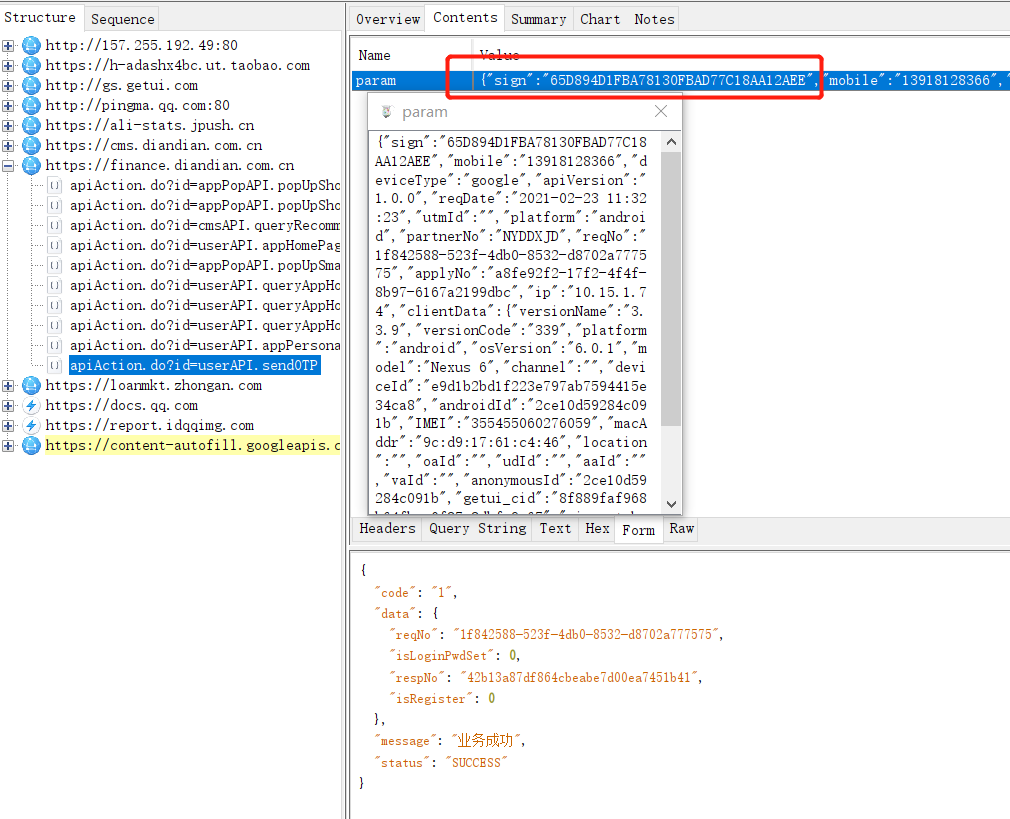
一、抓包分析
app注册入口
二、先脱壳
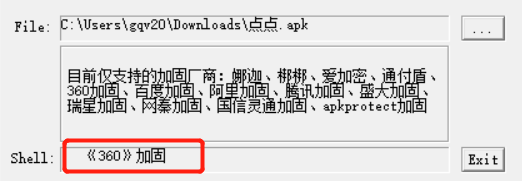
因为有360加固,所以先脱壳
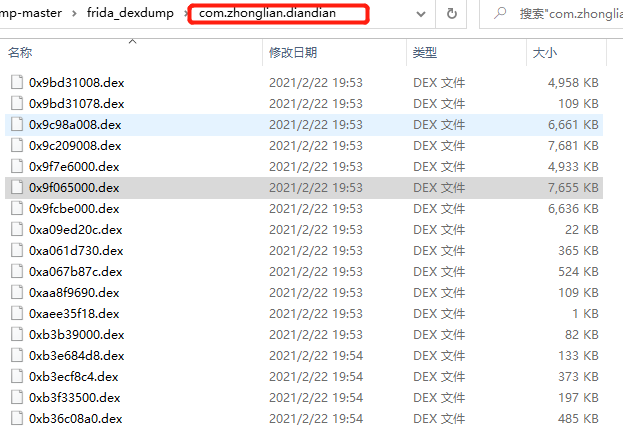
三、用jadx-gui打开
打开0x9f065000.dex
搜索关键字sign
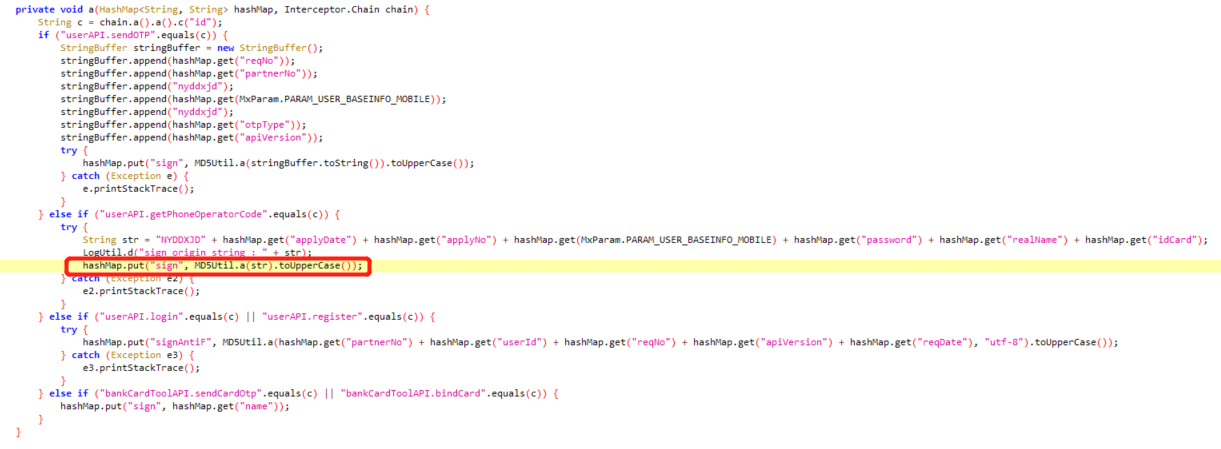
四、hook方法
上frida,hook a
frida脚本如下
hook.js
Java.perform(function () {
console.log('HOOK Start!!!');
var Des3Encrypt = Java.use("com.zhonglian.diandian.utils.MD5Util");
console.log(Des3Encrypt);
// 加密
Des3Encrypt.a.overload('java.lang.String').implementation = function (args1) {
console.log("Encrypt args1:",args1);
//console.log("Encrypt args2:",args2);
//console.log("Encrypt args3:",args3);
//console.log("Encrypt args4:",args4);
var result1 = this.a(args1);
console.log("Des3Encrypt.encode result1==:", result1);
return result1;
};
});
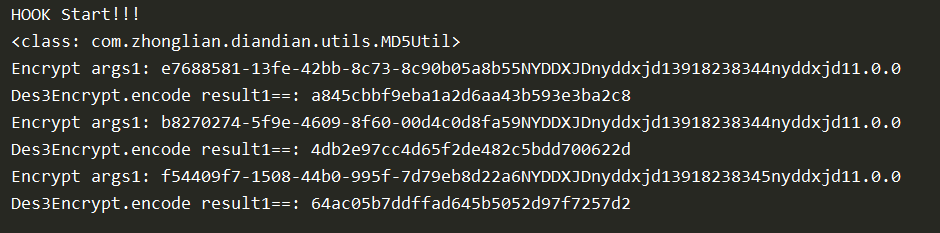
返回结果:
python 脚本
# -*- coding: utf-8 -*-
# @Time : 2021/2/22
# @Author : 点点
import logging
import frida
import sys
logging.basicConfig(level=logging.DEBUG)
def on_message(message, data):
print(message)
with open('hook.js', 'r', encoding='utf-8') as f:
sta = ''.join(f.readlines())
rdev = frida.get_remote_device()
processes = rdev.enumerate_processes() # 安卓手机中的所有进程
# print(processes)
# android.content.Intent android.content.Context android.view.ViewGroup java.lang.String, java.util.List [Ljava.lang.String;(String[]), javax.net.ssl.SSLSession SSLSession
session = rdev.attach("com.zhonglian.diandian")
# print(session)
script = session.create_script(sta)
script.on("message", on_message)
script.load()
sys.stdin.read()
五、请求测试
#!/usr/bin/env python
# -*- coding:utf-8 -*-
# @Time : 2021/2/23
# @Author :
# @Platform:点点
import requests
import json
import time
import uuid
import hashlib
import warnings
warnings.filterwarnings("ignore")
