
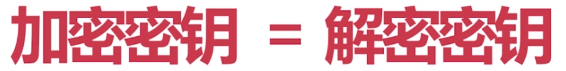
PS: 加密和解密运算 是对称的行为, 叫做对称加密算法

PS: 对称加密算法 是 初等的加密算法,最早出现的DES,因为长度安全问题,又出现了3DES,后续又有了其他加密算法
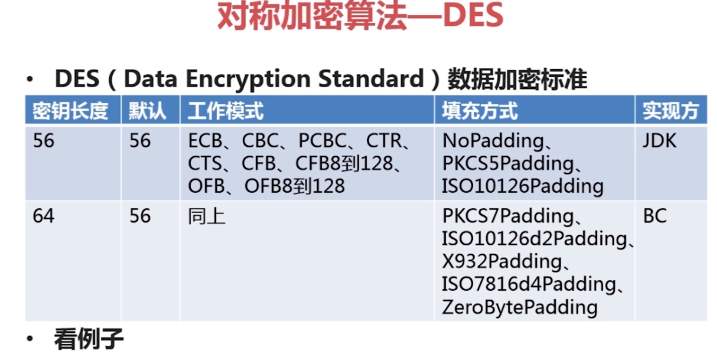
PS: DES现在已经不太安全了,一般不怎么实用,容易被破解
package com.bee.springboot.util.encrypt.des; import org.apache.commons.codec.binary.Hex; import javax.crypto.Cipher; import javax.crypto.KeyGenerator; import javax.crypto.SecretKey; import javax.crypto.SecretKeyFactory; import javax.crypto.spec.DESKeySpec; import java.security.Key; import java.security.Security; /** * 学习Des时创建的文件 */ public class BeeDes { public static final String src = "测试des"; public static void main(String[] args){ jdkDes(); } /** * jdk的Des加密方法 */ public static void jdkDes(){ try{ //生成key KeyGenerator keyGenerator = KeyGenerator.getInstance("DES"); keyGenerator.init(56);//根据Des的属性,自己生成的是56,也可以是64 SecretKey secretKey = keyGenerator.generateKey(); byte[] bytesKey = secretKey.getEncoded(); //Key转换 DESKeySpec desKeySpec = new DESKeySpec(bytesKey); SecretKeyFactory factory = SecretKeyFactory.getInstance("DES"); Key convertSecretKey = factory.generateSecret(desKeySpec); //加密 Cipher cipher = Cipher.getInstance("DES/ECB/PKCS5Padding"); cipher.init(Cipher.ENCRYPT_MODE,convertSecretKey); byte[] result = cipher.doFinal(src.getBytes());//等待价密的文字 System.out.println("jdk加密: "+result); System.out.println("jdk加密: "+ Hex.encodeHexString(result));//十六进制编码修改 // 解密: 上面用到的是 一套东西, 只是在解密的模式上不同 cipher.init(Cipher.DECRYPT_MODE,convertSecretKey); result = cipher.doFinal(result);//等待解密的文字 System.out.println("jdk解密: "+new String(result)); }catch (Exception e){ e.printStackTrace(); } } /* *//** * bc的Des加密方法 *//* public static void bcDes(){ try{ Security.addProvider(new BouncyCastleProvider());//报错是因为jdk版本问题 //生成key KeyGenerator keyGenerator = KeyGenerator.getInstance("DES","BC"); keyGenerator.getProvider(); keyGenerator.init(56);//根据Des的属性,自己生成的是56,也可以是64 SecretKey secretKey = keyGenerator.generateKey(); byte[] bytesKey = secretKey.getEncoded(); //Key转换 DESKeySpec desKeySpec = new DESKeySpec(bytesKey); SecretKeyFactory factory = SecretKeyFactory.getInstance("DES"); Key convertSecretKey = factory.generateSecret(desKeySpec); //加密 Cipher cipher = Cipher.getInstance("DES/ECB/PKCS5Padding"); cipher.init(Cipher.ENCRYPT_MODE,convertSecretKey); byte[] result = cipher.doFinal(src.getBytes());//等待价密的文字 System.out.println("jdk加密: "+result); System.out.println("jdk加密: "+ Hex.encodeHexString(result));//十六进制编码修改 // 解密: 上面用到的是 一套东西, 只是在解密的模式上不同 cipher.init(Cipher.DECRYPT_MODE,convertSecretKey); result = cipher.doFinal(result);//等待解密的文字 System.out.println("jdk解密: "+new String(result)); }catch (Exception e){ e.printStackTrace(); } }*/ }
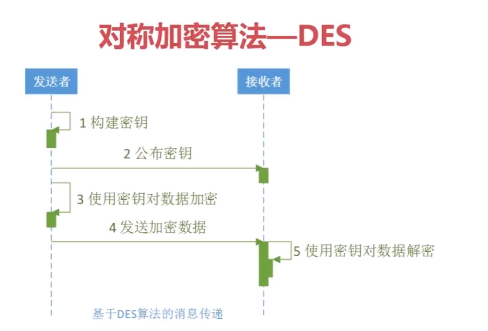
PS: 应用场景---上次做取号业务的时候就是DES处理的
package com.bee.springboot.util.encrypt.des; import org.apache.commons.codec.binary.Hex; import javax.crypto.Cipher; import javax.crypto.KeyGenerator; import javax.crypto.SecretKey; import javax.crypto.SecretKeyFactory; import javax.crypto.spec.DESKeySpec; import javax.crypto.spec.DESedeKeySpec; import java.security.Key; import java.security.SecureRandom; /** * 学习3Des时创建的文件,主要是因为 DES不安全才出现的 */ public class Bee3Des { public static final String src = "测试des"; public static void main(String[] args){ jdk3Des(); } /** * jdk的Des加密方法 */ public static void jdk3Des(){ try{ //生成key KeyGenerator keyGenerator = KeyGenerator.getInstance("DESede"); keyGenerator.init(168);//根据Des的属性,自己生成的是56,也可以是64 // keyGenerator.init(new SecureRandom()); SecretKey secretKey = keyGenerator.generateKey(); byte[] bytesKey = secretKey.getEncoded(); //Key转换 DESedeKeySpec desKeySpec = new DESedeKeySpec(bytesKey);//这也有修改!!!!!! SecretKeyFactory factory = SecretKeyFactory.getInstance("DESede"); Key convertSecretKey = factory.generateSecret(desKeySpec); //加密 Cipher cipher = Cipher.getInstance("DESede/ECB/PKCS5Padding"); cipher.init(Cipher.ENCRYPT_MODE,convertSecretKey); byte[] result = cipher.doFinal(src.getBytes());//等待价密的文字 System.out.println("jdk3加密: "+result); System.out.println("jdk加密: "+ Hex.encodeHexString(result));//十六进制编码修改 // 解密: 上面用到的是 一套东西, 只是在解密的模式上不同 cipher.init(Cipher.DECRYPT_MODE,convertSecretKey); result = cipher.doFinal(result);//等待解密的文字 System.out.println("jdk3解密: "+new String(result)); }catch (Exception e){ e.printStackTrace(); } } /* *//** * bc的Des加密方法 *//* public static void bcDes(){ //todo... }*/ }



