ingress https
ingress-nginx-controller 对应的版本是V1.0.0
openssl-ingress https
过程参考ingress-nginx/user-guide/tls
生成自签名证书和私钥
openssl req -x509 -nodes -days 3650 -newkey ras:2048 -keyout tls-key.pem -out tls-cert.pem -subj "/CN=mcsastest.com.cn"
生成tls secret
kubectl create secret tls test-tls --cert=tls-cert.pem --key=tls-key.pem
ingress追加配置
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: test-ingress
annotations:
nginx.ingress.kubernetes.io/rewrite-target: /
spec:
ingressClassName: nginx
tls:
- hosts:
- mcsastest.com.cn
secretName: test-tls
rules:
- host: mcsastest.com.cn
http:
paths:
- path: /test1
pathType: Prefix
backend:
service:
name: nginx
port:
number: 80
- 执行完后查看
ingress-controller日志,报错
Unexpected error validating SSL certificate "default/test-tls" for server "mcsastest.com.cn": x509: certificate relies on legacy Common Name field, use SANs instead
个人比较熟悉cfssl,下面采用cfssl生成:
cfssl-ingress https
ca-ingress-config.json
{
"signing": {
"default": {
"expiry": "876000h"
},
"profiles": {
"ingress": {
"usages": [
"server auth",
"client auth"
],
"expiry": "876000h"
}
}
}
}
ca-ingress-csr.json
{
"CN": "ingress",
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "JS",
"L": "NJ",
"O": "ingress",
"OU": "ingress"
}
],
"ca": {
"expiry": "876000h"
}
}
生成根证书
cfssl gencert -initca ca-ingress-csr.json | cfssljson -bare ca-ingress
ingress-csr.json
{
"CN": "mcsastest.com.cn",
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "JS",
"L": "NJ",
"O": "falcon",
"OU": "nginx.test"
}
]
}
生成ingress 用证书
cfssl gencert \
-ca=ca-ingress.pem \
