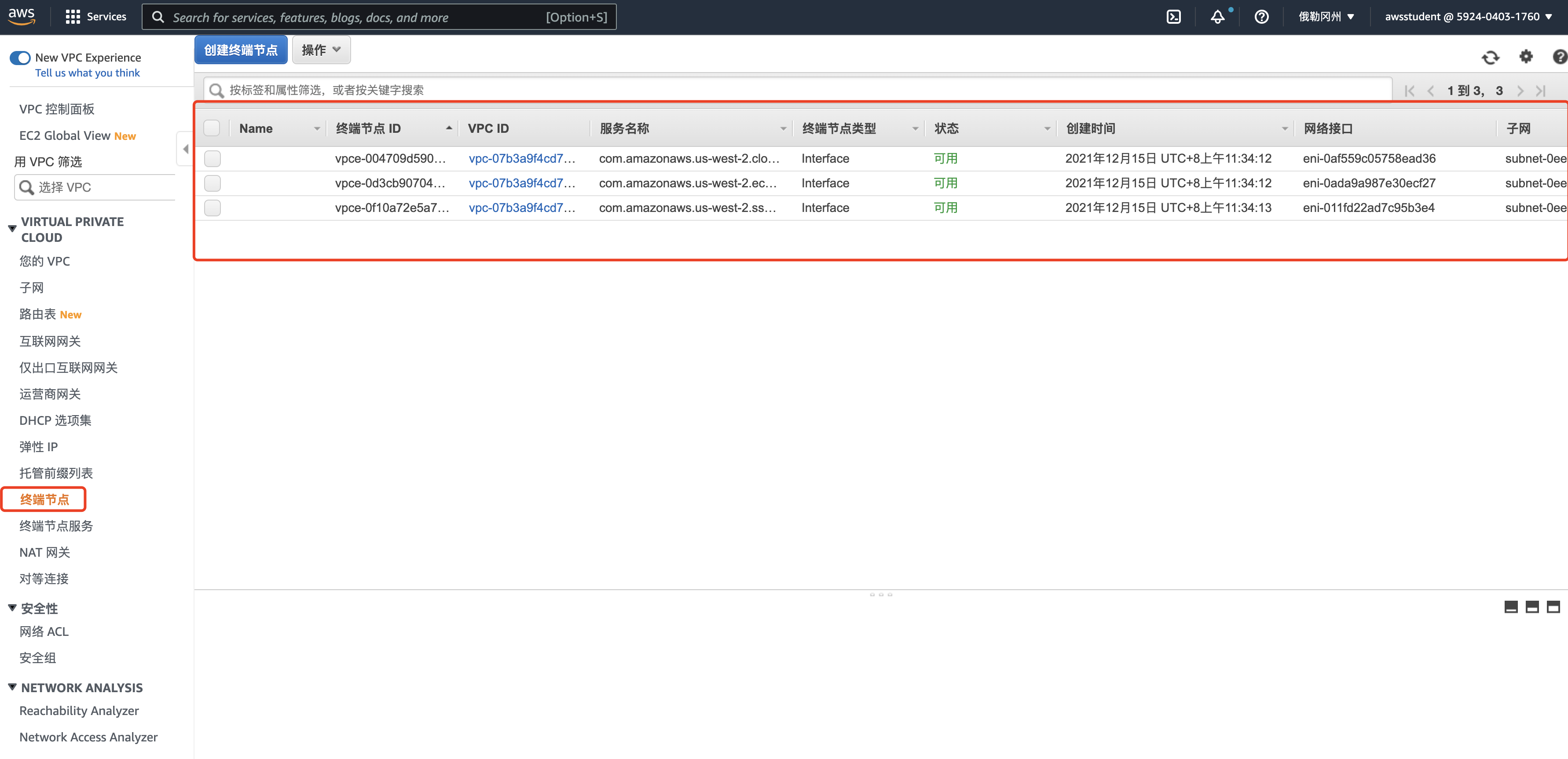
终端节点
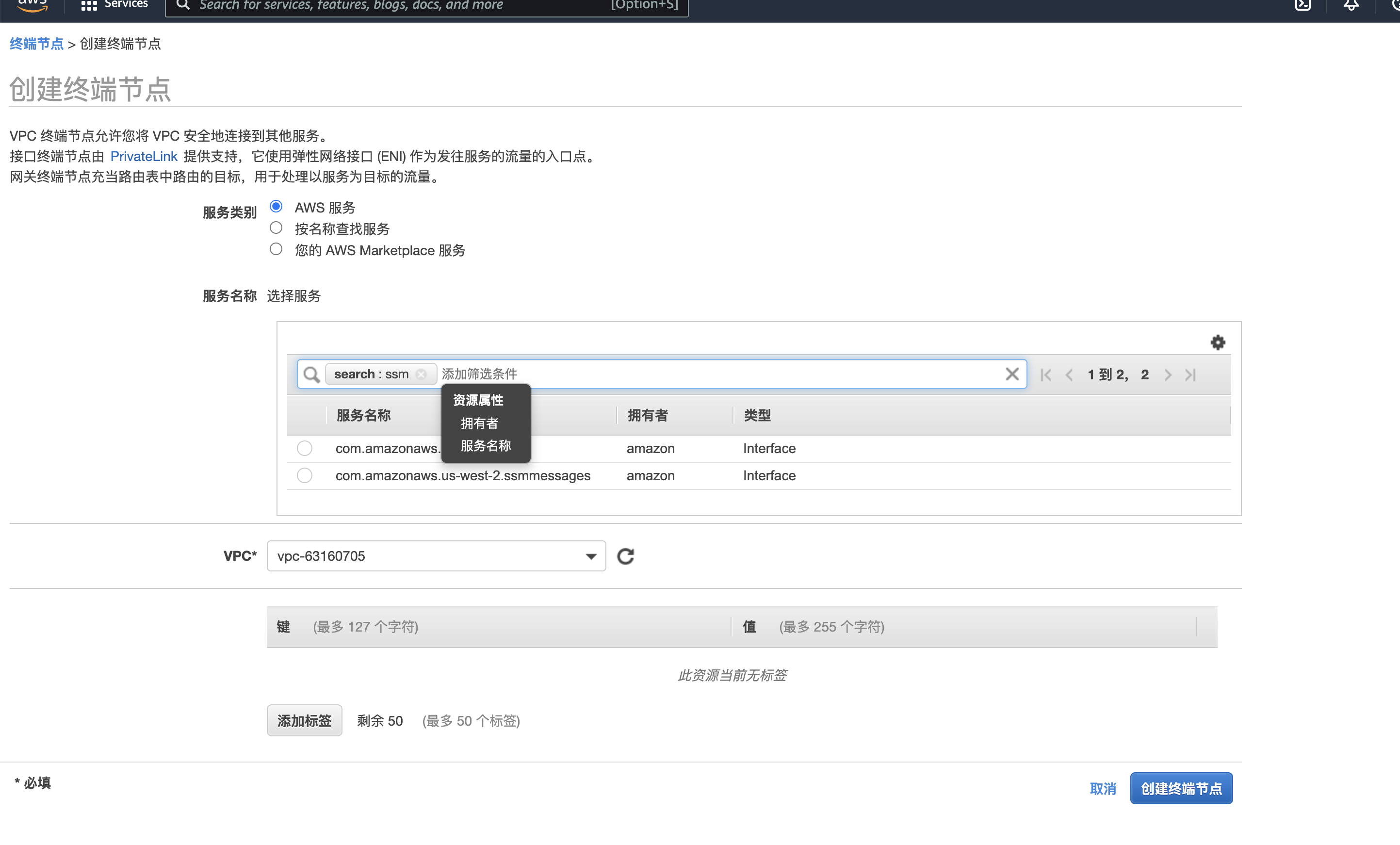
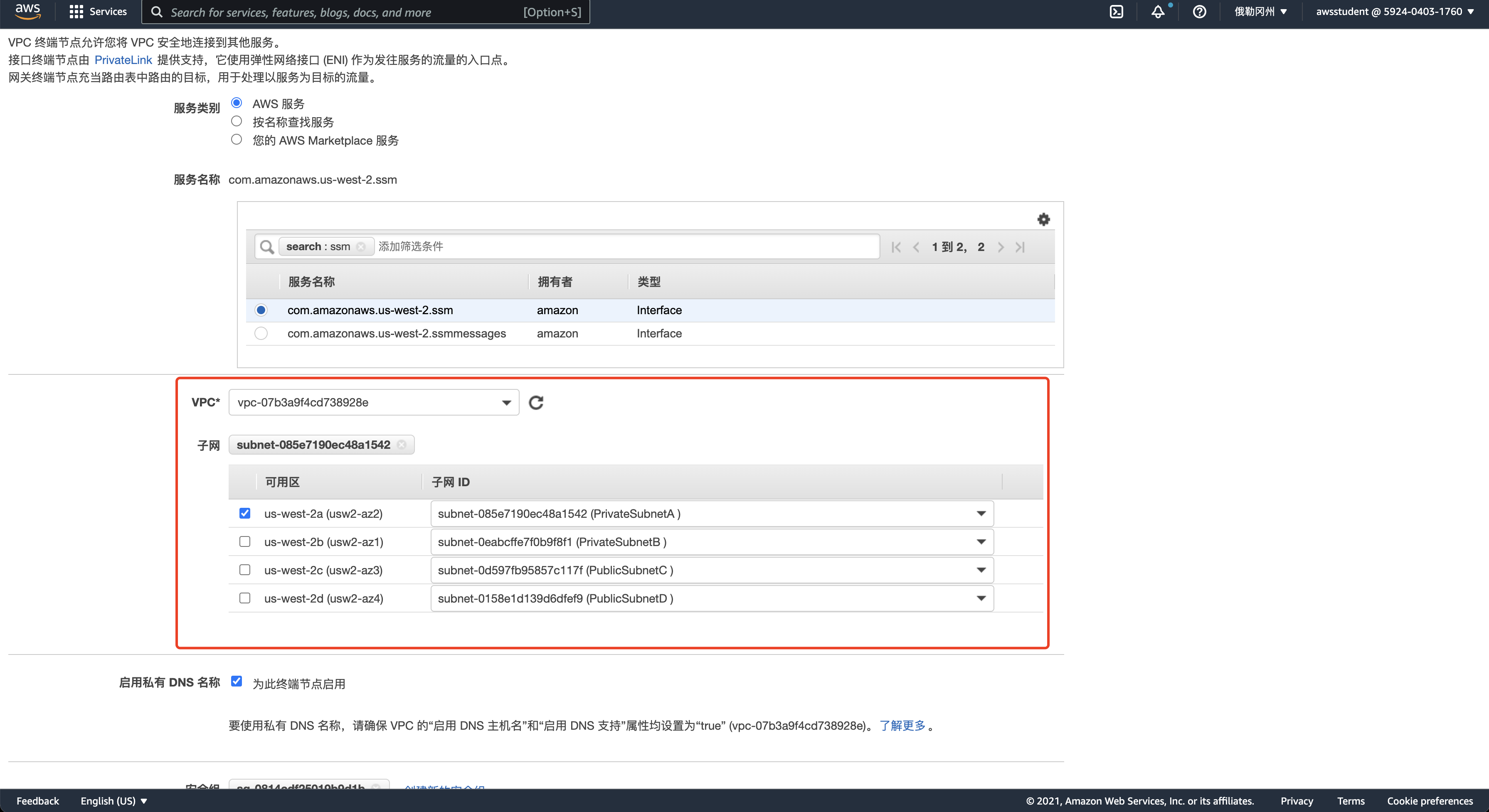

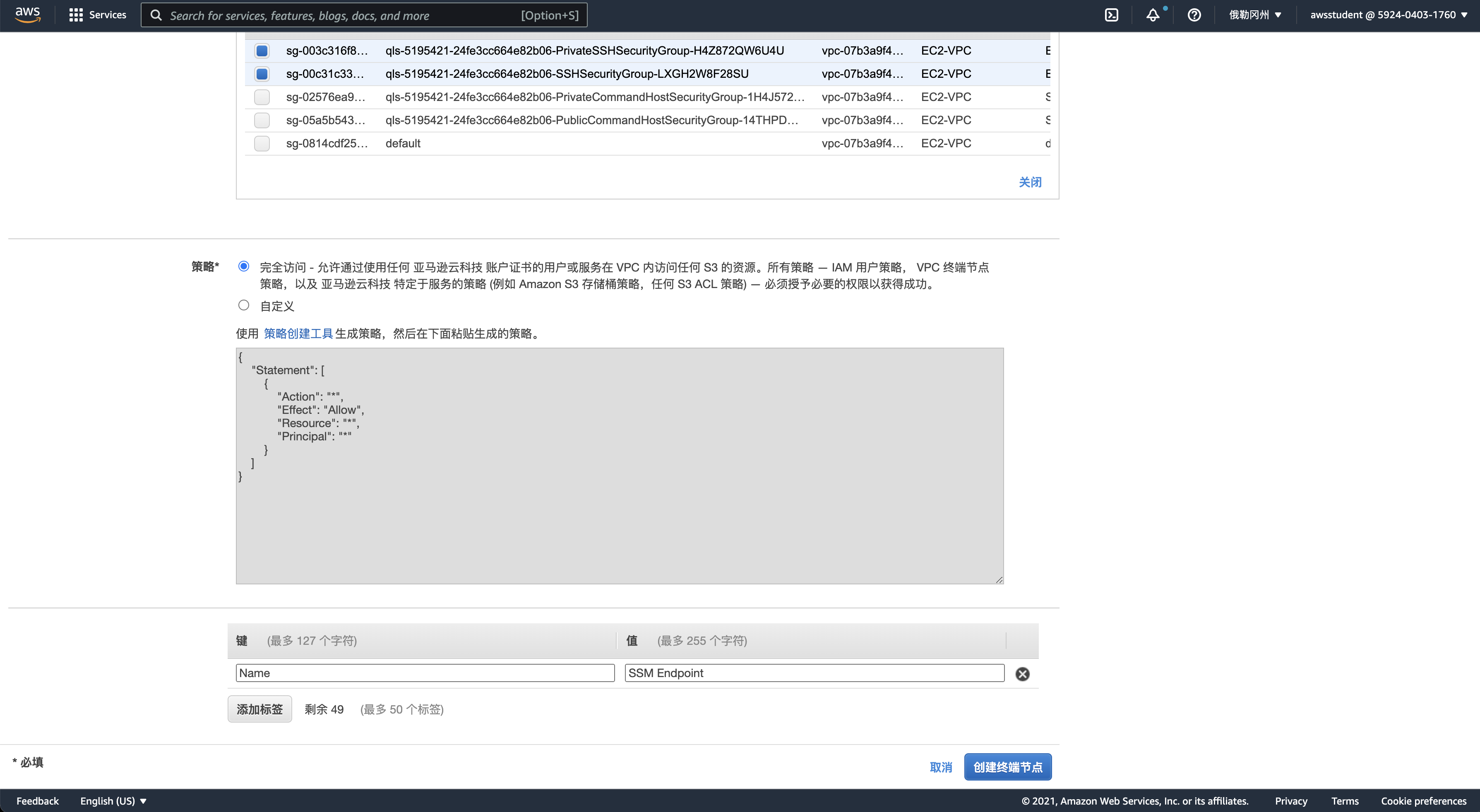

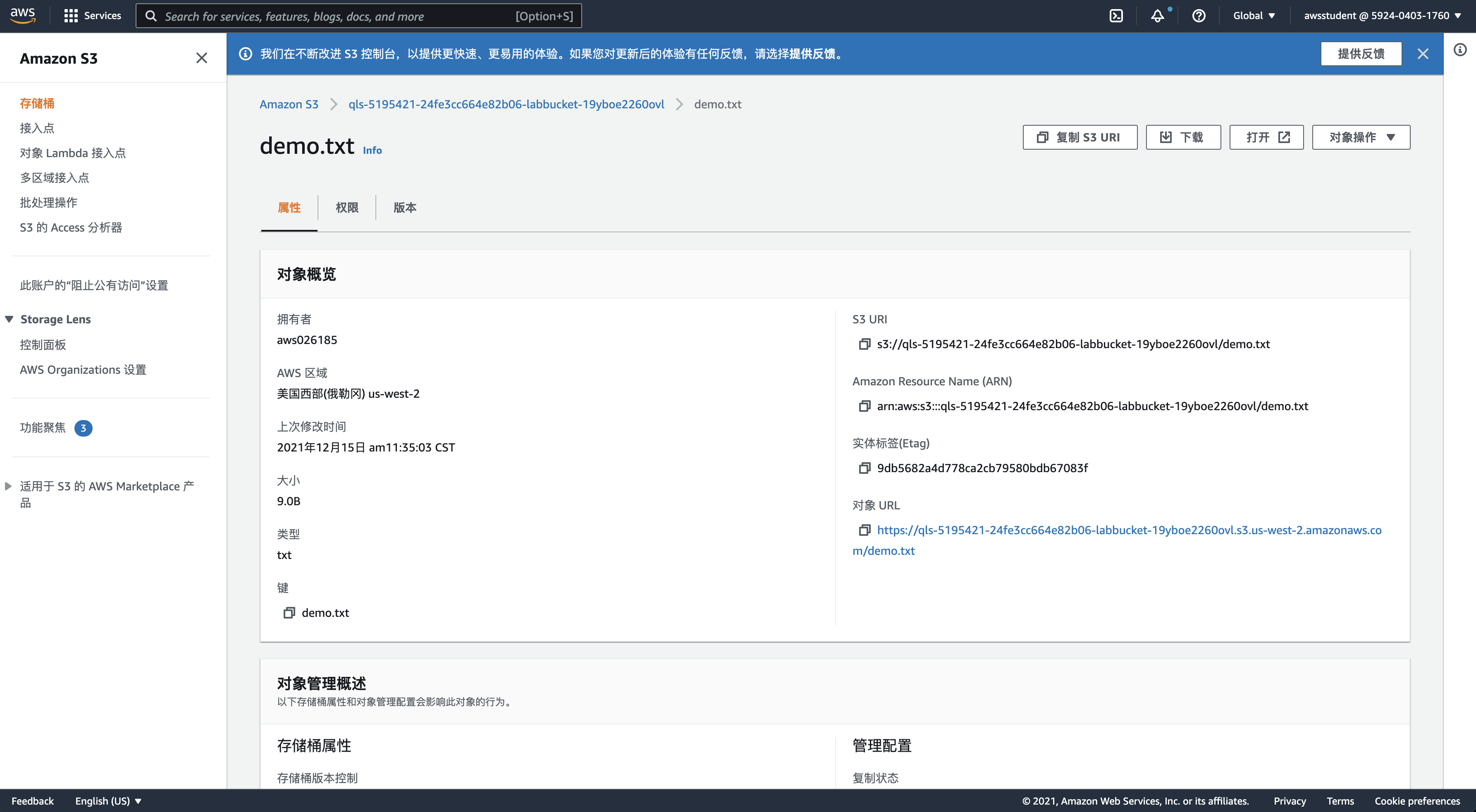
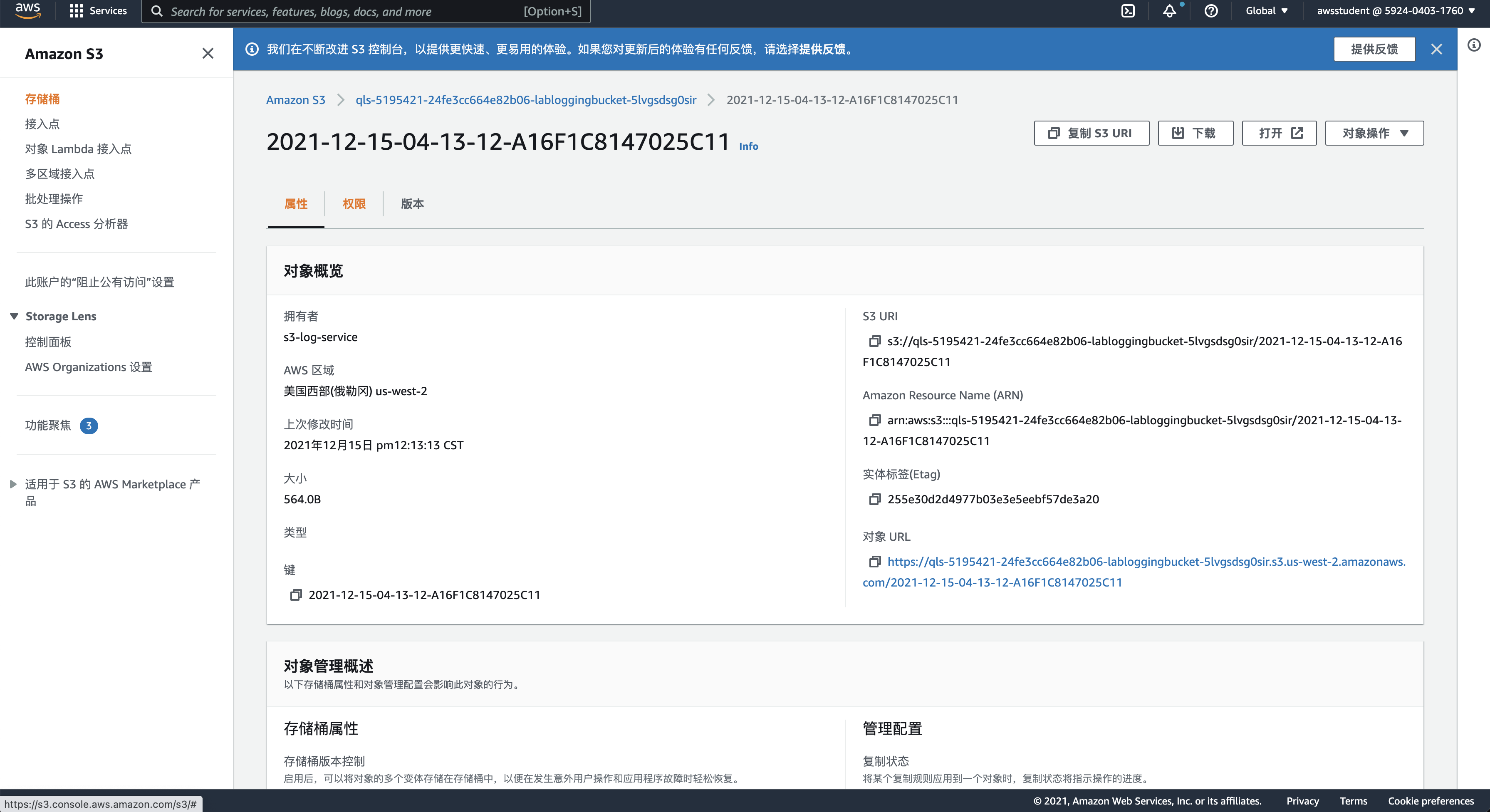

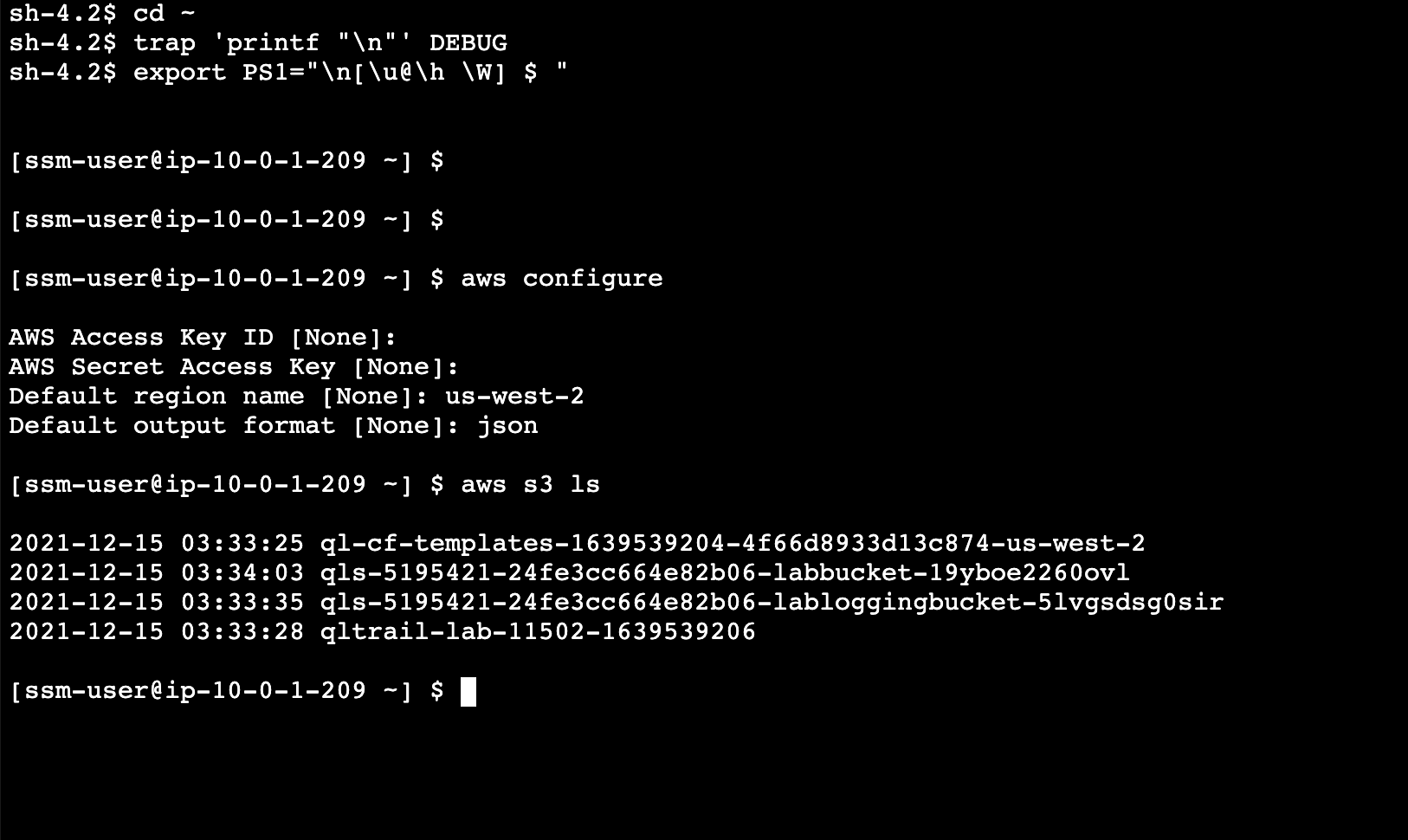
实例访问S3
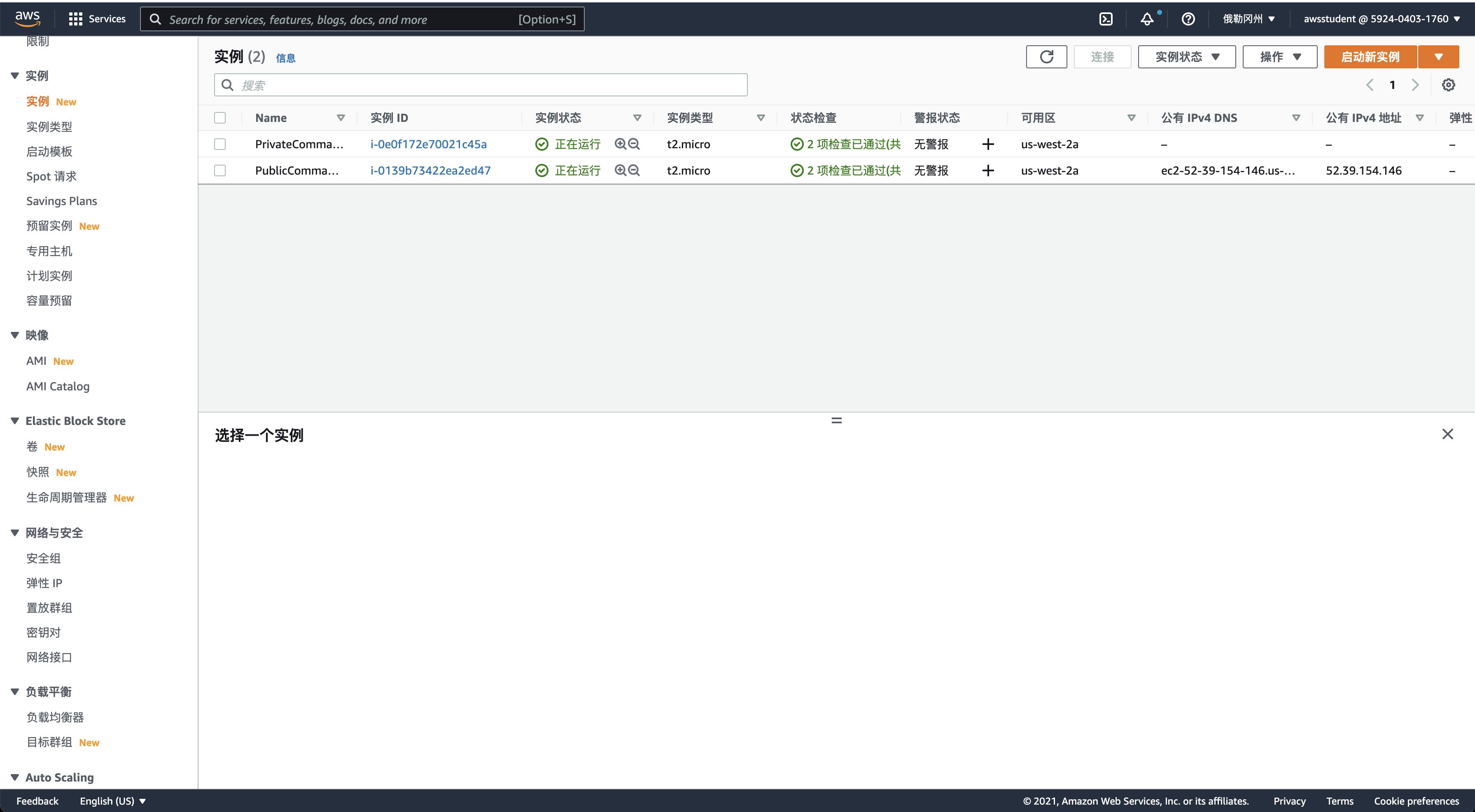
