ida找到关键函数
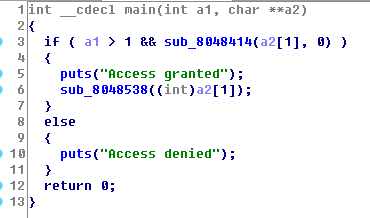
sub_8048414回调函数,a2初始值传入0,经过运算a2值的变化依次是:0 7 1 3 6 5 9 4
signed int __cdecl sub_8048414(_BYTE *a1, int a2) { signed int result; // eax@3 switch ( a2 ) { case 3: if ( *a1 == 110 ) goto LABEL_19; result = 0; break; case 9: if ( *a1 == 114 ) goto LABEL_19; result = 0; break; case 4: if ( *a1 == 100 ) goto LABEL_19; result = 0; break; case 1: if ( *a1 == 101 ) goto LABEL_19; result = 0; break; case 0: if ( *a1 == 105 ) goto LABEL_19; result = 0; break; case 5: if ( *a1 == 97 ) goto LABEL_19; result = 0; break; case 6: if ( *a1 == 103 ) goto LABEL_19; result = 0; break; case 7: if ( *a1 == 115 ) LABEL_19: result = sub_8048414(a1 + 1, 7 * (a2 + 1) % 11); else result = 0; break; default: result = 1; break; } return result; }
sub_8048538函数,利用刚才的result运算得到flag
int __cdecl sub_8048538(int a1) { int v2[33]; // [sp+18h] [bp-A0h]@1 int i; // [sp+9Ch] [bp-1Ch]@1 qmemcpy(v2, &unk_8048760, sizeof(v2)); for ( i = 0; i <= 32; ++i ) putchar(v2[i] ^ *(_BYTE *)(a1 + ((((unsigned int)(i >> 31) >> 29) + (_BYTE)i) & 7) - ((unsigned int)(i >> 31) >> 29))); return putchar(10); }
写出解密代码
a1=[105,115,101,110,103,97,114,100] # sub_8048414回调函数得到这组数据 a2=[0,7,1,3,6,5,9,4] v2=[15, 31, 4, 9, 28, 18, 66, 9, 12, 68, 13, 7, 9, 6, 45, 55, 89, 30, 0, 89, 15, 8, 28, 35, 54, 7, 85, 2, 12, 8, 65, 10, 20] for i in range(0,33): print(chr(v2[i]^a1[i&7]),end='')
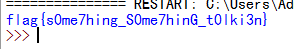
flag{s0me7hing_S0me7hinG_t0lki3n}