-ca-key=ca-ingress-key.pem \
-config=ca-ingress-config.json \
-hostname=192.168.0.110,localhost,mcsastest.com.cn \
-profile=ingress ingress-csr.json | cfssljson -bare tls
生成tls secret
kubectl create secret tls test-tls --cert=tls.pem --key=tls-key.pem
查看生成的证书
cfssl-certinfo -cert=tls.pem
{
"subject": {
"common_name": "mcsastest.com.cn",
"country": "CN",
"organization": "falcon",
"organizational_unit": "nginx.test",
"locality": "NJ",
"province": "JS",
"names": [
"CN",
"JS",
"NJ",
"falcon",
"nginx.test",
"mcsastest.com.cn"
]
},
"issuer": {
"common_name": "ingress",
"country": "CN",
"organization": "falcon",
"organizational_unit": "falcon",
"locality": "NJ",
"province": "JS",
"names": [
"CN",
"JS",
"NJ",
"falcon",
"falcon",
"ingress"
]
},
"serial_number": "129893924529548302690018454605660077012693905699",
"sans": [
"localhost",
"mcsastest.com.cn",
"192.168.0.110"
],
"not_before": "2021-11-18T01:52:00Z",
"not_after": "2121-10-25T01:52:00Z",
"sigalg": "SHA256WithRSA",
"authority_key_id": "55:08:29:3D:EC:7E:2F:DE:BA:B6:C6:CB:12:14:D9:C3:36:8A:A0:9B",
"subject_key_id": "A1:FF:92:52:43:AC:27:52:5C:11:5C:2E:2D:37:BA:2A:0E:1C:54:79",
"pem": "-----BEGIN CERTIFICATE-----\nMIID8jCCAtqgAwIBAgIUFsClIDn/RwEtRQxuhcl2tUMZcSMwDQYJKoZIhvcNAQEL\nBQAwWzELMAkGA1UEBhMCQ04xCzAJBgNVBAgTAkpTMQswCQYDVQQHEwJOSjEPMA0G\nA1UEChMGZmFsY29uMQ8wDQYDVQQLEwZmYWxjb24xEDAOBgNVBAMTB2luZ3Jlc3Mw\nIBcNMjExMTE4MDE1MjAwWhgPMjEyMTEwMjUwMTUyMDBaMGgxCzAJBgNVBAYTAkNO\nMQswCQYDVQQIEwJKUzELMAkGA1UEBxMCTkoxDzANBgNVBAoTBmZhbGNvbjETMBEG\nA1UECxMKbmdpbngudGVzdDEZMBcGA1UEAxMQbWNzYXN0ZXN0