一、Harbor
是由VMware公司的中国团队开发的。私有的docker镜像仓库。
Harbor是一个开放源代码可信云本机注册表项目,用于存储,签名和扫描内容。Harbor通过添加
用户通常需要的功能(例如安全性,身份和管理)扩展了开源Docker Distribution。使注册表更
接近于构建和运行环境可以提高图像传输效率。Harbor支持在注册表之间复制映像,还提供高级
安全功能,例如用户管理,访问控制和活动审核。
官方:https://hub.docker.com/
第三方:https://registry.cn-hangzhou.aliyuncs.com
私有的docker镜像仓库:Harbor
1、登录注册
2、安全认证
3、镜像仓库
官网:https://goharbor.io/
| 硬件 |
最低要求 |
推荐 |
| CPU |
2 CPU |
4 CPU |
| 内存 |
4GB |
8 GB |
| 磁盘 |
40 GB |
160 GB |
二、安装部署Harbor
#安装依赖
[root@harbor ~]# yum install -y yum-utils device-mapper-persistent-data lvm2
#安装阿里云源仓库
[root@harbor ~]# yum-config-manager --add-repo https://mirrors.aliyun.com/docker-ce/linux/centos/docker-ce.repo
[root@harbor ~]# sed -i 's+download.docker.com+mirrors.aliyun.com/docker-ce+' /etc/yum.repos.d/docker-ce.repo
#查看docker版本
[root@harbor ~]# yum list docker-ce --showduplicates | sort -r
#选择19版本,进行安装
[root@harbor ~]# yum install -y docker-ce-19.03.9
[root@harbor ~]# mkdir /etc/docker -p
[root@harbor ~]# cd /etc/docker
[root@harbor ~]# cat > /etc/docker/daemon.json <<EOF
{
"registry-mirrors": ["https://dp0vxr93.mirror.aliyuncs.com"]
}
EOF
[root@harbor ~]# systemctl daemon-reload
[root@harbor ~]# systemctl enable --now docker
#安装OpenSSL
[root@harbor ~]# yum install openssl openssl-devel -y
#下载Harbor
下载地址: https://github.com/goharbor/harbor/releases
[root@harbor ~]# tar xf harbor-offline-installer-v2.3.3.tgz -C /usr/local/
#安装docker-compose
下载地址:https://github.com/docker/compose/releases
[root@harbor /usr/local/bin]# wget https://github.com/docker/compose/releases/download/1.29.2/docker-compose-Linux-x86_64
[root@harbor /usr/local/bin]# mv docker-compose-Linux-x86_64 docker-compose
[root@harbor /usr/local/bin]# chmod +x docker-compose
[root@harbor /usr/local/bin]# docker-compose version
docker-compose version 1.29.2, build 5becea4c
docker-py version: 5.0.0
CPython version: 3.7.10
OpenSSL version: OpenSSL 1.1.0l 10 Sep 2019
#生成CA证书私钥
[root@harbor ~]# mkdir /opt/ssl
[root@harbor ~]# cd /opt/ssl
[root@harbor /opt/ssl]# openssl genrsa -out ca.key 4096
#生成CA证书
[root@harbor /opt/ssl]# openssl req -x509 -new -nodes -sha512 -days 3650 -subj "/C=CN/ST=ShangHai/L=ShangHai/O=example/OU=Personal/CN=10.0.0.75" -key ca.key -out ca.crt
#生成服务器端证书
1.生成私钥
[root@harbor /opt/ssl]# openssl genrsa -out 10.0.0.75.key 4096
2.生成证书签名请求
[root@harbor /opt/ssl]# openssl req -sha512 -new -subj "/C=CN/ST=ShangHai/L=ShangHai/O=example/OU=Personal/CN=10.0.0.75" -key 10.0.0.75.key -out 10.0.0.75.csr
#生成x509 v3服务文件
[root@harbor /opt/ssl]# cat > v3.ext <<-EOF
authorityKeyIdentifier=keyid,issuer
basicConstraints=CA:FALSE
keyUsage = digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment
extendedKeyUsage = serverAuth