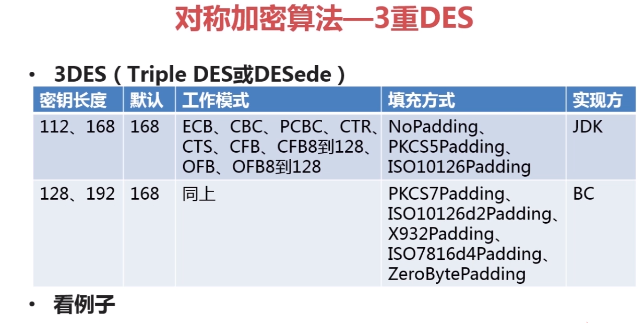
PS: 3DES速度慢,des不安全,所以有了AES; AES就是来替代DES的

package com.bee.springboot.util.encrypt.des; import org.apache.commons.codec.binary.Hex; import javax.crypto.Cipher; import javax.crypto.KeyGenerator; import javax.crypto.SecretKey; import javax.crypto.SecretKeyFactory; import javax.crypto.spec.DESKeySpec; import javax.crypto.spec.SecretKeySpec; import java.security.Key; /** * 学习Aes时创建的文件 */ public class BeeAes { public static final String src = "测试des"; public static void main(String[] args){ jdkAes(); } /** * jdk的Des加密方法 */ public static void jdkAes(){ try{ //生成key KeyGenerator keyGenerator = KeyGenerator.getInstance("AES"); keyGenerator.init(128);//根据Des的属性,自己生成的是56,也可以是64 SecretKey secretKey = keyGenerator.generateKey(); byte[] bytesKey = secretKey.getEncoded(); //Key转换 Key key = new SecretKeySpec(bytesKey, "AES"); //加密 Cipher cipher = Cipher.getInstance("AES/ECB/PKCS5Padding");//加密方式, 工作模式 ,填充方式 cipher.init(Cipher.ENCRYPT_MODE,key); byte[] result = cipher.doFinal(src.getBytes());//等待价密的文字 System.out.println("jdk aes加密: "+result); System.out.println("jdk aes加密: "+ Hex.encodeHexString(result));//十六进制编码修改 // 解密: 上面用到的是 一套东西, 只是在解密的模式上不同 cipher.init(Cipher.DECRYPT_MODE,key); result = cipher.doFinal(result);//等待解密的文字 System.out.println("jdk aes解密: "+new String(result)); }catch (Exception e){ e.printStackTrace(); } } /* *//** * bc的Aes加密方法 *//* public static void bcDes(){ //todo }*/ }
PS: 应用场景


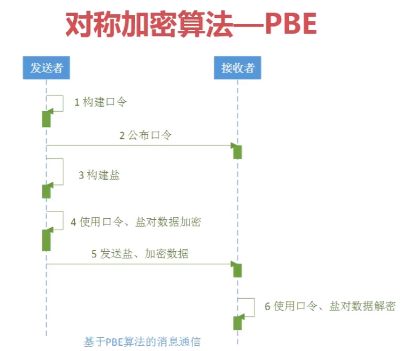
PS:以上的算法都比较类似,但是PBE是集合了他们所有的优势,最牛逼的


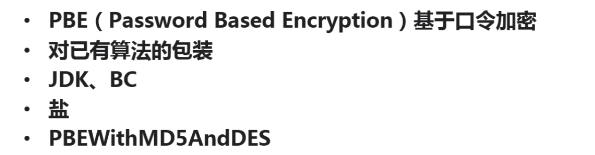
package com.bee.springboot.util.encrypt.des; import org.apache.commons.codec.binary.Hex; import javax.crypto.Cipher; import javax.crypto.KeyGenerator; import javax.crypto.SecretKey; import javax.crypto.SecretKeyFactory; import javax.crypto.spec.PBEKeySpec; import javax.crypto.spec.PBEParameterSpec; import javax.crypto.spec.SecretKeySpec; import java.security.Key; import java.security.SecureRandom; /** * PBE特殊在口令 + 盐(就是加密时的随机数) */ public class BeePBE { public static final String src = "测试des"; public static void main(String[] args){ jdkPBE(); } /** * jdk的Des加密方法 */ public static void jdkPBE(){ try{ //初始化 盐 SecureRandom random = new SecureRandom(); byte[] salt = random.generateSeed(8); //口令和密钥 String password = "imooc"; PBEKeySpec pbeKeySpec = new PBEKeySpec(password.toCharArray()); SecretKeyFactory factory = SecretKeyFactory.getInstance("PBEWITHMD5andDES"); Key key = factory.generateSecret(pbeKeySpec); //加密 PBEParameterSpec pbeParameterSpec = new PBEParameterSpec(salt, 100); Cipher cipher = Cipher.getInstance("PBEWITHMD5andDES");//加密方式, 工作模式 ,填充方式 cipher.init(Cipher.ENCRYPT_MODE,key,pbeParameterSpec); byte[] result = cipher.doFinal(src.getBytes());//等待价密的文字 System.out.println("jdk pbe加密: "+result); System.out.println("jdk pbe加密: "+ Hex.encodeHexString(result));//十六进制编码修改 // 解密: 上面用到的是 一套东西, 只是在解密的模式上不同 cipher.init(Cipher.DECRYPT_MODE,key,pbeParameterSpec); result = cipher.doFinal(result);//等待解密的文字 System.out.println("jdk pbe解密: "+new String(result)); }catch (Exception e){ e.printStackTrace(); } } /* *//** * bc的Aes加密方法 *//* public static void bcDes(){ //todo }*/ }
-------------------------------------------------------------------------------------------------------------------------------