LmNvbS5jbjCCASIw\nDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAMHOiTnzBe4KIuMecu4UFzLMLGZt\nF5Y2Kwc83duunxTomPOqRjly+LlOApz80vEJtm4jHrtSV0sUdCOG049ECqhoKusd\nnR0UADcqZh/EGsTb82x6BcamPXWezVGSq37jAv0m42uLmg0DQ223SNRkt367x3cA\n32rLa2/UPsrQGrEc+n5gEwds+wVH+kYLjS0uNvZqSZedrDUYQ33G09QykXsP4vo7\n6KZp81U/qR25Vfq4s6Eq84s+0o2bB/Z8koFTF4hgil37/e3Jtoqk5xxn66nxMyqk\nGqbWulVohKcNVg8kn+iH7DbiaReZwb3jq+m5BuJlLW9tAHaG0Uzdra8BQJcCAwEA\nAaOBnjCBmzAdBgNVHSUEFjAUBggrBgEFBQcDAQYIKwYBBQUHAwIwDAYDVR0TAQH/\nBAIwADAdBgNVHQ4EFgQUof+SUkOsJ1JcEVwuLTe6Kg4cVHkwHwYDVR0jBBgwFoAU\nVQgpPex+L966tsbLEhTZwzaKoJswLAYDVR0RBCUwI4IJbG9jYWxob3N0ghBtY3Nh\nc3Rlc3QuY29tLmNuhwQKkA/xMA0GCSqGSIb3DQEBCwUAA4IBAQCndNrtJSYTij8f\nc5osVLmefIa+aKN3FqUtndAQrvemwAzG3DN2BEpTKtniC1LcCqO1QUTkxHUOyPvr\nW//FA48J7L1eZcaK8c4wUaanKbq04Te9M9aKvYoJaXiz3/iI+Axn0H9rtKuXTUXa\nLbWTM6FA2AJ0dBL54Mjk/I3kgs1okVveBauu+giFryL+OjgIb66PgpSSn0A4UoOF\ns5m6oMsoYll/N0SHSyE/L8/4UkJ6TAmrlU1kS5A0AdDEPl10hv3v3IDJaQ3XYYat\nFxTRJ7x5MEhitYsTSlHe3dq47+RyQMm2OYlABcFjenXKES+NhzUo01tApLXhEO3b\nErh0qXVF\n-----END CERTIFICATE-----\n"
}
- 生成的证书中有了
sans属性
生成tls secret
kubectl create secret tls test-tls --cert=tls-cert.pem --key=tls-key.pem
ingress追加配置
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: test-ingress
annotations:
nginx.ingress.kubernetes.io/rewrite-target: /
spec:
ingressClassName: nginx
tls:
- hosts:
- mcsastest.com.cn
secretName: test-tls
rules:
- host: mcsastest.com.cn
http:
paths:
- path: /test1
pathType: Prefix
backend:
service:
name: nginx
port:
number: 80
重新启动后,ssl配置正确