subjectAltName = IP:10.0.0.75
EOF
#使用该 v3.ext 文件为您的Harbor主机生成证书
[root@harbor /opt/ssl]# openssl x509 -req -sha512 -days 3650 \
-extfile v3.ext \
-CA ca.crt -CAkey ca.key -CAcreateserial \
-in 10.0.0.75.csr \
-out 10.0.0.75.crt
#使用该 v3.ext 文件为您的Harbor主机生成证书
[root@harbor /opt/ssl]# openssl x509 -inform PEM -in 10.0.0.75.crt -out 10.0.0.75.cert
[root@harbor /opt/ssl]# ll
-rw-r--r-- 1 root root 2053 Nov 10 20:13 10.0.0.75.cert
-rw-r--r-- 1 root root 2053 Nov 10 20:12 10.0.0.75.crt
-rw-r--r-- 1 root root 1704 Nov 10 20:10 10.0.0.75.csr
-rw-r--r-- 1 root root 3243 Nov 10 20:09 10.0.0.75.key
-rw-r--r-- 1 root root 2033 Nov 10 20:06 ca.crt
-rw-r--r-- 1 root root 3243 Nov 10 20:06 ca.key
-rw-r--r-- 1 root root 17 Nov 10 20:12 ca.srl
-rw-r--r-- 1 root root 201 Nov 10 20:12 v3.ext
#创建docker证书存放目录
[root@harbor /opt/ssl]# mkdir -p /etc/docker/certs.d/10.0.0.75
[root@harbor /opt/ssl]# cp 10.0.0.75.key /etc/docker/certs.d/10.0.0.75/
[root@harbor /opt/ssl]# cp 10.0.0.75.cert /etc/docker/certs.d/10.0.0.75/
[root@harbor /opt/ssl]# cp ca.crt /etc/docker/certs.d/10.0.0.75/
[root@harbor /opt/ssl]# ll /etc/docker/certs.d/10.0.0.75
-rw-r--r-- 1 root root 2053 Nov 10 20:16 10.0.0.75.cert
-rw-r--r-- 1 root root 3243 Nov 10 20:16 10.0.0.75.key
-rw-r--r-- 1 root root 2033 Nov 10 20:16 ca.crt
[root@harbor /opt/ssl]# systemctl restart docker
#编辑yml文件
[root@harbor /opt/ssl]# cd /usr/local/harbor
[root@harbor /usr/local/harbor]# cp harbor.yml.tmpl harbor.yml
[root@harbor /usr/local/harbor]# vim harbor.yml
hostname: 10.0.0.75
certificate: /opt/ssl/10.0.0.75.crt
private_key: /opt/ssl/10.0.0.75.key
#生成配置并安装
[root@harbor /usr/local/harbor]# ./prepare
[root@harbor /usr/local/harbor]# ./install.sh
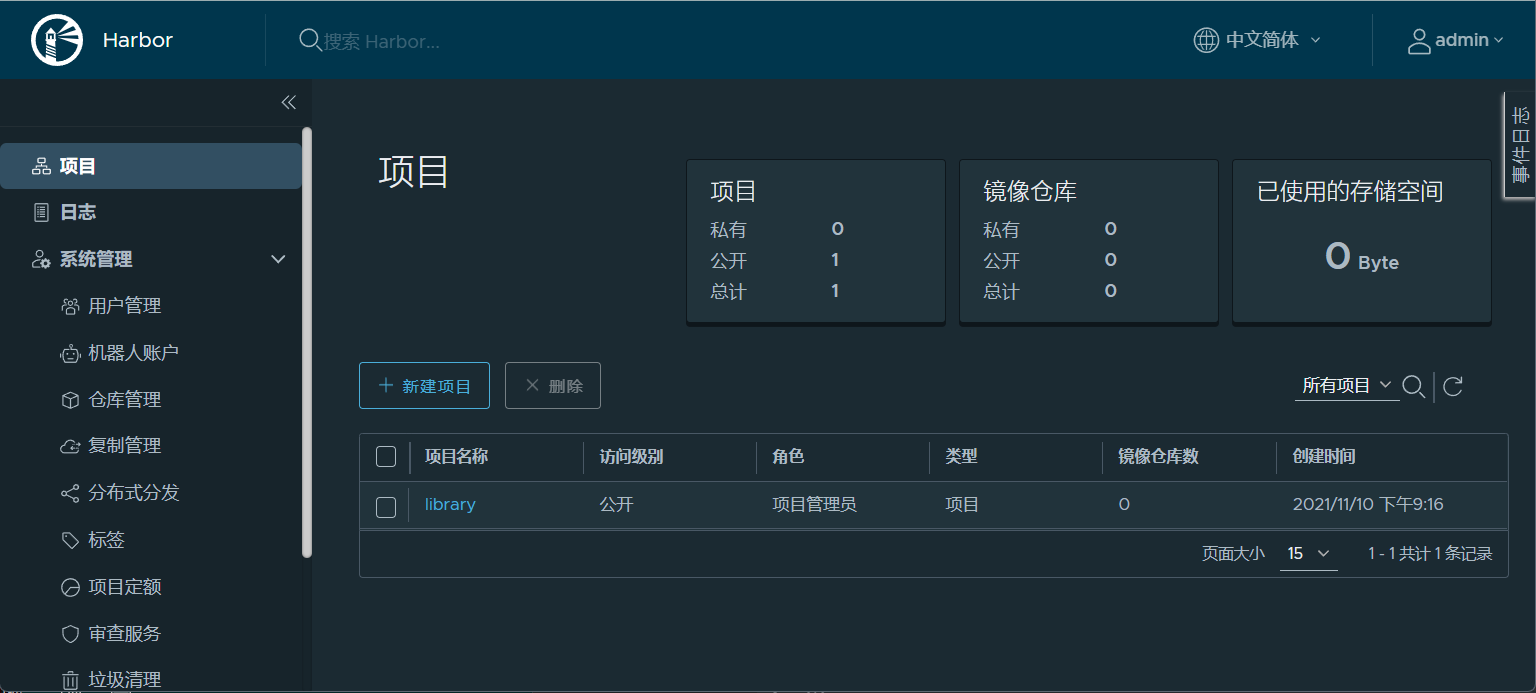
#浏览器访问10.0.0.75:80
#用户:admin
#密码:Harbor12345
3.报错
[root@harbor /usr/local/harbor]# docker login 10.0.0.75
Username: root
Password:
Error response from daemon: Get https://10.0.0.75/v2/: x509: certificate signed by unknown authority
#修改 /lib/systemd/system/docker.service 文件里的 ExecStart= 行:
[root@harbor /usr/local/harbor]# vim /lib/systemd/system/docker.service
ExecStart=/usr/bin/dockerd -H fd:// --containerd=/run/containerd/containerd.sock --insecure-registry=10.0.0.75
#重载、重启 docker 服务
[root@harbor /usr/local/harbor]# systemctl daemon-reload
[root@harbor /usr/local/harbor]# systemctl restart docker
#登录
[root@harbor /usr/local/harbor]# docker login 10.0.0.75
Username: root
Password:
WARNING! Your password will be stored unencrypted in /root/.docker/config.json.
Configure a credential helper to remove this warning. See
https://docs.docker.com/engine/reference/commandline/login/#credentials-store
Login Succeeded