def login_info(phone):
url = 'https://finance.diandian.com.cn/apiAction.do?id=userAPI.sendOTP'
headers = {
"Content-Type": "application/x-www-form-urlencoded",
"Content-Length": "1253",
"Host": "finance.diandian.com.cn",
"Connection": "Keep-Alive",
"Accept-Encoding": "gzip",
"User-Agent": "okhttp/3.11.0"
}
uuid_str1 = str(uuid.uuid4())
# print("uuid_str1=", uuid_str1)
uuid_str2 = str(uuid.uuid4())
# print(uuid_str2)
applyDate = time.strftime("%Y-%m-%d %H:%M:%S", time.localtime())
# print(applyDate)
s = f"{uuid_str1}NYDDXJDnyddxjd{phone}nyddxjd11.0.0"
# s.encode()#变成bytes类型才能加密
m = hashlib.md5(s.encode())
sign = (m.hexdigest()).upper()
# print(sign)
data = {
"param": json.dumps({
"sign": sign,
"mobile": phone,
"deviceType": "google",
"apiVersion": "1.0.0",
"reqDate": applyDate,
"utmId": "",
"platform": "android",
"partnerNo": "NYDDXJD",
"reqNo": uuid_str1,
"applyNo": uuid_str2,
"ip": "10.15.1.74",
"clientData": {
"versionName": "3.3.9",
"versionCode": "339",
"platform": "android",
"osVersion": "6.0.1",
"model": "Nexus 6",
"channel": "",
"deviceId": "e9d1b2bd1f223e797ab7594415e34ca8",
"androidId": "2ce10d59284c091b",
"IMEI": "",
"macAddr": "9c:d9:17:61:c4:46",
"location": "",
"oaId": "",
"udId": "",
"aaId": "",
"vaId": "",
"anonymousId": "2ce10d59284c091b",
"getui_cid": "8f889faf968b64fbcc0f87e8dbfc9c67",
"xinge_token": "23436814981bbc9d45abb302409b231e4caa2367"
},
"anonymousId": "2ce10d59284c091b",
"applyDate": applyDate,
"otpType": "1"
})
}
# print("data=",data)
response = requests.post(url, data=data, headers=headers, verify=False, timeout=10)
dict_data = json.loads(response.text)
print(dict_data)
if __name__ == '__main__':
print(login_info("13966661111"))
样本

链接:https://pan.baidu.com/s/1-UFwIGr_vDh6iSWJLXshqw
提取码:r43q