PS: 非对称加密,必须有公钥和私钥, 一把公钥和私钥共同打开 宝箱大门
PS: 学习 对称加密算法的时候,难点就是密钥的交换,使用非对称加密算法来交换密钥
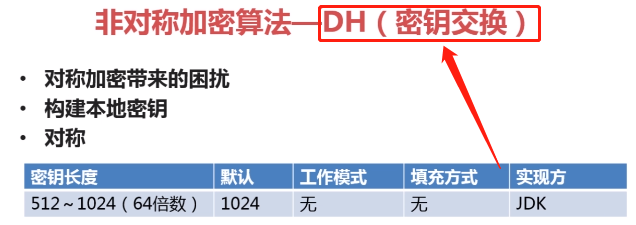
PS: KeyPair密钥的载体,也被称为密钥对(包括公钥和私钥),
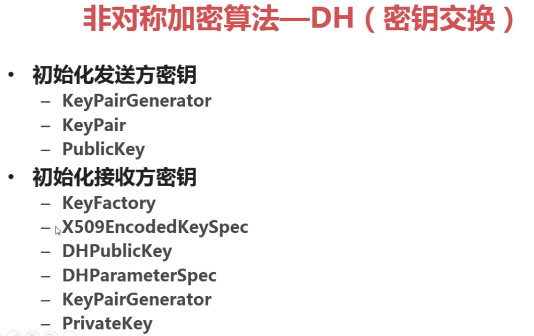


package com.bee.springboot.util.encrypt.des; import org.apache.commons.codec.binary.Hex; import javax.crypto.Cipher; import javax.crypto.KeyAgreement; import javax.crypto.SecretKey; import javax.crypto.SecretKeyFactory; import javax.crypto.interfaces.DHPublicKey; import javax.crypto.spec.DHParameterSpec; import javax.crypto.spec.PBEKeySpec; import javax.crypto.spec.PBEParameterSpec; import java.security.*; import java.security.spec.X509EncodedKeySpec; import java.util.Objects; /** * 非对称加密 */ public class BeeDH { public static final String src = "测试des"; public static void main(String[] args) { jdkDH(); } public static void jdkDH() { try{ //1.初始化发送方密钥 KeyPairGenerator senderKeyPairGenerator = KeyPairGenerator.getInstance("DH"); senderKeyPairGenerator.initialize(512); KeyPair sendKeyPair = senderKeyPairGenerator.generateKeyPair(); byte[] senderPublicKeyEnc = sendKeyPair.getPublic().getEncoded();//发送方公钥,发送给接收方 (网络、文件 ...) //2.初始化接收方的密钥 KeyFactory receiverKeyFactory = KeyFactory.getInstance("DH"); X509EncodedKeySpec x509EncodedKeySpec = new X509EncodedKeySpec(senderPublicKeyEnc);// 主要x509标准进行编码 PublicKey receiverPublicKey = receiverKeyFactory.generatePublic(x509EncodedKeySpec); DHParameterSpec dhParameterSpec = ((DHPublicKey) receiverPublicKey).getParams(); KeyPairGenerator receiverKeyPairGenerator = KeyPairGenerator.getInstance("DH"); receiverKeyPairGenerator.initialize(dhParameterSpec); KeyPair receiverKeyPair = receiverKeyPairGenerator.generateKeyPair(); PrivateKey receiverPrivateKey = receiverKeyPair.getPrivate(); byte[] receiverPublicKeyEnc = receiverKeyPair.getPublic().getEncoded(); //3.密钥构建 KeyAgreement receiverKeyAgreement = KeyAgreement.getInstance("DH"); receiverKeyAgreement.init(receiverPrivateKey); receiverKeyAgreement.doPhase(receiverPublicKey,true); SecretKey receiverDesKey = receiverKeyAgreement.generateSecret("DES"); KeyFactory senderKeyFactory = KeyFactory.getInstance("DH"); x509EncodedKeySpec = new X509EncodedKeySpec(receiverPublicKeyEnc); PublicKey senderPublicKey = senderKeyFactory.generatePublic(x509EncodedKeySpec); KeyAgreement senderKeyAgreement = KeyAgreement.getInstance("DH"); senderKeyAgreement.init(sendKeyPair.getPrivate()); senderKeyAgreement.doPhase(senderPublicKey,true); SecretKey senderDesKey = senderKeyAgreement.generateSecret("DES"); if(Objects.equals(receiverDesKey,senderDesKey)){ System.out.println("双方密钥相同"); } //加密 Cipher cipher = Cipher.getInstance("DES");//加密方式, 工作模式 ,填充方式 cipher.init(Cipher.ENCRYPT_MODE,senderDesKey); byte[] result = cipher.doFinal(src.getBytes());//等待价密的文字 System.out.println("jdk DH加密: "+result); System.out.println("jdk DH加密: "+ Hex.encodeHexString(result));//十六进制编码修改 // 解密: 上面用到的是 一套东西, 只是在解密的模式上不同 cipher.init(Cipher.DECRYPT_MODE,receiverDesKey); result = cipher.doFinal(result);//等待解密的文字 System.out.println("jdk DH解密: "+new String(result)); }catch (Exception e){ e.printStackTrace(); } } }
PS: DH为所有的非对称加密算法提供了基础, RSA 就是对 DH基础上拓展的
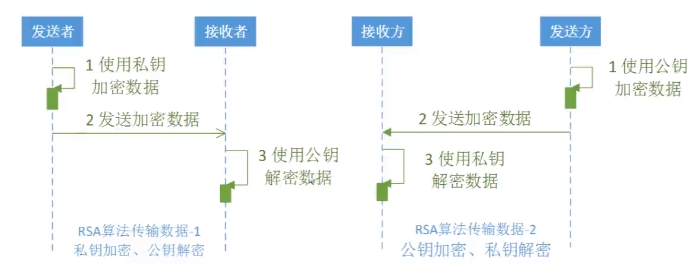
PS: RSA基本上已经成为 非对称加密的标准