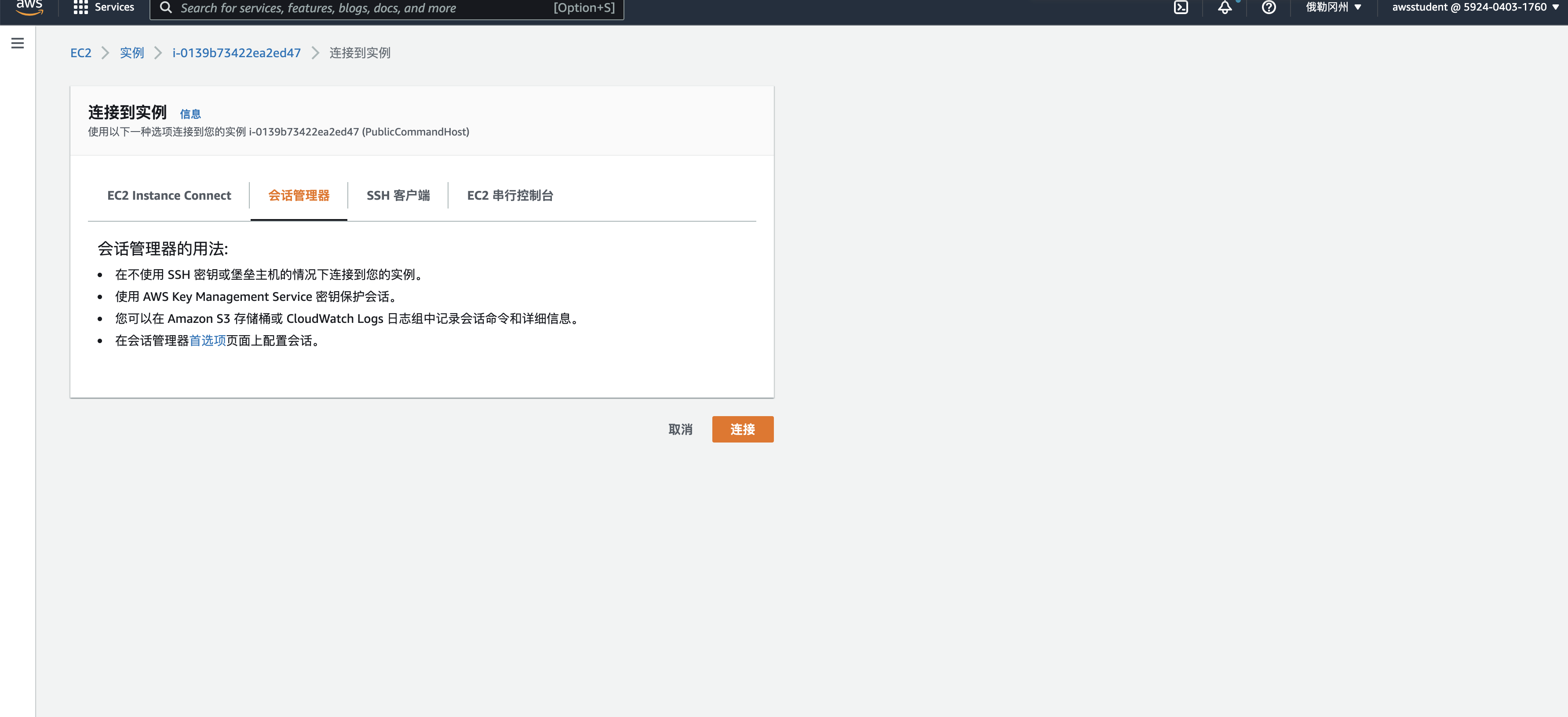
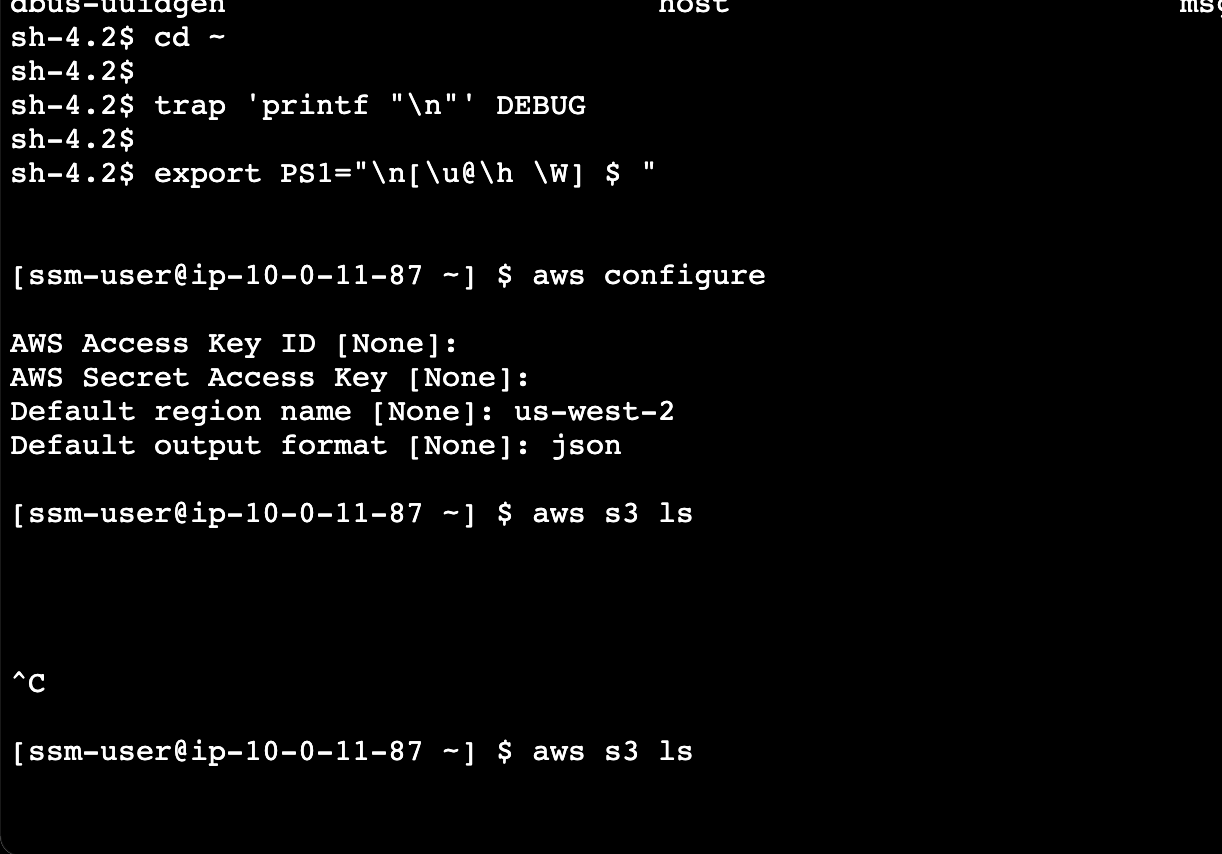
命令行配置
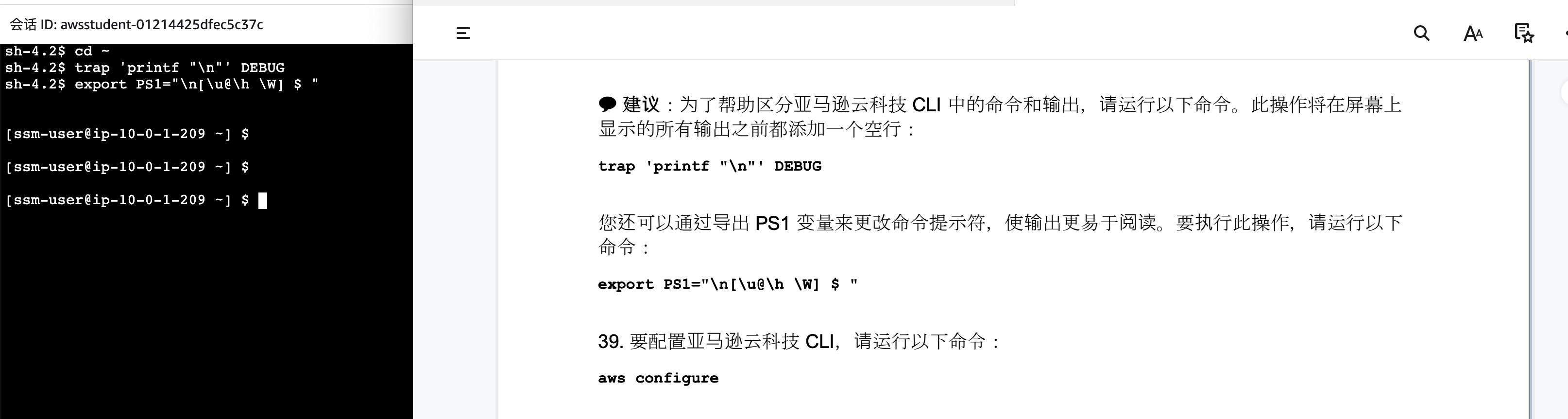
sh-4.2$ cd ~
sh-4.2$ trap 'printf "\n"' DEBUG
sh-4.2$ export PS1="\n[\u@\h \W] $ "
[ssm-user@ip-10-0-1-209 ~] $
[ssm-user@ip-10-0-1-209 ~] $
[ssm-user@ip-10-0-1-209 ~] $
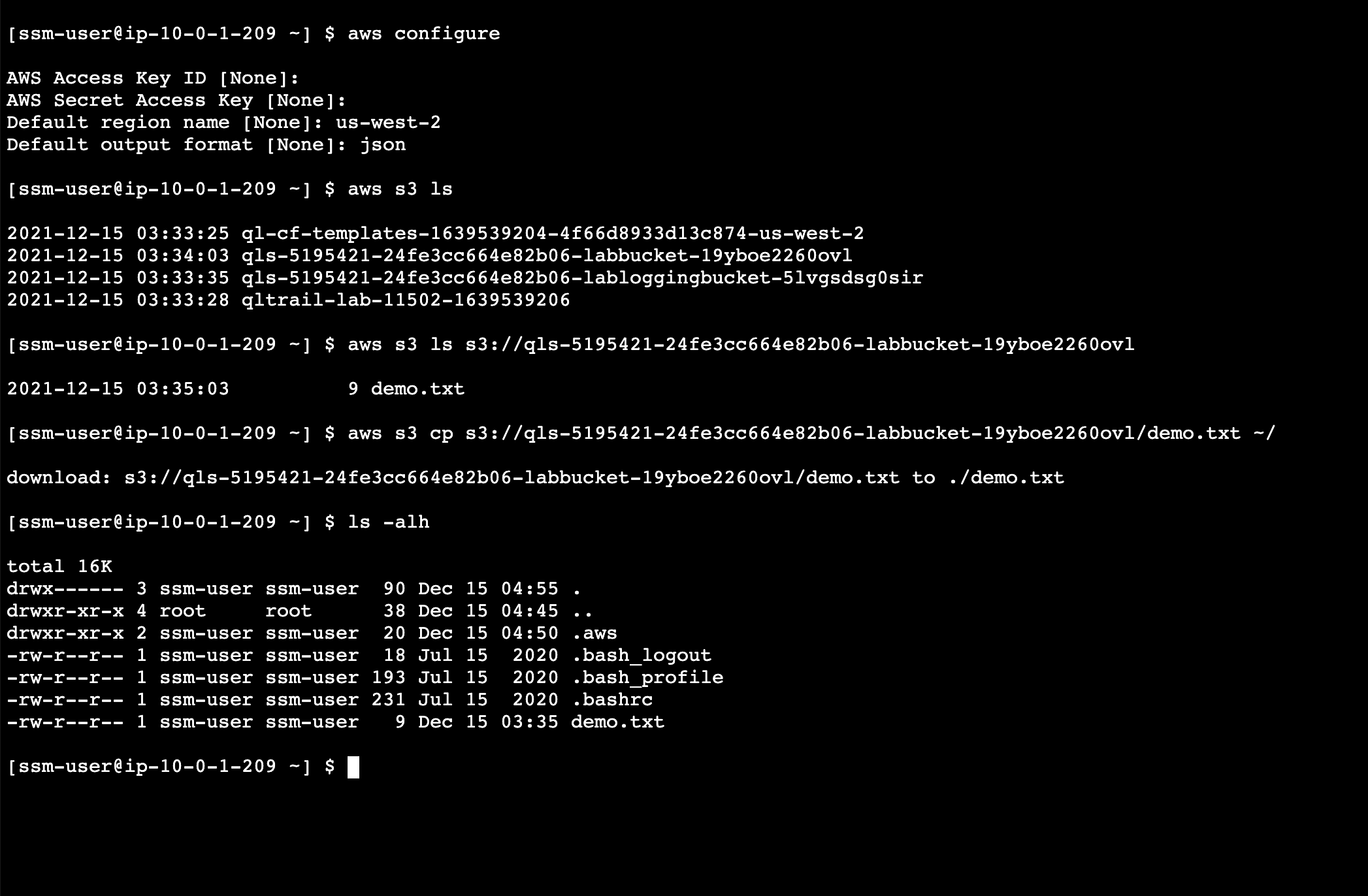
