https://www.cnblogs.com/qq952693358/p/6092199.html
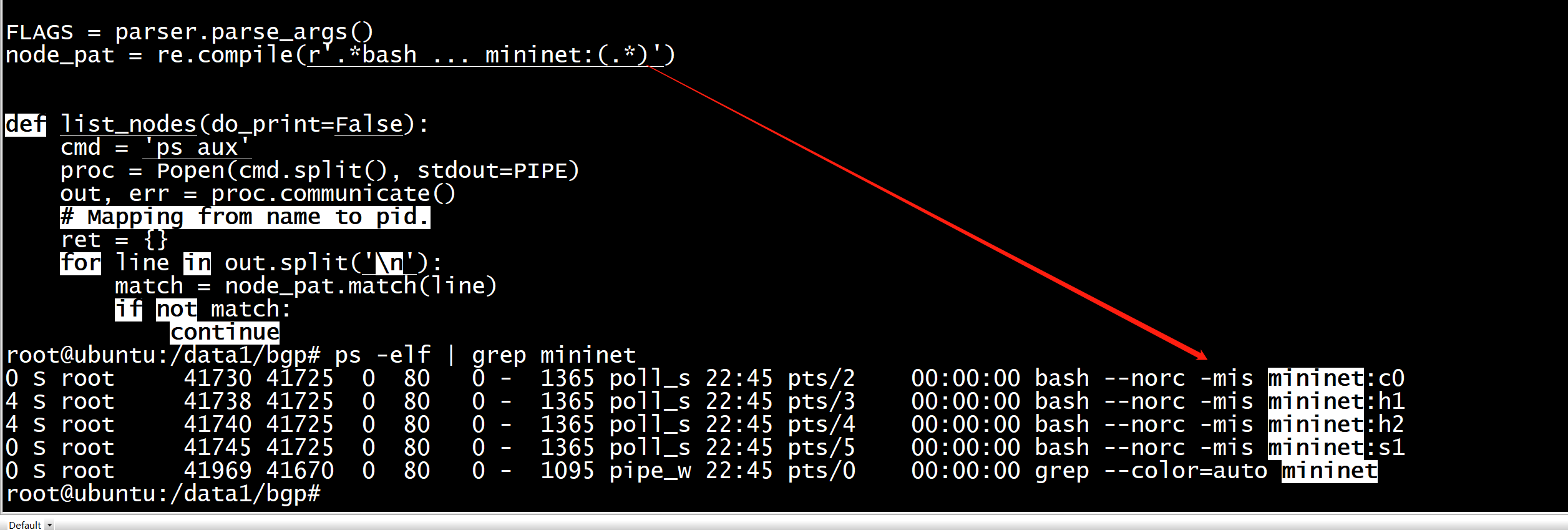
node_pat = re.compile(r'.*bash ... mininet:(.*)')
改成
node_pat = re.compile(r'.*bash --norc -mis mininet:(.*)')
root@ubuntu:/data1/bgp# ls /etc/quagga/ root@ubuntu:/data1/bgp# touch /etc/quagga/daemons root@ubuntu:/data1/bgp# vim /etc/quagga/daemons zebra=yes bgpd=yes ospfd=no ospf6d=no ripd=no ripngd=no isisd=no babeld=no ~
root@ubuntu:/etc/quagga# chown -R quagga:quagga /etc/quagga root@ubuntu:/etc/quagga# zebra root@ubuntu:/etc/quagga# ps -elf | grep zebra 0 S root 43367 43329 0 80 0 - 1095 pipe_w 23:07 pts/6 00:00:00 grep --color=auto zebra root@ubuntu:/etc/quagga#
root@ubuntu:/etc/quagga# mkdir -p /var/run/quagga root@ubuntu:/etc/quagga# chown quagga:quagga /var/run/quagga
root@ubuntu:/etc/quagga# systemctl enable zebra root@ubuntu:/etc/quagga# systemctl restart zebra Job for zebra.service failed because the control process exited with error code. See "systemctl status zebra.service" and "journalctl -xe" for details. root@ubuntu:/etc/quagga#
Aug 06 23:12:42 ubuntu systemd[43522]: zebra.service: Failed to attach to cgroup /system.slice/zebra.service: No s Aug 06 23:12:42 ubuntu systemd[43522]: zebra.service: Failed at step CGROUP spawning /sbin/ip: No such file or dir -- Subject: Process /sbin/ip could not be executed
root@ubuntu:/home/ubuntu# mkdir -p /var/run/quagga/ root@ubuntu:/home/ubuntu# chown quagga:quagga /var/run/quagga root@ubuntu:/home/ubuntu# zebra -f /etc/quagga/zebra.conf -d root@ubuntu:/home/ubuntu# ps -elf | grep zebra 1 S quagga 43724 1 0 80 0 - 1185 poll_s 23:41 ? 00:00:00 zebra -f /etc/quagga/zebra.conf -d 0 S root 43726 43699 0 80 0 - 1095 pipe_w 23:41 pts/8 00:00:00 grep --color=auto zebra root@ubuntu:/home/ubuntu#
pip install termcolor -i https://pypi.tuna.tsinghua.edu.cn/simple
root@ubuntu:/data1/bgp# whereis zebra zebra: /usr/sbin/zebra /usr/share/man/man8/zebra.8.gz root@ubuntu:/data1/bgp# whereis bgpd bgpd: /usr/sbin/bgpd /usr/share/man/man8/bgpd.8.gz root@ubuntu:/data1/bgp#