package com.bee.springboot.util.encrypt.des; import org.apache.commons.codec.binary.Base64; import org.apache.commons.codec.binary.Hex; import javax.crypto.Cipher; import javax.crypto.KeyAgreement; import javax.crypto.SecretKey; import javax.crypto.interfaces.DHPublicKey; import javax.crypto.spec.DHParameterSpec; import java.security.*; import java.security.interfaces.RSAPrivateKey; import java.security.interfaces.RSAPublicKey; import java.security.spec.PKCS8EncodedKeySpec; import java.security.spec.X509EncodedKeySpec; import java.util.Objects; /** * 非对称加密 RSA */ public class BeeRSA { public static final String src = "D撒旦法sddes"; public static void main(String[] args) { jdkRSA(); } public static void jdkRSA() { try{ //1.初始化密钥 KeyPairGenerator keyPairGenerator = KeyPairGenerator.getInstance("RSA"); keyPairGenerator.initialize(512); KeyPair keyPair = keyPairGenerator.generateKeyPair(); RSAPublicKey rsaPublicKey = (RSAPublicKey) keyPair.getPublic(); RSAPrivateKey rsaPrivateKey = (RSAPrivateKey) keyPair.getPrivate(); System.out.println("rsaPublicKey: "+ Base64.encodeBase64String(rsaPublicKey.getEncoded())); System.out.println("rsaPrivateKey: "+ Base64.encodeBase64String(rsaPrivateKey.getEncoded())); //2.私钥加密,公钥解密-----加密 PKCS8EncodedKeySpec pkcs8EncodedKeySpec = new PKCS8EncodedKeySpec(rsaPrivateKey.getEncoded()); KeyFactory keyFactory = KeyFactory.getInstance("RSA"); PrivateKey privateKey = keyFactory.generatePrivate(pkcs8EncodedKeySpec); Cipher cipher = Cipher.getInstance("RSA");//加密方式, 工作模式 ,填充方式 cipher.init(Cipher.ENCRYPT_MODE,privateKey); byte[] result = cipher.doFinal(src.getBytes());//等待价密的文字 System.out.println("私钥加密,公钥解密-----加密: "+ Base64.encodeBase64String(result));//十六进制编码修改 //3.私钥加密,公钥解密-----解密 X509EncodedKeySpec x509EncodedKeySpec = new X509EncodedKeySpec(rsaPublicKey.getEncoded());// 主要x509标准进行编码 keyFactory = KeyFactory.getInstance("RSA"); PublicKey publicKey = keyFactory.generatePublic(x509EncodedKeySpec); cipher = Cipher.getInstance("RSA");//加密方式, 工作模式 ,填充方式 cipher.init(Cipher.DECRYPT_MODE,publicKey); result = cipher.doFinal(result);//等待价密的文字 System.out.println("私钥加密,公钥解密-----解密: "+new String(result)); /*********************************分割*********************************************************/ //4.公钥加密,私钥解密---加密 x509EncodedKeySpec = new X509EncodedKeySpec(rsaPublicKey.getEncoded());// 主要x509标准进行编码 keyFactory = KeyFactory.getInstance("RSA"); publicKey = keyFactory.generatePublic(x509EncodedKeySpec); cipher = Cipher.getInstance("RSA");//加密方式, 工作模式 ,填充方式 cipher.init(Cipher.ENCRYPT_MODE,publicKey); result = cipher.doFinal(src.getBytes());//等待价密的文字 System.out.println("公钥加密,私钥解密---加密: "+Base64.encodeBase64String(result));//十六进制编码修改 //5.公钥加密,私钥解密---解密 pkcs8EncodedKeySpec = new PKCS8EncodedKeySpec(rsaPrivateKey.getEncoded()); keyFactory = KeyFactory.getInstance("RSA"); privateKey = keyFactory.generatePrivate(pkcs8EncodedKeySpec); cipher = Cipher.getInstance("RSA");//加密方式, 工作模式 ,填充方式 cipher.init(Cipher.DECRYPT_MODE,privateKey); result = cipher.doFinal(result);//等待价密的文字 System.out.println("公钥加密,私钥解密---加密: "+new String(result)); }catch (Exception e){ e.printStackTrace(); } } }
PS: 应用场景
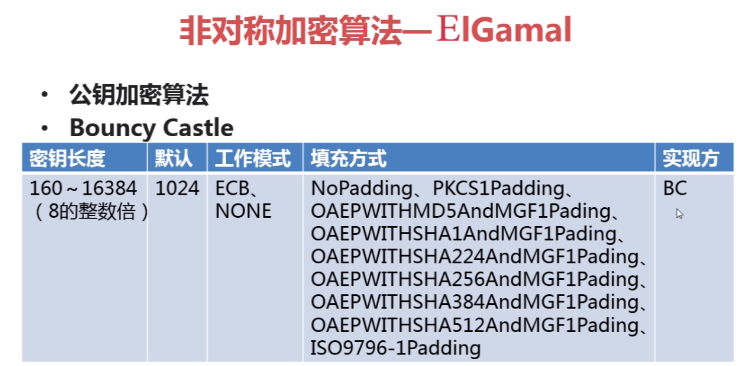
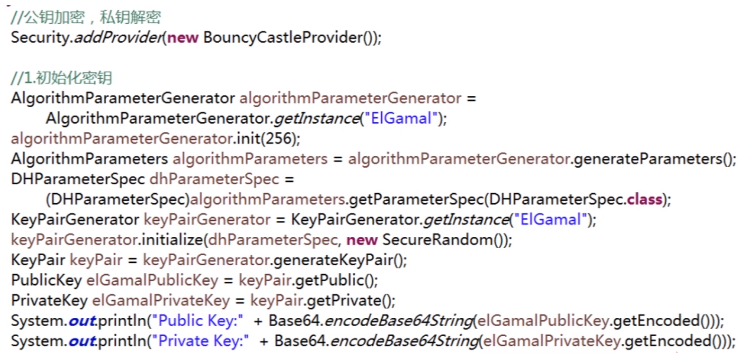
PS: 这个算法也很常用,但是jdk没有提供实现,只有bc,只提供了 公钥加密 算法; 在使用时和RSA是极其相似的


