exe文件,运行后闪退,peid查一下,发现是是c#写的
Reflector打开 找到Main:
private static void Main(string[] args) { string hostname = "127.0.0.1"; int port = 0x7a69; TcpClient client = new TcpClient(); try { Console.WriteLine("Connecting..."); client.Connect(hostname, port); } catch (Exception) { Console.WriteLine("Cannot connect!\nFail!"); return; } Socket socket = client.Client; string str2 = "Super Secret Key"; string text = read(); socket.Send(Encoding.ASCII.GetBytes("CTF{")); foreach (char ch in str2) { socket.Send(Encoding.ASCII.GetBytes(search(ch, text))); } socket.Send(Encoding.ASCII.GetBytes("}")); socket.Close(); client.Close(); Console.WriteLine("Success!"); } 31337 0x7a69private static void Main(string[] args) { string hostname = "127.0.0.1"; int port = 0x7a69; TcpClient client = new TcpClient(); try { Console.WriteLine("Connecting..."); client.Connect(hostname, port); } catch (Exception) { Console.WriteLine("Cannot connect!\nFail!"); return; } Socket socket = client.Client; string str2 = "Super Secret Key"; string text = read(); socket.Send(Encoding.ASCII.GetBytes("CTF{")); foreach (char ch in str2) { socket.Send(Encoding.ASCII.GetBytes(search(ch, text))); } socket.Send(Encoding.ASCII.GetBytes("}")); socket.Close(); client.Close(); Console.WriteLine("Success!"); }
可以看出来 是通过31337( 0x7a69 )端口向127.0.0.1通信
传输的内容是search()函数的返回值,原本我的想法是分析search函数
private static string search(char x, string text) { int length = text.Length; for (int i = 0; i < length; i++) { if (x == text[i]) { int num3 = (i * 0x539) % 0x100; return Convert.ToString(num3, 0x10).PadLeft(2, '0'); } } return "??"; }
但是发现text这个字符串不知道,返回去寻找text:
发现: string text = read();
private static string read() { string[] strArray = Process.GetCurrentProcess().MainModule.FileName.Split(new char[] { '\\' }); string path = strArray[strArray.Length - 1]; using (StreamReader reader = new StreamReader(path)) { return reader.ReadToEnd(); } }
但是对于这个read函数的定义我还是有搞不明白的地方,它定义了一个输入的数组,但是根据我贫弱的(等于0)C#语法知识还是看不明白
但是!如果直接监听程序与本机的通讯过程不就好了吗!
脚本送上(python3):
import http.server server_address = ('127.0.0.1', 31337) handler_class = http.server.BaseHTTPRequestHandler httpd = http.server.HTTPServer(server_address, handler_class) httpd.serve_forever()
BaseHTTPRequestHandler是继承SocketServer.StreamRequestHandler,对http连接的请求作出应答
http_server.serve_forever()是循环监听请求的
运行这个脚本后再运行exe文件就好了:
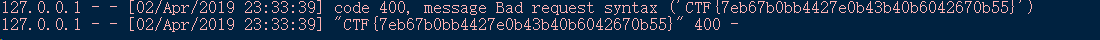
emmmm好像是一段报错 但是不管怎么说flag还是出来了呀(逃)