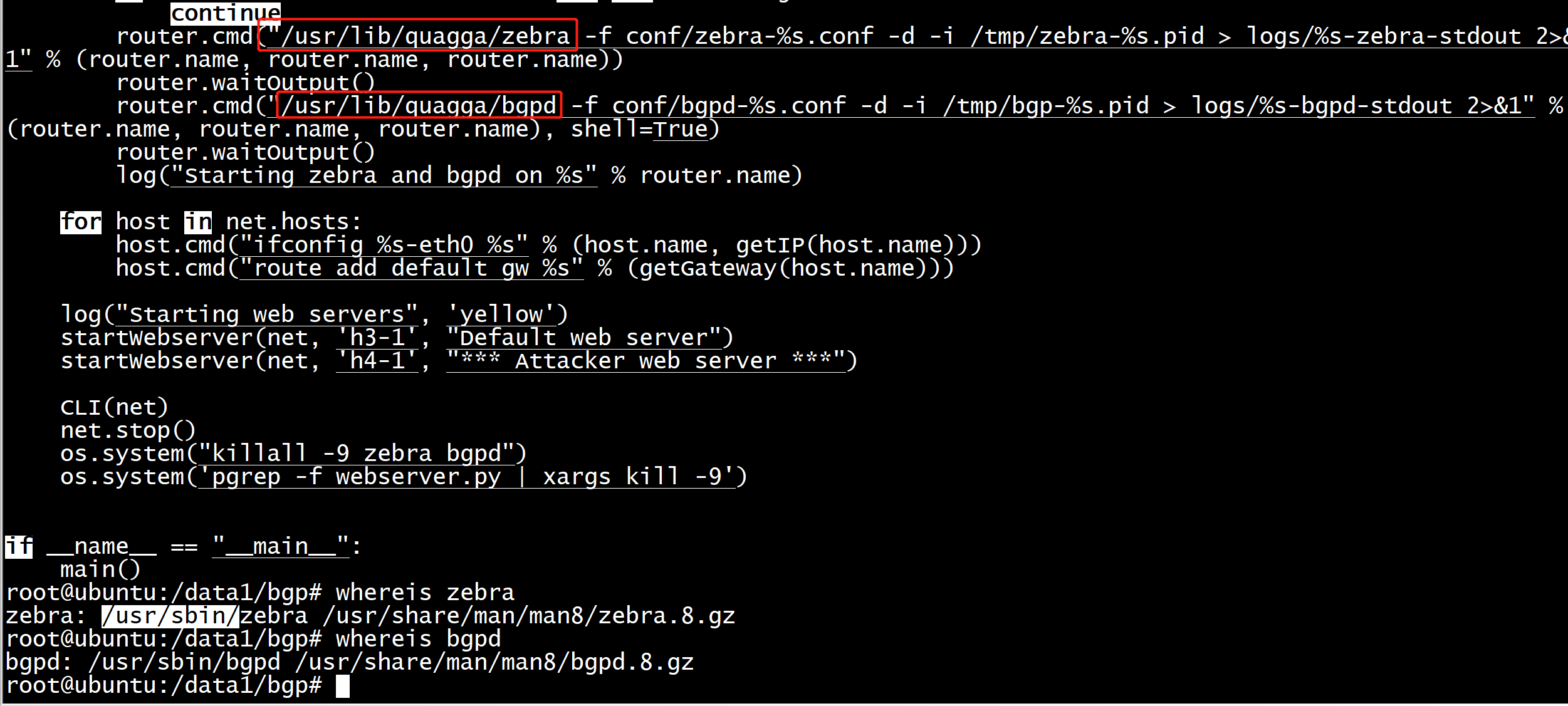
cd /home/bgp
screen python bgp.py
root@ubuntu:/data1/bgp# ps -elf | grep zebra 5 S quagga 45529 1 0 80 0 - 1252 poll_s 23:51 ? 00:00:00 /usr/sbin/zebra -f conf/zebra-R1.conf -d -i /tmp/zebra-R1.pid 5 S quagga 45533 1 0 80 0 - 1252 poll_s 23:51 ? 00:00:00 /usr/sbin/zebra -f conf/zebra-R2.conf -d -i /tmp/zebra-R2.pid 5 S quagga 45537 1 0 80 0 - 1251 poll_s 23:51 ? 00:00:00 /usr/sbin/zebra -f conf/zebra-R3.conf -d -i /tmp/zebra-R3.pid 0 S root 45570 44682 0 80 0 - 1095 pipe_w 23:51 pts/28 00:00:00 grep --color=auto zebra root@ubuntu:/data1/bgp# ps -elf | grep bgpd 1 S quagga 45531 1 0 80 0 - 1995 poll_s 23:51 ? 00:00:00 /usr/sbin/bgpd -f conf/bgpd-R1.conf -d -i /tmp/bgp-R1.pid 1 S quagga 45535 1 0 80 0 - 1963 poll_s 23:51 ? 00:00:00 /usr/sbin/bgpd -f conf/bgpd-R2.conf -d -i /tmp/bgp-R2.pid 1 S quagga 45539 1 0 80 0 - 1963 poll_s 23:51 ? 00:00:00 /usr/sbin/bgpd -f conf/bgpd-R3.conf -d -i /tmp/bgp-R3.pid 0 S root 45572 44682 0 80 0 - 1095 pipe_w 23:51 pts/28 00:00:00 grep --color=auto bgpd root@ubuntu:/data1/bgp#
采用e bgp
ubuntu@ubuntu:/data1/bgp/conf$ cat bgpd-R1.conf ! -*- bgp -*- ! ! BGPd sample configuratin file ! ! $Id: bgpd.conf.sample,v 1.1 2002/12/13 20:15:29 paul Exp $ ! hostname bgpd-R1 password en enable password en router bgp 1 bgp router-id 9.0.0.1 network 11.0.0.0/8 neighbor 9.0.0.2 remote-as 2 neighbor 9.0.0.2 ebgp-multihop neighbor 9.0.0.2 next-hop-self neighbor 9.0.0.2 timers 5 5 neighbor 9.0.4.2 remote-as 4 neighbor 9.0.4.2 ebgp-multihop neighbor 9.0.4.2 next-hop-self neighbor 9.0.4.2 timers 5 5 log file /tmp/R1-bgpd.log debug bgp as4 debug bgp events debug bgp filters debug bgp fsm debug bgp keepalives debug bgp updates ! log stdout ubuntu@ubuntu:/data1/bgp/conf$ ls bgpd-R1.conf bgpd-R3.conf zebra-R1.conf zebra-R3.conf bgpd-R2.conf bgpd-R4.conf zebra-R2.conf zebra-R4.conf ubuntu@ubuntu:/data1/bgp/conf$ cat bgpd-R2.conf ! -*- bgp -*- ! ! BGPd sample configuratin file ! ! $Id: bgpd.conf.sample,v 