----------------------------------------------------------------------Java Base64加密
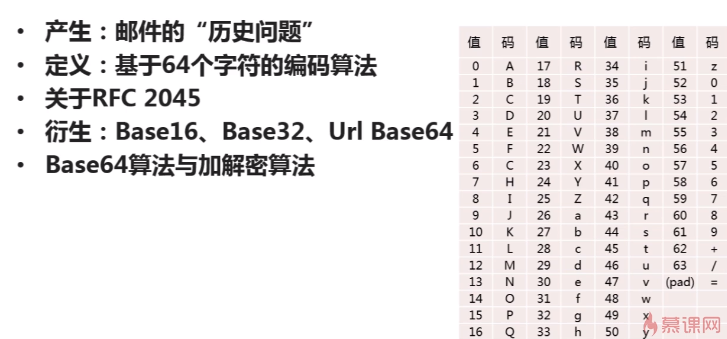
PS: Base64可以说是 不太算一种加密算法,它源于邮件加密

PS: MD5是不存在解密过程的










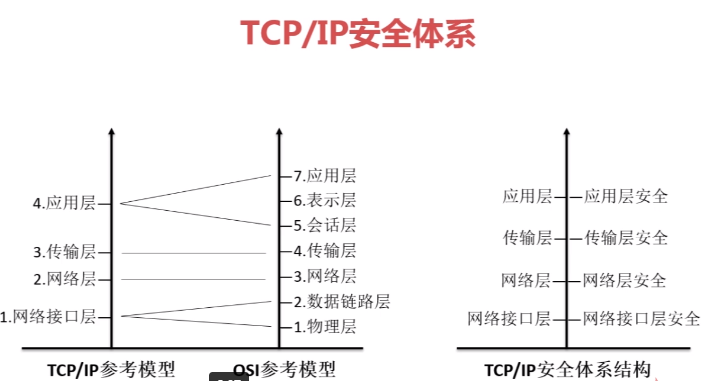


PS:
JCA: 提供基本的加密框架,such as 消息摘要、数字签名
JCE:在JCA原来基础上做了拓展了


JAAS:提供了 java 环境下的身份验证的功能
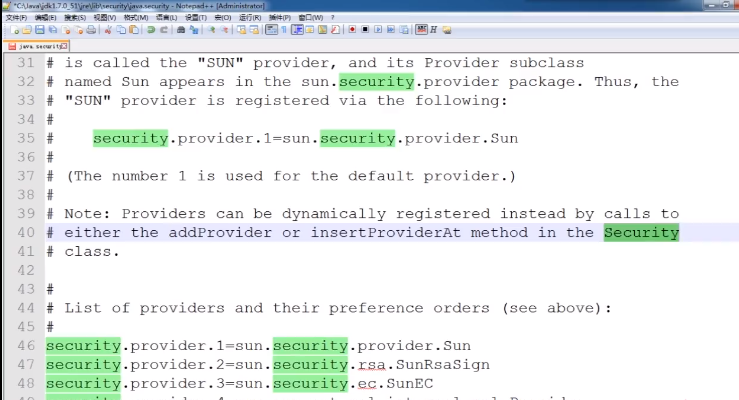
PS: 添加其他拓展的安全包和用法,要么在配置文件(jdk的security)中配置,要么在代码中添加addProvider





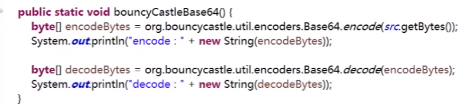
PS: Base64的三种实现方式,推荐使用第二种方式
public static void jdkBase64() { try { BASE64Encoder encoder = new BASE64Encoder(); String encode = encoder.encode(src.getBytes()); System.out.println("encode: " + encode); BASE64Decoder decoder = new BASE64Decoder(); System.out.println("decode: " + new String(decoder.decodeBuffer(encode))); } catch (Exception e) { e.printStackTrace(); } }

---------------------------------------------------------------消息摘要算法(一种不可逆的操作)


