场景: 传输数据安全
缺点: 若被中间人 同时模拟客户端 和服务器 则无法防止
这个缺点需要CA签名证书
http://www.ruanyifeng.com/blog/2011/08/what_is_a_digital_signature.html
https://blog.csdn.net/wangtaomtk/article/details/80917081
1生成密钥,CA签名证书, 利用openssl
[root@izwz97j0sus9exlvpgweqpz ~]# openssl version OpenSSL 1.0.2k-fips 26 Jan 2017
生成密钥前确认环境
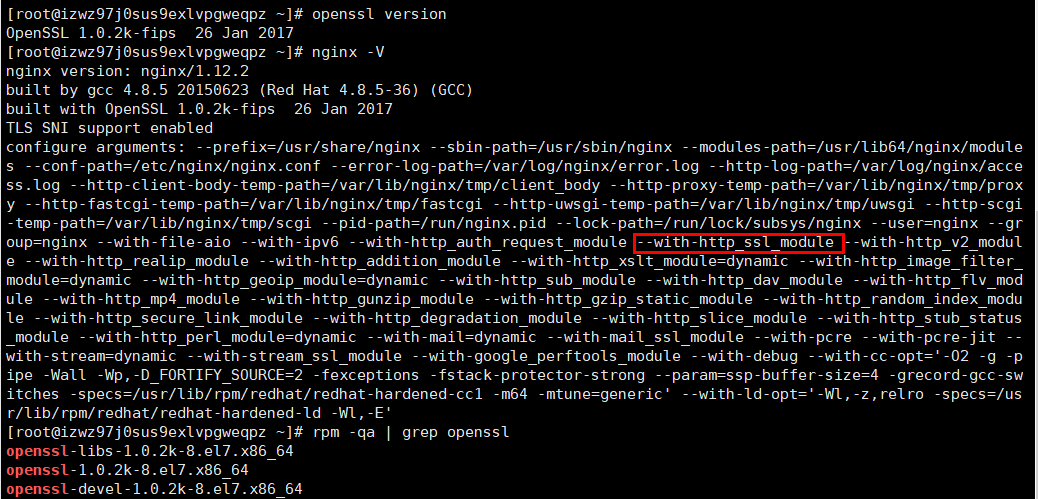
1: 生成密钥
openssl genrsa -idea -out guo.key 1024
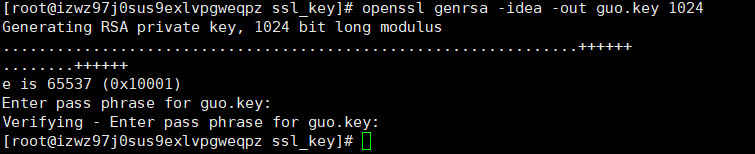
2: 生成证书签名请求文件(crs文件)
openssl req -new -key guo.key -out guo.csr
3: 生成证书签名(CA文件)
把这2个guo.csr guo.key给签名机构, 不过这里得自己CA
openssl x509 -req -days 3650 -in guo.csr -signkey guo.key -out guo.crt
-days 3650 不填默认也就1个月.

此时CA已经完成
2 配置语法 核心
打开ssl on
Syntax: ssl on | of
Default: ssl off
Context:http, server
证书文件
Syntax: ssl_certificate file
Default:---
Context:http, server
证书密码文件
Syntax: ssl_certificate_key file
Default: ---
Context:http, server
参考地址 阿里云Nginx Https配置
https://blog.csdn.net/qq_40917843/article/details/81215325
upstream imserver { server 127.0.0.1:8300; #Apache } server { listen 443 ssl; server_name www.bob3.top; ssl on; ssl_certificate /root/ssl/bob3.top.pem; ssl_certificate_key /root/ssl/bob3.top.key; ssl_session_timeout 5m; ssl_ciphers ECDHE-RSA-AES128-GCM-SHA256:ECDHE:ECDH:AES:HIGH:!NULL:!aNULL:!MD5:!ADH:!RC4; ssl_protocols TLSv1 TLSv1.1 TLSv1.2; ssl_prefer_server_ciphers on; #root html; #index index.html index.htm index.php; ## send request back to im server ## location /im { proxy_pass http://imserver; } location /route { proxy_pass http://imserver; } location /api { proxy_pass http://imserver; } location /doc { proxy_pass https://wildfirechat.github.io/docs/; } }