1.1 2002/12/13 20:15:29 paul Exp $ ! hostname bgpd-R2 password en enable password en router bgp 2 bgp router-id 9.0.0.2 network 12.0.0.0/8 neighbor 9.0.0.1 remote-as 1 neighbor 9.0.0.1 update-source 9.0.0.2 neighbor 9.0.0.1 ebgp-multihop neighbor 9.0.0.1 next-hop-self neighbor 9.0.0.1 timers 5 5 neighbor 9.0.1.2 remote-as 3 neighbor 9.0.1.2 update-source 9.0.1.1 neighbor 9.0.1.2 ebgp-multihop neighbor 9.0.1.2 next-hop-self neighbor 9.0.1.2 timers 5 5 log file /tmp/R2-bgpd.log debug bgp as4 debug bgp events debug bgp filters debug bgp fsm debug bgp keepalives debug bgp updates ! log stdout ubuntu@ubuntu:/data1/bgp/conf$ cat bgpd-R3.conf ! -*- bgp -*- ! ! BGPd sample configuratin file ! ! $Id: bgpd.conf.sample,v 1.1 2002/12/13 20:15:29 paul Exp $ ! hostname bgpd-R3 password zebra enable password zebra router bgp 3 bgp router-id 9.0.1.2 network 13.0.0.0/8 neighbor 9.0.1.1 remote-as 2 !neighbor 9.0.1.1 ebgp-multihop 2 neighbor 9.0.1.1 next-hop-self neighbor 9.0.1.1 timers 5 5 log file /tmp/R3-bgpd.log debug bgp as4 debug bgp events debug bgp filters debug bgp fsm debug bgp keepalives debug bgp updates ! log stdout ubuntu@ubuntu:/data1/bgp/conf$
ubuntu@ubuntu:/data1/bgp/conf$ cat bgpd-R4.conf ! -*- bgp -*- ! ! BGPd sample configuratin file ! ! $Id: bgpd.conf.sample,v 1.1 2002/12/13 20:15:29 paul Exp $ ! hostname bgpd-R4 password en enable password en router bgp 4 bgp router-id 9.0.4.2 network 13.0.0.0/8 neighbor 9.0.4.1 remote-as 1 neighbor 9.0.4.1 ebgp-multihop neighbor 9.0.4.1 next-hop-self neighbor 9.0.4.1 timers 5 5 log file /tmp/R4-bgpd.log debug bgp as4 debug bgp events debug bgp filters debug bgp fsm debug bgp keepalives debug bgp updates ! log stdout
实验原理:
互联网是由相互连接的自治系统AS组成的,通过一个通用的边界网关协议(BGP)进行交互彼此的路由信息。如果利用BGP进行特殊攻击,比如一个伪装的AS伪造了一个更短的路径到前缀P,其他的AS要路由到前缀P时就会选择这个更短的路径,受到感染的AS会把该攻击信息继续向其他的AS传播,使得更多的AS受到感染,逐渐形成了BGP劫持攻击。
实验任务:
通过创建下图所示的网络拓扑,包括四个AS(AS1,AS2,AS3,AS4)。每个AS都有它的路由守护进程(R1,R2,R3,R4),守护路由的对接情况如下:
1.R1和R2,R4对接
2.R2和R1,R3对接
3.R3和R2对接