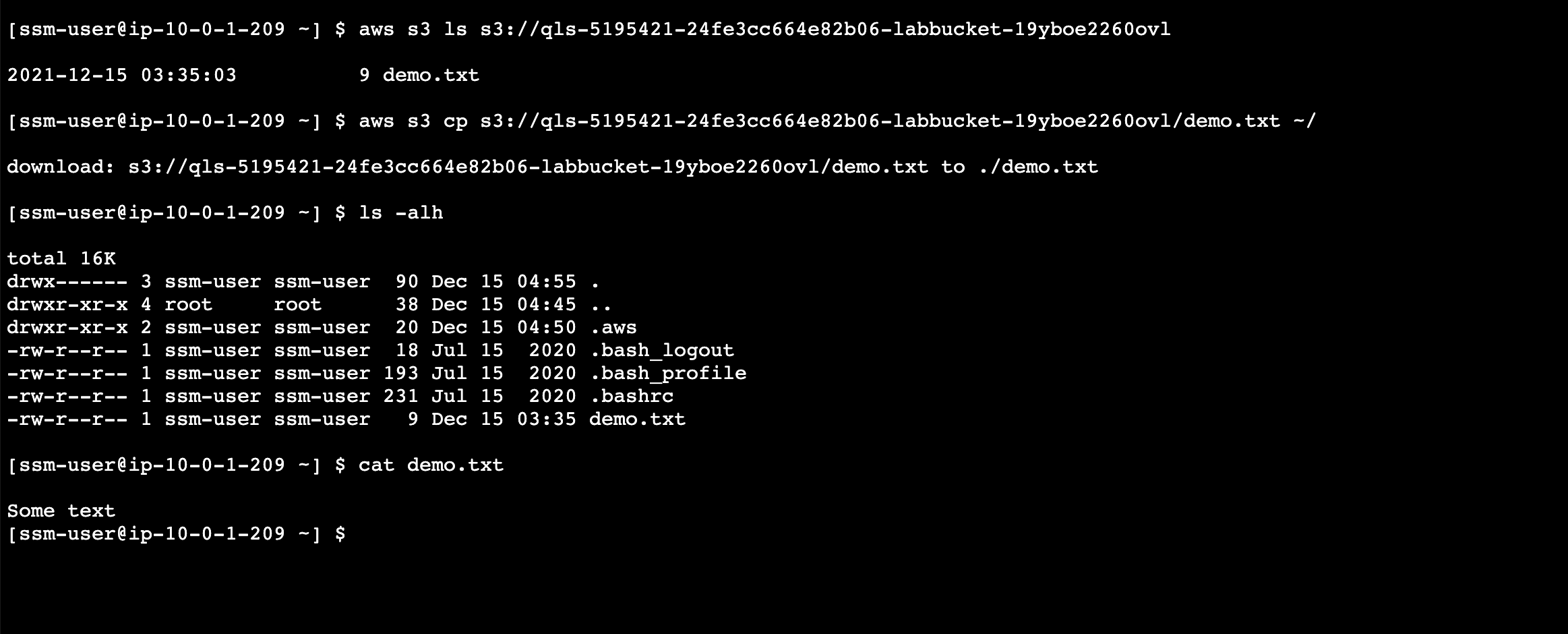
公有子网实例访问
[ssm-user@ip-10-0-1-209 ~] $ aws s3 ls s3://qls-5195421-24fe3cc664e82b06-labbucket-19yboe2260ovl
2021-12-15 03:35:03 9 demo.txt
[ssm-user@ip-10-0-1-209 ~] $

sh-4.2$ aws ec2 describe-vpc-endpoints --query 'VpcEndpoints[*].ServiceName'
[
"com.amazonaws.us-west-2.ec2messages",
"com.amazonaws.us-west-2.cloudformation",
