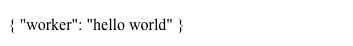前言
因工作原因,接触到了WAF,今天部署了一下Naxsi,记录一下
GitHub
正文
环境
Centos 7
下载
更新yum
yum update -y
安装必要依赖
yum install gcc gcc-c++ cmake ncurses ncurses-devel libxml2 libxml2-devel zlib zlib-devel gd gd-devel openssl openssl-devel curl curl-devel libtool pcre pcre-devel wget unzip vim
下载Nginx
可使用最新版
wget http://nginx.org/download/nginx-1.17.8.tar.gz
下载Naxsi
可使用最新版
wget https://github.com/nbs-system/naxsi/archive/0.56.tar.gz
解压
tar -xvzf nginx-1.17.8.tar.gz
tar -xvzf 0.56.tar.gz
编译安装带插件的Nginx
cd nginx-1.17.8
注意 --add-module 后面跟的路径
./configure --prefix=/opt/nginx --add-module=/root/naxsi/naxsi-0.56/naxsi_src --user=nginx --group=nginx --with-http_ssl_module --with-http_geoip_module --without-mail_pop3_module --without-mail_smtp_module --without-mail_imap_module --without-http_uwsgi_module --without-http_scgi_module
make
make install
mkdir /var/log/nginx
安装Naxsi插件
cp /root/naxsi/naxsi-0.56/naxsi_config/naxsi_core.rules /opt/nginx/conf/
vim /opt/nginx/conf/naxsi.rules
写入以下内容保存
SecRulesEnabled;
DeniedUrl "/RequestDenied";
## check rules
CheckRule "$SQL >= 8" BLOCK;
CheckRule "$RFI >= 8" BLOCK;
CheckRule "$TRAVERSAL >= 4" BLOCK;
CheckRule "$EVADE >= 4" BLOCK;
CheckRule "$XSS >= 8" BLOCK;
上面的内容是拦截的规则, naxsi的流程是将每个请求URL解析,发现一个可疑处增加一些分数,从2到8分都有,然后根据此文件的规则确定规则
比如 CheckRule "$SQL >= 8" BLOCK; 的意思是如果SQL部分分数大于等于8返回错误的状态码(404)
更多详细可看 Naxsi规则简单说明
开启Naxsi插件
vim /opt/nginx/conf/nginx.conf
修改为
user nginx nginx;
worker_processes 1;
events {
worker_connections 1024;
}
http {
include mime.types;
include /opt/nginx/conf/naxsi_core.rules;
default_type application/octet-stream;
access_log off;
error_log /var/log/nginx/error.log;
sendfile on;
keepalive_timeout 65;
tcp_nodelay on;
gzip on;
gzip_disable "MSIE [1-6].(?!.*SV1)";
server {
listen 80;
server_name localhost;
location / {
include /opt/nginx/conf/naxsi.rules; # 开启插件
proxy_pass http://127.0.0.1:3456; # 通过后转发到内部监听业务地址
}
error_page 500 502 503 504 /50x.html;
location = /50x.html {
root html;
}
}
}
开启Nginx
测试
/opt/nginx/sbin/nginx -t
启动
/opt/nginx/sbin/nginx
测试
使用Post测试
访问业务地址
比如一个Python的接口,路由是 / ,接收Post和Get请求,直接返回 helloworld
访问时带上SQL注入
http://x.x.x.x/?q="><script>alert(1)</script>
返回404代表已成功拦截

去掉sql注入访问返回200