package com.bee.springboot.util.encrypt.des; import org.apache.commons.codec.binary.Base64; import org.apache.commons.codec.binary.Hex; import org.apache.commons.codec.digest.DigestUtils; import org.bouncycastle.crypto.Digest; import org.bouncycastle.crypto.digests.MD4Digest; import org.bouncycastle.crypto.digests.MD5Digest; import org.bouncycastle.jce.provider.BouncyCastleProvider; import sun.misc.BASE64Decoder; import sun.misc.BASE64Encoder; import java.security.MessageDigest; import java.security.Security; /** * MD5 * PS: jdk只提供了md5、2没有提供md4;使用cc实现md5 * PS: 通过cc可以简化一些操作,cc提供md4的实现, */ public class BeeMD { public static final String src = "D撒旦法sddes"; public static void main(String[] args) { jdkMD5(); jdkMD2(); bcMD4(); bcMD5(); ccMD5(); } public static void jdkMD5() { try { MessageDigest md = MessageDigest.getInstance("MD5"); byte[] md5Bytes = md.digest(src.getBytes()); System.out.println("Jdk md5: " + Hex.encodeHexString(md5Bytes)); } catch (Exception e) { e.printStackTrace(); } } public static void jdkMD2() { try { MessageDigest md = MessageDigest.getInstance("MD2"); byte[] md2Bytes = md.digest(src.getBytes()); System.out.println("Jdk md2: " + Hex.encodeHexString(md2Bytes)); } catch (Exception e) { e.printStackTrace(); } } /** * 通过引入BC的maven实现的 */ public static void bcMD4() { try { Security.addProvider(new BouncyCastleProvider());// 后面也能实现,只是这种方式是通过添加provider实现的 MessageDigest md = MessageDigest.getInstance("MD4"); byte[] md4Bytes = md.digest(src.getBytes()); System.out.println("BC md4: " + Hex.encodeHexString(md4Bytes)); /* Digest digest = new MD4Digest(); digest.update(src.getBytes(),0,src.getBytes().length); byte[] md4Bytes = new byte[digest.getDigestSize()]; digest.doFinal(md4Bytes,0); System.out.println("BC md4: " + org.bouncycastle.util.encoders.Hex.toHexString(md4Bytes));*/ } catch (Exception e) { e.printStackTrace(); } } public static void bcMD5() { try { Digest digest = new MD5Digest(); digest.update(src.getBytes(),0,src.getBytes().length); byte[] md5Bytes = new byte[digest.getDigestSize()]; digest.doFinal(md5Bytes,0); System.out.println("BC md5: " + org.bouncycastle.util.encoders.Hex.toHexString(md5Bytes)); } catch (Exception e) { e.printStackTrace(); } } public static void ccMD5() { System.out.println("CC md5: " + DigestUtils.md5Hex(src.getBytes())); } public static void ccMD2() { System.out.println("CC md2: " + DigestUtils.md2Hex(src.getBytes())); } }
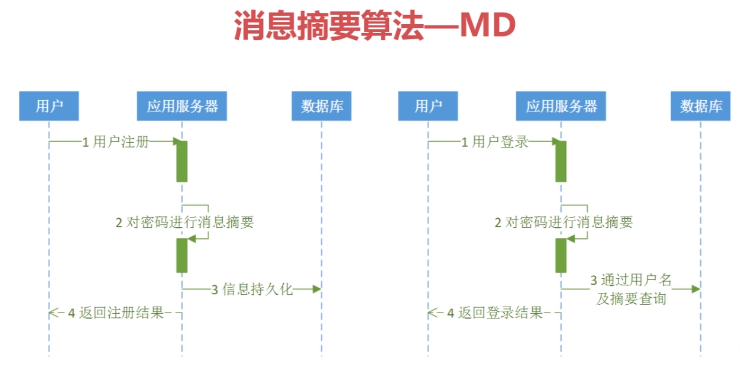
PS: 注册的时候,直接对密码处理; 登录的时候, 对输入的密码再md5处理,通过处理的md5密码和账号登录
PS:消息摘要算法的主要特征是加密过程不需要密钥,并且经过加密的数据无法被解密
PS: SHA是在MD5之后产生的,说是对md5的继承

PS: 一般jdk只提供基础的实现,BC进行一些补充,CC进行简化
package com.bee.springboot.util.encrypt.des; import org.apache.commons.codec.binary.Hex; import org.apache.commons.codec.digest.DigestUtils; import org.bouncycastle.crypto.Digest; import org.bouncycastle.crypto.digests.MD5Digest; import org.bouncycastle.crypto.digests.SHA1Digest; import org.bouncycastle.crypto.digests.SHA224Digest; import org.bouncycastle.jce.provider.BouncyCastleProvider; import java.security.MessageDigest; import java.security.Security; /** * SHA */ public class BeeSHA { public static final String src = "D撒旦法sddes"; public static void main(String[] args) { jdkSHA1(); bcSHA1(); bcSHA224(); ccSHA1(); ccSHA2(); } public static void jdkSHA1() { try { MessageDigest md = MessageDigest.getInstance("SHA1"); md.update(src.getBytes()); System.out.println("Jdk sha-1: " + Hex.encodeHexString(md.digest())); } catch (Exception e) { e.printStackTrace(); } } /** * 通过引入BC的maven实现的 */ public static void bcSHA1() { try { Digest digest = new SHA1Digest(); digest.update(src.getBytes(),0,src.getBytes().length); byte[] md4Bytes = new byte[digest.getDigestSize()]; digest.doFinal(md4Bytes,0); System.out.println("BC SHA1: " + org.bouncycastle.util.encoders.Hex.toHexString(md4Bytes)); } catch (Exception e) { e.printStackTrace(); } } public static void bcSHA224() { try { Digest digest = new SHA224Digest(); digest.update(src.getBytes(),0,src.getBytes().length); byte[] sha224Bytes = new byte[digest.getDigestSize()]; digest.doFinal(sha224Bytes,0); System.out.println("BC sha224: " + org.bouncycastle.util.encoders.Hex.toHexString(sha224Bytes)); } catch (Exception e) { e.printStackTrace(); } } public static void bcSHA224_2() { //使用 provider的方式实现,和之前一样 } public static void ccSHA1() { System.out.println("CC ccSHA1: " + DigestUtils.sha1Hex(src.getBytes())); } public static void ccSHA2() { System.out.println("CC ccSHA2: " + DigestUtils.sha1Hex(src)); } }