"com.amazonaws.us-west-2.ssmmessages",
"com.amazonaws.us-west-2.ssm"
]
sh-4.2$

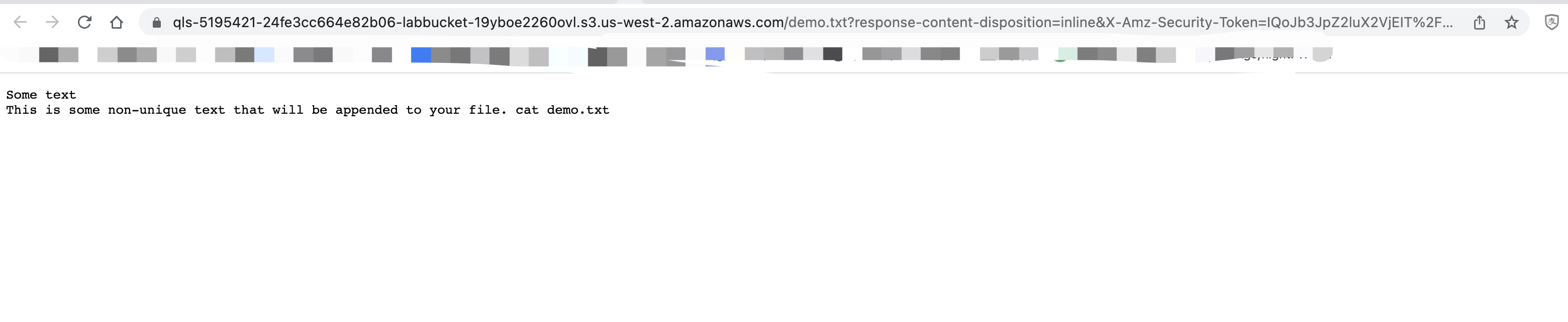
私有子网实例访问s3通过vpc网关节点
[ssm-user@ip-10-0-11-87 ~] $ aws s3 ls
2021-12-15 03:33:25 ql-cf-templates-1639539204-4f66d8933d13c874-us-west-2
2021-12-15 03:34:03 qls-5195421-24fe3cc664e82b06-labbucket-19yboe2260ovl