I1118 06:09:31.150376 7 backend_ssl.go:66] "Adding secret to local store" name="default/test-tls"
I1118 06:09:31.150718 7 controller.go:150] "Configuration changes detected, backend reload required"
I1118 06:09:31.219582 7 controller.go:167] "Backend successfully reloaded"
I1118 06:09:31.219870 7 event.go:282] Event(v1.ObjectReference{Kind:"Pod", Namespace:"ingress-nginx", Name:"ingress-nginx-controller-55f74b4f85-w72hf", UID:"73fe36ea-aec2-4039-bc1a-77de84181298", APIVersion:"v1", ResourceVersion:"8003802", FieldPath:""}): type: 'Normal' reason: 'RELOAD' NGINX reload triggered due to a change in configuration
I1118 06:09:45.762996 7 status.go:284] "updating Ingress status" namespace="default" ingress="test-ingress" currentValue=[] newValue=[{IP:192.168.0.110 Hostname: Ports:[]}]
I1118 06:09:45.769930 7 event.go:282] Event(v1.ObjectReference{Kind:"Ingress", Namespace:"default", Name:"test-ingress", UID:"341bc44c-440b-4d5d-ae7a-4714e6c81725", APIVersion:"networking.k8s.io/v1", ResourceVersion:"8035260", FieldPath:""}): type: 'Normal' reason: 'Sync' Scheduled for sync
访问
未导入ca时浏览器访问
新版本的chrome,在ca没有被信任前不允许再访问
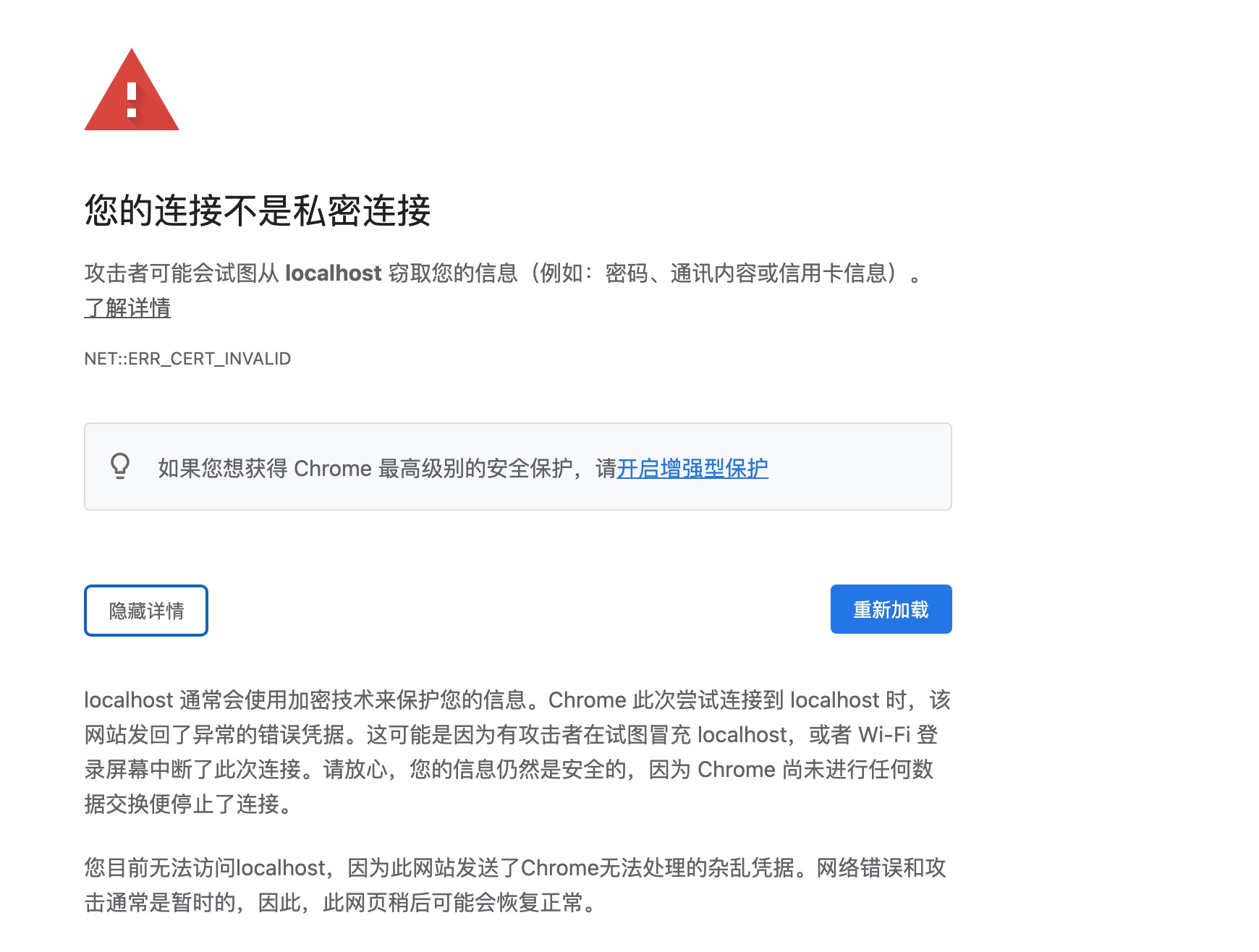
浏览器导入证书(mac下操作,在钥匙串中追加证书)

- 选择【登录】,菜单项中点击【文件】->【导入项目】
- 直接导入的【ca】,这样,用这个ca签名的其他证书也会被浏览器信任
- 双击导入的【ca】,将信任修改成【始终信任】
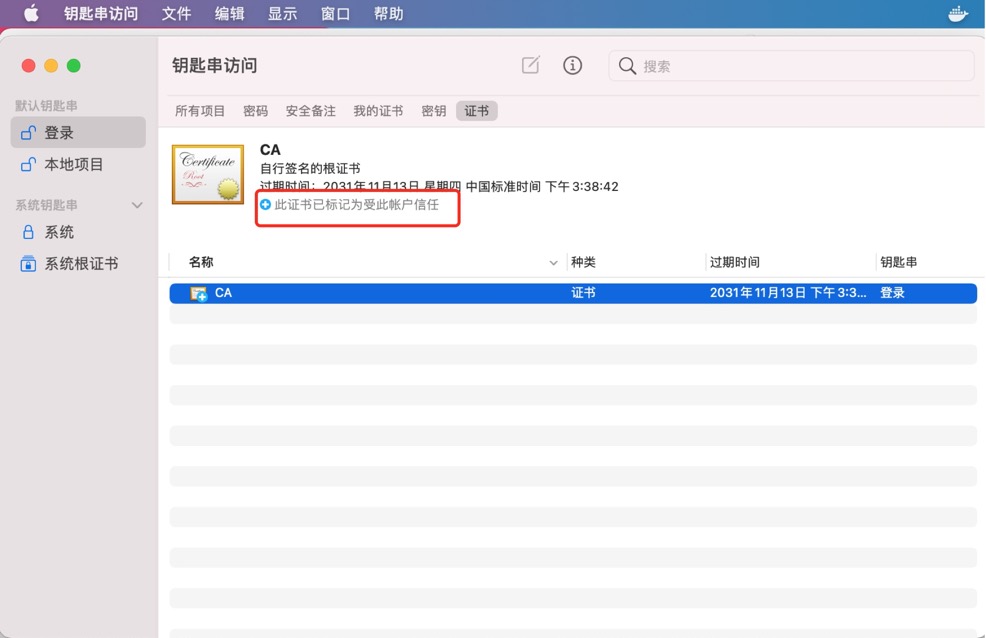
再次浏览器访问

问题
执行curl出现下面的错
ssl received a record that exceeded the maximum permissible length
经过检查,发现是用https访问了ingress-controller对应service的http端口30371造成的,换成31534就正常了
ingress-nginx-controller NodePort 10.97.51.229 <none> 80:30371/TCP,443:31534/TCP 3h25m