采用Linux自带的OPENSSL进行证书的生成工作
- 准备阶段
以root登录,同时在el01gbcn01上完成
|
[oracle@el01gbcn01]# which java /u01/FMW/weblogic/jdk1.7.0/bin/java [oracle@el01gbcn01]# dir sslcert [oracle@el01gbcn01]$ cd sslcert [oracle@el01gbcn01]$ mkdir certs private [oracle@el01gbcn01]$ echo '100001' >serial [oracle@el01gbcn01]$ touch certindex.txt [oracle@el01gbcn01]$ touch openssl.cnf |

将下面文本粘贴如openssl.cnf
|
# # OpenSSL configuration file # # Working directory dir = . [ ca ] default_ca = CA_default [ CA_default ] serial = $dir/serial database = $dir/certindex.txt new_certs_dir = $dir/certs certificate = $dir/cacert.pem private_key = $dir/private/cakey.pem default_days = 365 default_md = sha1 preserve = no email_in_dn = no nameopt = default_ca certopt = default_ca policy = policy_match [ policy_match ] countryName = match stateOrProvinceName = match organizationName = match organizationalUnitName = optional commonName = supplied emailAddress = optional [ req ] default_bits = 2048 # Size of keys default_keyfile = key.pem # name of generated keys default_md = sha1 # message digest algorithm string_mask = nombstr # permitted characters distinguished_name = req_distinguished_name req_extensions = v3_req [ req_distinguished_name ] # Variable name Prompt string #------------------------- ---------------------------------- 0.organizationName = Organization Name (company) organizationalUnitName = Organizational Unit Name (department, division) emailAddress = Email Address emailAddress_max = 40 localityName = Locality Name (city, district) stateOrProvinceName = State or Province Name (full name) countryName = Country Name (2 letter code) countryName_min = 2 countryName_max = 2 commonName = Common Name (hostname, IP, or your name) commonName_max = 64 # Default values for the above, for consistency and less typing. # Variable name Value #------------------------ ------------------------------ 0.organizationName_default = My Company organizationalUnitName_default = My Org emailAddress_default = demo@sample.com localityName_default = My Town stateOrProvinceName_default = My Providence countryName_default = CN [ v3_ca ] basicConstraints = CA:TRUE subjectKeyIdentifier = hash authorityKeyIdentifier = keyid:always,issuer:always [ v3_req ] basicConstraints = CA:FALSE subjectKeyIdentifier = hash [ my_v3_ext ] basicConstraints = CA:true [ policy_anything ] countryName = optional stateOrProvinceName = optional localityName = optional organizationName = optional organizationalUnitName = optional commonName = supplied emailAddress = optional |
-
生成guilin bank CA Root根证书
有效期10年
|
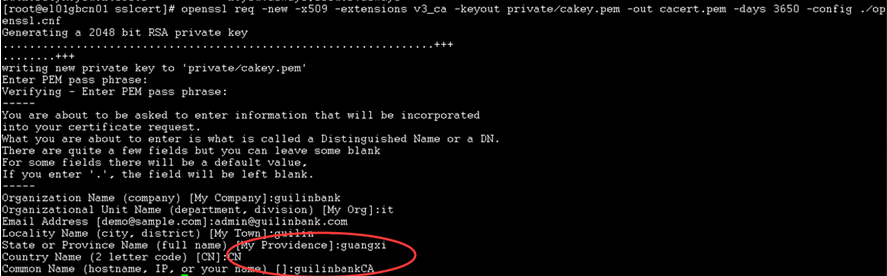
openssl req -new -x509 -extensions v3_ca -keyout private/cakey.pem -out cacert.pem -days 3650 -config ./openssl.cnf |
密码为password1
输入信息如下:
-
生成guilinBank CA 二级证书
|
openssl req -new -nodes -out GCSLevel2CA-req.pem -keyout private/GCSLevel2CA-key.pem -pubkey -days 3650 -config ./openssl.cnf |

-
对二级证书进行签名
|
openssl ca -extensions my_v3_ext -out GCSLevel2CA-cert.pem -days 3650 -config ./openssl.cnf -infiles GCSLevel2CA-req.pem |

-
生成服务器请求证书
对*.guilinbank.com.cn的主机都有效, 可用于WebLogic, OTD VIP等
|
keytool -genkey -dname "cn=*.guilinbank.com.cn, ou=it, o=guilinbank, c=CN" -keyalg RSA -keysize 2048 -alias mykey -keypass password1 -keystore mykeystore.jks -storepass password1 -validity 3650 |
|
keytool -certreq -alias mykey -file mykey-req.pem -keypass password1 -storetype JKS -keystore mykeystore.jks -storepass password1 |