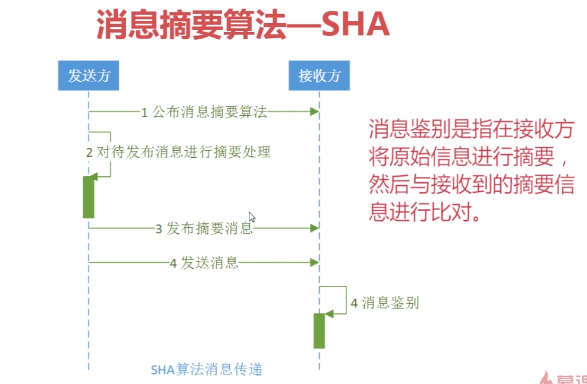
PS: 校验数据,只不过在校验的同时(出于安全机制)会加入一些东西,

PS: MAC是融合MD和SHA基础上,加入验证码的算法

package com.bee.springboot.util.encrypt.des; import org.apache.commons.codec.binary.Hex; import org.apache.commons.codec.digest.DigestUtils; import org.bouncycastle.crypto.Digest; import org.bouncycastle.crypto.digests.MD5Digest; import org.bouncycastle.crypto.digests.SHA1Digest; import org.bouncycastle.crypto.digests.SHA224Digest; import org.bouncycastle.crypto.macs.HMac; import org.bouncycastle.crypto.params.KeyParameter; import javax.crypto.KeyGenerator; import javax.crypto.Mac; import javax.crypto.SecretKey; import javax.crypto.spec.SecretKeySpec; import java.security.MessageDigest; /** * mac */ public class BeeHmac { public static final String src = "D撒旦法sddes"; public static void main(String[] args) { jdkHmacMD5(); bcHmacMD5(); } public static void jdkHmacMD5() { try { KeyGenerator keyGenerator = KeyGenerator.getInstance("HmacMD5");//初始化KeyGenerator SecretKey secretKey = keyGenerator.generateKey();//产生密钥 //byte[] key = secretKey.getEncoded();//获得密钥 byte[] key = new byte[]{'a','a','a','a','a','a','a','a','a','a'};//为了和下面生成的一致 SecretKeySpec restoreSecretKey = new SecretKeySpec(key, "HmacMD5");//还原密钥 Mac mac = Mac.getInstance(restoreSecretKey.getAlgorithm());//实例化mac mac.init(restoreSecretKey);//初始化mac byte[] hmacMD5Bytes = mac.doFinal(src.getBytes());//执行摘要 System.out.println("jdk hmacMD5: "+Hex.encodeHexString(hmacMD5Bytes)); } catch (Exception e) { e.printStackTrace(); } } /** * 通过引入BC的maven实现的 */ public static void bcHmacMD5() { try { HMac hmac = new HMac(new MD5Digest()); hmac.init(new KeyParameter(org.bouncycastle.util.encoders.Hex.decode("aaaaaaaaaa"))); hmac.update(src.getBytes(),0,src.getBytes().length); byte[] bcHmacMD5Bytes = new byte[hmac.getMacSize()];//执行摘要 hmac.doFinal(bcHmacMD5Bytes,0); System.out.println("BC bcHmacMD5B: " + org.bouncycastle.util.encoders.Hex.toHexString(bcHmacMD5Bytes)); } catch (Exception e) { e.printStackTrace(); } } }

///////////////////////////////////////////----------------------------数字签名算法------------//////////////////////////////////////////////////////

--------------------------------------------------------------------------------------------------------


package com.bee.springboot.util.encrypt.des; import org.apache.commons.codec.binary.Hex; import java.security.*; import java.security.interfaces.RSAPrivateKey; import java.security.interfaces.RSAPublicKey; import java.security.spec.PKCS8EncodedKeySpec; import java.security.spec.X509EncodedKeySpec; /** * 非对称加密 RSA 签名算法 */ public class BeeRSAName { public static final String src = "D撒旦法sddes"; public static void main(String[] args) { jdkRSA(); } public static void jdkRSA() { try{ //1.初始化密钥 KeyPairGenerator keyPairGenerator = KeyPairGenerator.getInstance("RSA"); keyPairGenerator.initialize(512); KeyPair keyPair = keyPairGenerator.generateKeyPair(); RSAPublicKey rsaPublicKey = (RSAPublicKey) keyPair.getPublic(); RSAPrivateKey rsaPrivateKey = (RSAPrivateKey) keyPair.getPrivate(); //System.out.println("rsaPublicKey: "+ Base64.encodeBase64String(rsaPublicKey.getEncoded())); //System.out.println("rsaPrivateKey: "+ Base64.encodeBase64String(rsaPrivateKey.getEncoded())); //2.私钥加密,公钥解密-----加密 PKCS8EncodedKeySpec pkcs8EncodedKeySpec = new PKCS8EncodedKeySpec(rsaPrivateKey.getEncoded()); KeyFactory keyFactory = KeyFactory.getInstance("RSA"); PrivateKey privateKey = keyFactory.generatePrivate(pkcs8EncodedKeySpec); Signature signature = Signature.getInstance("MD5withRSA"); signature.initSign(privateKey); signature.update(src.getBytes()); byte[] result = signature.sign(); System.out.println("私钥加密,公钥解密-----加密: "+ Hex.encodeHexString(result)); //签名验证 X509EncodedKeySpec x509EncodedKeySpec = new X509EncodedKeySpec(rsaPublicKey.getEncoded());// 主要x509标准进行编码 keyFactory = KeyFactory.getInstance("RSA"); PublicKey publicKey = keyFactory.generatePublic(x509EncodedKeySpec); signature = Signature.getInstance("MD5withRSA"); signature.initVerify(publicKey); signature.update(src.getBytes()); boolean bool = signature.verify(result); System.out.println("jdk rsa verify : "+bool); }catch (Exception e){ e.printStackTrace(); } } }
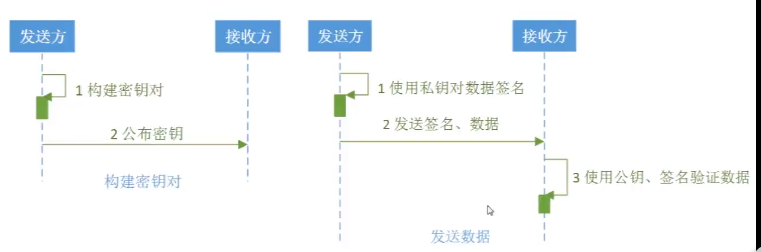

