1 [root@web01 www]# cat /app/server/nginx/conf/vhosts/default.conf 2 server { 3 listen 80 default_server; 4 server_name 192.168.1.24 web01.espressos.cn; 5 root /app/www; 6 index index.php index.html index.htm; 7 location ~* .(gif|jpg|png|swf|flv)$ { #对gif,jpg,png,swf,flv后缀的文件实行防盗链 8 valid_referers none blocked 192.168.1.24 web01.espressos.cn; #对192.168.1.24 web01.espressos.cn这两个来路进行判断(主要是根椐http协议里的referer) 9 if ($invalid_referer) { #if{}里面内容的意思是,如果来路不是指定来路就跳转到错误页面,当然直接返回403也是可以的。 10 rewrite ^/ http://192.168.1.24/403.html; 11 #return 404; 12 } 13 } 14 location ~ .*.(php|php5)?$ 15 { 16 #fastcgi_pass unix:/tmp/php-cgi.sock; 17 fastcgi_pass 127.0.0.1:9000; 18 fastcgi_index index.php; 19 include fastcgi.conf; 20 } 21 access_log /app/log/nginx/access/default.log; 22 }
第8行;valid_referers none blocked *.espressos.cn *qq.com *baidu.com ;
就是白名单,允许文件链出的域名白名单,自行修改成您的域名! *.espressos.cn这个指的是子域名,域名与域名之间使用空格隔开!baidu.com是搜索引擎,做qq.com的白名单是因为可能有用户用邮箱订阅你的站点,如果不设置为白名单,用户在邮箱就无法看见你的图了,同理,如果还有其他订阅方式、搜索引擎都最好添加一下。
验证代码:
[root@web01 www]# cat q.html <html> <body><img alt="http://192.168.1.24/cat.png" src="http://192.168.1.24/cat.png" height="auto" width="auto"></body> </html> [root@web01 www]#

另一台WEB服务器盗用WEB01的图片(配置如下):
[root@lmr default]# cat /app/server/nginx/conf/vhosts/default.conf server { listen 80; server_name localhost; index index.html index.htm index.php; root /app/www/default; location ~ .*.(php|php5)?$ { #fastcgi_pass unix:/tmp/php-cgi.sock; fastcgi_pass 127.0.0.1:9000; fastcgi_index index.php; include fastcgi.conf; } location ~ .*.(gif|jpg|jpeg|png|bmp|swf)$ { expires 30d; } location ~ .*.(js|css)?$ { expires 1h; } include /app/server/nginx/conf/rewrite/default.conf; access_log /app/log/nginx/access/default.log; }
验证:
[root@lmr default]# pwd /app/www/default [root@lmr default]# cat q.html <html> <body><img alt="http://192.168.1.24/cat.png" src="http://192.168.1.24/cat.png" height="auto" width="auto"></body> </html> [root@lmr default]#
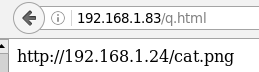
防盗成功!!!
把web01上的防盗代码注释掉:
[root@web01 www]# cat /app/server/nginx/conf/vhosts/default.conf server { listen 80 default_server; server_name 192.168.1.24 web01.espressos.cn; root /app/www; index index.php index.html index.htm; #location ~* .(gif|jpg|png|swf|flv)$ { #valid_referers none blocked 192.168.1.24 web01.espressos.cn; #if ($invalid_referer) { # rewrite ^/ http://192.168.1.24/403.html; # return 404; # } #} location ~ .*.(php|php5)?$ { #fastcgi_pass unix:/tmp/php-cgi.sock; fastcgi_pass 127.0.0.1:9000; fastcgi_index index.php; include fastcgi.conf; } access_log /app/log/nginx/access/default.log; } [root@web01 www]# /app/server/nginx/sbin/nginx -s reload
重新测式盗连图片的服务器,盗图是否成功:

图片盗连成功!!
============新测试======================
1 sh-4.1# cat /etc/nginx/vhosts/test.espressos.cn.conf 2 server { 3 listen 80; 4 server_name test.espressos.cn; 5 index index.html 123.57.37.211 index.htm index.php; 6 root /usr/html/test.espressos.cn; 7 location ~ .*.(php|php5) 8 { 9 #fastcgi_pass unix:/tmp/php-cgi.sock; 10 fastcgi_pass 127.0.0.1:9000; 11 fastcgi_index index.php; 12 include fastcgi.conf; 13 fastcgi_param PATH_INFO $fastcgi_script_name; 14 } 15 location ~ .*.(gif|jpg|jpeg|png|bmp|swf)$ 16 { 17 valid_referers none blocked 123.57.37.211 test.espressos.cn; 18 if ($invalid_referer) { 19 #rewrite ^/ http://123.57.36.227/404.html; 20 return 404; 21 } 22 } 23 location ~ .*.(js|css)?$ 24 { 25 expires 1h; 26 } 27 include /etc/nginx/rewrite/test.espressos.cn.conf; 28 access_log /var/log/nginx/test.espressos.log; 29 }
注意上面的第19和20行:(图片服务器的IP:123.57.37.211)
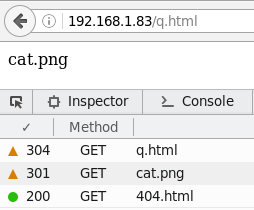
[root@lmr default]# cat q.html <html> <body><img alt="cat.png" src="http://123.57.37.211/cat.png" height="auto" width="auto"></body> </html> [root@lmr default]# 本机是另外一台WEB服务器IP192.168.1.83
访问测试面q.html(上面的页网代码),测试结果如下:

图片服务器的404.html:
1 sh-4.1# cat /usr/html/test.espressos.cn/404.html 2 error 3 sh-4.1# cat /etc/nginx/vhosts/test.espressos.cn.conf 4 server { 5 listen 80; 6 server_name test.espressos.cn; 7 index index.html 123.57.36.227 index.htm index.php; 8 root /usr/html/test.espressos.cn; 9 location ~ .*.(php|php5) 10 { 11 #fastcgi_pass unix:/tmp/php-cgi.sock; 12 fastcgi_pass 127.0.0.1:9000; 13 fastcgi_index index.php; 14 include fastcgi.conf; 15 fastcgi_param PATH_INFO $fastcgi_script_name; 16 } 17 location ~ .*.(gif|jpg|jpeg|png|bmp|swf)$ 18 { 19 valid_referers none blocked 123.57.36.227 test.espressos.cn; 20 if ($invalid_referer) { 21 rewrite ^/ http://123.57.36.227/404.html; 22 #return 404; 23 } 24 } 25 location ~ .*.(js|css)?$ 26 { 27 expires 1h; 28 } 29 include /etc/nginx/rewrite/test.espressos.cn.conf; 30 access_log /var/log/nginx/test.espressos.log; 31 }
注意21和22行(上为图片服务器的web配置文件)