用ll察看一下当前目录,已经有的文件包括
total 48
-rw-rw-r-- 1 oracle oracle 954 Sep 27 22:04 mykey-req.pem <-- 应用证书请求文件
-rw-rw-r-- 1 oracle oracle 1606 Sep 27 21:59 cacert.pem <-- 根证书
-rw-rw-r-- 1 oracle oracle 82 Sep 27 22:02 certindex.txt
-rw-rw-r-- 1 oracle oracle 21 Sep 27 22:02 certindex.txt.attr
-rw-rw-r-- 1 oracle oracle 0 Sep 27 21:57 certindex.txt.old
drwxrwxr-x 2 oracle oracle 4096 Sep 27 22:02 certs
-rw-rw-r-- 1 oracle oracle 4055 Sep 27 22:02 GCSLevel2CA-cert.pem <-- 二级证书
-rw-rw-r-- 1 oracle oracle 1582 Sep 27 22:02 GCSLevel2CA-req.pem <-- 二级证书请求文件
-rw-rw-r-- 1 oracle oracle 2117 Sep 27 22:04 mykeystore.jks <-- Java Keystore
-rw-rw-r-- 1 oracle oracle 3057 Sep 27 21:58 openssl.cnf <-- OpenSSL 配置文件
drwxrwxr-x 2 oracle oracle 4096 Sep 27 22:01 private
-rw-rw-r-- 1 oracle oracle 7 Sep 27 22:02 serial
-rw-rw-r-- 1 oracle oracle 7 Sep 27 21:57 serial.old
-
使用二级证书对应用请求文件进行签名
|
openssl ca -policy policy_anything -keyfile private/GCSLevel2CA-key.pem -cert GCSLevel2CA-cert.pem -days 3650 -config ./openssl.cnf -out mykey.pem -infiles mykey-req.pem |

-
生成应用证书链
|
openssl crl2pkcs7 -nocrl -certfile mykey.pem -certfile GCSLevel2CA-cert.pem -certfile cacert.pem -outform PEM -out mykey.p7b |