1.为每个AS节点创建容器,每个容器都有一个路由守护进程,我们使用开源路由组件quagga,每个AS运行bgpd来承载BGP,通过zebra配置linus内核中的路由规则。
2.每个as的配置信息存放在实验代码包的conf文件夹中
3.因为mininet使用网络域名,每个容器的路由表都是相互独立的,因此改变AS1的路由表不会影响AS2的路由表。
4.AS是通过静态路由规则中分离的网络接口互相连接的。
注意第一点:quagga是用来创建路由守护程序的,bgpd是用来在AS中承载BGP的。
root@ubuntu:/data1/bgp# ./connect.sh Connecting to R1 shell Trying ::1... Connected to localhost. Escape character is '^]'. Hello, this is Quagga (version 1.2.4). Copyright 1996-2005 Kunihiro Ishiguro, et al. User Access Verification Password: -------------------en
执行命令sh ip bgp查看AS1的路由表信息:
bgpd-R1> sh ip bgp BGP table version is 0, local router ID is 9.0.0.1 Status codes: s suppressed, d damped, h history, * valid, > best, = multipath, i internal, r RIB-failure, S Stale, R Removed Origin codes: i - IGP, e - EGP, ? - incomplete Network Next Hop Metric LocPrf Weight Path *> 11.0.0.0 0.0.0.0 0 32768 i *> 12.0.0.0 9.0.0.2 0 0 2 i *> 13.0.0.0 9.0.0.2 0 2 3 i
从上图中可以看出,要到达“13.0.0.0/8”选择的AS路径是“2 3”(例如通过AS2和AS3)。
执行exit退出到系统操作界面。执行以下脚本访问mininet开启在AS3中的一个默认web服务器,并判定可以直接从AS的host1-1直接访问。
在代码目录下有一个“website.sh”,这个脚本执行后会在AS1上循环执行curl -s 13.0.1.1这个命令.
ubuntu@ubuntu:/data1/bgp$ cat website.sh #!/bin/bash node=${1:-h1-1} bold=`tput bold` normal=`tput sgr0` while true; do out=`sudo python run.py --node $node --cmd "curl -s 13.0.1.1"` date=`date` echo $date -- $bold$out$normal sleep 1 done ubuntu@ubuntu:/data1/bgp$ ./website.sh [sudo] password for ubuntu: Fri Aug 7 00:07:02 EDT 2020 -- <h1>Default web server</h1> Fri Aug 7 00:07:04 EDT 2020 -- <h1>Default web server</h1> Fri Aug 7 00:07:05 EDT 2020 -- <h1>Default web server</h1> Fri Aug 7 00:07:06 EDT 2020 -- <h1>Default web server</h1> Fri Aug 7 00:07:07 EDT 2020 -- <h1>Default web server</h1> Fri Aug 7 00:07:08 EDT 2020 -- <h1>Default web server</h1> Fri Aug 7 00:07:09 EDT 2020 -- <h1>Default web server</h1> Fri Aug 7 00:07:10 EDT 2020 -- <h1>Default web server</h1> Fri Aug 7 00:07:12 EDT 2020 -- <h1>Default web server</h1> Fri Aug 7 00:07:13 EDT 2020 -- <h1>Default web server</h1> ^C ubuntu@ubuntu:/data1/bgp$