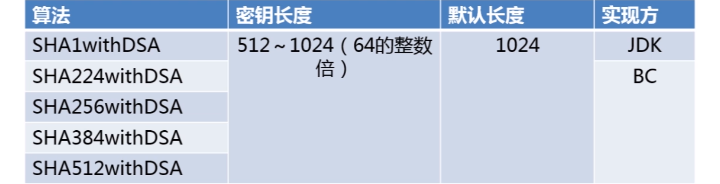
package com.bee.springboot.util.encrypt.des; import org.apache.commons.codec.binary.Base64; import org.apache.commons.codec.binary.Hex; import javax.crypto.Cipher; import java.security.*; import java.security.interfaces.DSAPrivateKey; import java.security.interfaces.DSAPublicKey; import java.security.interfaces.RSAPrivateKey; import java.security.interfaces.RSAPublicKey; import java.security.spec.PKCS8EncodedKeySpec; import java.security.spec.X509EncodedKeySpec; /** * 非对称加密 RSA */ public class BeeDSA { public static final String src = "D撒旦法sddes"; public static void main(String[] args) { jdkDSA(); } public static void jdkDSA() { try{ //1.初始化密钥 KeyPairGenerator keyPairGenerator = KeyPairGenerator.getInstance("DSA"); keyPairGenerator.initialize(512); KeyPair keyPair = keyPairGenerator.generateKeyPair(); DSAPublicKey dsaPublicKey = (DSAPublicKey) keyPair.getPublic(); DSAPrivateKey dsaPrivateKey = (DSAPrivateKey) keyPair.getPrivate(); /* System.out.println("rsaPublicKey: "+ Base64.encodeBase64String(rsaPublicKey.getEncoded())); System.out.println("rsaPrivateKey: "+ Base64.encodeBase64String(rsaPrivateKey.getEncoded()));*/ //2.私钥加密,公钥解密-----加密 PKCS8EncodedKeySpec pkcs8EncodedKeySpec = new PKCS8EncodedKeySpec(dsaPrivateKey.getEncoded()); KeyFactory keyFactory = KeyFactory.getInstance("DSA"); PrivateKey privateKey = keyFactory.generatePrivate(pkcs8EncodedKeySpec); Signature signature = Signature.getInstance("SHA1withDSA"); signature.initSign(privateKey); signature.update(src.getBytes()); byte[] result = signature.sign(); System.out.println("私钥加密,公钥解密-----加密: "+ Hex.encodeHexString(result)); //3.签名验证 X509EncodedKeySpec x509EncodedKeySpec = new X509EncodedKeySpec(dsaPublicKey.getEncoded());// 主要x509标准进行编码 keyFactory = KeyFactory.getInstance("DSA"); PublicKey publicKey = keyFactory.generatePublic(x509EncodedKeySpec); signature = Signature.getInstance("SHA1withDSA"); signature.initVerify(publicKey); signature.update(src.getBytes()); boolean bool = signature.verify(result); System.out.println("jdk dsa verify : "+bool); }catch (Exception e){ e.printStackTrace(); } } }
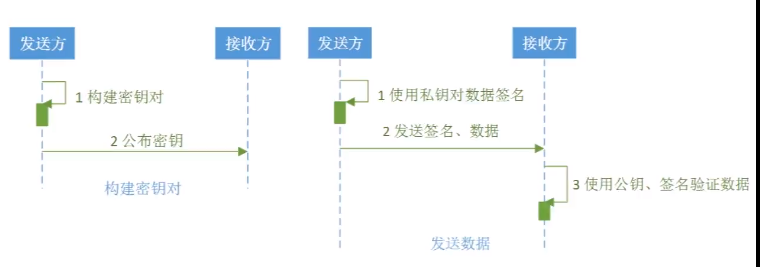

PS: 微软的操作系统、office的验证标准 都是ecdsa实现的;;;;
PS: 他是在jdk1.7以后出现的,使用的时候要注意
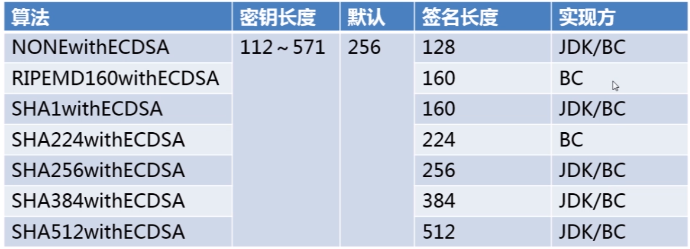
package com.bee.springboot.util.encrypt.des; import org.apache.commons.codec.binary.Hex; import java.security.*; import java.security.interfaces.ECPrivateKey; import java.security.interfaces.ECPublicKey; import java.security.interfaces.RSAPrivateKey; import java.security.interfaces.RSAPublicKey; import java.security.spec.PKCS8EncodedKeySpec; import java.security.spec.X509EncodedKeySpec; /** * 非对称加密 RSA 签名算法 */ public class BeeECDSA { public static final String src = "D撒旦法sddes"; public static void main(String[] args) { jdkECDSA(); } public static void jdkECDSA() { try{ //1.初始化密钥 KeyPairGenerator keyPairGenerator = KeyPairGenerator.getInstance("EC"); keyPairGenerator.initialize(256); KeyPair keyPair = keyPairGenerator.generateKeyPair(); ECPublicKey ecPublicKey = (ECPublicKey) keyPair.getPublic(); ECPrivateKey ecPrivateKey = (ECPrivateKey) keyPair.getPrivate(); //2.执行签名 PKCS8EncodedKeySpec pkcs8EncodedKeySpec = new PKCS8EncodedKeySpec(ecPrivateKey.getEncoded()); KeyFactory keyFactory = KeyFactory.getInstance("EC"); PrivateKey privateKey = keyFactory.generatePrivate(pkcs8EncodedKeySpec); Signature signature = Signature.getInstance("SHA1withECDSA"); signature.initSign(privateKey); signature.update(src.getBytes()); byte[] result = signature.sign(); System.out.println("jdk ecdsa sign-----加密: "+ Hex.encodeHexString(result)); //3.签名验证 X509EncodedKeySpec x509EncodedKeySpec = new X509EncodedKeySpec(ecPublicKey.getEncoded());// 主要x509标准进行编码 keyFactory = KeyFactory.getInstance("EC"); PublicKey publicKey = keyFactory.generatePublic(x509EncodedKeySpec); signature = Signature.getInstance("SHA1withECDSA"); signature.initVerify(publicKey); signature.update(src.getBytes()); boolean bool = signature.verify(result); System.out.println("jdk ecdsa verify : "+bool); }catch (Exception e){ e.printStackTrace(); } } }