2021-12-15 03:33:35 qls-5195421-24fe3cc664e82b06-labloggingbucket-5lvgsdsg0sir
2021-12-15 03:33:28 qltrail-lab-11502-1639539206
[ssm-user@ip-10-0-11-87 ~] $
ssm-user@ip-10-0-11-87 ~] $ aws s3 cp s3://qls-5195421-24fe3cc664e82b06-labbucket-19yboe2260ovl/demo.txt ~/
download: s3://qls-5195421-24fe3cc664e82b06-labbucket-19yboe2260ovl/demo.txt to ./demo.txt
[ssm-user@ip-10-0-11-87 ~] $ ls -alh
total 16K
drwx------ 3 ssm-user ssm-user 90 Dec 15 05:43 .
drwxr-xr-x 4 root root 38 Dec 15 05:27 ..
drwxr-xr-x 2 ssm-user ssm-user 20 Dec 15 05:30 .aws
-rw-r--r-- 1 ssm-user ssm-user 18 Jul 15 2020 .bash_logout
-rw-r--r-- 1 ssm-user ssm-user 193 Jul 15 2020 .bash_profile
-rw-r--r-- 1 ssm-user ssm-user 231 Jul 15 2020 .bashrc
-rw-r--r-- 1 ssm-user ssm-user 88 Dec 15 04:57 demo.txt
[ssm-user@ip-10-0-11-87 ~] $
存储访问策略配置
cd ~
cat <<EOT >> policy.json
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": "*",
"Action": "s3:List*",
"Resource": "arn:aws:s3:::*"
},
{
"Effect": "Allow",
"Principal": "*",
"Action": "s3:*",
"Resource": [
"arn:aws:s3:::<LabBucket>",
"arn:aws:s3:::<LabBucket>/*"
]
},
{
"Effect": "Deny",
"Principal": "*",
"Action": "s3:*",
"Resource": [
"arn:aws:s3:::<LabLoggingBucket>",
"arn:aws:s3:::<LabLoggingBucket>/*"
]
}
]
}
EOT
aws ec2 modify-vpc-endpoint --vpc-endpoint-id ${vpcEndpointId} --policy-document file://policy.json
trap 'printf "\n"' DEBUG
export PS1="\n[\u@\h \W] $ "
aws configure
跨账户授权