-
将应用证书链导入Jks证书库
|
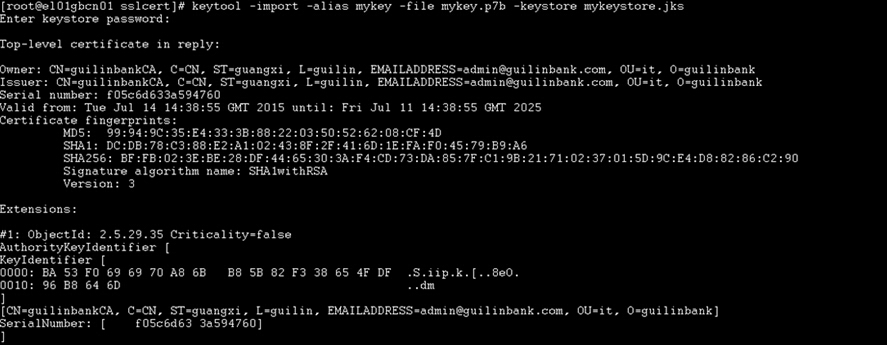
keytool -import -alias mykey -file mykey.p7b -keystore mykeystore.jks |
|
[root@el01gbcn01 sslcert]# keytool -list -keystore mykeystore.jks -storepass password1 -v Keystore type: JKS Keystore provider: SUN Your keystore contains 1 entry Alias name: mykey Creation date: Jul 14, 2015 Entry type: PrivateKeyEntry Certificate chain length: 3 Certificate[1]: Owner: CN=*.guilinbank.com.cn, OU=it, O=guilinbank, C=CN Issuer: CN=guilinbankLevel2CA, OU=it, O=guilinbank, ST=guangxi, C=CN Serial number: 100002 Valid from: Tue Jul 14 14:44:14 GMT 2015 until: Fri Jul 11 14:44:14 GMT 2025 Certificate fingerprints: MD5: C4:D7:9D:1C:E1:E3:64:26:4A:23:50:2B:02:58:3E:37 SHA1: AC:F3:3E:00:B4:96:8D:4D:3E:29:FA:B1:57:43:9A:31:C2:74:2A:D8 SHA256: B3:DC:96:34:75:83:03:76:91:12:80:5E:FE:78:1D:7A:5D:33:C2:27:6A:9E:BE:E7:BE:BF:B5:B2:9E:64:6C:DC Signature algorithm name: SHA1withRSA Version: 1 Certificate[2]: Owner: CN=guilinbankLevel2CA, OU=it, O=guilinbank, ST=guangxi, C=CN Issuer: CN=guilinbankCA, C=CN, ST=guangxi, L=guilin, EMAILADDRESS=admin@guilinbank.com, OU=it, O=guilinbank Serial number: 100001 Valid from: Tue Jul 14 14:40:53 GMT 2015 until: Fri Jul 11 14:40:53 GMT 2025 Certificate fingerprints: MD5: 76:2A:F3:2A:69:1A:3B:69:A7:81:AC:66:8D:FE:67:FD SHA1: 6D:A3:72:84:5D:76:12:02:35:37:B6:94:BA:36:00:AC:35:23:7C:F0 SHA256: 6D:66:0C:64:C6:45:5B:67:21:E6:4B:B7:3F:F9:63:54:4D:9D:12:F2:80:67:C4:35:D0:59:E6:70:98:02:F3:0D Signature algorithm name: SHA1withRSA Version: 3 Extensions: #1: ObjectId: 2.5.29.19 Criticality=false BasicConstraints:[ CA:true PathLen:2147483647 ] Certificate[3]: Owner: CN=guilinbankCA, C=CN, ST=guangxi, L=guilin, EMAILADDRESS=admin@guilinbank.com, OU=it, O=guilinbank Issuer: CN=guilinbankCA, C=CN, ST=guangxi, L=guilin, EMAILADDRESS=admin@guilinbank.com, OU=it, O=guilinbank Serial number: f05c6d633a594760 Valid from: Tue Jul 14 14:38:55 GMT 2015 until: Fri Jul 11 14:38:55 GMT 2025 Certificate fingerprints: MD5: 99:94:9C:35:E4:33:3B:88:22:03:50:52:62:08:CF:4D SHA1: DC:DB:78:C3:88:E2:A1:02:43:8F:2F:41:6D:1E:FA:F0:45:79:B9:A6 SHA256: BF:FB:02:3E:BE:28:DF:44:65:30:3A:F4:CD:73:DA:85:7F:C1:9B:21:71:02:37:01:5D:9C:E4:D8:82:86:C2:90 Signature algorithm name: SHA1withRSA Version: 3 Extensions: #1: ObjectId: 2.5.29.35 Criticality=false AuthorityKeyIdentifier [ KeyIdentifier [ 0000: BA 53 F0 69 69 70 A8 6B B8 5B 82 F3 38 65 4F DF .S.iip.k.[..8eO. 0010: 96 B8 64 6D ..dm ] [CN=guilinbankCA, C=CN, ST=guangxi, L=guilin, EMAILADDRESS=admin@guilinbank.com, OU=it, O=guilinbank] SerialNumber: [ f05c6d63 3a594760] ] #2: ObjectId: 2.5.29.19 Criticality=false BasicConstraints:[ CA:true PathLen:2147483647 ] #3: ObjectId: 2.5.29.14 Criticality=false SubjectKeyIdentifier [ KeyIdentifier [ 0000: BA 53 F0 69 69 70 A8 6B B8 5B 82 F3 38 65 4F DF .S.iip.k.[..8eO. 0010: 96 B8 64 6D ..dm ] ] ******************************************* ******************************************* |
至此生成mykeystore.jks证书完毕
-
配置weblogic使用证书
登录weblogic server管理控制台,选择服务器Server1,选择配置,秘要库,选择更改

选择定制标示和java标准信任

输入mykeystore.jks的具体地址,为保证访问权限,需要将文件拷贝到/u01/sampleapp/application下并且修改owner为weblogic
选择类型为JKS
输入密码password1

选择SSL选项卡,然后输入别名和密码,保存
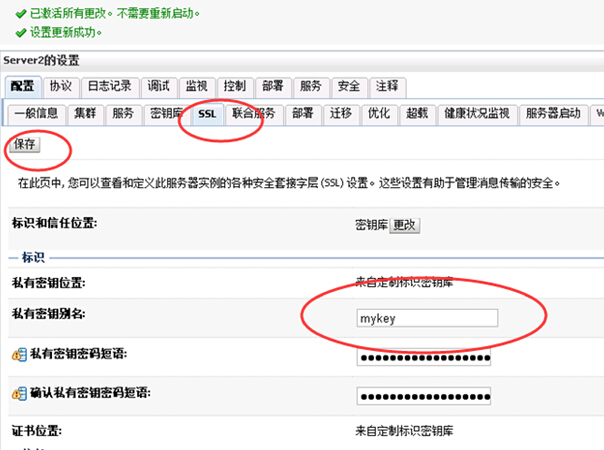
最后启用SSL端口7002

Server1配置完成,同样完成Server2
Weblogic Server SSL配置完成,验证